Patch Tuesday Update – July 2021
Zero-days galore and lots more…
July 2021 Patch Tuesday contains fixes for 117 vulnerabilities in total, with 9 zero-days amongst them. This is across the Microsoft suite of products, by far the most in a month this year. Products impacted by this latest security update include Microsoft Office, SharePoint, Excel, Microsoft Exchange Server, Windows Defender, Windows Kernel, and Windows SMB.
In terms of risk scoring for these vulnerabilities, 13 are classified as Critical, 1 Moderate, and 103 as Important.
Per Microsoft’s classification, a zero-day vulnerability is one that is publicly disclosed or actively exploited, with no official security updates or patches released. Of the 9 zero-day vulnerabilities included in this July’s Patch Tuesday, 4 are being actively exploited in the wild.
There is one publicly disclosed, and actively exploited vulnerability known as PrintNightmare.
PrintNightmare print spooler flaw (CVE-2021-34527) is among the critical bugs for which Microsoft released an official fix. This flaw is in most versions of Windows that prompted Microsoft to release an out of band patch last week in response to exploit code for the flaw that got accidentally published online.
Besides the print spooler vulnerability, there is one other issue attackers have exploited in the wild, according to Microsoft. CVE-2021-34448 is a memory corruption vulnerability in the Scripting Engine that is triggered when the user opens a specially crafted file, either attached to an email or a compromised website.
There is another critical vulnerability, CVE-2021-34473, in Microsoft Exchange Server. This vulnerability was already patched in Microsoft’s April security update but was mistakenly not disclosed. Users who already installed the April 2021 update are already protected from this vulnerability, though it is worth noting that this issue was part of a series of zero-days in Exchange Server used in a wide-ranging APT attack.
Other zero-days to patch:
CVE-2021-33771 – Windows Kernel Elevation of Privilege Vulnerability
CVE-2021-31979 – Windows Kernel Elevation of Privilege Vulnerability
The other publicly disclosed, but not exploited, zero-day vulnerabilities are:
CVE-2021-34492 – Windows Certificate Spoofing Vulnerability
CVE-2021-34523 – Microsoft Exchange Server Elevation of Privilege Vulnerability
CVE-2021-33779 – Windows ADFS Security Feature Bypass Vulnerability
CVE-2021-33781 – Active Directory Security Feature Bypass Vulnerability
Some of the other interesting vulnerabilities also resolved in this update are:
- CVE-2021-31206: A Microsoft Exchange Server RCE found during Pwn2Own.
- CVE-2021-34494: A Windows DNS Server RCE, albeit restricted to DNS servers only.
- CVE-2021-34458: A Windows Kernel RCE which permits a single root input/output virtualization (SR-IOV) device, assigned to a guest, to potentially tamper with PCIe associates.
A complete list of all the vulnerabilities Microsoft disclosed this month is available on its update page.
How quickly can you resolve the exposure from this set of CVEs?
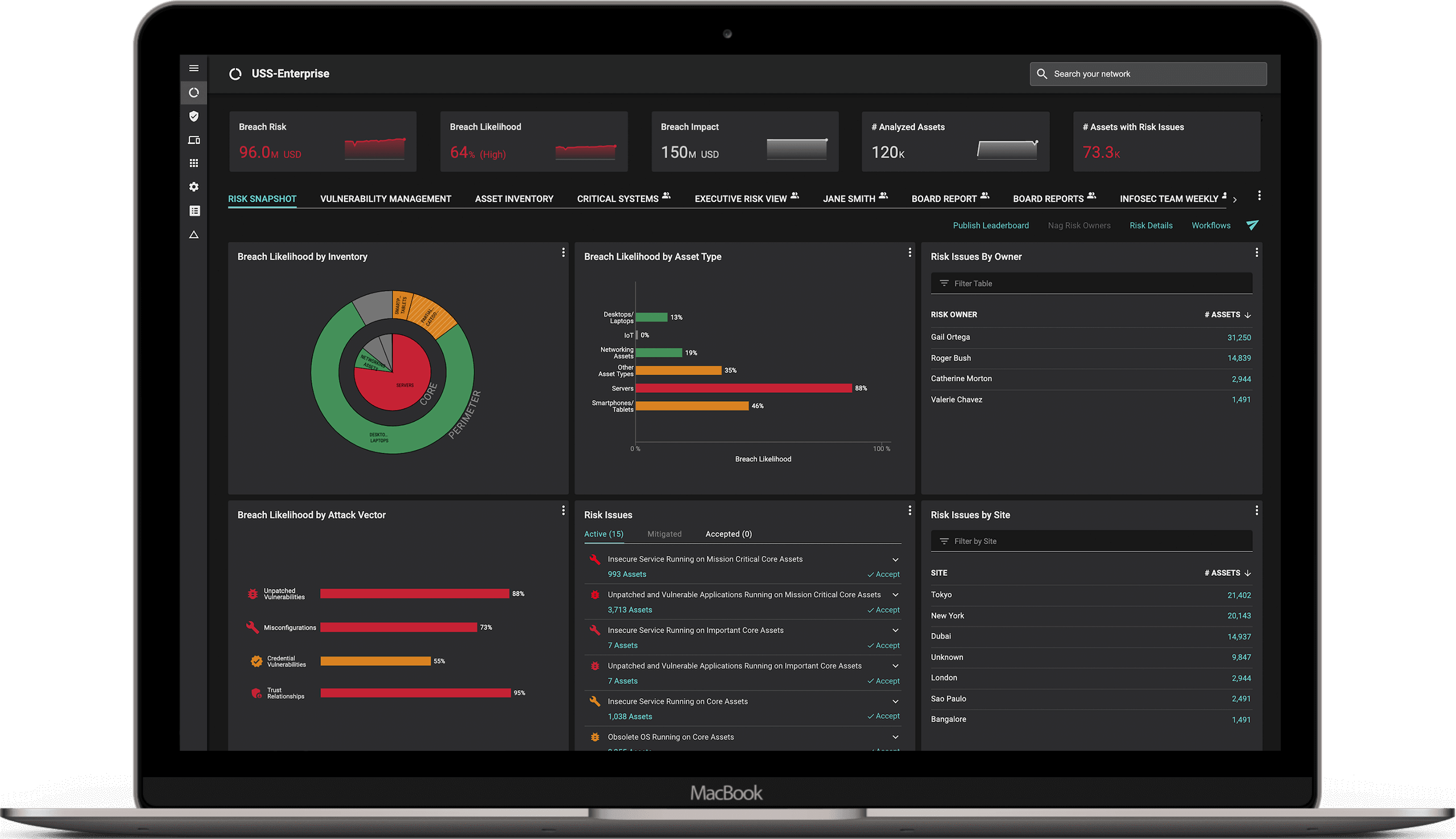
There is an immense need for speed for cyber-defenders to protect against the adversaries. The industry average for Mean Detection Time for CVEs in IT networks is 15 days and for MTTP is > 150 days. Balbix customers can detect < 1 hour and fix within a day or two.
To view the list of affected assets for a specific CVE in your Balbix dashboard, enter the CVE in the Search field and hit Enter. Balbix automatically prioritizes the search results for remediation. You can also use the filtered search functionality to search for the CVE by site, subnet, location, or other distinguishing factors.
If you have additional questions, please contact [email protected].
See Balbix Live
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Ruchika Mishra. Read the original post at: https://www.balbix.com/blog/patch-tuesday-july-2021/




