Home » Cybersecurity » Threats & Breaches » Vulnerabilities » Trojanized PyPI Package Imitates a Popular Python Server Library
Trojanized PyPI Package Imitates a Popular Python Server Library
Sonatype has once again stumbled upon a malicious Python package called ‘aiohttp-socks5‘—this time imitating a massively popular middleware library. But instead, this package drops a Remote Access Trojan (RAT) that compromises your system completely.
The legitimate AIOHTTP library is a popular asynchronous HTTP Client/Server for the asyncio library and Python-based applications. The component receives over 9 million weekly downloads on average.
AIOHTTP powers famous sites like Yandex, Skyscanner, Farmer Business Network, among others, and has been used to build commonly used libraries, which explains why would threat actors capitalize on the opportunity to ship counterfeit versions of AIOHTTP.
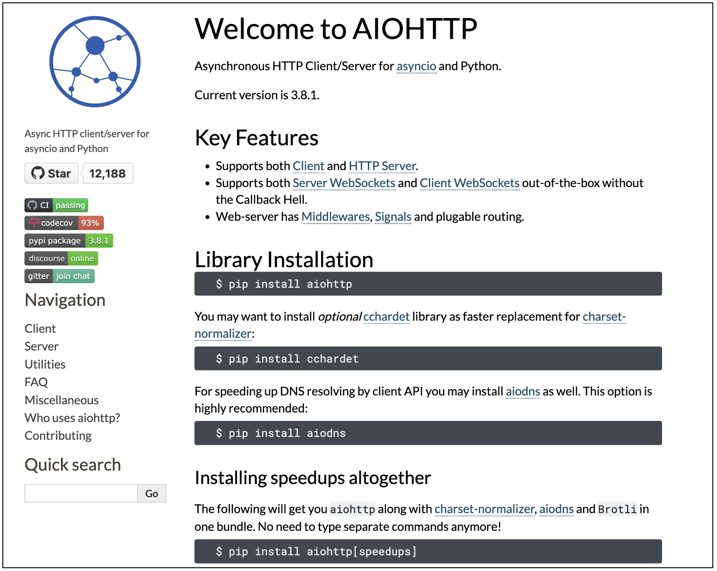
For developers looking to make AIOHTTP work with SOCKS4/SOCKS5 proxies, maintainers of AIOHTTP recommend using the aiohttp-socks component.

But this week, Sonatype’s automated malware detection systems came across a counterfeit component named aiohttp-socks5, claiming itself to be a “proxy connector for aiohttp,” which is far from the case. Instead, aiohttp-socks5 is spyware primarily targeting Windows 64-bit users, with some versions of the component capable of also running on Linux, Termux, and macOS systems.
Sources indicate ‘aiohttp-socks5’ has been retrieved over 2,200 times since its publication, both in form of user-initiated downloads and by automated mirrors.
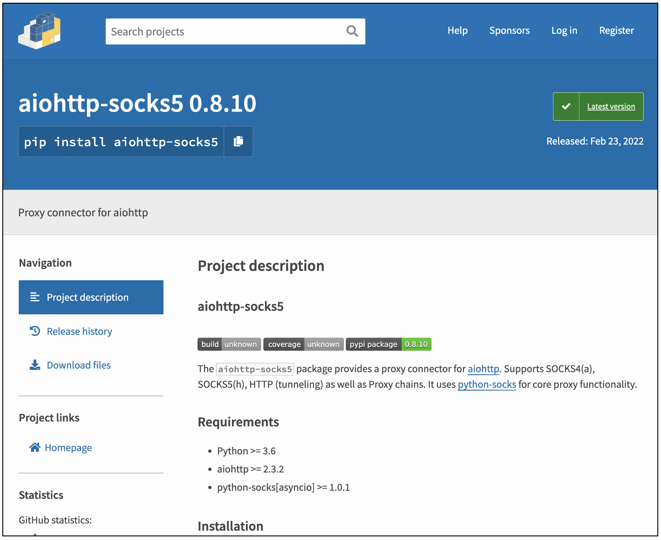
The malicious ‘aiohttp-socks5’ had 11 versions when discovered, with different versions conducting varied levels of malicious activity.
The first version of ‘aiohttp-socks5’ (0.7.1) largely appears to be benign, borrowing skeleton code from the legitimate aiohttp-socks package. But subsequent versions are spyware packed with malicious trojans.
Fake ‘metadata’ field packs malicious EXE
Starting with version 0.8.1 of ‘aiohttp-socks5’ we see the setup.py manifest file containing a sneaky ‘metadata’ field toward the end:

This so-called ‘metadata’ variable contains a long string value that spans hundreds of lines. Essentially, the ‘metadata’ field is just a ploy (Read more...)
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Ax Sharma. Read the original post at: https://blog.sonatype.com/trojanized-pypi-package-imitates-a-popular-python-server-library





