Multi-Factor Authentication is Not Foolproof Protection
Multi-Factor Authentication (MFA) has become increasingly common both in business and personal use. Yet, despite MFA providing increased security, threat actors are using the availability of sophisticated technology and even legitimate infrastructure to bypass this and access corporate networks and personal data.
To the uninitiated, MFA is when a user is required to provide two or more verification factors. The most typical type of MFA employed is Two Factor Authentication (2FA), when a user signs on to a site with their username and password and receives a code sent to a secondary device such as a mobile phone, email, or authenticator app. Once this code is entered into the site, it grants access. Until now, this security has been reasonably effective, and therefore users feel assured that it is entirely tamper-proof if the attacker does not have access to the secondary device which receives the code.
However, the bad actors have found ways to bypass MFA, putting network security at risk.
Man-in-the-Middle or Web Proxy Attack
The first technique bad actors employ is a man-in-the-middle (MitM) or reverse web proxy attack. This is when an attacker sends the user a link either through email or SMS that directs them to a phishing website. The link leads the user to a fake replica of a legitimate site – one that is nearly impossible to recognize as not legitimate for the average user.
For example, assume a Chase bank login page employs 2FA (Example 1). The attacker knows that even if they get the username and password, they still cannot access the site. And so, they use a reverse Web proxy between the phishing page and the actual service i.e., the man-in-the-middle.
Once the user enters the credentials, the phishing page will ‘talk’ to the original service, which will send the user the token or code to enter. At this point, the phishing page gets the code because the user enters it assuming s/he is on the official site. This gives the attacker the username, password, and code to authenticate with the real service and compromise the account.
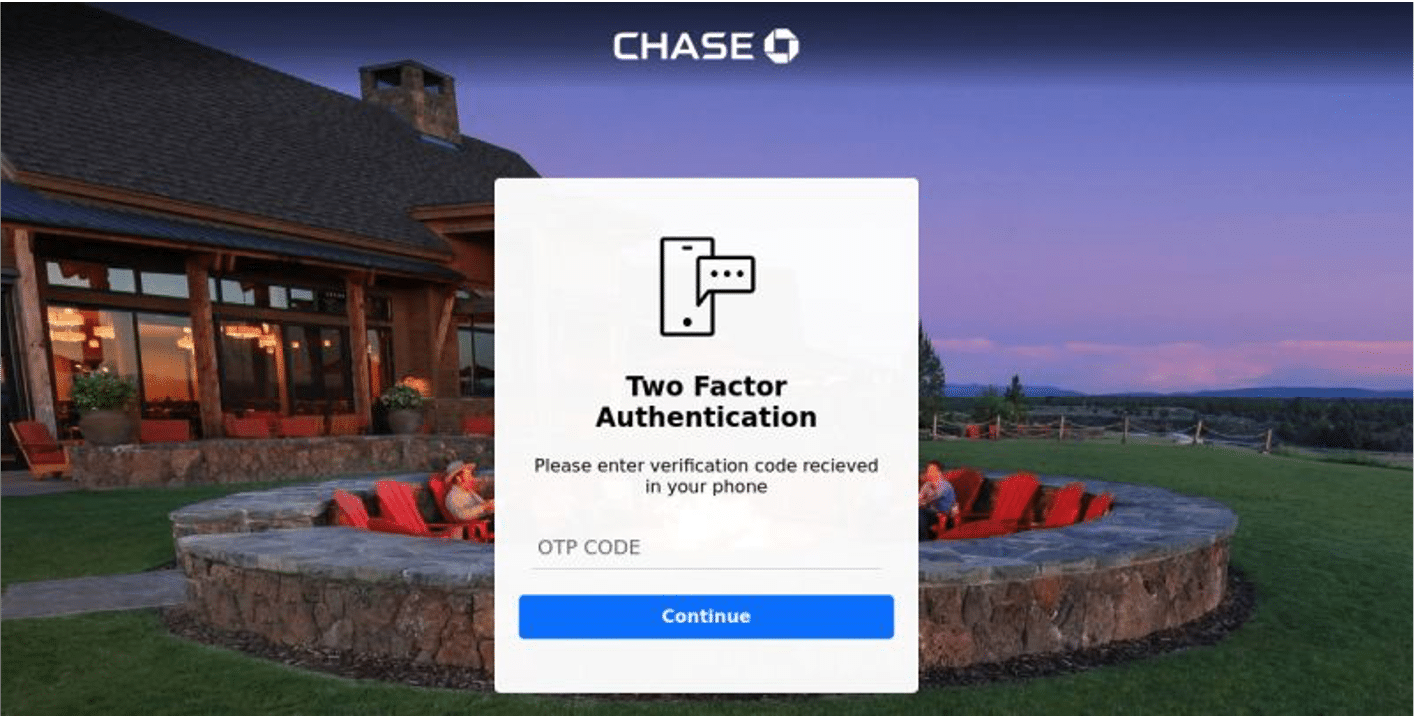
Example 1: A phishing site using reverse web proxy to hijack session cookies
Even more troubling, this type of attack is straightforward to perpetrate. Recently, some researchers made a toolkit available on GitHub that automates MitM. While they did so for educational purposes, it illustrates how easily accessible malicious tools have become to download and use by threat actors – even those without an in-depth technical background.
