Integrating Acunetix with CircleCI
If you want to include Acunetix in your DevSecOps, you need to integrate it with a CI/CD system. Acunetix has an out-of-the box integration for the most popular CI/CD system – Jenkins. However, you can use the Acunetix REST API to integrate the scanner with any CI/CD system. In this article, we’ll show you how to integrate Acunetix with the CircleCI CI/CD platform.
In this step-by-step example, we will use a simple web application running on Node.JS. We will integrate this application with GitHub and CircleCI.
Step 1. Prepare your Acunetix target information
- Log in to your Acunetix installation.
- Create a target for your web application. In this example, our web application is available via the following URL: http://testwebapp.acunetixexample.com:8080.
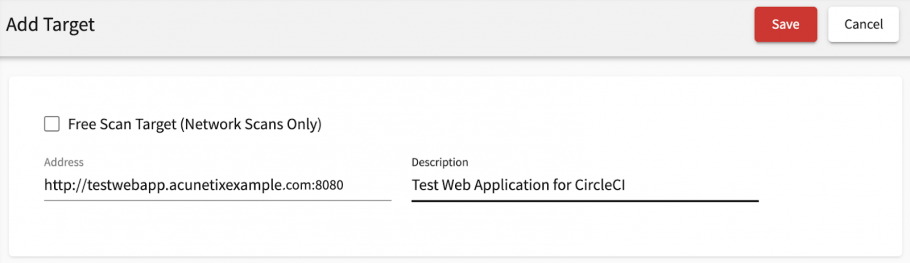
- Enter the URL for your web application
- Enter a Description for your web application
- Click on the Save button
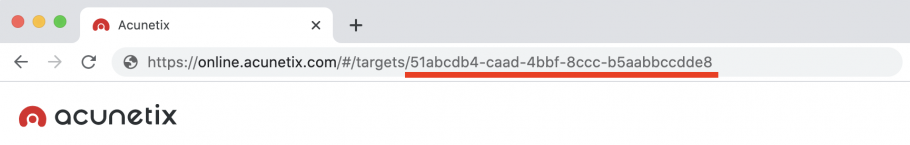
- You will be taken to the Target Settings page, where you can now retrieve the target ID from the URL.
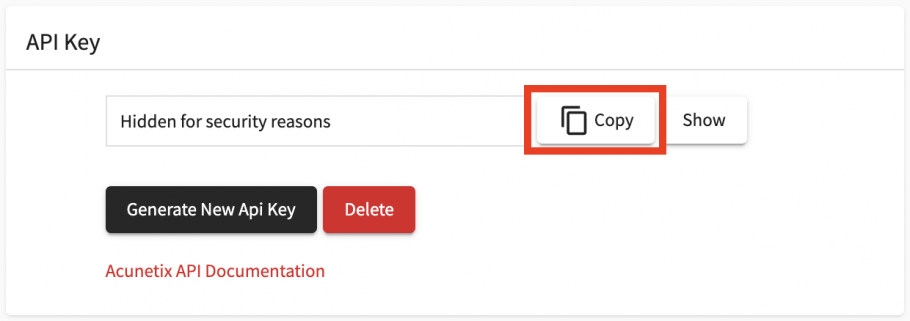
- Go to your profile page and retrieve your API key by clicking on the Copy button.
Step 2. Prepare your GitHub repository
- Log in to your GitHub account – in this example, the account name is acunetix-test and the account email address is [email protected].
- On the Repositories page, click on the New button.
