Data security is broken: What’s next?
One out of every two on-premises databases globally has at least one vulnerability, finds a new study from Imperva Research Labs spanning 27,000 on-prem databases, based on insights from a proprietary database scanning service introduced by Imperva Innovation five years ago. The question is: why is securing data so challenging?
Key Findings
This research proves that the way data is being secured today simply isn’t working. For years, organizations have prioritized and invested in perimeter and endpoint security tools, assuming the protection of the systems or network around the data would be enough. However, that approach is not working as this is an expansive and global problem. Organizations need to rethink the way they secure data in a way that genuinely protects the data itself.
The research uncovered several notable trends:
Organizations aren’t maintaining regular patching: With nearly half of all databases globally (46%) containing a vulnerability and the average number of Common Vulnerabilities and Exposures (CVEs) per database standing at 26, it’s clear that businesses are ignoring one of the basic tenets of data security which is to patch and update databases as soon and often as possible. We’ve even identified vulnerabilities which have gone unpatched for more than three years — an incredible amount of time considering the sensitivity and value of data. The volume of CVEs present in most databases means that hackers now have dozens of well-known, easily exploitable paths to businesses’ most sensitive data. Indeed, today hackers simply have to search tools like ExploitDB to find proof of concept code that allows them to take advantage of such vulnerabilities.
Severe vulnerabilities are being ignored: More than half of the vulnerabilities present in databases globally are ranked as either ‘High’ or ‘Critical’ severity according to NIST guidelines — vulnerabilities that allow attackers to, amongst other things, steal or manipulate sensitive data, take control or move laterally through the network once the database is compromised. Not only are businesses not investing enough effort into patching, but it seems some databases have just gone unnoticed as we identified CVEs dating back three and four years.
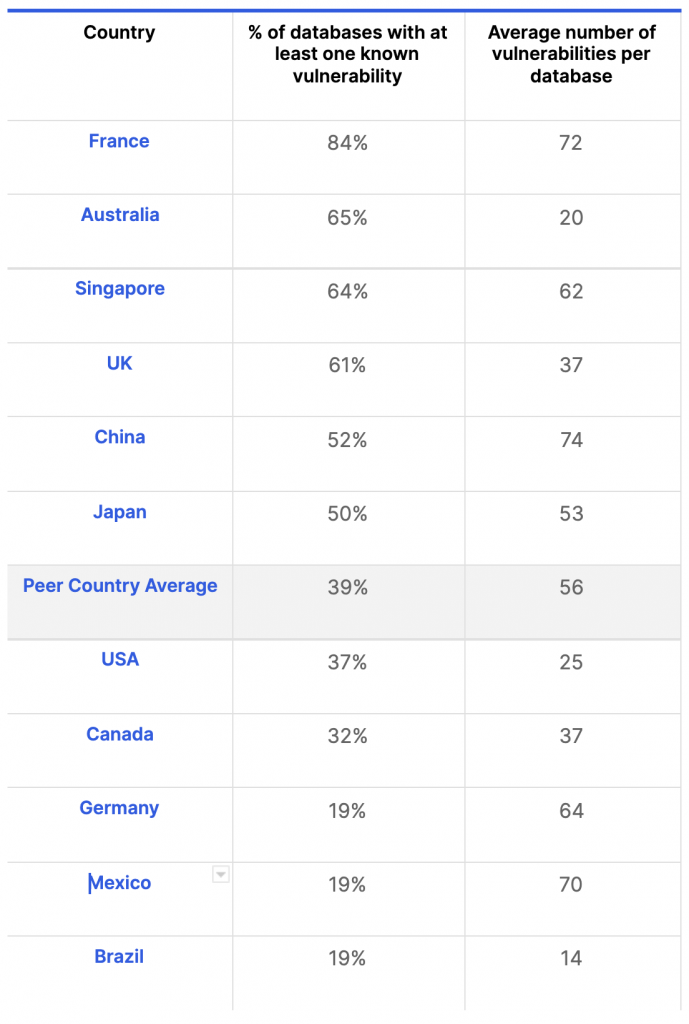
Geography matters: While the global figures are concerning, the regional breakdown is even more worrisome for industrialized countries like France, Singapore and China. The databases in these nations all have vulnerabilities that exceed the global average, both in terms of the percentage of databases which are vulnerable, and the average number of vulnerabilities per database. However, even for countries like Germany which have a relatively low percentage of vulnerable databases (19%), the average number of vulnerabilities is still relatively high. Thus, improvements are still needed.
What steps should be taken?
Get visibility: It’s impossible to protect data unless you have an overview of all the places where data is being stored across the organization, including rogue databases that have been set up outside the purview of security. The complexity of modern business means that data has become more diffuse than ever and therefore it’s essential to automate this discovery process to ensure that nothing has been inadvertently missed. Crucially, this should also involve deploying tools to detect database activity anomalies, coupled with solutions that can prevent vulnerabilities from being exploited.
Prioritise the crown jewels: In an ideal world, security teams would have time to patch every vulnerability in every database as soon as it’s issued. However, given the onslaught of other tasks from across the business and the restrictions on when patches can be issued, this is becoming harder and harder to manage. Therefore, security teams need to make sure they’re prioritising their time correctly, both in terms of mitigating the most serious vulnerabilities, but also in terms of which data is being protected. Having tools that can identify which databases hold sensitive customer data (e.g. credit card numbers or passport numbers) means that security teams can understand where the crown jewels are and secure them accordingly.
Understand the risks of digital transformation: Across all industries, businesses are pressing ahead with digital transformation initiatives and shifting data to the cloud. However, these findings demonstrate that managing on-prem security is already incredibly challenging even before the complexity of securing data in the cloud is considered. While digital transformation is essential to maintain competitiveness, businesses need to develop a clear, cohesive strategy for protecting data, and all paths to it, wherever it resides.
Learn how Imperva’s Database Risk & Compliance solution delivers analytics, protection and response across all data assets – on-premise and in the cloud – giving you the risk visibility needed to prevent data breaches and avoid compliance incidents.
The post Data security is broken: What’s next? appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Elad Erez. Read the original post at: https://www.imperva.com/blog/data-security-is-broken-whats-next/





