Cybersecurity News Round-Up: Week of January 24, 2022

Hello and welcome back to the GlobalSign blog. Fortunately there have not been any new major incidents, but of course, there’s still plenty of news to cover! Let’s dig in.
The LockBit ransomware gang is claiming to have hit France’s Ministry of Justice as part of its recent spree of ransomware attacks, such as Linux servers. According to the group’s official website the Ministry has 13 days to meet its demands or sensitive data of it will be published on February 10th. Targets of the attack supposedly extend beyond the Ministry, and includes entities in Spain, Italy, France, Germany and the United Kingdom.
Canada’s federal government confirmed this week it was responding to a “cyber incident” that was first detected on Jan. 19 targeting Global Affairs Canada (GAC). While mitigation actions were taken on the same day, the attacks continued to cause disruptions to numerous departmental systems on Monday and would take “days” to address, sources told National Post.
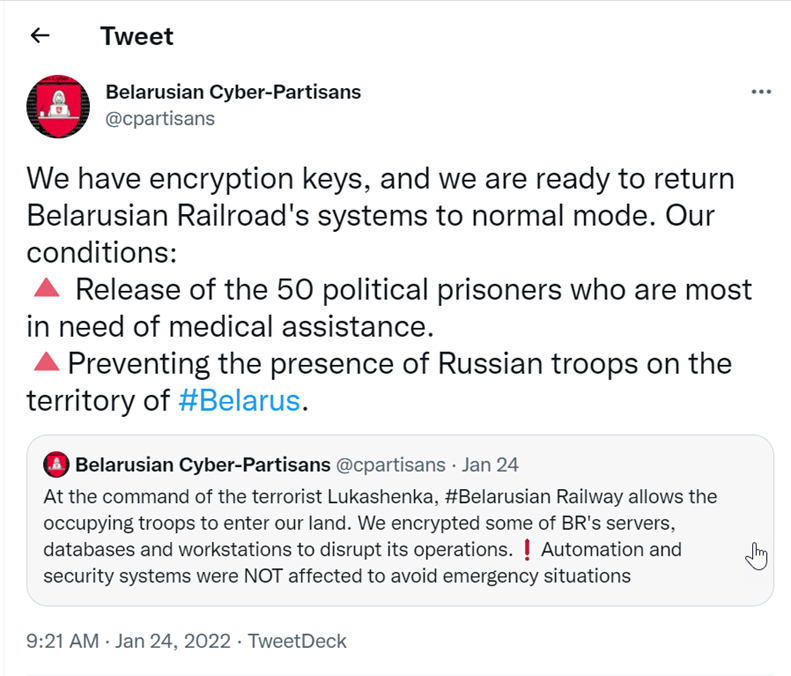
The Belarusian hacktivist group, known as The Belarusian Cyber-Partisans allegedly launched a ransomware attack against Belarus’s railway system. The hacktivist organization revealed the details on Twitter, claiming it encrypted the Belarusian Railways’ networks, which crippled the system and disrupted their ticket sales. They say they implemented the attack in protest of the government of President Alexander Lukashenko and the surge in Russian troops movements across Belarus. The hacktivists criticized the policies of Lukashenko, referring to him as a “terrorist,” and posted a list of demands to provide encryption keys to unlock the system.
Germany’s domestic intelligence services, known as the BfV, is warning of ongoing attacks coordinated by the APT27 Chinese-backed hacking group. The latest campaign targets German commercial organizations, with the attackers using the HyperBro remote access trojans (RAT) to backdoor their networks. The agency said the threat group’s goal is to steal sensitive information and may also attempt to target their victims’ customers in supply chain attacks. A year ago, APT27 was thought to be behind some attacks on major videogame companies.
Another week, another warning from Microsoft. This time, the software giant is warning that Office 365 customers are receiving phishing emails that aim to trick them into giving OAuth permissions to a bogus app that then lets attackers read and write emails. The attackers are sending emails to “hundreds” of Office 365 customers. A potentially malicious app, dubbed ‘Upgrade’, asks users to grant it OAuth permissions that would allow attackers to create inbox rules, read and write emails and calendar items, and read contacts, according to Microsoft Security Intelligence.

Finally, U.S. Securities and Exchange Commission (SEC) Chairman Gary Gensler is exploring an expansion of the SEC’s core cybersecurity rules to cover a broader swath of entities and require public companies to improve disclosure of breaches and risks. In a speech on Monday, Gensler said that SEC staff may update the commission’s “Regulation Systems Compliance and Integrity,” or Reg SCI, which the SEC adopted in 2014. SEC staff is considering recommendations on bolstering the financial sector’s cybersecurity hygiene and incident reporting, how customers and clients receive notifications of financial sector breaches and how public companies disclose cybersecurity practices and risks. And he wants staff to examine how to better address cyber risk that comes from service providers.
That’s a wrap for this week. Thanks for stopping by our blog and have a great weekend!
Amy
Top Global Industry News
HackRead (January 27, 2022) LockBit ransomware hits French Ministry of Justice & European firms
The infamous LockBit ransomware gang is claiming to have hit the Ministry of Justice of France (justice.fr) as part of its recent spree of ransomware attacks. Although the details of the attack are limited, according to the group’s official website the Ministry has 13 days to meet its demands or sensitive data of it will be published on February 10th, 2022.
Hackread.com can exclusively confirm that the ransomware attack was not limited to the French Ministry of Justice. In fact, the group is claiming responsibility for hitting several top companies and businesses in several European countries including Spain, Italy, France, Germany, and United Kingdom.