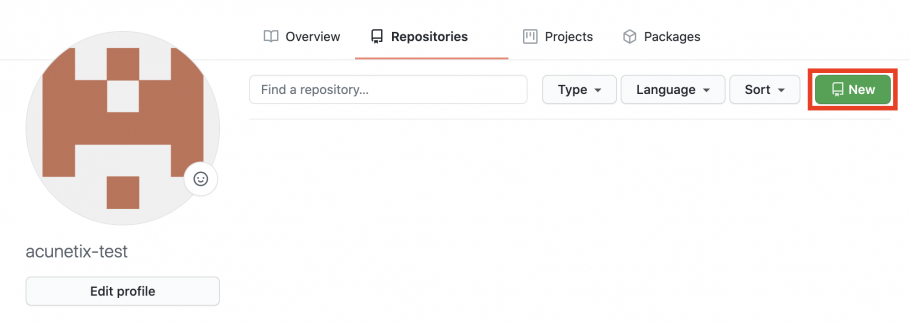
- Create the new repository:

- Enter a Repository name – in this example, the repository name will be testwebapp
- Enter a Description for your repository
- Enable the Add a README file checkbox to initialize the repository
- Click on the Create repository button
Step 3. Prepare your local environment
In this example, the local environment will be a Ubuntu 20.04.1 desktop setup, but it should be the same for most Linux or MacOS setups. It should be sufficient to replace platform-specific steps with those appropriate for your environment. All the following steps will be performed on your local environment machine.
Install prerequisites
- Update and upgrade your environment:
sudo apt update && sudo apt upgrade -y - Install git to interact with your GitHub repository:
sudo apt install git -y - Install Node.JS and npm:
sudo apt install npm -y
Write your local source code
- Check out your GitHub repository:
cd ~ git clone https://github.com/acunetix-test/testwebapp.git (substitute "acunetix-test" with your GitHub account name) - Initialize npm within your local code repository:
cd ~/testwebapp npm init -y - Create your basic web application with the file app.js in the base folder:
nano ~/testwebapp/app.js - Add the following lines to your app.js file:
const http = require('http'); http.createServer(function (req, res) { res.write('<html><head></head><body>'); res.write('Welcome to the Test Web Application!'+'<br/>'); res.write('===================================='+'<br/>'); res.write('</body></html>'); res.end(); }).listen(80, '0.0.0.0');
Add a CircleCI workflow configuration file to your source code
- Create the configuration file:
mkdir ~/testwebapp/.circleci nano ~/testwebapp/.circleci/config.yml - Add the following lines to your config.yml file:
version: 2.1 # Define the jobs for testwebapp (check out code and run a deploy.sh script) jobs: pull-and-build: docker: – image: arvindr226/alpine-ssh steps: – checkout – run: ssh -oStrictHostKeyChecking=no -v $USERNAME@$HOSTNAME "./deploy.sh" # Orchestrate the testwebapp job run sequence (runs only on commit to main branch) workflows: version: 2 build-project: jobs: – pull-and-build: filters: branches: only: – main
Commit changes to the GitHub repository
- Change to the correct directory:
cd ~/testwebapp - Set your GitHub credentials and remote repository (substitute with your GitHub account email address):
git config user.email "[email protected]" - Commit your code changes:
cd ~/testwebapp git add . git commit -m "first code commit" git push
Step 4. Prepare your deployment environment
In this example, the deployment environment will be a Ubuntu 18.04 LTS server running on a cloud platform. Therefore, the hostname for your deployment environment would be the same as for your target (in this example: testwebapp.acunetixexample.com).
Create a user for CircleCI to connect to the deployment environment
- Log in to your deployment environment as the root user.
- Create a user that does not use a password for login:
useradd -m -d /home/circleuser -s /bin/bash circleuser - Create an SSH key without a passphrase for the circleuser user:
ssh-keygen -m PEM -t rsa -f ~/.ssh/circleuser - Add the newly-created public key to /home/circleuser/.ssh/authorized_keys:
mkdir -p /home/circleuser/.ssh printf "n" >> /home/circleuser/.ssh/authorized_keys cat ~/.ssh/circleuser.pub >> /home/circleuser/.ssh/authorized_keys chown -R circleuser:circleuser /home/circleuser - Show the contents of the private key:
cat ~/.ssh/circleuser - Copy the contents of the private key – you will use this to allow your CircleCI to log in to your deployment environment.
Create a set of SSH keys for the user to authenticate in GitHub
- Log in to your deployment environment as the circleuser user.
- Create new SSH keys without a passphrase:
ssh-keygen -t rsa - Display the public key in the console and copy it for later:
cat ~/.ssh/id_rsa.pub - Log in to your GitHub account and navigate to your application’s repository.
