Intelligent Orchestration and Code Dx: Security superheroes
Building security into DevOps has its challenges. Address them with a modern approach to AppSec using Intelligent Orchestration and Code Dx.
As a kid, I was fascinated by superheroes like Spider-Man and Superman, and now as an adult I enjoy watching Wonder Woman. There is something about these movies—all the superheroes are unseen and come to the rescue at the right time, and once they have helped, they just disappear without even taking any credit. It made me wonder: why can’t application security be invisible to an organization and especially to developers? Why should developers care what tools we run, how and where we run them, or how they’re configured?
Developers need a prioritized set of security test results and guidance on how to fix them. Synopsys Intelligent Orchestration, along with Code Dx, provide just that. Let’s get started and dig deep.
Application security challenges
Organizations in all industries are adopting DevOps practices and automation tools as part of their software development life cycle (SDLC). At the same time, they’re placing increased importance on application security. There are numerous security activities (automated and manual) that discover software security defects—bugs and flaws—such as static application security testing (SAST), dynamic application security testing (DAST), software composition analysis (SCA), manual penetration testing, and many more.
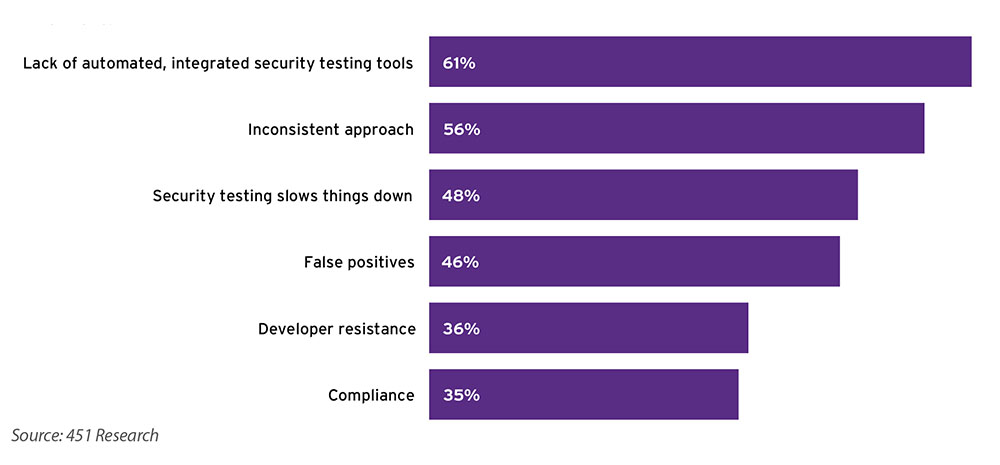
Organizations have been reporting challenges related to security tools for years. The “DevSecOps Realities and Opportunities” report, based on research conducted by 451 Research (commissioned by Synopsys), identified some of the biggest challenges to DevSecOps. The results are shown in Figure 1, below.
Figure 1: The biggest challenges to DevSecOps, according to the “DevSecOps Realities and Opportunities” report
Read more about these challenges in a blog post I wrote.
Strengths of Intelligent Orchestration and Code Dx
Intelligent Orchestration helps address these challenges. It provides organizations with the ability to:
- Abstract and isolate application security testing tools away from the core development pipeline
- Provide a simple API and/or connector to minimize the risk and disruption of the integration
- Run tests without slowing down the pipeline
- Reduce the burden on developers by automating as much as possible and only surfacing the most important issues back to them for remediation
- Ensure that the right tests and analysis are performed at the right time, based on policies, risk profiles, and changes to the code
- Give teams the flexibility to adapt the solution to their specific development workflows and toolchains
Code Dx by Synopsys works with Intelligent Orchestration to give organizations the ability to:
- Execute tests and automatically run AppSec tools
- Correlate results from multiple tools, combining security issues found by 75+ tools
- Prioritize security issues, filtering out noise using machine learning
- Track remediation
- Centralize risk visibility
When you use Intelligent Orchestration and Code Dx together, you truly have a security superhero that is a game changer.
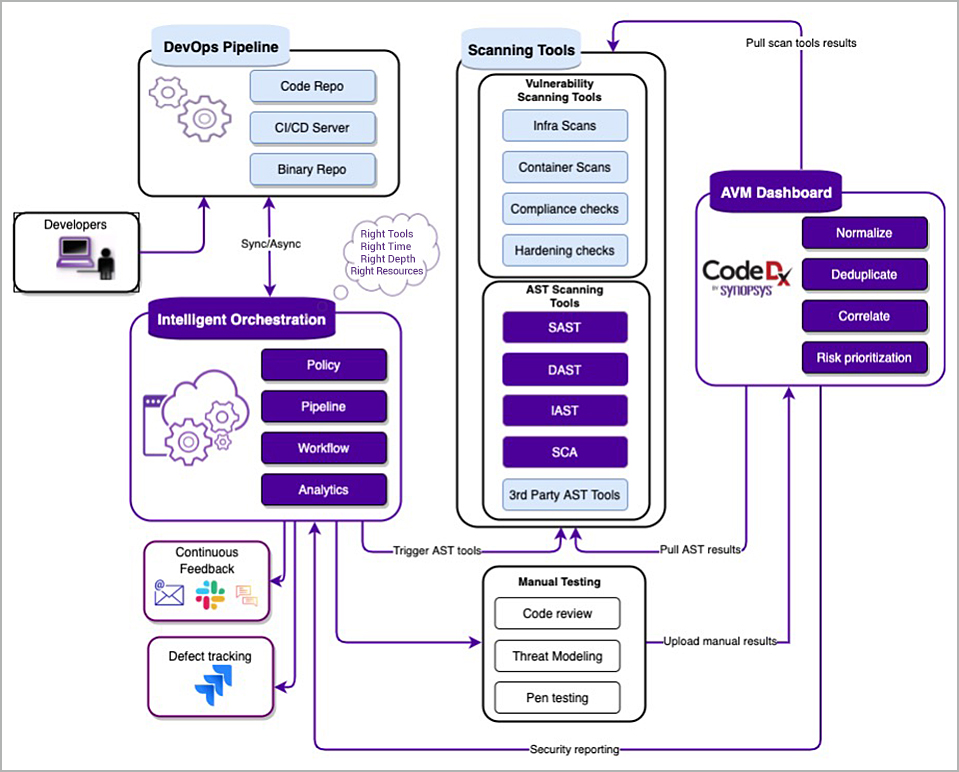
The Intelligent Orchestration and Code Dx integration
Figure 2: High-level architecture diagram of the Intelligent Orchestration and Code Dx integration
Let’s look through the steps shown in Figure 2, above:
- Developers check-in or merge their code to their dedicated branch.
