12 Days of Phish-mas: A Festive Look at Phishing Examples
The holidays are synonymous with cold weather, good food, and spending time with family. But for cybercriminals, it’s a lucrative time of the year for phishing attacks. We’ll explore more than a dozen phishing examples you can learn from to avoid falling for cyber scams in the 2021 holiday season (and in the year 2022 to come)!
It’s that time of the year: Christmas decorations can now be found virtually everywhere you go and holiday sales abound online. But this time of the year also has a dark side — it represents a great opportunity for cybercriminals to carry out phishing scams on unsuspecting holiday shoppers.
According to Barracuda, the holidays are a time when phishing-related cybercrimes spike. Their data shows that in 2020, spearphishing attacks increased by more than 150% above average in the days leading up to Christmas and then those rates fell significantly following the holiday.
But the reality is that phishing scams aren’t limited to just the holiday season, and they’re not limited to targeting only shoppers. It’s no surprise that cybercriminals love to use phishing scams as a way to take advantage of unsuspecting or cyber ignorant users. As I recently discussed in a recent interview with PrivateInternetAccess.com, cybercriminals love to focus on the “soft” targets within your business — people they can trick, coerce, or manipulate into making a big mistake (such as giving them your login information or making a fraudulent payment to them).
But what are some common signs of phishing? We’ll explore phishing email examples and other common scams you’re likely to receive via phone calls (vishing) and text messages (smishing) long after the holiday season has passed. We’re only going to share 1-2 examples for each topic because this article will otherwise get out of control very quickly. With all of this in mind…
Let’s hash it out.
On the First Day of Phish-mas, a Hacker Sent to Me… A Poorly Written Communication
The weather outside is frightful — and so are the grammar, spelling, and punctuation found in many phishing messages. Bad writing is one of the most obvious indicators of a phishing email or text; these scammers often don’t speak English as a primary language. Even if they are native English speakers, they tend to not put much effort into creating these messages. In many cases, they can’t even be bothered to create content with consistent designs or colors.
Sending out general phishing messages is largely a numbers game — it’s about hitting as many targets as possible while expending the least amount of effort. If an attacker sends out a general phishing message to 10,000 users, a handful of people may fall for it and that number may be profitable enough to make their minimal effort worthwhile.
Here’s a look at an example of a poorly written email phishing message I recently received:
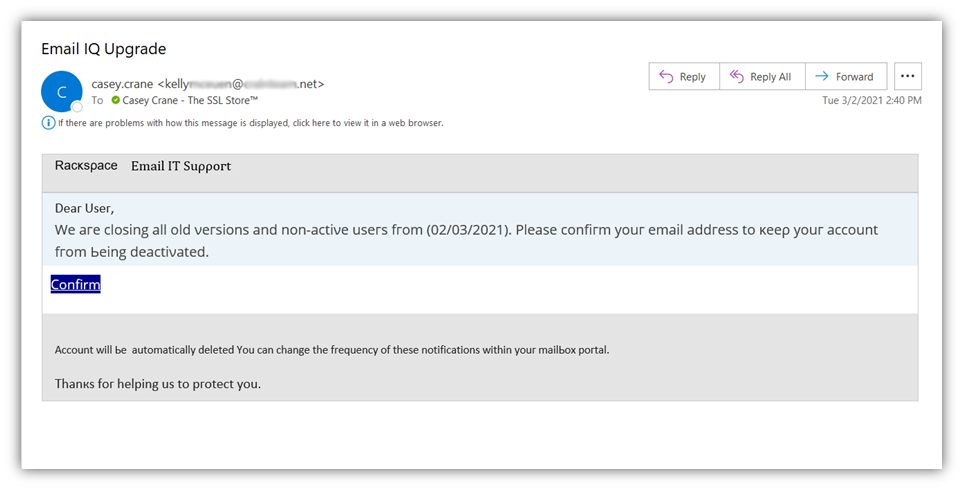
First, you’ll probably notice the lack of Rackspace branding in the message. Next, you’ll likely notice the apparent brain aneurysm they had while adding the mix of colors and typefaces to the message. Yeah, that’s pretty hinky and definitely off-brand. But if all of that wasn’t enough, you’ll then probably notice the typos and use of non-ASCII characters. (Speaking of, look at that email subject line: Email IQ Upgrade… yup, cracked me up, too!)
All of these things combined is sure to scream “phishing scam email!” But, of course, there are some other obvious issues here as well when you look at the message a little more closely:
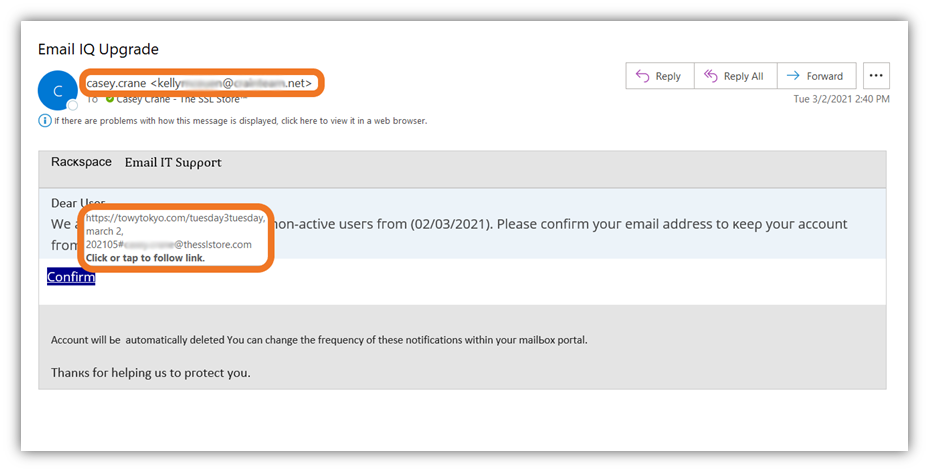
One glaring giveaway is that they embedded a link to a blatantly phony phishing website. This clearly indicates that the message didn’t come from Rackspace because, if it did, it would have included a link to Rackspace’s official website.
The cherry on top for me is that they made the interesting choice of sending the email to me while pretending to be me. However, they used an email address that clearly doesn’t belong to me or The SSL Store. Umm… yeah. They didn’t think I’d realize that I wouldn’t send an email like that to anyone, let alone myself? Yeah… SMH.