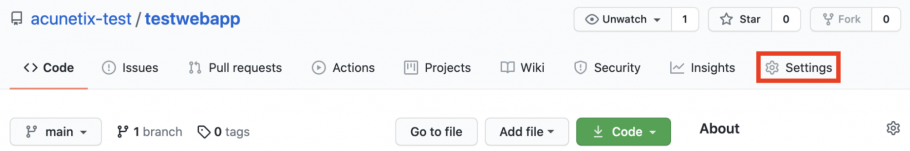
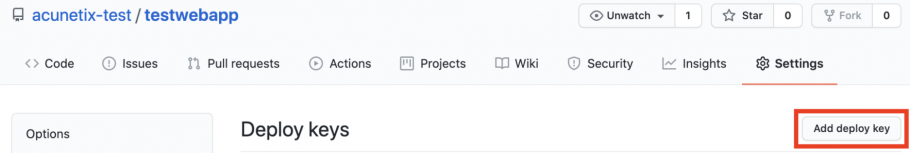
- Click on the Settings tab.
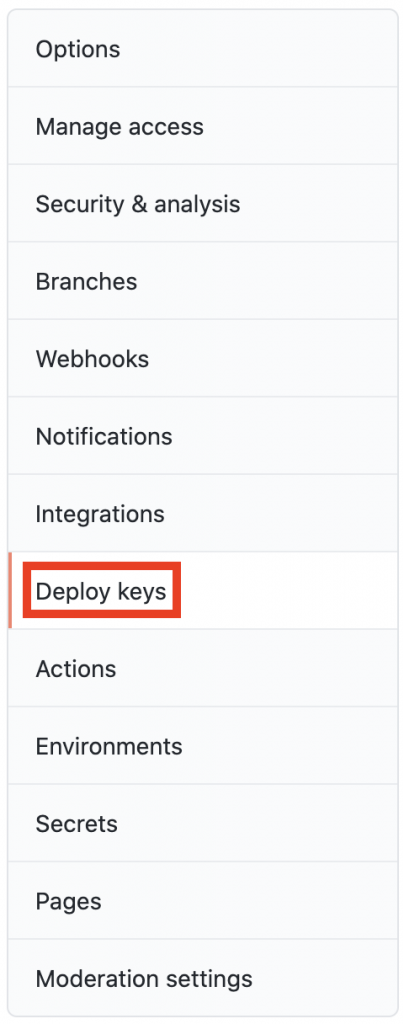
- Select Deploy keys in the sidebar.
- Click on the Add deploy key button.
- Add a new key:

- Set the Title field to LogFromDeployEnvironment (or any other easy to remember name)
- Paste the contents of the public key you copied earlier into Key field
- Click on the Add key button
Configure firewall access for SSH and HTTP
Allow SSH and HTTP traffic through the firewall:
- Log in to your deployment environment and run the following:
sudo ufw allow OpenSSH sudo ufw allow 80 sudo ufw enable
Set up the project
- Log in to your deployment environment as the circleuser user.
- Clone the project source code (replace as necessary in the format: [email protected]:your_user_name/your_application_name.git):
git clone [email protected]:acunetix-test/testwebapp.git - Temporarily move to the testwebapp folder and install dependencies:
cd testwebapp npm install cd ~ - Temporarily elevate your privileges to the root user and install pm2 to allow running a Node app as a background process:
su npm install -g pm2 Exit - Start up your Node app using pm2 to register the process:
pm2 start ~/testwebapp/app.js - Create a deploy.sh file:
nano ~/deploy.sh - Add the following lines to your deploy.sh file:
#!/bin/bash # Replace this with the path of your project on the VPS cd ~/testwebapp # Pull from the branch git pull origin main # Followed by instructions specific to your project that you used to do manually npm install export PATH=~/.npm-global/bin:$PATH source ~/.profile pm2 restart ~/testwebapp/app.js
Step 5. Configure CircleCI to integrate with GitHub
Set up the CircleCI project
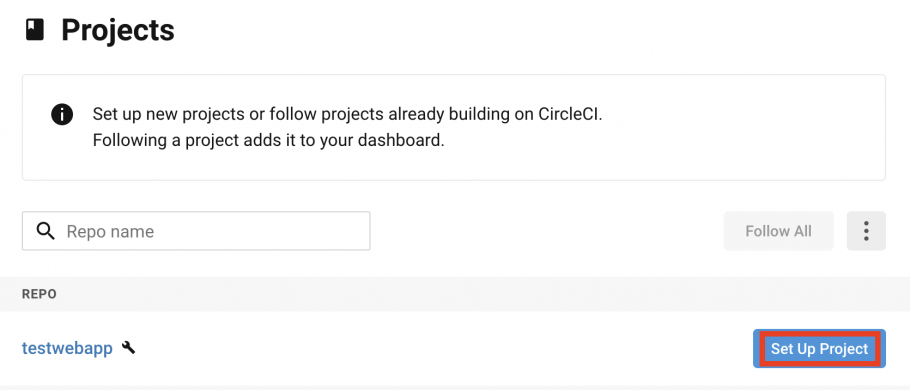
- Log in to your CircleCI account.