- Their DevOps pipeline runs based on the deployment model chosen. The Intelligent Orchestration pipeline runs a parallel security pipeline.
- Intelligent Orchestration examines application attributes like accessibility, business criticality, data classification, code change significance, and open vulnerabilities and calculates a score that indicates what automated tools to run and what manual activities should happen.
- The appropriate tools and analysis are run, and the results are shared with the development teams.
- Intelligent Orchestration can also trigger manual testing based on compliance needs.
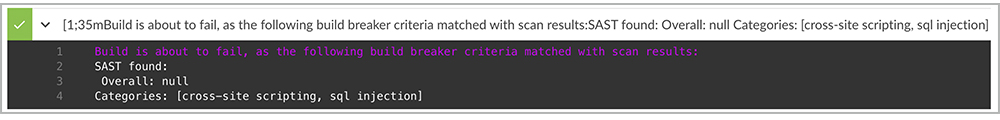
- Intelligent Orchestration sends Slack or email notifications (as determined by preconfigured settings) to the developers, so they are aware of any critical SQL injection issues found by a SAST tool, or a critical cross-site scripting issue found by a DAST tool.
- If defect-tracking is enabled, Intelligent Orchestration can push the defects that the development team has specified as important into a defect-tracking system, like Jira.
- The results from all these automated tools are pulled by Code Dx, and then correlated and prioritized.
- Intelligent Orchestration gets the consolidated, correlated, and prioritized results at the end of the pipeline. Based on an organization’s policy, Code Dx can break the build, pause the build, or wait for a signoff authority to approve the build.
Intelligent Orchestration and Code Dx work together to address AppSec challenges
Now that you have a basic idea of how Intelligent Orchestration and Code Dx work together, let’s go through each of the challenges and see how these security superheroes can work together and help an organization.
Lack of automated, integrated security testing tools
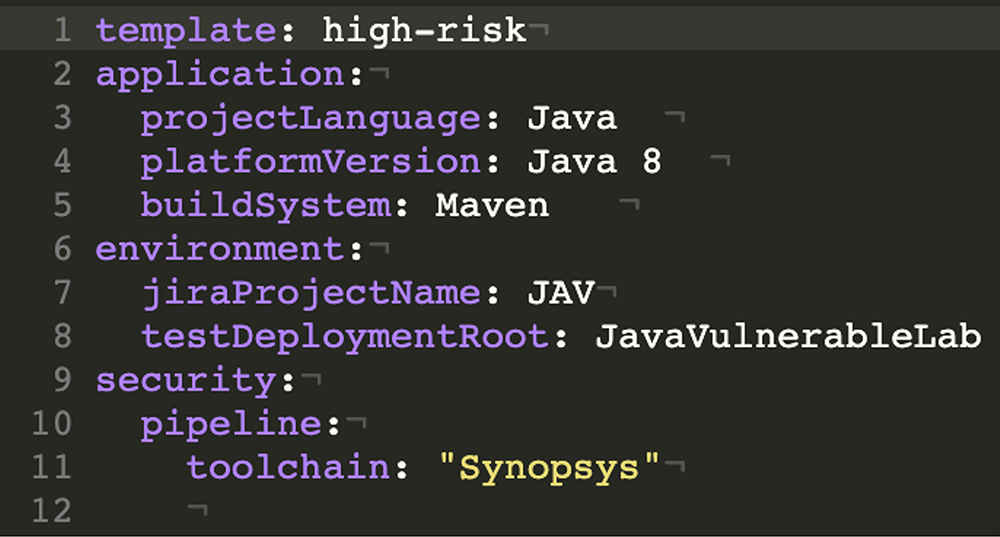
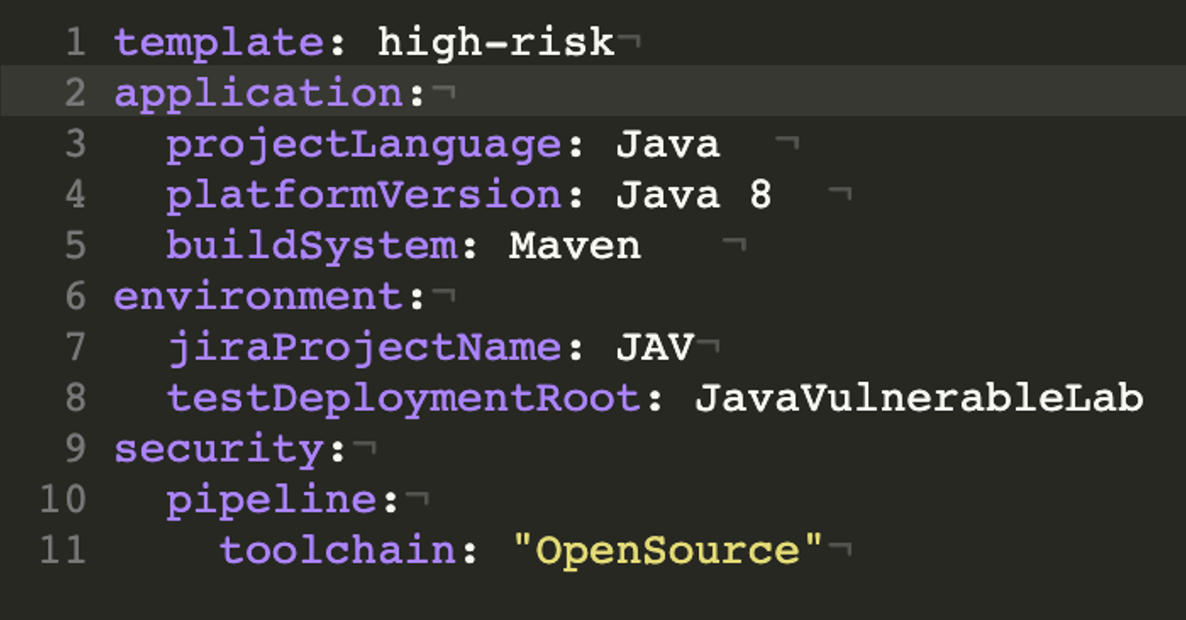
Intelligent Orchestration completely abstracts how security tools are integrated and configured to run scans. Organizations can configure application-specific details that pipelines use to run SAST, SCA, or any AST or vulnerability scanning tools underneath. Intelligent Orchestration can seamlessly run Synopsys tools, open source tools, or commercial tools, as shown in Figures 3 and 4.