Malicious OAuth Apps
The second technique bad actors use is Malicious OAuth applications. Every cloud service allows users to grant certain access to third-party applications without continually signing in and authenticating themselves. Once permission is granted to the third-party app, it can access the account through OAuth tokens. The downside to this is that because the process of granting permission is so straightforward, attackers can easily fool users into authorizing malicious applications.
In this instance, the attack flow would be a user receiving a phishing link that would point to the original vendor website. Users trained to look out for suspicious URLs are easily deceived. Using a Microsoft 365 example, the user would click on the Microsoft link, which will ask for their username and password. Once entered, the page would request permission from the user to access the third-party application. When they authorize this, typically based on a well-crafted message, the malicious application will have complete access to the account.
Suppose this were to happen to a user with access to most of the network – such as an IT leader or executive. In that case, the app can trick the person into granting permission to the entire Active Directory of the organization, leaving the business completely open.
Malicious Browser Extensions for Browser Hijack
The third example of attack is probably the most dangerous: malicious browser extensions or the browser hijacker
As a result of the software-as-a-service business model, most people are doing everything in their browsers – from online shopping to accessing emails and corporate document repositories. All modern browsers have extensions that are essentially plugins. Once installed, these have the same access and privilege as the browser. So, whatever is rendered inside the browser, is completely visible to the plugin.
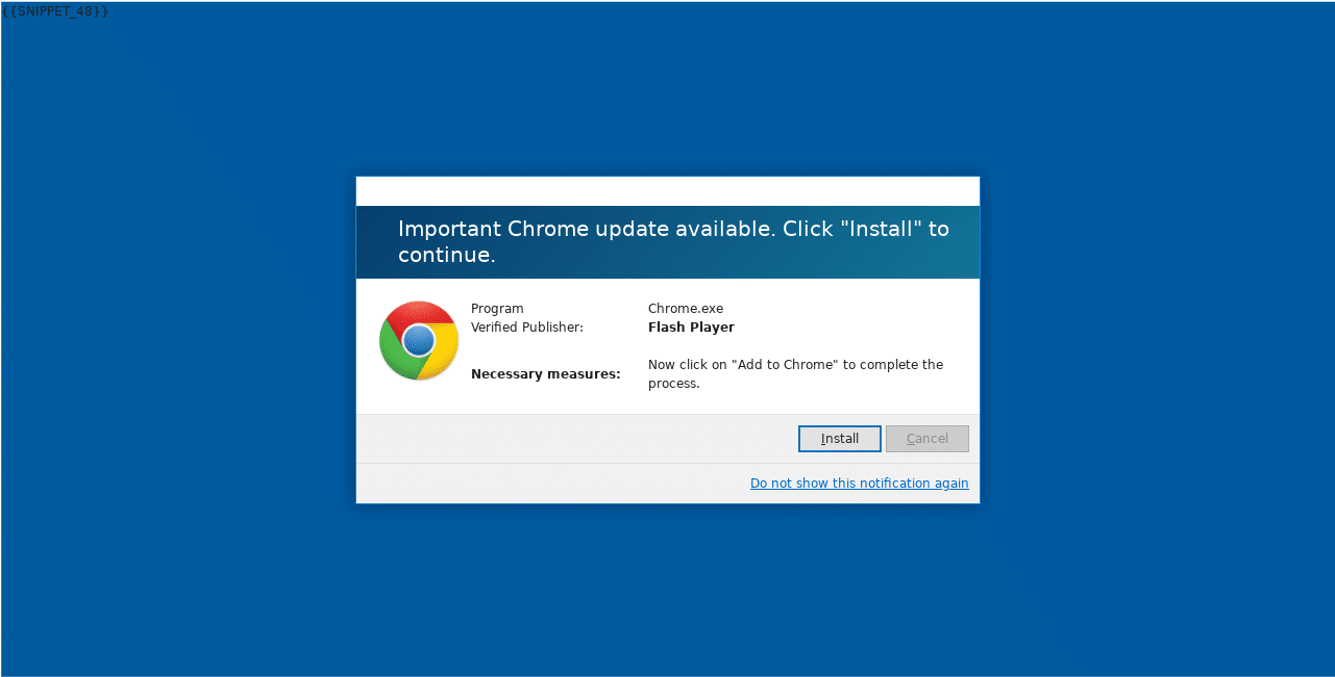
Example 2: A phishing page asking to install a rogue browser extension/browser hijacker
A user that receives a phishing link — potentially through email, SMS or an online ad is asked to download a specific extension. Usually, the threat actors would employ clever social engineering techniques to get people to install this plugin disguised as a legitimate application. But once installed, the plugin can scrape all the data from within the browser, such as Microsoft 365 login data or anything else the user is typing, like online banking information.
‘Overcoming’ Training
All these MFA compromises are increasingly using legitimate cloud services like Google, Dropbox, or SharePoint to spread phishing attacks. Organizations have these services whitelisted, so it becomes easy to have a phishing page hosted on the legitimate infrastructure. We even recently pointed out to Google that they had approximately 50,000 hosted attacks coming from deep inside its domains.
