DEF CON 29: SEVillage Recap
The SEVillage was established back in 2010 at DEF CON 18. It has been the official home for all things social engineering for 12 years straight. Our flagship event, the SECTF, has been joined by other events over the years, such as the SECTF4Kids, and SECTF4Teens. SEVillage is also the home for all social engineering speeches at DEF CON.
Over the last two years, we have all adapted to the demands of virtual work, meetings, and yes, even conferences. We truly miss seeing our SEVillage family in person. Fortunately, we can experience SEVillage from the comfort of our own homes! While seeing your faces in 2D isn’t quite the same, we want to thank each of you for your support. This year’s village was one of the most unique ones yet. Until the time we can all be safely together again, let’s look back at DEF CON 29: the SEVillage recap.

Friday: SECTF4Kids and SEVillage Speakers
Friday launched the Social Engineering Capture the Flag 4 Kids (SECTF4Kids). Ryan MacDougall and Colin Hadnagy hosted the annual competition this year. They created a virtual world within Minecraft, complete with challenges that all could enjoy. In a world inspired by Wreck It Ralph, participants pictured themselves trapped inside of an arcade game after being sucked into a power strip. They had to complete social-engineering-themed puzzles to gather materials that would help them build a signal for help. What was their objective? First, to obtain enough materials. Second, to climb the radio tower as high as possible. And finally, to project an SOS signal to the arcade owner. The team to make the brightest signal would win.
We had 11 kids participate in the competition this year, ages spanning from 7-12 years old. As always, these kids went above and beyond our expectations and handled every challenge we threw at them. The SECTF4Kids is a great way to get kids involved in the community in an entertaining and challenging way. Over the years, some of these children have even given us ideas for future kids CTFs that we implemented! We value the opportunity to be a part of their journey and are excited to see them continue to grow and learn. We want to extend a huge thank you to one such young person. She dedicated hours of her time to help us build and create this virtual competition! SEVillage couldn’t have done it without you, Hydra!

Christina Lekati
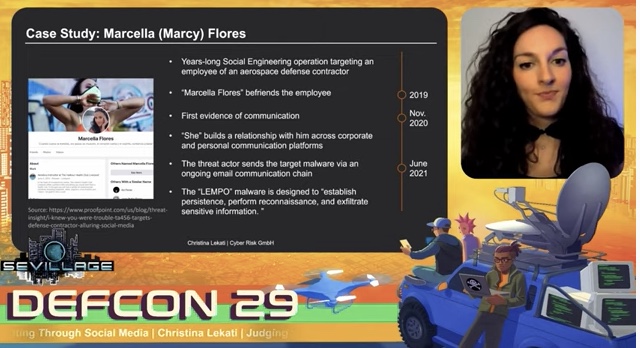
The first of our amazing speakers was Christina Lekati. Christina is a psychologist, a social engineer and an open-source intelligence analyst. She specializes in behavioral analysis and in intelligence collection and analysis through open-source and human intelligence. Her speech was titled “Judging by the Cover: Profiling & Targeting Through Social Media.” In this presentation, she dissected multiple case studies, broke down social engineering patterns, and helped her audience understand how to apply various profiling techniques to various social media profiles.
Ryan MacDougall
Social-Engineer, LLC’s very own Ryan MacDougall was our next presenter. Ryan is the Chief Operating Officer and Open-Source Intelligence trainer for Social-Engineer, LLC. In addition, he runs operations during penetration tests and exercises with clients, as well as managing client relationships. His topic was “SE Team vs. Red Team.” He explained the difference between the two by telling his experience of a standout SE Team engagement. A direct quote from that story: “It was such a surreal experience, to feel like you’re going to die in that moment.” Spoiler alert: they did not die.
Saturday: SECTF4Teens and SEVillage Speakers
Saturday brought with it another Social Engineering Capture the Flag 4 Teens (SECTF4Teens) hosted by C.G. Consulting Service for the second year in a row. The goal of the event was to retrieve the flags, via open-source intelligence (OSINT) on the targets they were given. We had 3 people, or as we lovingly refer to them, “voluntargets,” who willingly let us use them for the competition. The targets provided us with answers to the flags that the teens would then search the internet for, collecting points along the way.
The SECTF4teens competition gives older kids the chance to practice their social engineering skills. With the virtual format, doing a competition like the OSINT CTF gives them a chance to see what a real engagement looks like and hone skills they can use in a future career. It also highlights how easy it is to find information online. They see the dangers firsthand and see how important it is to keep their personal information safe.
Lisa Forte
Lisa Forte kicked off our Saturday speeches with a bang. She is a social engineering and insider threat expert. Lisa runs cyber crisis simulations for large companies to help them prepare for attacks of all types. She actually started her security career stopping pirates off the coast of Somalia. Her background made her the perfect person to deliver the topic “Using SE to Create Insider Threats and Win all the Things.” She defined the different types of insider threats that exist and how malicious individuals will leverage social engineering tactics to gain footholds in organizations.

John McCombs
We were ecstatic to have Innocent Lives Foundation (ILF) employee John McCombs speak about “The Innocent Lives Foundation: A Beacon of Light in a Dark World.” John’s speech aimed to bring awareness to the ILF and their mission of identifying and bringing child predators to justice. He highlighted why the ILF is needed now more than ever, their stance on vigilantism, and neutrality. To learn how you can help support the ILF in their mission, watch this speech on our YouTube channel or visit their website to get involved.

Chis Hadnagy
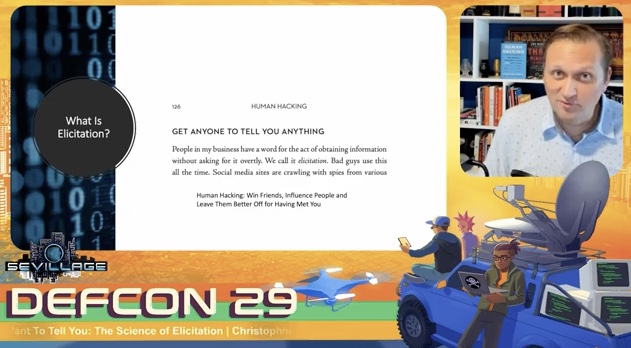
Last but not least, the founder and CEO of Social-Engineer, LLC., Chris Hadnagy wrapped up the day with the presentation “Make Them Want To Tell You: The Science of Elicitation.” Chris brought his 18 years of experience in the information security industry to the fore to define what elicitation is. He explained how social engineers use it, and looked at the science behind it. Chris is an Adjunct Professor of Social Engineering for the University of Arizona’s NSA-designated Center of Academic Excellence in Cyber Operations. He has written 5 books on social engineering and has countless hands-on experiences in the field. This unique skill set made him the perfect speaker to understand and explain these techniques.
What’s Next?
We want to give a huge shout out to not only or speakers and those at the forefront of our CTF’s, but also to everyone who worked behind the scenes to make this year’s SEVillage run so smoothly. A special thank you to everyone who participated and who continue on this journey of education and learning alongside us. If you missed any of the speeches, or would like to hear one a second time, you can find them here on our YouTube channel. If you would like to hear Ryan and Chris speak again (and have the opportunity to learn from them) keep an eye on our SEVillage Twitter account for an exciting announcement coming soon! Until next year!
*** This is a Security Bloggers Network syndicated blog from Security Through Education authored by SEORG. Read the original post at: https://www.social-engineer.org/social-engineering/def-con-29-sevillage-recap/