Figure 3: An example of Synopsys tools used in the Intelligent Orchestration pipeline
Figure 4: An example of open source tools used in the Intelligent Orchestration pipeline
And when it’s time to replace a tool or integrate a new tool, the changes required are minimal and have little or no impact on your developer pipeline.
The only thing needed to switch from one set of tools to another is a minor change within the Intelligent Orchestration manifest file, as shown in Figure 5.
Figure 5: Intelligent Orchestration manifest file showing the minor change in toolchain using Synopsys tools
Figure 6: Intelligent Orchestration manifest file showing the minor change in toolchain using open source tools
Code Dx is now able to consume all the results from all automated scans that run as part of the Intelligent Orchestration pipelines, as shown in Figure 7.
Figure 7: An example of Code Dx consuming all the results from Synopsys tools and open source tools
Inconsistent approach
Intelligent Orchestration streamlines vulnerability remediation by standardizing, filtering, and prioritizing security analysis findings. It then delivers them directly to the developers within their existing development and bug-tracking tools, so they can address security defects without disrupting their normal workflows.
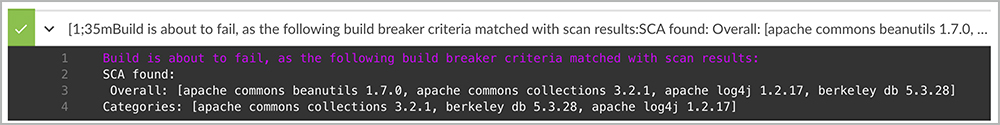