This is one of the core challenges. Looking for suspicious domains has become part of cybersecurity training. This means that if the user sees a domain that appears legitimate, they will trust the site and assume it is safe. Most training also focuses on helping users identify phishing emails – when today phishing attacks are occurring through SMS, collaboration apps and other channels.
The best way to mitigate against this is to employ a Zero Trust approach. Where the user is taught not to trust anything, regardless of its source. Bad actors are active in all channels perpetuating human hacking – that is, taking advantage of the fact that humans are the weakest link of the security process. Inevitably, human error will result in a compromise occurring.
Employing Machine Defenses
Bad actors have more tools available to them that they can easily combine with automation and legitimate infrastructure. That means they can quickly spin up attacks inside Azure, Google, or AWS. These attacks can correlate user behavioral information on the Dark Web and become very targeted to specific individuals.
The best way to combat this is to fight machines with machines. The human hours required to defend against these automated attacks are virtually impossible to employ – and attacks move too fast for human forensics to catch and protect against. Before last year, our AI-powered detection caught about 15,000 daily unique phishing attacks. Today, there are days when we detect more than 50,000 unique phishing attacks. With the level of automation now available, imagine how much this will grow over the coming year or two.
Because the velocity of these attacks is so high, corporations need multiple defenses that combine various techniques. Using MFA is an excellent security step, but the lesson is nothing is foolproof. Part of any good network security plan is protecting from attacks against the humans using your network – on any channel, from any location. Threat actors are always looking at how best to evade these techniques and compromise the network.
To hear more about MFA, and how to protect your organization, watch the latest episode of SlashNext’s Phish Stories with SlashNext founder and cybersecurity expert Atif Mushtaq and CEO Patrick Harr. Available on-demand at https://www.slashnext.com/phish-stories-webinar-series/
The post Multi-Factor Authentication is Not Foolproof Protection first appeared on SlashNext.
*** This is a Security Bloggers Network syndicated blog from SlashNext authored by Lisa O'Reilly. Read the original post at: https://www.slashnext.com/blog/multi-factor-authentication-is-not-foolproof-protection/