But enough about that — let’s quickly look at another example of a poorly written phishing email:
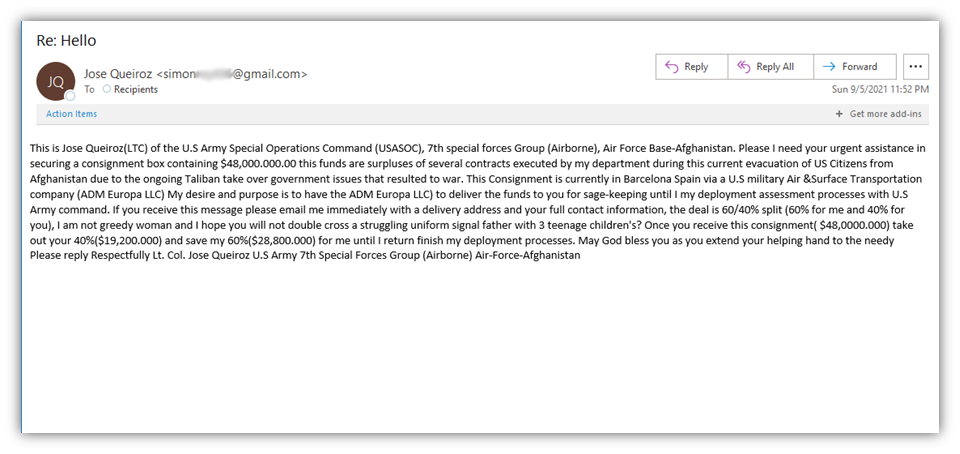
- The unsolicited email comes from an entirely unrelated email account. (The sender’s display name is Jose yet the email comes from a “simon” email address.)
- The message is trying to entice and coerce me into responding by promising millions of dollars
- Typos, punctuation issues, and poor grammar abound in this phishing example email.
- Jose describes himself both as “not a jealous woman” and a single father of three kids… in the same sentence!
Forget the hippopotamus — this scammer should be hoping to receive a subscription to Grammarly for Christmas!
On the Second Day of Phish-mas, a Hacker Sent to Me… 2 Phony Copyright Emails
Scammers love trying to find new ways to scam people and their activities aren’t limited to just the holidays. In many cases, they’re content to simply slap a new shade of lipstick on the same pig. Rather than reinventing the wheel by coming up with entirely new scams, they’ll instead change up their storylines or tactics for old ones. One such example is the ongoing copyright infringement scam.
This type of phishing scam involves an attacker sending you an email that falsely claims that you’ve committed some type of copyright infringement by using one of their images without their permission. The goal here is typically one of two things:
- To trick you into clicking on a phishing or malicious link, or
- To get you to link to their fake website, which helps their scam site gain higher domain authority (i.e., better rankings on Google and other search engines).
Let’s take a quick peek at one such example I recently received:
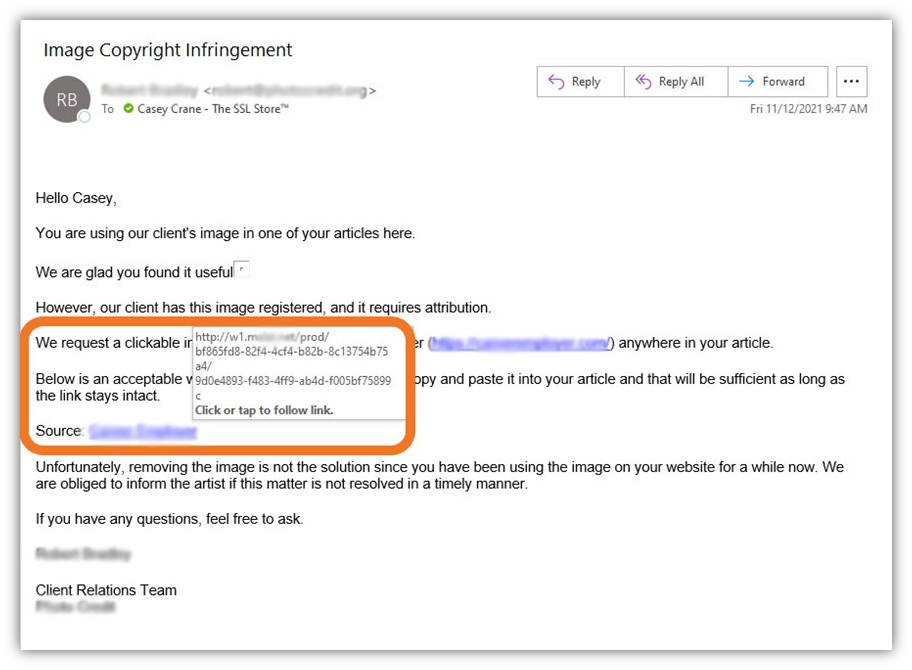
In this phishing example, the threat actor poses as a copyright notice organization and claims that we’ve used an image without their client’s approval. But there are two key issues with this:
- Their vague email doesn’t specify which image specifically we’ve allegedly used — and their apparent remedy is for us to add a link to their site’s home page as attribution to the unspecified image.
- Let’s consider the links. The first link they include leads to the homepage of the described website, but the second link is a clear phishing link. If I click on it, it’s possible that my device could become infected with malware.
No, thanks. I’m pretty sure our IT admin doesn’t want to spend his holiday season wiping malware and fixing other issues that would be caused by me or any other employees who fall for such scams…
On the Third Day of Phish-mas, a Hacker Sent to Me… 3 Urgent Messages
Urgent messages and phishing scams go together like coal and Santa’s naughty list. Creating a sense of urgency, fear, panic, excitement, or by eliciting other emotional responses is a tactic that’s commonly used in social engineering scams. The idea here is that if the attacker can do something to trick, provoke or coerce you into clicking on a phishing link, sending them sensitive information, or calling them on the phone.
Let’s take a quick look at a Microsoft subscription phishing email that one of my colleagues received:
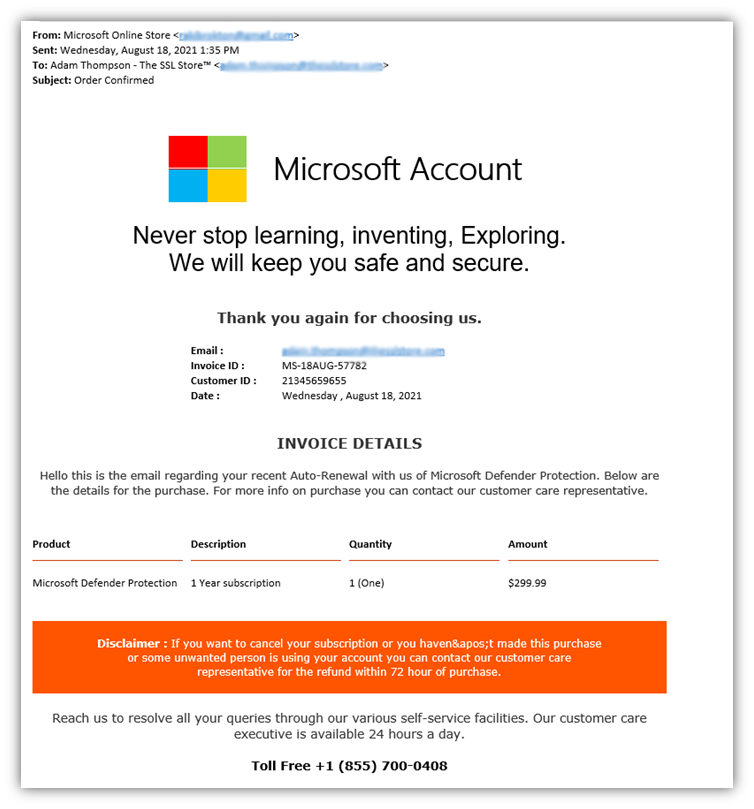
The example above is an invoice phishing message that’s designed to look like an official Microsoft message. However, unlike most of the phishing examples we share in this article, this one is a bit different in that these email scams typically turn into vishing scams as well.