Based on criteria set for notifying the teams when specific issues are found (as shown in Figures 8 and 9), the Intelligent Orchestration pipeline can break or pause the builds, send notifications, or even create defect-tracking tickets.
Figure 8: An example demonstrating SCA findings
Figure 9: An example demonstrating SAST findings
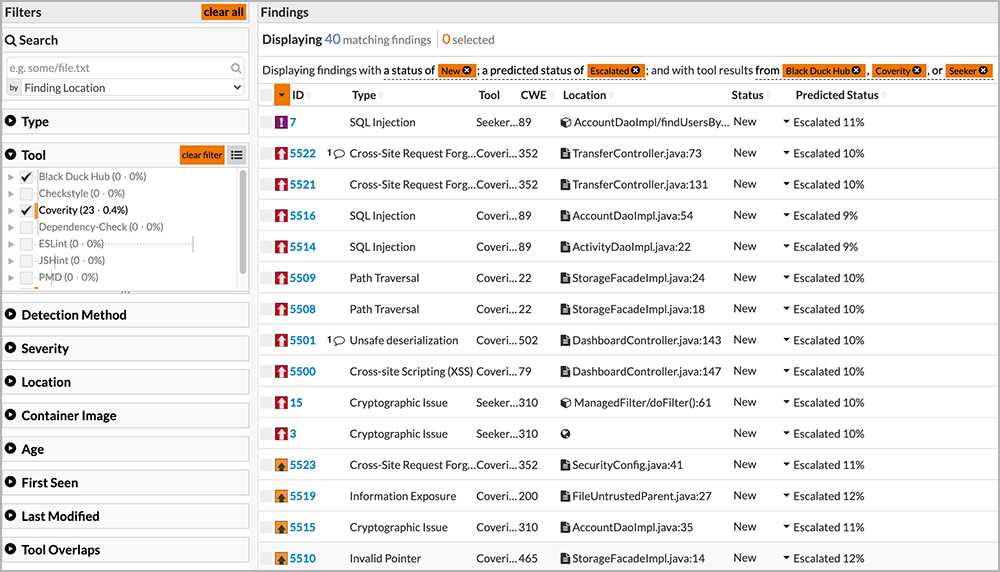
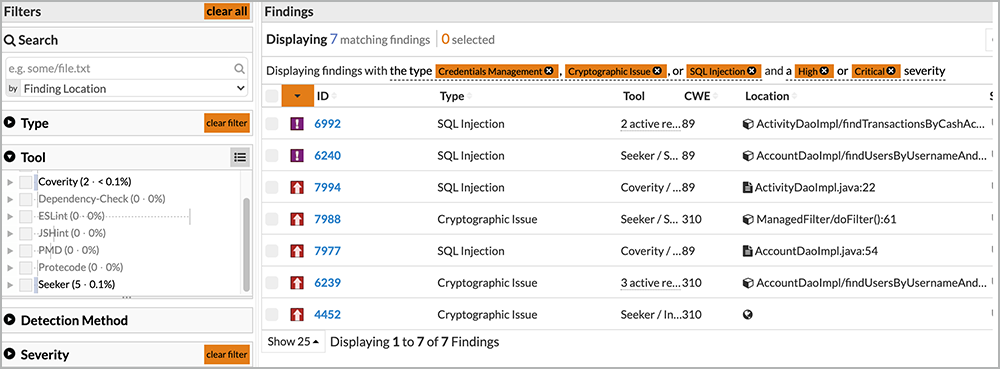
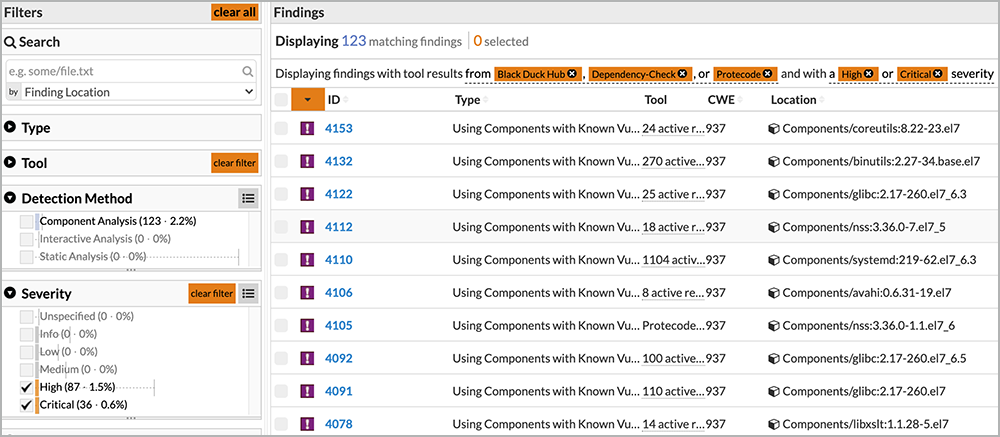
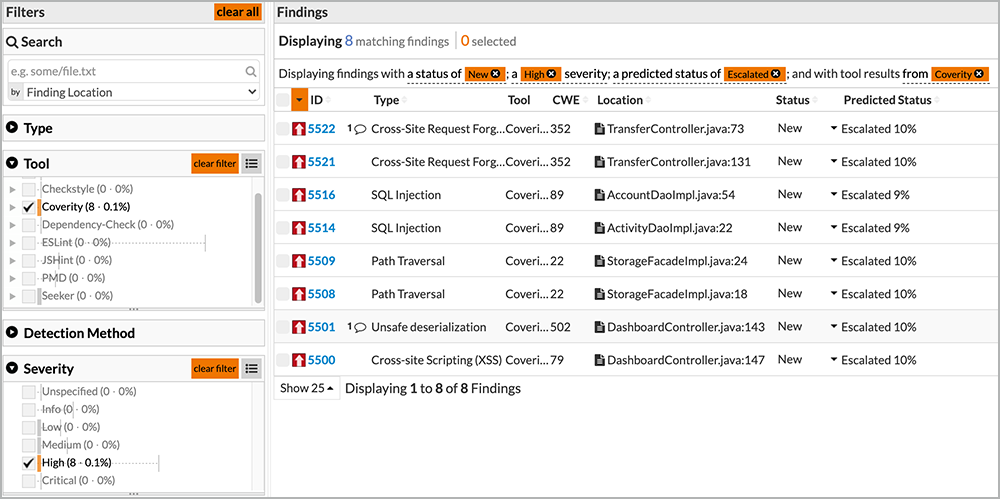
Code Dx also allows users to query for specific vulnerabilities, as shown in Figures 10 and 11. And through its extensive APIs and integration with the Intelligent Orchestration pipeline, it can break or pause the build, send notifications, or create defect-tracking tickets.
Figure 10: An example of Code Dx filtering results based on findings found by two tools: Coverity and Seeker
Figure 11: An example of Code Dx drilling down to detection method, type of tool, and severity
Security testing slows things down
Intelligent Orchestration is a dynamic security pipeline that isolates security testing from the developer toolchain with a dedicated CI pipeline that integrates easily with your development pipelines. It triggers the appropriate automated testing activities with the right tools, at the right time, with the right depth, and notifies the right resources.