- Go to your list of projects and click on the Set Up Project button for the project you wish to work with – in this example, your project is called testwebapp.
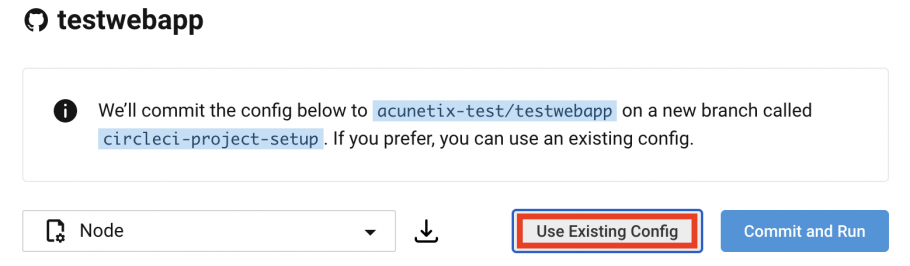
- Click on the Use Existing Config button (you have already created a config.yml file in the repository).
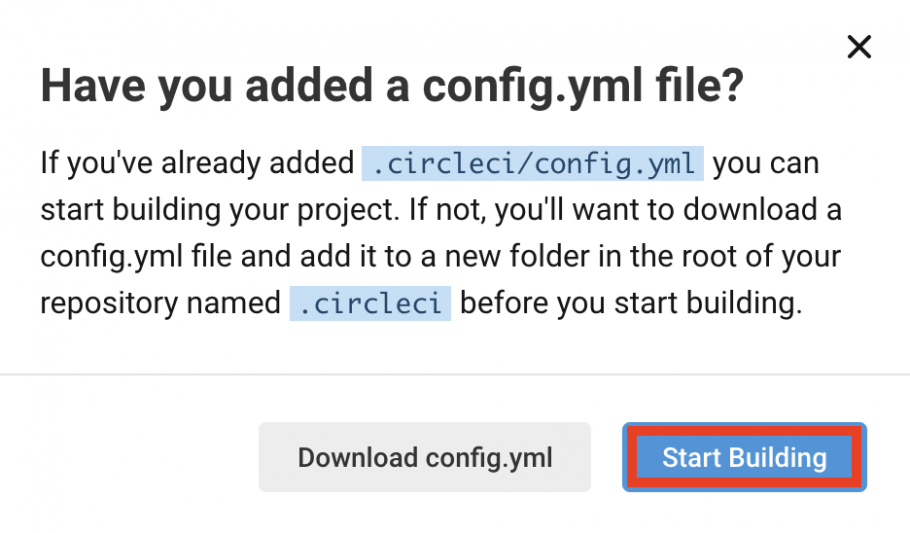
- Click on the Start Building button (this will use the config.yml from your repository). This will immediately trigger the first build and send you to the pipeline page. This initial build will fail because you need to perform some additional steps.
Configure the SSH key for CircleCI to connect to the deployment environment
- On your application’s pipeline page, click on the Project Settings button.