Here, the attacker uses urgent language to prompt you to call them right away, stating you only have 72 hours to request a refund.
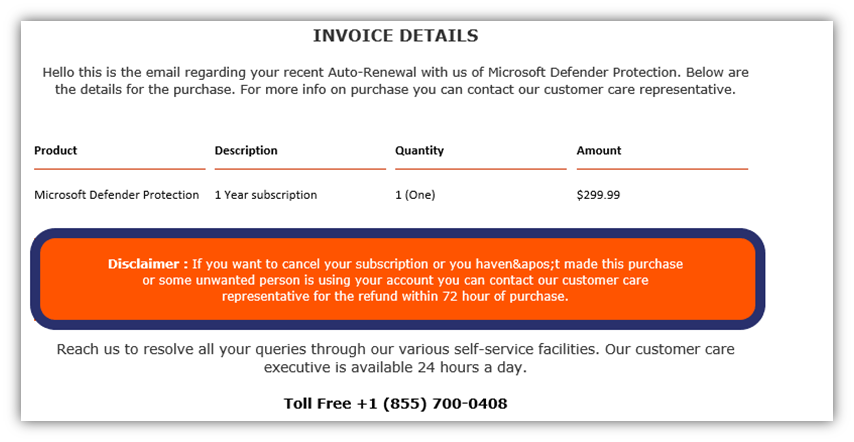
Why bother with the phone number? It’s because they want to get you on the line so they can try to get you to do one of the following:
- Make a payment over the phone,
- Share credit card, bank account, or personal information over the phone, or
- Direct you to download remote desktop software that gives them access to your device (and any networks and other devices its connected to).
On the Fourth Day of Phish-mas, a Hacker Sent to Me… 4 Malicious Attachments
Malicious email attachments are seemingly as plentiful as snowflakes in the winter. They’re found everywhere and are just as annoying as snow when you’re leaving for work and discover your freshly shoveled driveway has been snowplowed in.
But unlike a snowplow, which creates a frustrating situation, malicious email attachments are dangerous and pose a threat to your data, device, network, customers and company as a whole. Let’s consider the following example:
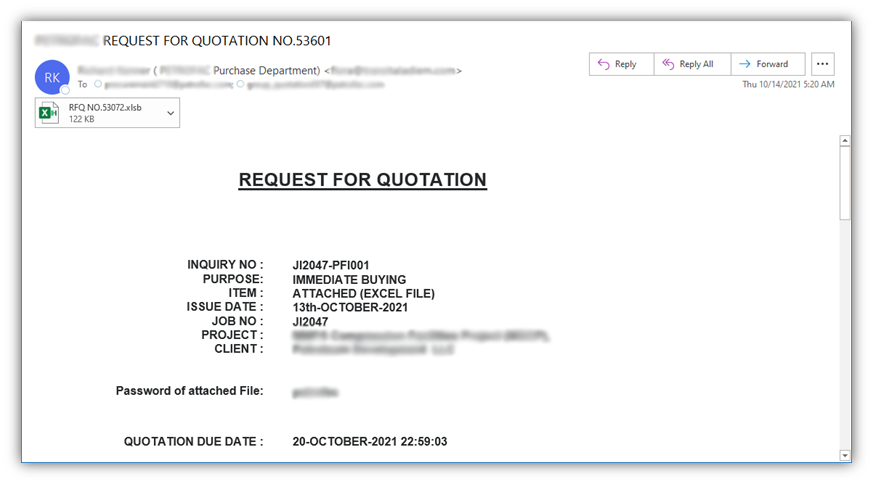
In the phishing example above, I received a fake request for a quote that contains a potentially malicious Microsoft Office file attachment. Office files, including Word docs and Excel spreadsheets, are commonly used to spread malware and embedded phishing links via email. In fact, SonicWall’s research shows that weaponized Microsoft Office files increased 67% in 2020.
What makes these file attachments potentially so dangerous? These attachments may install malware onto your device that can do everything from stealing your login or baking account information to encrypting your data and locking your device. Furthermore, businesses typically don’t block these files because they’re commonly used and shared by employees in their day-to-day jobs.
As such, it’s best to avoid these issues altogether by not engaging with any attachments in suspicious emails and by not opening unsolicited emails from unknown individuals in general.
On the Fifth Day of Phish-mas, a Hacker Sent to Me… 5 Links to Phishing Websites
Here come phishing links, here come malicious links — we receive them every day! … Yes, I’ve got so many different cybersecurity-themed parodies of Christmas carols and songs floating through my head right now that it’s not even funny. Sorry.
As you’ll see with the following screenshots of phishing examples, there’s typically a lot of overlap in email phishing examples in terms of certain attributes to look out for. For example:
- Phishing emails frequently have mismatched or incorrect information in the “From” sender field.
- Many different types of phishing messages include links to phony websites or legitimate websites that have been hacked and are controlled by the attacker.