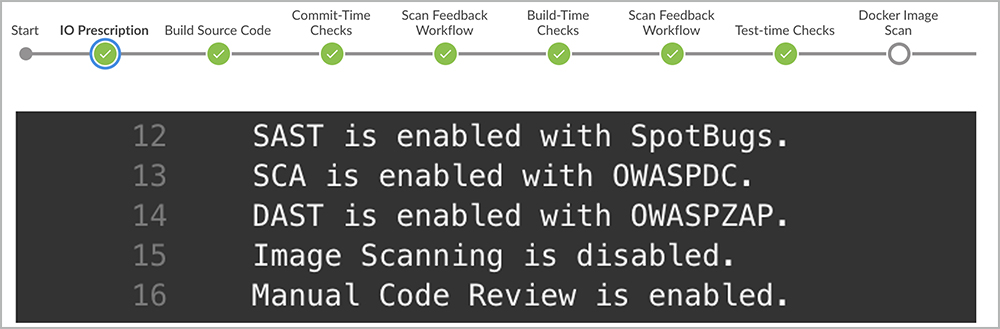
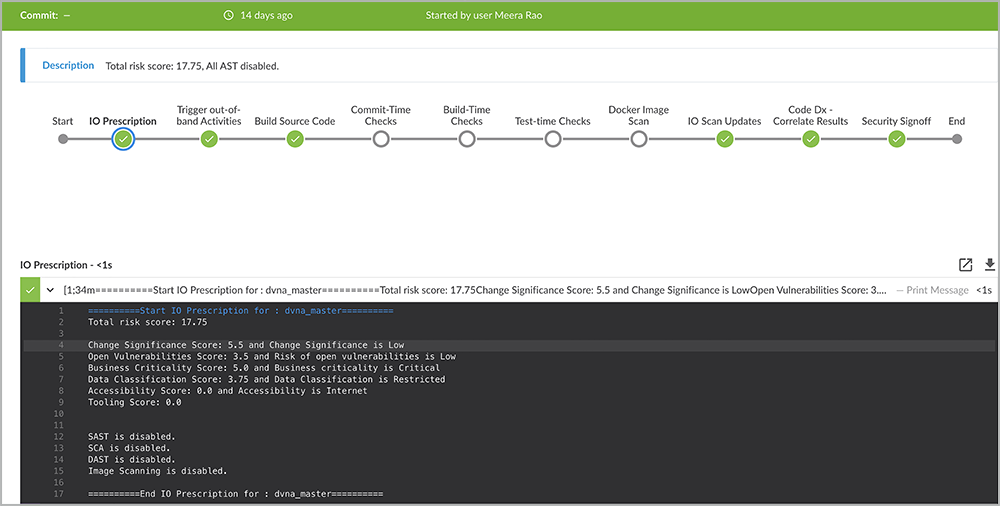
Intelligent Orchestration can also determine which scan actions or manual testing is required, based on actual code changes, resultant risk score, and corporate policies. If the code changes are minor, such as changing the font using CSS in an HTML file, the resultant risk score would be low, so no security scan tools would need to run at all, as shown in Figure 13 Scanning would be disabled, saving valuable time and resources.
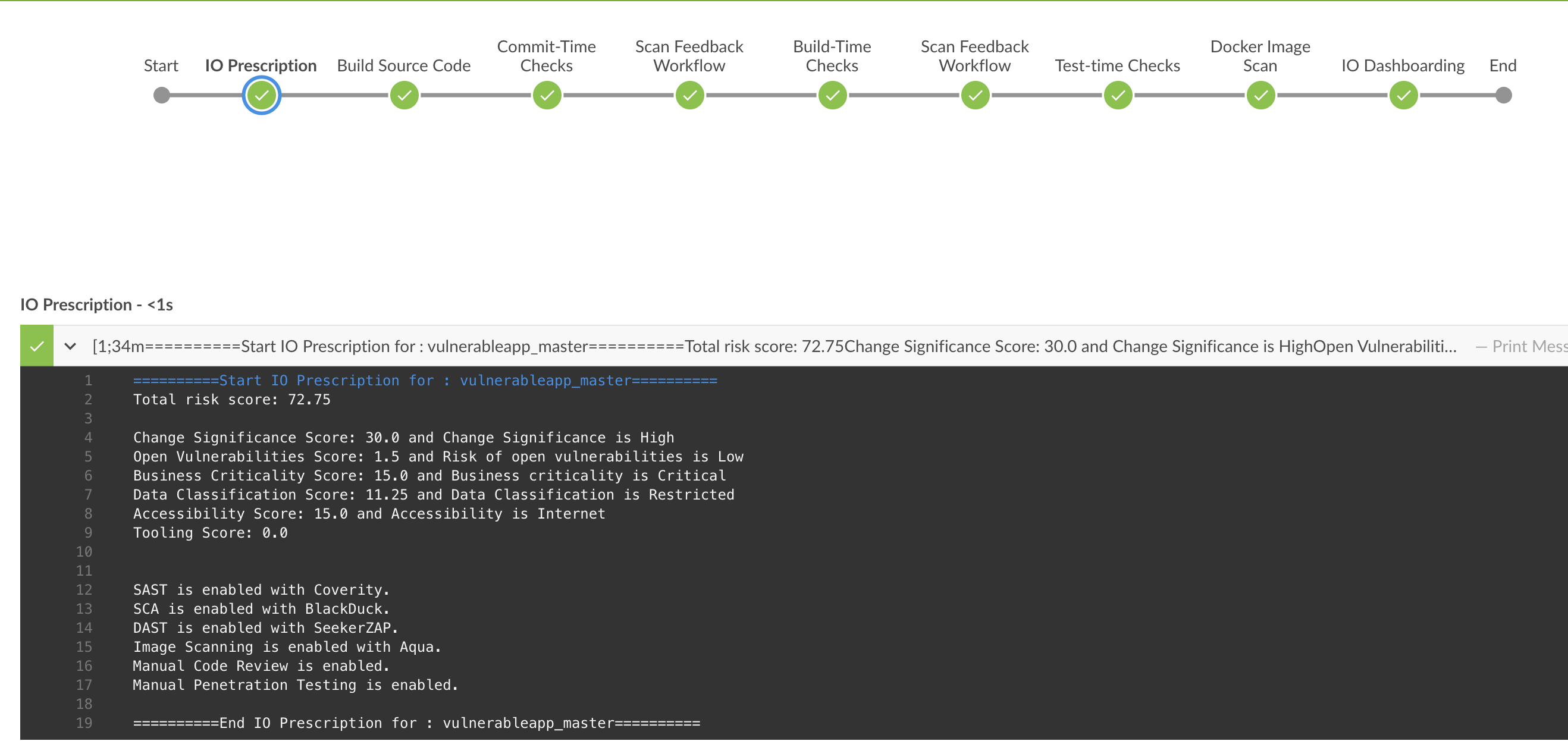
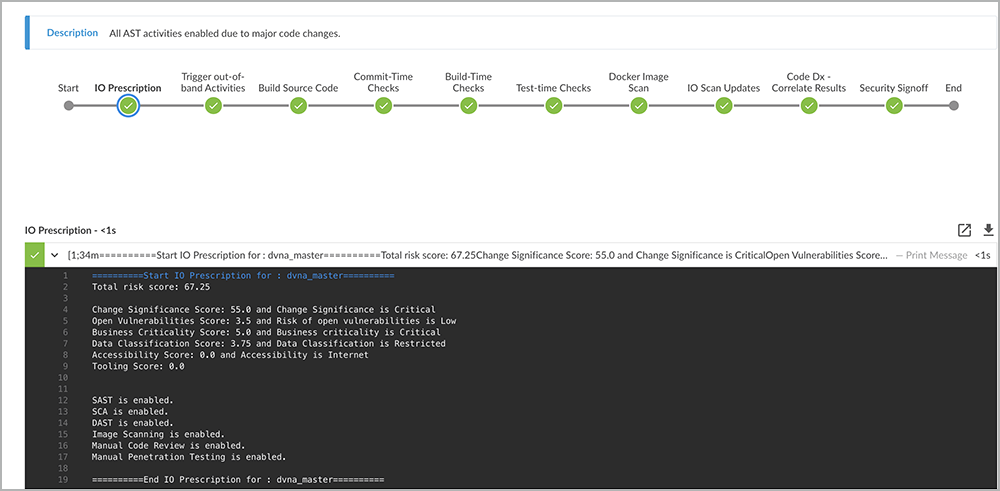
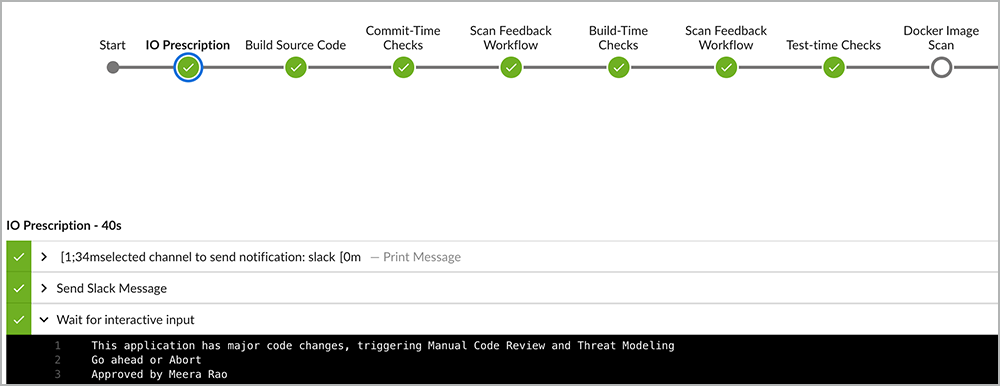
However, if the code change was major and critical in nature, such as changing an authentication API, this would result in a high risk score, and multiple security testing scans such as SAST, SCA, and DAST would be enabled, as shown in Figure 12. In addition, this would also trigger manual code review and manual penetration testing as required actions.
Figure 12: An example of major code changes, enabling all AST activities
Figure 13: An example of the sample application when a minor JavaScript file was changed
False positives
It is well-known in the industry that developers are not often security experts, and security teams are often not experienced developers. When security teams are delegated to triage, they often lack a full understanding of the application. Security defects are often rejected by developers as false positives.
With Code Dx, the correlation engine can normalize and correlate findings from multiple tools, so it becomes easy for security teams to triage in one place rather than doing this work on multiple tools and technologies, as shown in Figure 14.
Figure 14: An example showing issue drilldown for only the findings that are marked as new
Developer resistance
When we push everything found by security scanning tools, we also push away developers. With Intelligent Orchestration, developers are given prioritized vulnerabilities determined by their organization’s security policies to fix (e.g., only critical vulnerabilities or only critical SQLi vulnerabilities), so they aren’t overwhelmed by analysis results. Some figures above showed the build broken based on SCA and SAST findings.
Development teams can also specify that any time a developer pushes a code change, for example, GitHub Actions will run. Developers are provided with all the information they need to understand how to fix identified issues and later merge the fixed code into the main branch— detailed descriptions, actionable remediation advice, file changed, line number, and the commit ID.
For example, when a developer checks in source files, Synopsys Intelligent Security Scan knows to run static analysis and push just the results that the development team cares about.