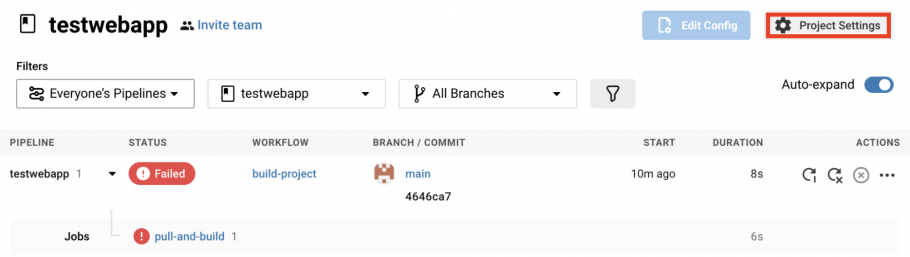
- Click on the SSH Keys menu item.
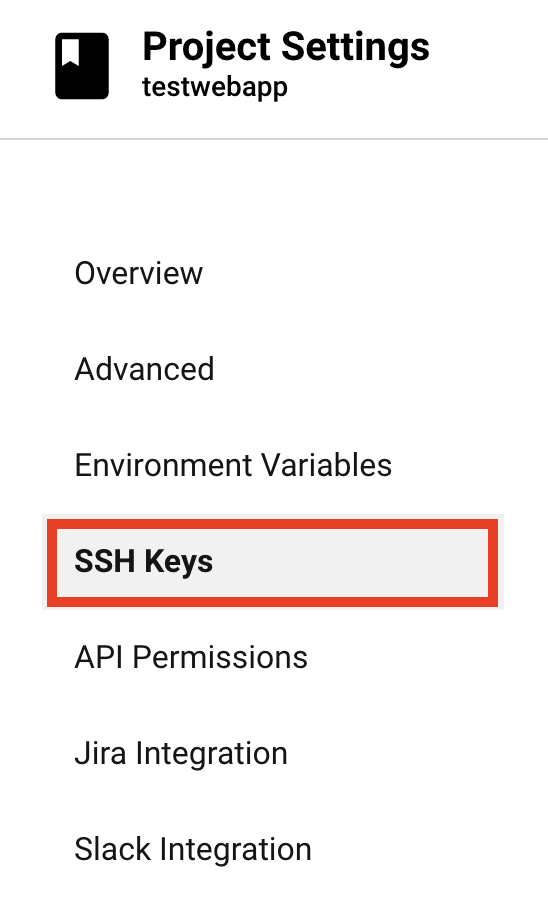
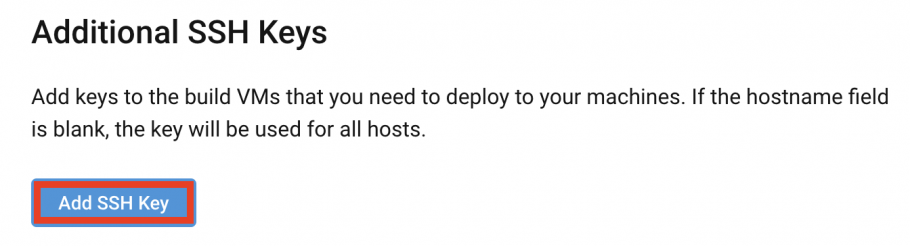
- Click on the Add SSH Key button.