With this in mind, let’s explore the first of our two phishing examples of emails that tried to direct me to visit their highly suspect websites:
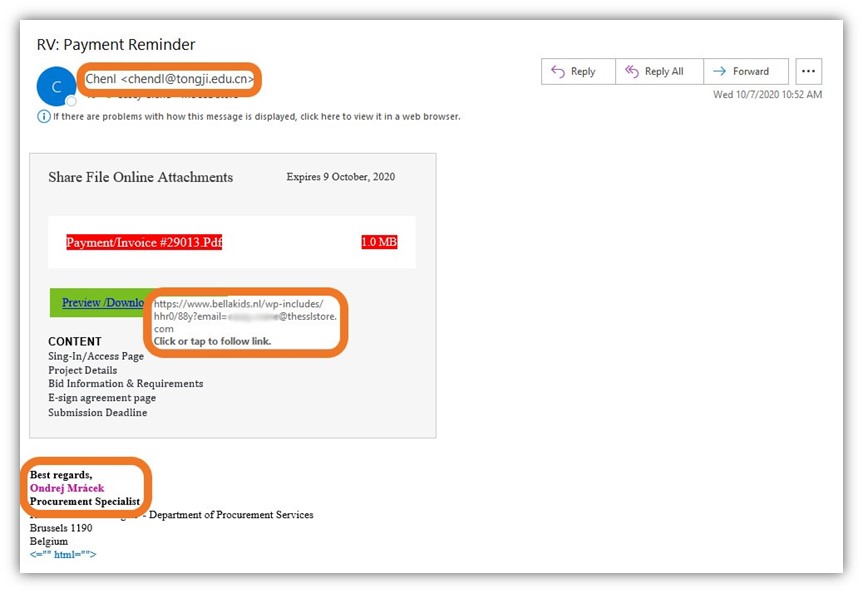
The goal here is to get me to click on the “Download Attachment” phishing link that’s designed to look like a button. Doing so will take me to a site where the attacker will try to coerce me to log in so they can steal my credentials.
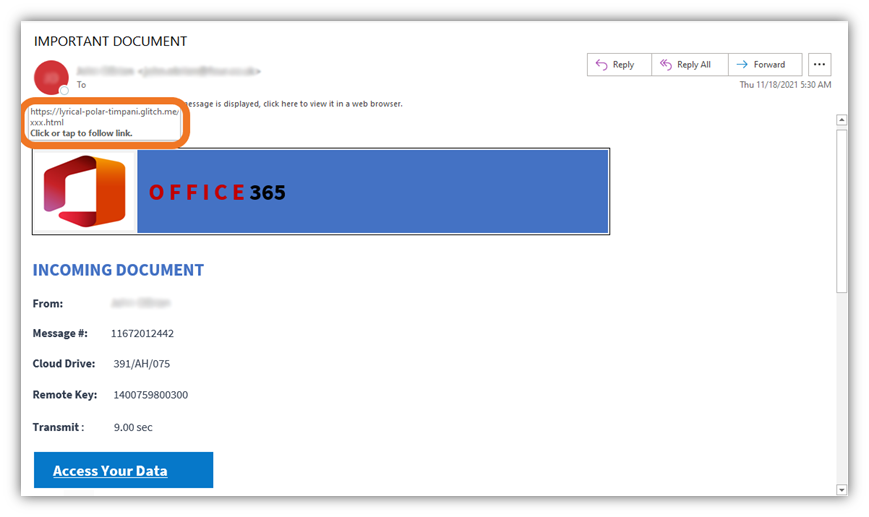
This next example, shown below, is much the same. The email is designed to look like a Microsoft Office 365 and provides a link under the guise of having important information for you to access. However, if you look at that URL, you’ll quickly see how illegitimate it really is. I’m quite certain that Office 365 wouldn’t be using legitimate URLs that contain “XXX” in the web address…
On the Sixth Day of Phish-mas, a Hacker Sent to Me… 6 Requests for Data
Cybercriminals love data and will do everything within their power to get their hands on it. And we can assure you — they’re not looking for a Naughty and Nice list to become Santa’s little helpers. Having access to your most sensitive data — login credentials, employee records, customer contact lists, intellectual property, personally identifiable information, etc. — gives them many reasons to celebrate.
If you unknowingly send customers’ or employees’ personally identifying information (PII) to cybercriminals, the effects of that mistake can be felt for years to come in the form of:
- Identity theft issues,
- Non-compliance fines and penalties,
- Lawsuits, and
- A spoiled reputation and brand image.
Let’s take a look at a phishing email that one of my colleagues received that requested her personal sensitive information:
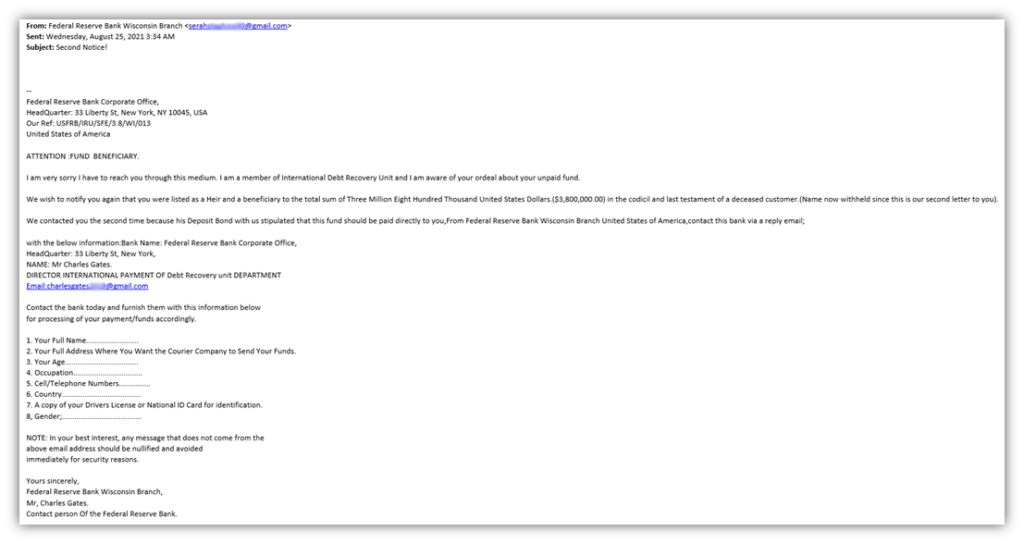
This is an email that’s listed as coming from the Federal Reserve Bank Wisconsin Branch and contains a message saying that she’s they’ve been trying to get in touch with Marina about some money she’s allegedly to receive as someone’s beneficiary. Hmm, promises of unexpected riches — definitely a big red flag.
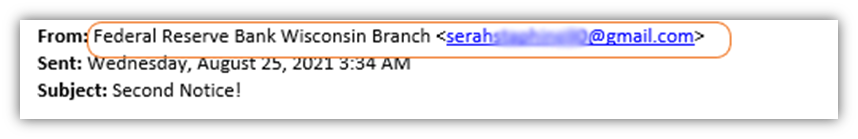
In the following screenshot, we can see that the message is sent from an email address that’s clearly not part of the Federal Reserve Bank of Wisconsin. (It’s a Gmail address belonging to someone whose name is Serah.) That’s red flag number two.
The contents of the unsolicited message are written to seem urgent, saying she’s the beneficiary of millions of dollars since an unnamed customer died and left her the money. That’s red flag number three.