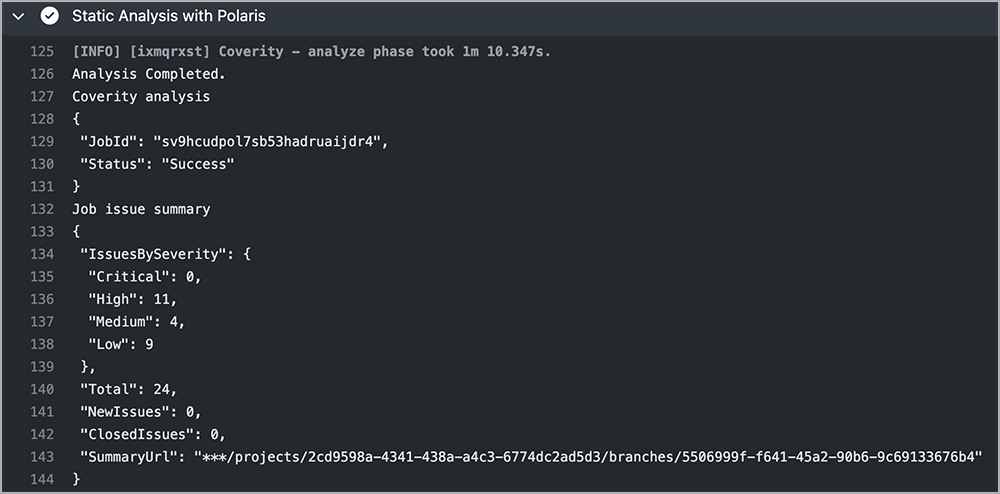
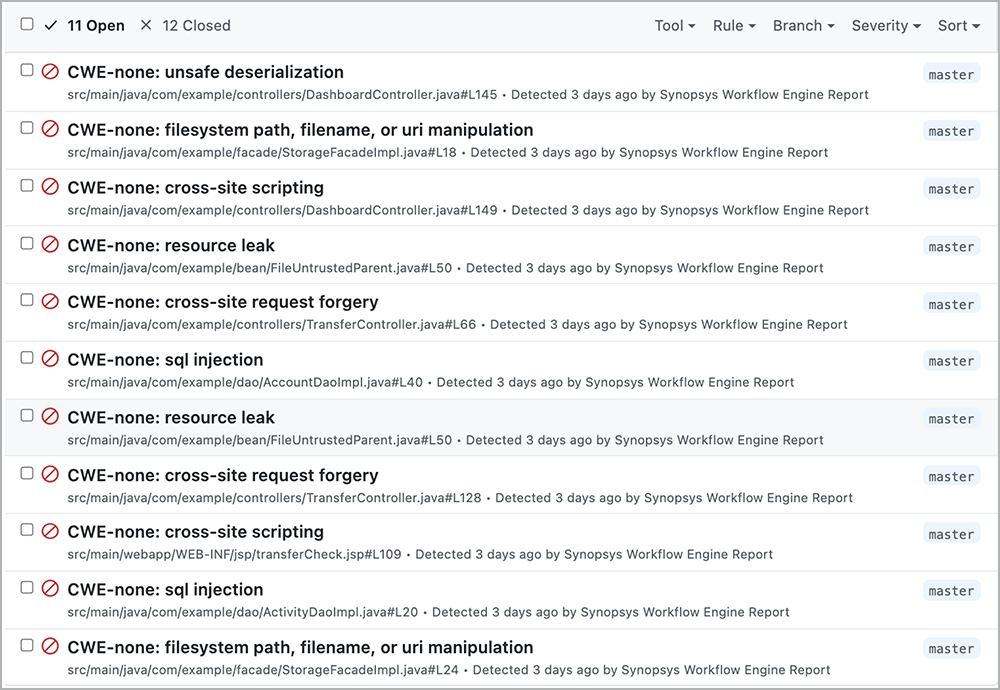
Figure 15 shows static analysis resulting in a total of 24 issues. In Figure 16, the code scanning alerts in GitHub Actions list just the top 11 issues. Which issues are prioritized is configured by the organization based on the issues the team cares about.
Figure 15: Static analysis scan identifying 24 issues within the build
Figure 16: Code scanning alerts in GitHub Actions list only the 11 issues the team is concerned about
Compliance
With Intelligent Orchestration, security teams can easily configure governance and compliance requirements. If an organization needs to perform manual penetration testing every 60 days, a manual code review will be triggered for every major release. All these policies can be configured as policy as code and enforced within the pipeline automatically, as shown in Figure 17.
Figure 17: The Intelligent Orchestration pipeline triggers a manual code review for a major release, based on policies configured by the DevSecOps team
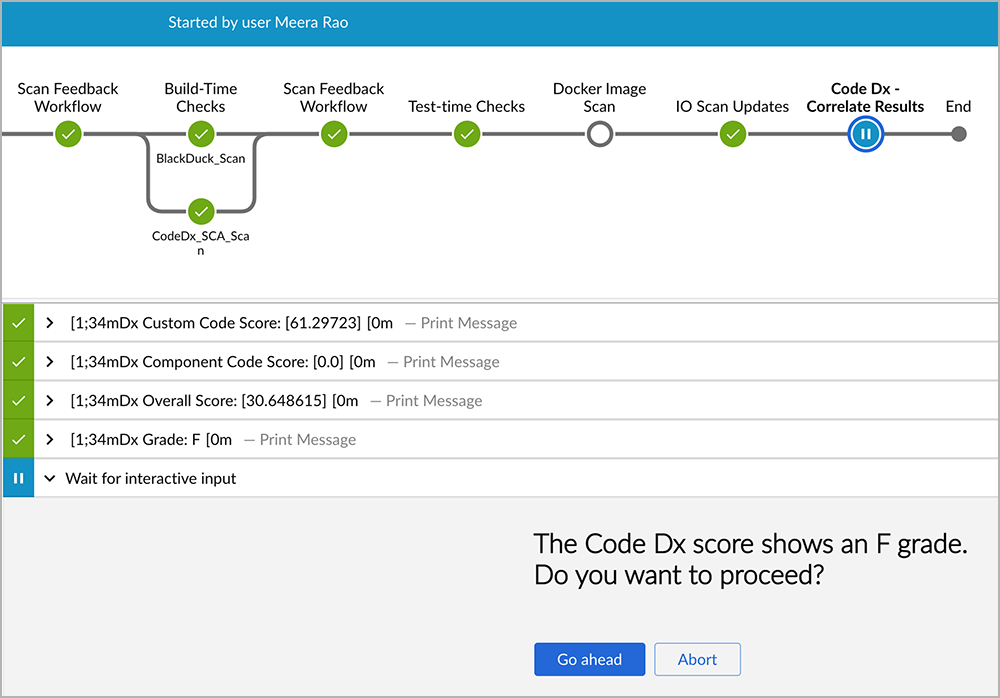
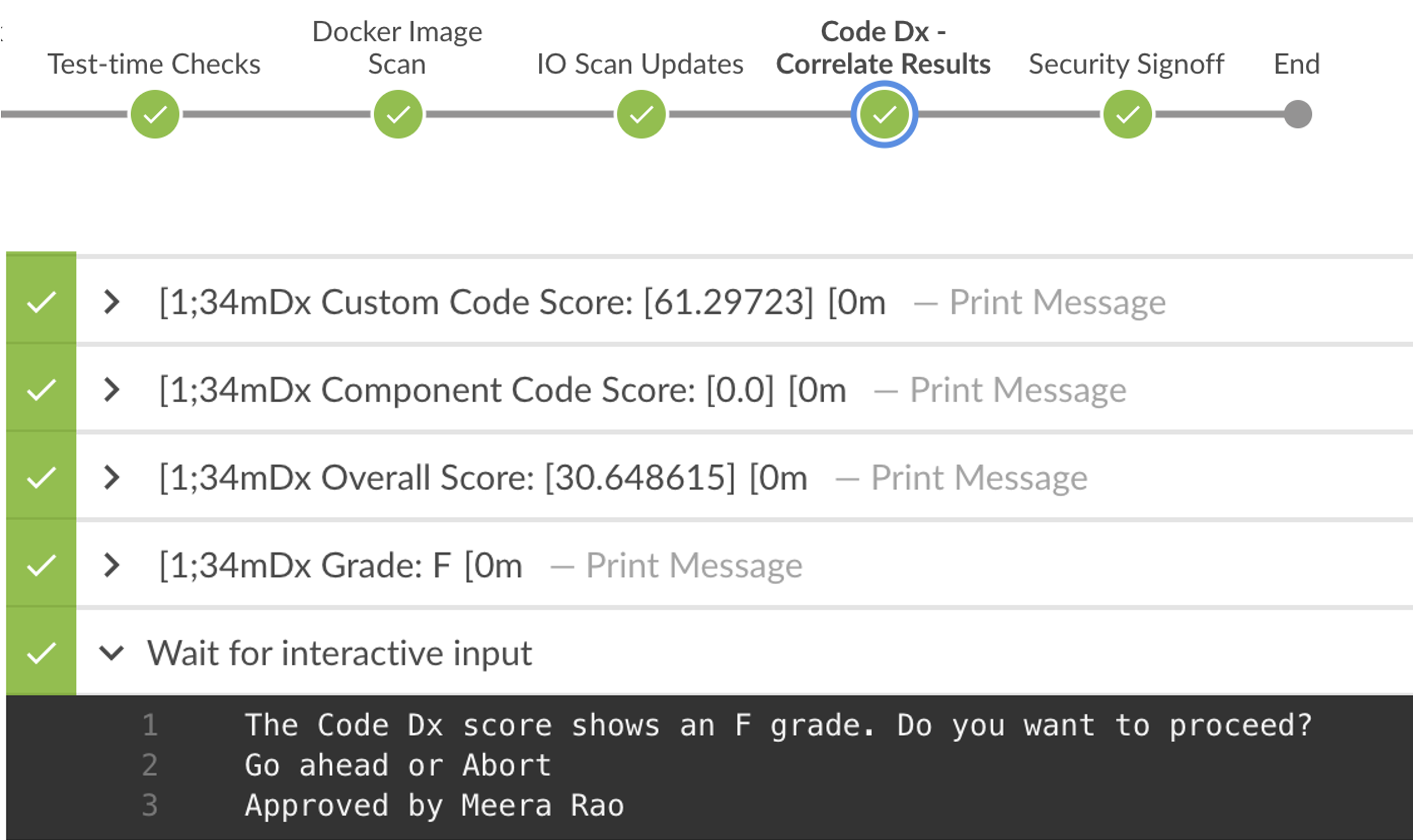
With Code Dx, it is easy to implement security gates based on configurable failing criteria or Code Dx Risk Score, as shown in Figure 18. Teams can query the risk score through the extensive APIs it provides, and allow the Intelligent Orchestration pipeline to pause the build, as shown in Figure 19.
Figure 18: An example of a Code Dx Risk Score based on configurable failing criteria
Figure 19: Intelligent Orchestration pauses the build based on information provided from the Code Dx Risk Score
Stronger DevSecOps with Intelligent Orchestration and Code Dx
Figure 20 shows the reasons why I think these two solutions combined create security superheroes.
Figure 20: The benefits of combining Intelligent Orchestration and Code Dx