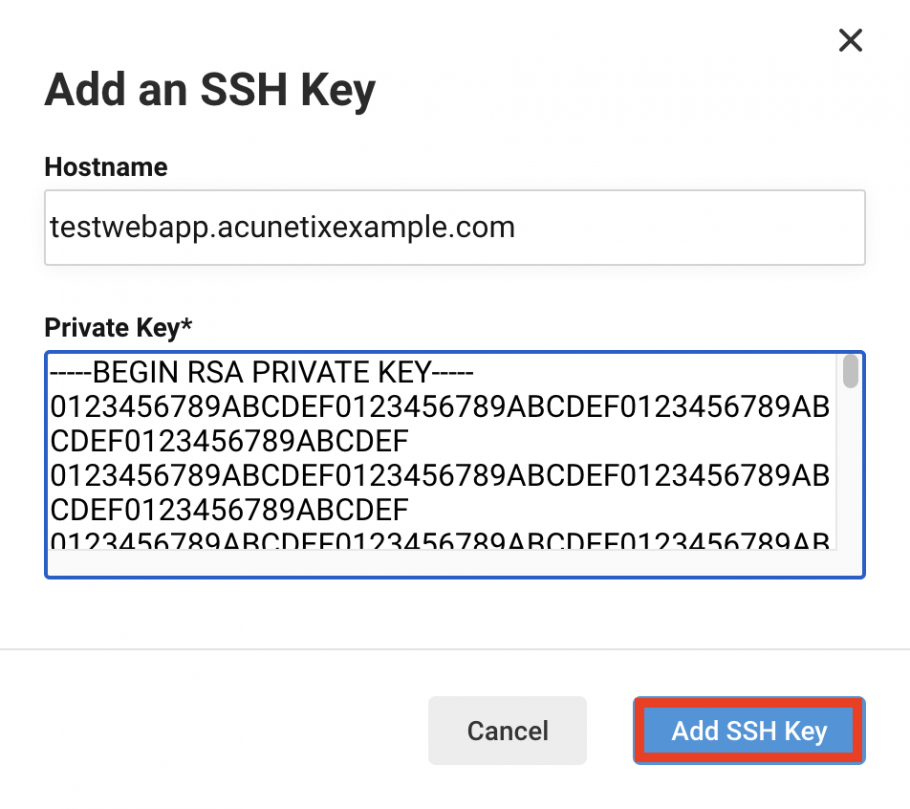
- Enter the Hostname for your deployment environment (in this example: testwebapp.acunetixexample.com).
- Enter the private key that you copied from your deployment environment.
- Click on the Add SSH Key button.
Configure environment variables
- On your application’s pipeline page, click on the Project Settings button.

- Click on the Environment Variables menu item.
- Click on the Add Environment Variable button.
- Add an environment variable for the circleuser user that you created earlier in the deployment environment:
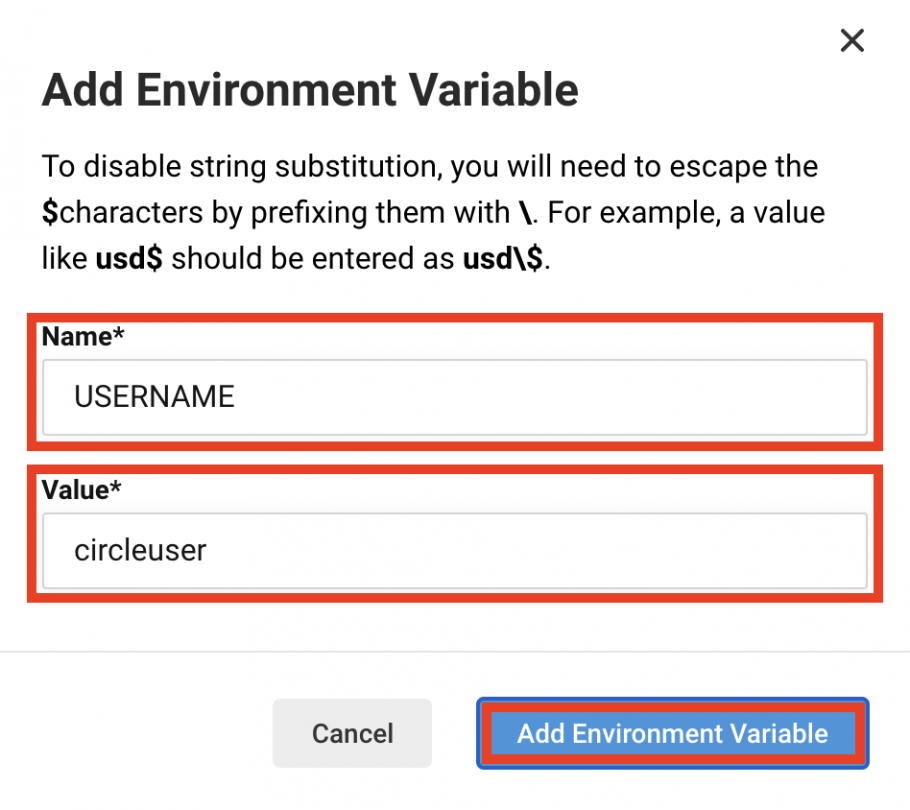
- Set the Name field to USERNAME
- Set the Value field to circleuser
- Click on the Add Environment Variable button