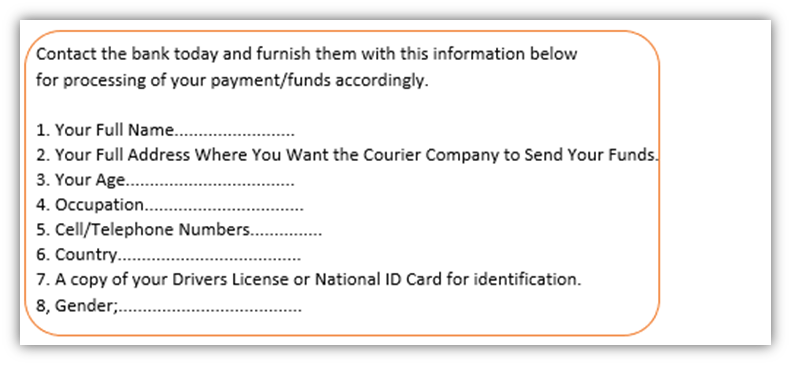
Next, the email states that they require her to share highly personal information — Marina’s name, age, contact information, and even a copy of her driver’s license — in order for their institution to process the funds. BIG red flag number four.
Finally, the email directs Marina to respond to a completely separate email address than the one that the email was sent from originally. The message even goes as far as to try to create a phony air of security — it states that if she receives a message from anyone else regarding the matter, the messages should be “nullified and avoided immediately for security reasons.” Red flag number five.
On the Seventh Day of Phish-mas, a Hacker Sent to Me… 7 Requests for Payment
Everyone loves a little extra green in their pockets during the holidays, and cybercriminals are no different. They want to scam people and companies out of as much money as they can while expending the least amount of energy possible. In some cases, this involves tricking people into making wire transfers for fraudulent transactions — in others, cybercriminals get users to purchase and provide the codes for pre-paid gift cards or get them to make other phony purchases on their behalf.
Some requests for payment come in the form of fake invoices and account statements. Here’s one such example that I received back in 2020:
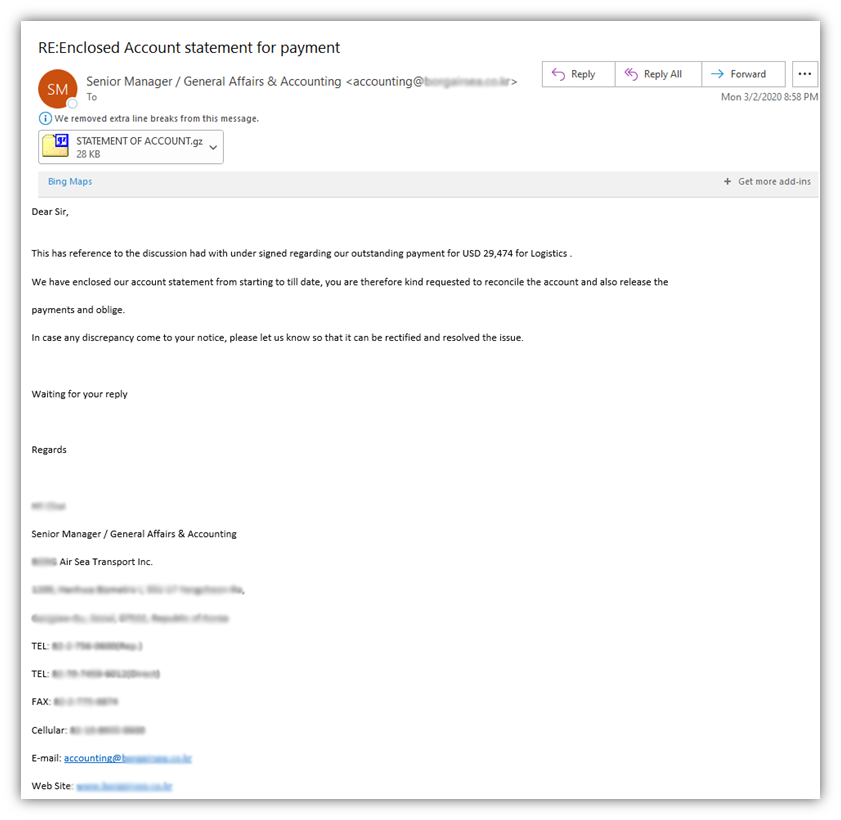
… Yeah, I’m pretty sure we don’t have any “logistics” services rendered for us from a cargo-related corporation considering that we sell digital certificates. And, even if we did, I certainly wouldn’t be the person handling paying said invoices!
Needless to say, there are some other obvious giveaways that this is a phishing email — an unsolicited message containing a suspicious attachment, poor grammar, and a request for immediate payment. But at least with this email, they were consistent in representing themselves as this specific sea and air transport corporation. (They even bothered to send it from an email address that actually has “accounting” in it!)
However, I’m not falling for this obvious ruse, and neither should you. This is where flexing your critical thinking skills comes into play.
Let’s take a look at another email that one of my colleagues received — this one falls within the “phony purchases” category we mentioned earlier:
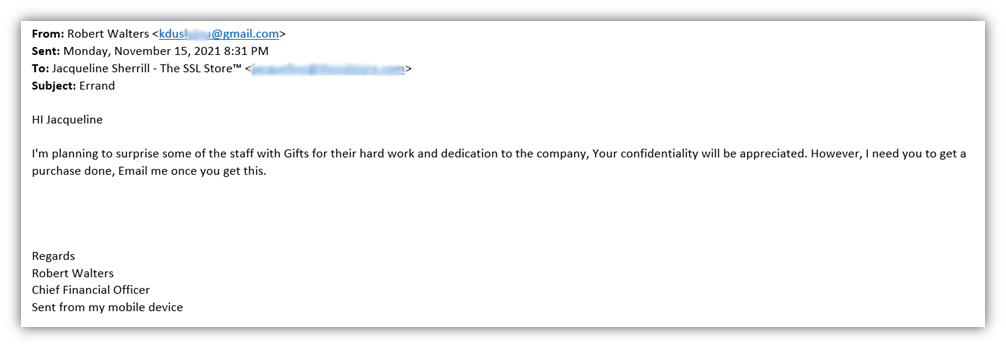
As you probably guessed, this guy definitely isn’t Santa’s little helper. This scam email is just one more additional message on our ever-growing list of phishing examples.
- The SSL Store is a small business — everybody pretty much knows everyone else here.
- Since all employees receive cyber awareness training, they are aware of phishing scams like this where someone tried to pose as the CEO or another company executive. (More on that momentarily.)