- Higher speed: Instead of running all AppSec scans (e.g., SAST, SCA, IAST, DAST) for every build, these security superheroes run the right tools at the right time, or not at all.
- Lower cost: Your teams can fix software defects quickly, easily, and correctly with fast analysis results and actionable remediation advice as they code. Issue tickets are automatically created in Jira for tracking and triage. The earlier you find and fix, the cheaper it is to remediate.
- Reduced friction: With Intelligent Orchestration and Code Dx, security will meet developers where they are, using the interfaces and tools they prefer, reducing friction.
- Continuous feedback: Developers are given prioritized vulnerabilities determined by their organization’s security policies to fix (e.g., only critical vulnerabilities or only critical SQLi vulnerabilities), so they aren’t overwhelmed by analysis results. Intelligent Orchestration can determine when to run a specific tool and when not to, based on the actual code changes, a dynamically calculated total risk score, and predetermined security policies.
- Continuous compliance: Security teams can easily configure governance and compliance requirements. The policies that determine depth and breadth of security activities, detect any anomalies in normal development workflows, and scan compliance requirements can be configured for each individual business unit, product team, application, or the entire organization.
This is just the beginning of what these superheroes can do for enterprise application security. Try Intelligent Orchestration and Code Dx now and see for yourself.
![]()
*** This is a Security Bloggers Network syndicated blog from Software Integrity Blog authored by Meera Rao. Read the original post at: https://www.synopsys.com/blogs/software-security/intelligent-orchestration-code-dx-integration/