The full list of recent alleged victims of the LockBit ransomware gang are:
- Izo Group, Spain (Izo.es)
- ESTPM, France (Estpm.fr)
- City of Saint Cloud, France (Saintcloud.fr)
- Joda, Germany (Joda.de)
- Heubeck AG, Germany (Heubeck.de)
- Isnardi, Italy (Isnardi.it)
- La Ponte Marmi Srl, Italy (laponte.it)
- AMBAU Personalservice, Germany (Ambau-team.de)
- Girlguiding Charity, United Kingdom (Girlguidinglaser.org.uk)
ZDNet (January 27, 2022) $300,000 in fines issued as Canadian officials take down dark web marketplace
Officials said they shut down CanadianHQ, which they claimed was one of the largest Dark Web marketplaces in the world.
Officials with the Canadian Radio-television and Telecommunications Commission (CRTC) said they took down dark web marketplace Canadian HeadQuarters on Wednesday and fined four of those involved in the platform.
In a statement, CRTC chief compliance and enforcement officer Steven Harroun said Canadian HeadQuarters, also known and Canadian HQ, was “one of the largest Dark Web marketplaces in the world and significantly contributed to harmful cyber activity in Canada.”
CRTC staff executed warrants in the greater Montreal area through 2020 and 2021 that led to the marketplace being taken offline. They also issued fines to Chris Tyrone Dracos, Marc Anthony Younes, Souial Amarak and Moustapha Sabir. Dracos was given a $150,000 fine, and the other three were given $50,000 fines.
Bleeping Computer (January 26, 2022) German govt warns of APT27 hackers backdooring business networks
The BfV German domestic intelligence services (short for Bundesamt für Verfassungsschutz) warn of ongoing attacks coordinated by the APT27 Chinese-backed hacking group.
This active campaign is targeting German commercial organizations, with the attackers using the HyperBro remote access trojans (RAT) to backdoor their networks.
HyperBro helps the threat actors maintain persistence on the victims’ networks by acting as an in-memory backdoor with remote administration capabilities.
The agency said the threat group’s goal is to steal sensitive information and may also attempt to target their victims’ customers in supply chain attacks.
HackRead (January 25, 2022) Cyber-Partisans hackers hit Belarus railroad system with ransomware attack
Belarusian hacktivist group, known as The Belarusian Cyber-Partisans allegedly launched a ransomware attack against Belarus’s railway system to protest against the government of President Alexander Lukashenko and the surge in Russian troops movements across Belarus.
The hacktivist group took to Twitter to reveal details of the hack. The group claimed it encrypted the Belarusian Railways’ networks, which crippled the system and disrupted their ticket sales.
The hacktivists criticized the policies of Lukashenko, referring to him as a “terrorist,” and posted a list of demands to provide encryption keys to unlock the system.
ZDNet (January 25, 2022) Microsoft warns about this phishing attack that wants to read your emails
Microsoft is warning that Office 365 customers are receiving phishing emails that aim to trick them into giving OAuth permissions to a bogus app that then lets attackers read and write emails.
Microsoft’s Security Intelligence team warned this week that attackers are sending the OAuth phishing emails to “hundreds” of Office 365 customers.
The potentially malicious app, dubbed ‘Upgrade’, asks users to grant it OAuth permissions that would allow attackers to create inbox rules, read and write emails and calendar items, and read contacts, according to Microsoft Security Intelligence.
Cyberscoop (January 25, 2022) SEC’s Gensler signals enhancement of cybersecurity, breach disclosure rules for financial sector
U.S. Securities and Exchange Commission Chairman Gary Gensler is exploring an expansion of the SEC’s core cybersecurity rules to cover a broader swath of entities and require public companies to improve disclosure of breaches and risks.
Gensler said in a speech on Monday that he instructed staff to look into an update of the commission’s “Regulation Systems Compliance and Integrity,” or Reg SCI, which the SEC adopted in 2014. Staff will examine whether the regulation — under which trading organizations and others must take security steps like backing up data — should extend to include the largest market-makers and broker-dealers.
Gensler also said he asked staff to consider recommendations on bolstering the financial sector’s cybersecurity hygiene and incident reporting, how customers and clients receive notifications of financial sector breaches and how public companies disclose cybersecurity practices and risks. And he wants staff to examine how to better address cyber risk that comes from service providers.
National Post (January 24, 2022) Canada’s foreign affairs department targeted in ‘significant’ cyber attack
The federal government confirmed on Monday that it was responding to a “cyber incident” that was first detected on Jan. 19 targeting Global Affairs Canada (GAC).
Mitigation actions were taken on the same day, but the attacks continued to cause disruptions to a host of departmental systems on Monday and would take “days” to address, sources told National Post. For example, many said they were barred from browsing the Internet, but could still use their work email.
“Critical services for Canadians through Global Affairs Canada are currently functioning. Some access to Internet and internet-based services are not currently available as part of the mitigation measures and work is underway to restore them,” read a statement from the Treasury Board of Canada Secretariat.
Other Top Industry News
Malicious PowerPoint files used to push remote access trojans – Bleeping Computer
Merck wins cyber-insurance lawsuit related to NotPetya attack – The Record by Recorded Future
Pennsylvania approves ransomware bill – InfoSecurity
Push to Explain What Software Contains Gains Steam After Log4j Flaw – Wall Street Journal (requires subscription)
Outpatient Facilities Continue To Be Targeted In Healthcare Cyberattacks – HealthITSecurity
Segway store hacked to steal customers’ credit cards – Bleeping Computer
FCC Proposes Stricter Regulations for Data Breach Disclosure – Security Boulevard
*** This is a Security Bloggers Network syndicated blog from Blog Feed authored by Blog Feed. Read the original post at: https://www.globalsign.com/en/blog/cybersecurity-news-round-week-january-24-2022