- My colleague, Jacqueline, was able to quickly look at this email and know that it wasn’t sent by Robert Walters.
- She also knew that there was no reason why someone in that position would have any expectation of her making purchases on behalf of the company.
Nice try, poser. But none of us is taking the bait.
On the Eighth Day of Phish-mas, a Hacker Sent to Me… 8 Emails From Your Boss
This next topic of our list of phishing examples follows the last perfectly. It’s quite common for phishing emails to be sent by someone impersonating an authority figure within your organization. This could be a middle-level manager, a c-suite executive, or even a board member. Regardless of which rank they try to pull, you must know what to look out for to avoid getting scammed.
In the time since I started working here at The SSL Store, I’ve received a multitude of phishing emails from schmucks who’ve pretended to be everyone from the company’s founder, CEO, or vice presidents. (By the way, this is known as CEO fraud.) But what do these types of messages look like? Well, the truth is that these messages can actually span several of the categories we cover in this article.
Let’s quickly explore a phishing example that we haven’t shared yet on Hashed Out:
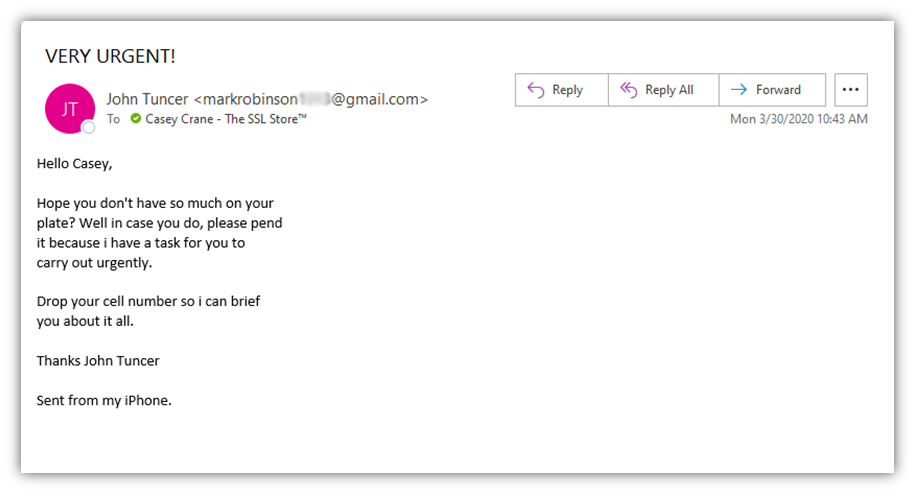
The first thing to notice here is the email address. It’s coming from an account with the name “markrobinson,” which is clearly not his name, and it’s also coming from a Gmail account. Gmail accounts are free, easy, and fast to create — three qualities that every cybercriminal finds very appealing.
Second, the message is written with highly urgent language. (Look at the subject line.) Remember what we talked about earlier? It’s all about instigating an emotional reaction from the email recipient so they’ll do what’s asked without pausing to ask if they should.
The last thing to note is that the imposter is trying to direct me to provide my personal cell phone to him. This is a big no-no because it can be used for a litany of purposes, including:
- Sending me malicious links via SMS text message,
- Spoofing my legitimate phone number to try to phish one of my colleagues or family members, and
- SIM swapping attacks that involve the attacker using personal information they collect about me to try to gain access to my phone number through my cell phone provider.
On the Ninth Day of Phish-mas, a Hacker Sent to Me… 9 HR & Payroll Email Scams
Poor Nellie. As you can imagine, our ever-jolly office manager receives a lot of these phishing messages. Payroll fraud and other related phishing scams typically target employees in accounting, payroll and human resources. As such, it’s a good thing she knows what to look out for when it comes to recognizing phishing email scams.
Nellie’s also savvy enough to know that if she receives unsolicited email requests regarding changes to any employees’ payroll information, she should reach out to the employee directly using other channels (such as by making a phone call or walking down to hall to speak to the person directly). She knows better than to respond to the suspected phishing email!
But what does a payroll diversion scam email actually look like? Let’s take a look at an old example email she received a while ago from someone pretending to be our vice president of sales:
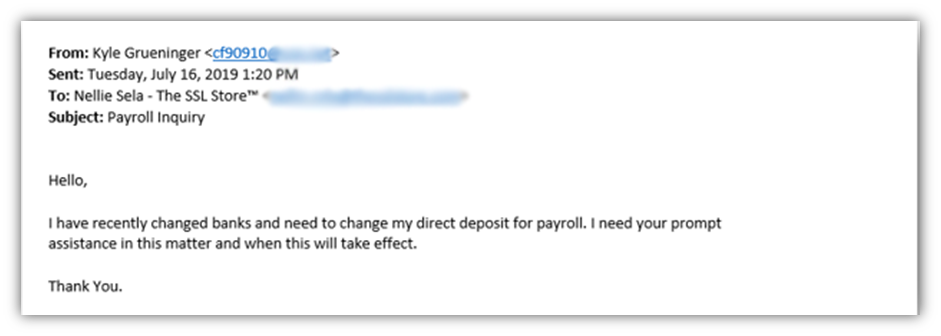
This type of email is designed to trick her into changing Kyle’s direct deposit information to a phony account controlled by the attacker. However, as you can see from the email address that starts with “cf90910,” that’s definitely not an email address for one of our vice presidents.
Thankfully, Nellie’s aware of these types of tricks and simply forwarded it to me as an example of the types of HR payroll email phishing examples people should look out for. If she didn’t know what to look out for, it’s likely that she could have made the mistake of responding to the email directly. This would have resulted in a lot of problems for Kyle, Nellie, and our company as a whole.
When you receive a questionable email, it’s always best to reach out to that person directly through other channels to confirm the message’s legitimacy.
Of course, another favorite of mine was this email, which attempts to catch me off guard and scare me into clicking on the embedded link:
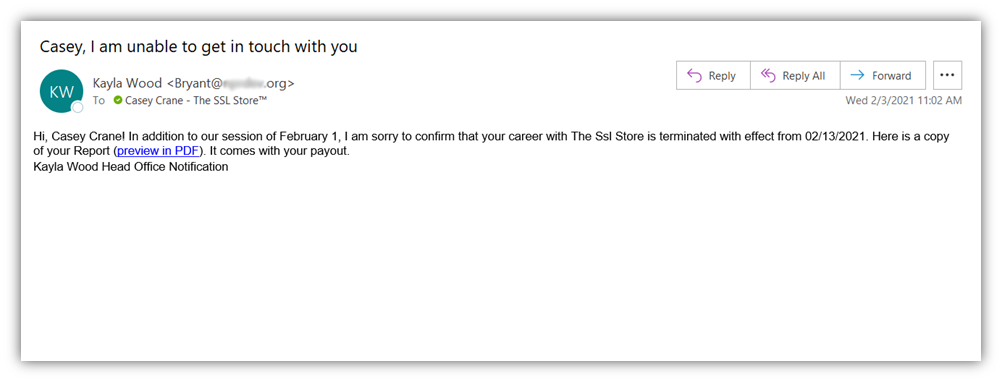
Okay, there are so many things wrong here:
- The email comes from an unknown name that doesn’t match the sender’s email address information.
