File Inclusion Vulnerabilities — Web-based Application Security, Part 9
In today’s business climate, it’s hard to imagine running a company without web applications. Web-based applications have become an essential business tool due to their multiple benefits from streamlining workflows to improving communication and collaboration, and relationships with clients.
As such, any issue with your web application can hinder business operations, lead to data loss or potentially bring your business to a standstill. Therefore, it’s critical to know about the vulnerabilities in web applications to ensure your online information is more secure.
In this blog series, we deep-dive into file inclusion vulnerabilities and how you can protect your organization against these web-based threats.
What Is PHP File Inclusion?
PHP File Inclusion is a security flaw in web applications that allows unauthorized users to access files, provide download functionality, look for information, and so on. As defined by OWASP, the File Inclusion vulnerability allows an attacker to include a file, usually exploiting a “dynamic file inclusion” mechanisms implemented in the target application. The vulnerability occurs due to the use of user-supplied input without proper validation.
The Web Technology Surveys indicate that a whopping 79.2% of all websites use PHP. This means that majority of today’s web applications are at risk.
There are two PHP functions that website or web application programmers use to include the content of one PHP file into another PHP file.
- The include() function
- The require() function
The difference between the “include” and the “require” functions is the way each function responds when a file loading problem arises. The include() function only gives a warning while allowing the script to continue, whereas the require() function generates a fatal error and stops the script.
What Is the Difference Between LFI and RFI?
Local File Inclusion (LFI) and Remote File Inclusion (RFI) are two common vulnerabilities that typically affect PHP web applications. These vulnerabilities are caused due to poorly written web applications and/or failing to follow appropriate security practices. Cybercriminals can exploit these weaknesses to disclose sensitive information or take control of the entire server.
The main difference between an LFI and an RFI is the included file’s point of origin. In an LFI attack, threat actors use a local file that is stored on the target server to execute a malicious script. These types of attacks can be carried out by using only a web browser. In an RFI attack, they use a file from an external source.
Local File Inclusion (LFI)
LFI is a web vulnerability that results from mistakes at the website or web application programmers’ end. A hacker can take advantage of this vulnerability to include malicious files which are then executed by the vulnerable website or web application.
In an LFI vulnerability, the included file is already present on the local application server, targeted by the hacker. If successful, the attacker can read important files, access more sensitive information, or run arbitrary commands.
How Does Local File Inclusion Work?
In Local File Inclusion, perpetrators exploit vulnerable PHP programs to access confidential data or run malicious scripts on the target server. This can expose critical data or allow threat actors to launch remote code execution or Cross-site Scripting (XSS) attacks. LFI occurs when an application includes a file as user input without properly validating it. This allows an attacker to include malicious files by manipulating the input.
Here’s an example of a vulnerable PHP code that could lead to LFI:
https://example.com/?page=filename.php
Without proper input sanitizing, an attacker could easily modify the input (as shown below) to manipulate the application into accessing unauthorized files and directories from the host server using the “../” directive. This is known as Directory (Path) Traversal:
https://example.com/?page=../../../../etc/test.txt
In this example, a hacker was able to successfully exploit the vulnerability by simply replacing the “filename.php” with “../../../../etc/test.txt” in the path URL to access the test file. If this can be accomplished, a hacker can then backdoor upload a malicious script to the host server and use LFI to access the script. A simplified version of the process would look something like this:
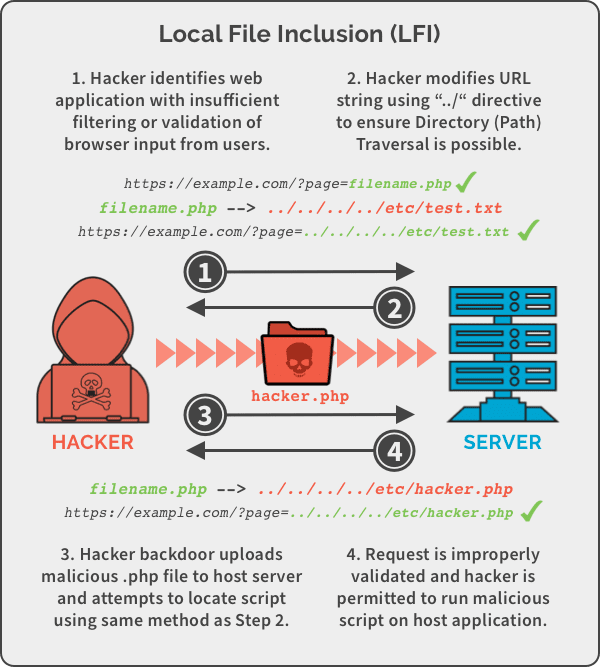
Remote File Inclusion (RFI)
OWASP defines Remote File Inclusion as the process of including remote files by exploiting vulnerable inclusion procedures implemented in the application. This vulnerability occurs, for example, when a page receives, as input, the path to the file that has to be included and this input is not properly sanitized, allowing the external URL to be injected.