- Add an environment variable for the IP address or the hostname of your deployment environment. In this example, the hostname is testwebapp.acunetixexample.com:
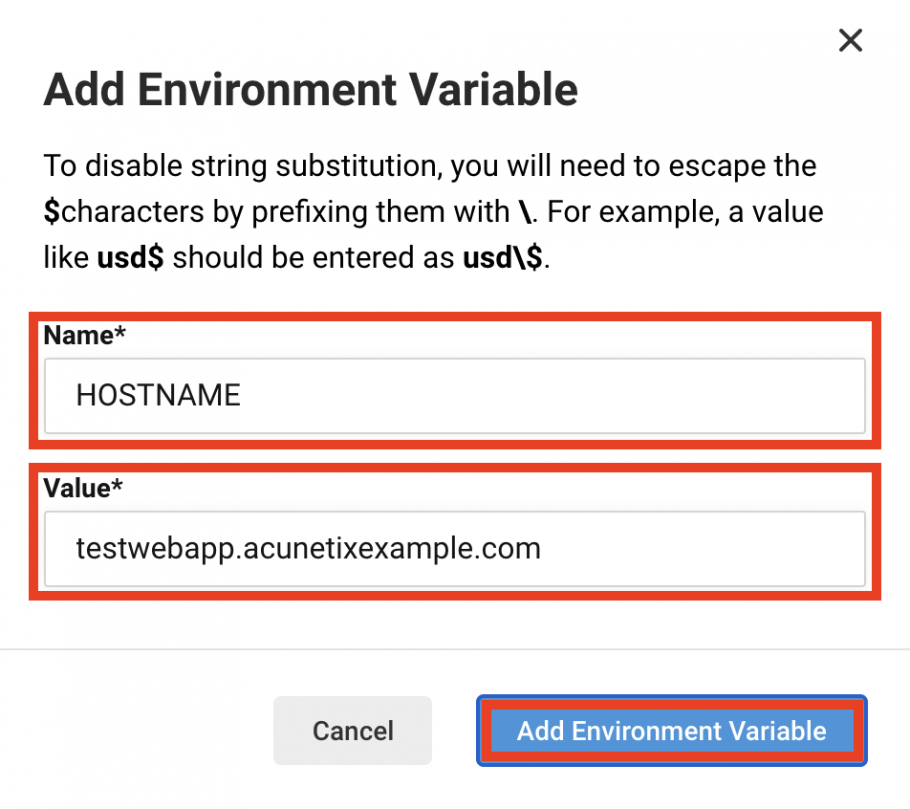
- Set the Name field to HOSTNAME
- Set the Value field to testwebapp.acunetixexample.com
- Click on the Add Environment Variable button
Step 6. Test pipeline workflow
The main test to check everything is working correctly is to simply make a change to the source code, commit the changes, and push the changes to GitHub. This will show up in your CircleCI pipeline page:
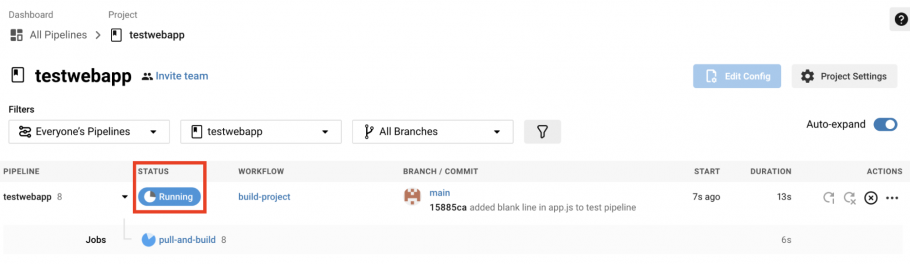
Step 7. Integrate with Acunetix
Finally, you need to edit the deploy.sh file in your deployment environment to add instructions to trigger an Acunetix scan of your web application target after every build.
- Log in to your deployment environment as the circleuser user.