- No self-respecting company would fire an employee this way. The SSL Store definitely wouldn’t do it this way!
- It’s full of poorly written text that doesn’t even write the name of our company correctly and is signed “Kayla Wood Head Office Notification.” … Say, what?
- The embedded link goes to a bit.ly URL that, when expanded out, would take me to an equally fake website.
On the 10th Day of Phish-mas, a Hacker Sent to Me… 10 Romance Scam Outreaches
It’s hard to be in a holly-jolly mood knowing that romance scams are affecting people around the world at this very moment. While these scams aren’t new, they’re among the worst (in my book) because they target vulnerable individuals in the most personal ways possible to exploit their emotions and steal their savings.
The FBI’s Internet Crime Complaint Center (IC3) reports that more than $600 million was reported lost by 23,751 victims of confidence fraud/romance scams in 2020 alone. Now, keep in mind that this estimate only includes reported incidents and doesn’t include the, undoubtedly, countless others that went unreported because the victims were unaware that they were being scammed or were too embarrassed to report the crimes.
Romance scams vary but often generally involve the following:
- A cybercriminal targets someone who’s recently single, widowed, or is otherwise lonely. The idea here is that because they may be emotionally vulnerable, they’re easier to exploit. These phishing examples typically come via emails, text messages, and social media outreaches.
- A bad guy pretends to be a prospective romantic interest. Here, the attacker might pose as a prospective suitor to win over the victim’s trust and to isolate them from their legitimate friends and family. They also may pretend to have incriminating or private information about the victim that they can use as blackmail.
- An attacker pretends to be a friend or relative of the victim. While posing as the relative, the attacker will reach out (typically via email, phone call or text message) to say that they’re in some type of emergency situation and need immediate financial help from the victim.
So, what does one of these types of phishing examples look like? Here’s an example from ScamWatch at the Australia Competition & Consumer Commission (ACCC):
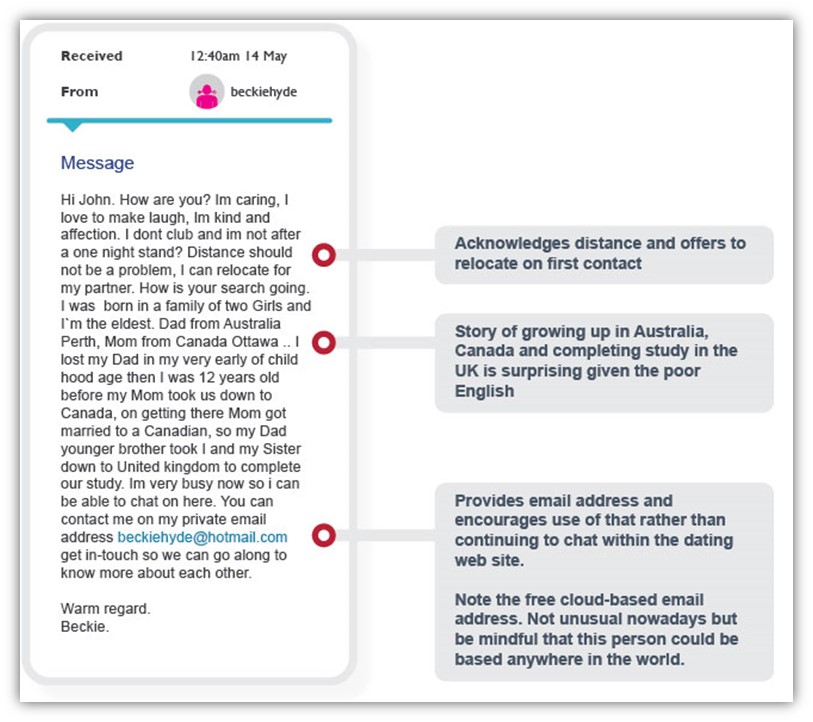
Now, imagine if someone used one of these scams to get one of your employees to send them company money or to provide access to secure company resources. All hell will break loose, and your organization and customers will be the ones left paying the price as a result.
Needless to say, someone definitely should be getting far worse than coal in their stocking for sending these types of phishing messages…
On the 11th Day of Phish-mas, a Hacker Sent to Me… 11 Extortion Emails
For cybercriminals, nothing brings out the holiday spirit and festive cheer quite like extortion. Many Bitcoin phishing extortion scams, for example, involve cybercriminals demanding crypto payments in exchange for not sending allegedly incriminating or embarrassing information, photos or video footage of you to your employer, friends, and family members.
Other extortion scams involve a bad guy demanding your employee do something bad as a way to get them from spilling the bad information. One example would be targeting a cell phone provider employee to get them to carry out SIM swapping by porting legitimate customers’ phone numbers to devices controlled by the cybercriminal.
But how do they achieve this? A few examples of cyber extortion scams include:
- Saying they’ve exploited some kind of vulnerability that gave them access to your device browser history, camera, and/or microphone.
- Claiming they have video recording(s) of you doing inappropriate things (such as visiting child pornographic websites).
- Saying they have other allegedly incriminating about you that you can’t risk becoming known publicly.
Now, mind you, these scams are typically hogwash because they’re targeting a bunch of users at once with the hope that at least one of them is secretly being naughty and doesn’t want to get caught. However, all it takes is one employee being afraid and not wanting to risk their secret getting out to lead to your organization or customers becoming compromised.