Since PHP supports native functions that allow users to include remote files, web applications written in PHP code are more susceptible to RFI attacks.
How Does Remote File Inclusion Work?
While RFI and LFI vulnerabilities are similar, in an RFI attack, the perpetrator can execute malicious code from an external source instead of accessing a file on the local web server, as is the case with an LFI attack.
In Remote File Inclusion attacks, hackers take advantage of the “dynamic file include” command in web applications to upload malicious external files or scripts. When web applications allow user input, such as URL, parameter value, etc., and pass them to the “file include” mechanisms without proper sanitization, perpetrators can manipulate the web application to include remote files with malicious scripts.
Here is a simplified version of what Remote File Inclusion looks like:
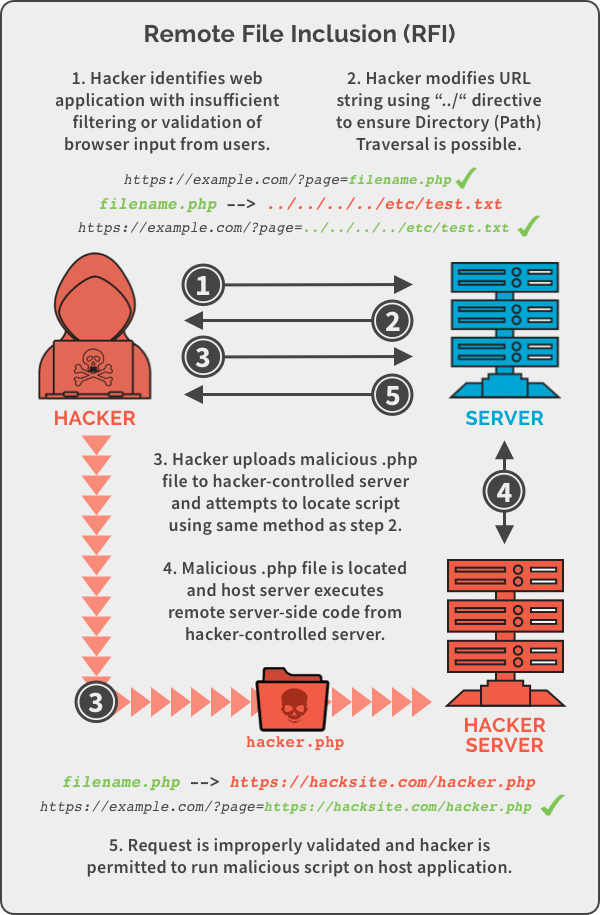
What Can File Inclusion Attacks Lead To?
The consequences of a PHP file inclusion may differ depending on the type of attack. Successful file inclusion attacks may result in information disclosure, XSS, remote code execution and complete compromise of the system.
Protecting Against LFI & RFI Attacks
The main cause for LFI and RFI vulnerabilities is improper input validation; therefore, efforts should be made to ensure the input received is properly sanitized before allowing it to pass to an include function.
Here are a few ways you can protect your web applications from these vulnerabilities.
- Disable the remote inclusion feature by setting the “allow_url_include to 0” in your PHP configuration.
- If circumstances demand that you enable the remote file inclusion feature, ensure that you make a whitelist of accepted filenames and limit the input to only those files on the list.
- Disable the “allow_url_fopen” option to control the ability to open, include or use a remote file.
- Use preset conditions as an alternative to filenames when file inclusion is based on user input.
How to Ensure Business Continuity After a Successful File Inclusion Attack
File inclusion vulnerabilities are a gold mine for cybercriminals who can access your valuable information by leveraging the “include” functionality. While there are several preventative measures to remediate such vulnerabilities, a single successful attack can comprise your mission-critical data and impede business continuity.
Spanning securely backs up your organization’s online data and enables administrators and users to quickly restore data and get back to work in just a few clicks in the event of a cyber incident. This ensures your web-based business never stops, even during a disaster.
If you found this article valuable and informative, don’t forget to check out our previous blog posts in this series, Cross-Site Forgery, SQL Injection (SQLi), and Insecure Direct Object Reference (IDOR) to learn more about web-based application security risks and how you can prevent them from occurring.
*** This is a Security Bloggers Network syndicated blog from Spanning authored by Shyam Oza. Read the original post at: https://spanning.com/blog/file-inclusion-vulnerabilities-lfi-rfi-web-based-application-security-part-9/