- Edit the deploy.sh file:
nano ~/deploy.sh - Add a curl line to your deploy.sh file to trigger the scan; the final file should look like this:
#!/bin/bash # Replace this with the path of your project on the VPS cd ~/testwebapp # Pull from the branch git pull origin main # Followed by instructions specific to your project that you used to do manually npm install export PATH=~/.npm-global/bin:$PATH source ~/.profile pm2 restart ~/testwebapp/app.js curl -k -i --request POST --url "https://online.acunetix.com/api/v1/scans" --header "X-Auth: [API KEY]" --header "content-type: application/json" --data '{"profile_id":"11111111-1111-1111-1111-111111111111","schedule":{"disable":false,"start_date":null,"time_sensitive":false},"user_authorized_to_scan":"yes","target_id":"[Target ID]"}' - Replace the 3 highlighted fields:
- To set the correct X-Auth value, replace the [API KEY] text with the API key that you retrieved in the first section.
- The suggested value for profile_id is 11111111-1111-1111-1111-111111111111 – this default value is for a full scan. If you wish to specify a different scan profile, you can set one of the following values:
- For the online version of Acunetix:
- Full scan: 11111111-1111-1111-1111-111111111111
- High risk vulnerabilities: 11111111-1111-1111-1111-111111111112
- SQL injection vulnerabilities: 11111111-1111-1111-1111-111111111113
- Weak passwords: 11111111-1111-1111-1111-111111111115
- Cross-site scripting vulnerabilities: 11111111-1111-1111-1111-111111111116
- Crawl only: 11111111-1111-1111-1111-111111111117
- Malware scan: 11111111-1111-1111-1111-111111111120
- Full web and network scan: 11111111-1111-1111-1111-211111111111
- Network scan: 11111111-1111-1111-1111-211111111112
- Network scan (safe checks): 11111111-1111-1111-1111-211111111113
- Network scan quick: 11111111-1111-1111-1111-211111111114
- For the on-premises version of Acunetix:
- Full scan: 11111111-1111-1111-1111-111111111111
- High risk: 11111111-1111-1111-1111-111111111112
- SQL injection vulnerabilities: 11111111-1111-1111-1111-111111111113
- Weak passwords: 11111111-1111-1111-1111-111111111115
- Cross-site scripting vulnerabilities: 11111111-1111-1111-1111-111111111116
- Crawl only: 11111111-1111-1111-1111-111111111117
- High/medium risk: 11111111-1111-1111-1111-111111111119
- Malware scan: 11111111-1111-1111-1111-111111111120
- You can also use the scan profile ID of any custom scan profiles you may have created. You can retrieve the scan profile ID of custom scan profiles programmatically using the Acunetix REST API or by navigating to the custom scan profile and checking the URL:
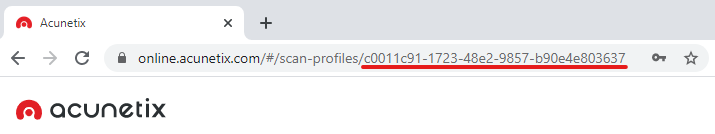
- For the online version of Acunetix:
- To set the correct target_id value, replace the [Target ID] text with the target ID you retrieved in the first section.
- All future commits will now also trigger a scan request to Acunetix:
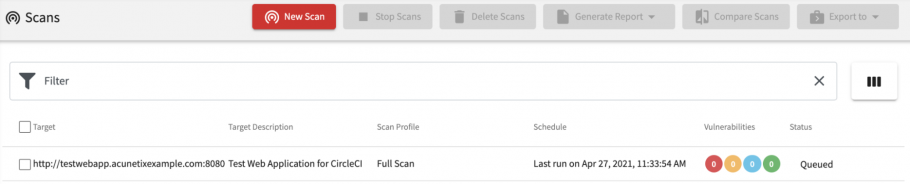
Get the latest content on web security
in your inbox each week.
*** This is a Security Bloggers Network syndicated blog from Web Security Blog – Acunetix authored by Kevin Attard Compagno. Read the original post at: http://feedproxy.google.com/~r/acunetixwebapplicationsecurityblog/~3/AsNgbxuSKwU/