Here’s one such example that one of my former colleagues received a while ago:
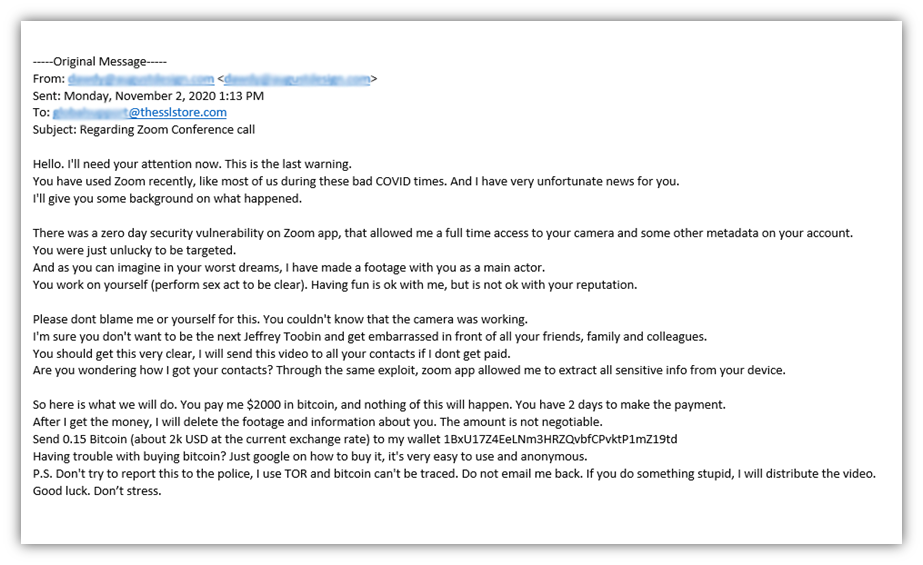
In this case, the attacker claims to have exploited the Zoom zero day vulnerability that was all over the news around that time. They claim to have used that exploit to gain access to your Zoom app, where they could record you doing naughty things — and if you hand over $2,000 in Bitcoin, they’re going to share the footage with everyone you know.
… Ho, ho, ho, indeed.
On the 12th Day of Phish-mas, a Hacker Sent to Me… 12 Requests to Access Resources
Alright, it’s time to wrap up this list of not-so-merry phishing examples. This type of phishing scam is one of the most brazen. It involves an attacker trying to trick or manipulate you into giving them direct access to your device, secure resources, or organization’s IT systems.
- If you give them access to secure resources (such as databases, web apps, admin portals and drives), then they can use that access to alter, steal or delete your most sensitive data.
- If they gain access to your device, they can then use that access as a foothold on your organization’s network.
- Lastly, if they gain access to your network, then they can use it to search for misconfigurations and other vulnerabilities they can exploit.
So, what do these phony requests for access look like? Here’s a quick example:
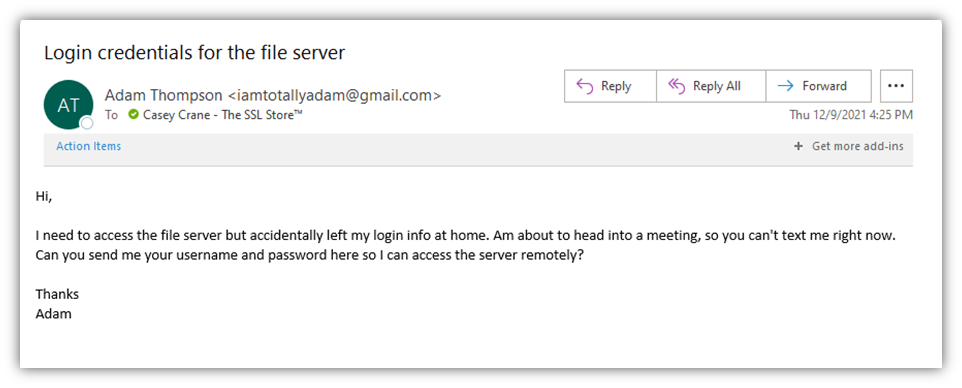
(Note: The screenshot above and below are not legitimate phishing emails. I created both specific phishing example images for the purpose of this educational article).
At a quick glance, it looks like it could be an email from my director. However, the email address clearly gives it away because:
- It’s not his work email address (which wouldn’t be a Gmail account), and
- He’d never ask me for this type of sensitive information because he knows it’s a security risk.
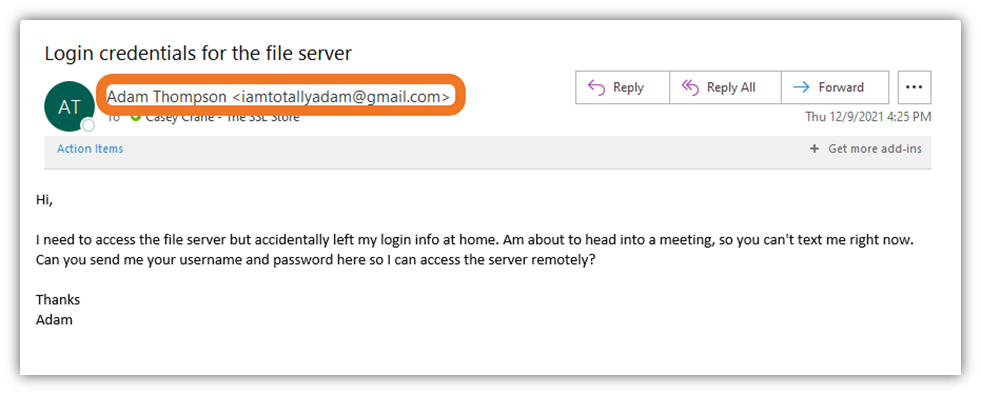
In this type of situation, I know the best thing to do would be to reach out to him directly through another trusted method (regardless of the email statement saying not to call him). Adam and I both know that I’d 100% need to confirm this type of request directly and would never simply hand over such secret information in response to such an unexpected (and urgent) email request.
Every employee helps to form your company’s strongest or weakest line of defense — the difference often boils down to whether they have the cyber security awareness to recognize and avoid phishing scams and other cyber threats.
Final Thoughts on the 12 Days of Phish-Mas Phishing Examples
We hope you’ve found this article enlightening and useful in terms of learning what phishing scams look like, so you know what to avoid in the future.
Data security and online safety rely on people being aware of different types of threats and scam tactics. If you don’t know what you don’t know, how can you help keep yourself, your company, or your customers and data safe from cybercriminals? Simply put, you can’t. This is why it’s essential to invest the time, energy, and focus in educating yourself and your employees so they know how to recognize and respond to phishing attempts.
Furthermore, have the right tools and resources in place to help make the process easier. For example, use email signing certificates within your organization to ensure that your team is sending digitally signed, verifiable emails. Using these certificates means that the email sender has to have access to that user’s device and email client to send the message.
Here are some additional resources that you may find useful:
- An email header analyzer tool
- A URL and/or File Analyzer tool
- Our article on 5 Ways to Determine If a Website Is Fake, Fraudulent or a Scam
- FTC’s website on How to Recognize and Avoid Phishing Scams
- Google and JigSaw’s Phishing Quiz
*** This is a Security Bloggers Network syndicated blog from Hashed Out by The SSL Store™ authored by Casey Crane. Read the original post at: https://www.thesslstore.com/blog/12-days-of-phish-mas-a-festive-look-at-phishing-examples/





