Home » Security Bloggers Network » How US Federal Government Proposals Promote Zero Trust Network Access
How US Federal Government Proposals Promote Zero Trust Network Access

As part of the mandates from President Joe Biden’s May 12th Executive Order on Improving the Nation’s Cybersecurity the Office of Management and Budget (OMB) is giving agencies until the end of October to assess how well they log cybersecurity incident data against a new maturity model. Agencies have just 60 days to identify “critical software” and 1 year to implement enhanced security measures.
The Executive Order (EO) follows the rise of cyberattacks such as the SolarWinds Orion security breach and Colonial Pipeline ransomware attack. It requires agencies to improve their investigative and remediation capabilities around logging, log retention, and log management, focusing on centralized access and visibility for the highest-level enterprise security operations center (SOC) of each agency.
The executive memo from the OMB outlines four maturity levels starting with event logging 0 (EL0) as least mature to EL3 as having a mature program that agencies should assess themselves against. (See table below). After the 60-day review, agencies then have 18 months to reach EL2 and 24 months to reach EL3.
Summary of Event Logging Tiers
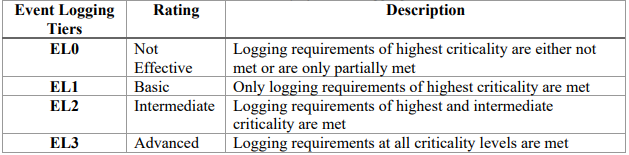
Ensuring visibility before, during, and after a cybersecurity incident is critical to defending against cyberattacks. Increasingly, however, detection, investigation, and remediation of cyber threats requires recognition that users today work in a hybrid environment and data is increasingly moving from on-premises servers to cloud services.
The government’s recent requests for public comment reflect a growing recognition that zero trust, and in particular ZTNA (Zero Trust Network Access), is foundational to cybersecurity – an approach that abandons perimeter and instead trusts no one, restricts access on a least-privilege model, and continuously monitors all connections and data for anomalies.
That’s where Cloud Access Security Brokers (CASBs) are immensely useful. Using the principle of zero trust they provide the necessary visibility and control of cloud data that can help detect intrusions, mitigate those in progress, and help determine the extent of an incident after the fact. CASBs provide IT teams with detailed logs with information on all cloud app transactions, including downloads, uploads, logins, and more. They can track and scan application-specific behaviors like contact database downloads in cloud apps and external file-sharing. They generate logs in human-readable form, allow for search and filter functionality, and integrate seamlessly with SIEMs and other security operations tools and workflows.
To learn how Bitglass is helping government agencies move toward a zero trust architecture, while avoiding the need to support VPN infrastructures, download our brief on Bitglass Zero Trust Network Access for Government.
*** This is a Security Bloggers Network syndicated blog from Bitglass Blog authored by Jonathan Andresen. Read the original post at: https://www.bitglass.com/blog/how-us-federal-government-proposals-promote-zero-trust-network-access






