A Guided Threat Hunting Example with LogRhythm CloudAI
Threat hunting is a great way to uncover cyberattacks or malicious activity within your environment, which would otherwise have gone undetected. This post outlines a guided example of a threat hunting process where we will be looking for evidence of account compromise or insider threat activity by examining authentication data.
It is useful for you to think about how such an attack would manifest in log data to help guide your threat hunting activities. For this scenario, we will use LogRhythm CloudAI to get us started and to guide us throughout our hunt.
How LogRhythm CloudAI Can Help with Your Threat Hunting Process
CloudAI is an anomaly-detection engine feature that is an add-on of the LogRhythm NextGen SIEM Platform and provides observation on authentication behaviors. It identifies anomalies by firstly developing a baseline of normal behavior for each user, then by raising observations when the user deviates from that baseline. In other words, CloudAI will tell you when a user does something different to what they have done over the past month.
As the security analyst, it is up to you to interpret the data to determine what these behaviors represent for the user. Some questions to ask yourself throughout your threat-hunting process are:
- Is the data showing anything malicious?
- Is the data showing anything anomalous?
- Can I display the data in a better way to determine this?
It is important to use your knowledge of the environment to determine if there are any contextual anomalies present in the data. In other words, identify anything that looks out of place and determine if it is malicious.
Threat hunting is something you need to do consistently if you want to improve your threat-detection capabilities. The following example should take you about 15 minutes. You should execute this once or twice per day.
Let’s get started!
Step-By-Step Threat Hunting Example
- In the LogRhythm Web Console, start with pulling up the Analyst Dashboard with CloudAI and look at the AIE: Compromise: CloudAI user with risky anomaly widget. This widget shows users with the riskiest CloudAI observations:
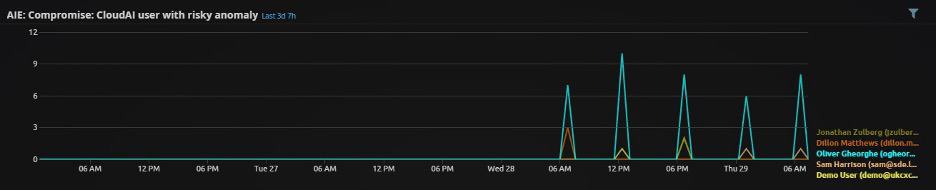
Figure 1: AIE: Compromise: CloudAI user with risky anomaly widget
- Select a user from this widget to perform your threat hunt and run the following search:
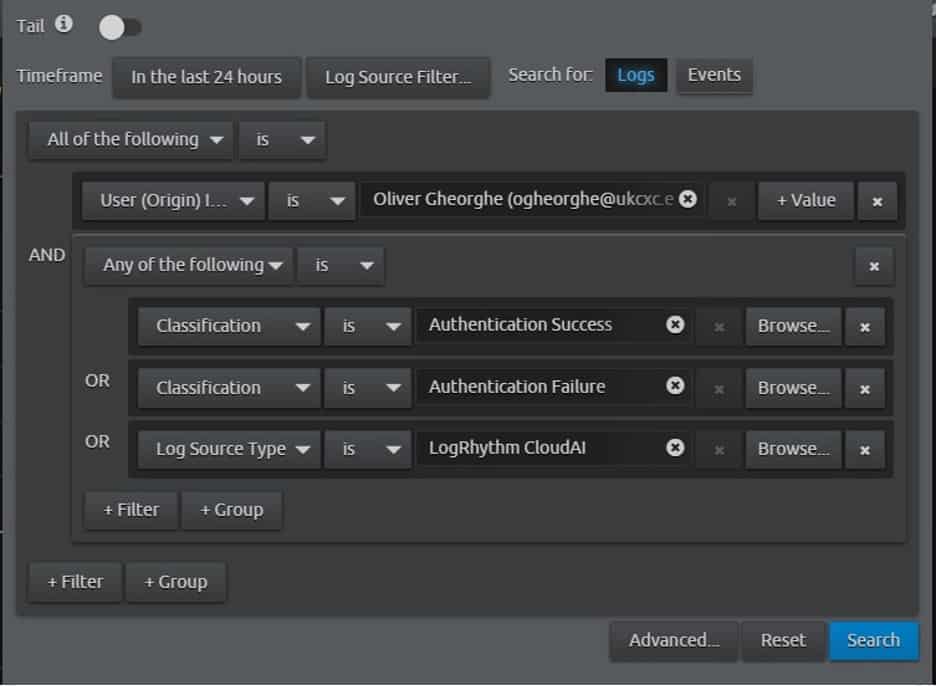
Figure 2: Useful CloudAI search
- View the search results in the CloudAI User Analysis — top behavior risks analyze dashboard. Examine the widgets Anomalies: unusual number of new locations, new origin hosts or new impacted hosts and the Top critical severity MPE CloudAI. This will give you some context to your hunt by showing the types of anomalous observations, and when they occurred:
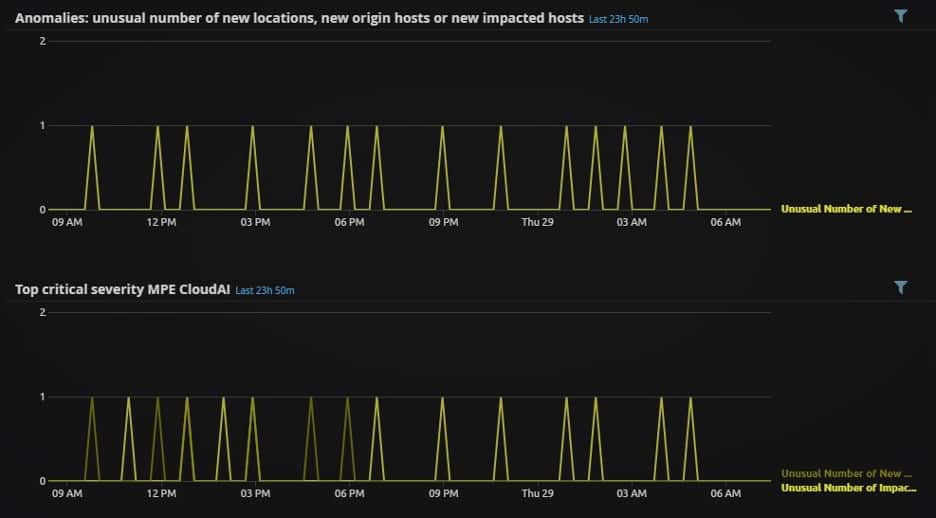
Figure 3: CloudAI anomalies
- Next, examine the widget Top MPE non-CloudAI. Look for any abnormal log types seen at the same times as in the observations above:
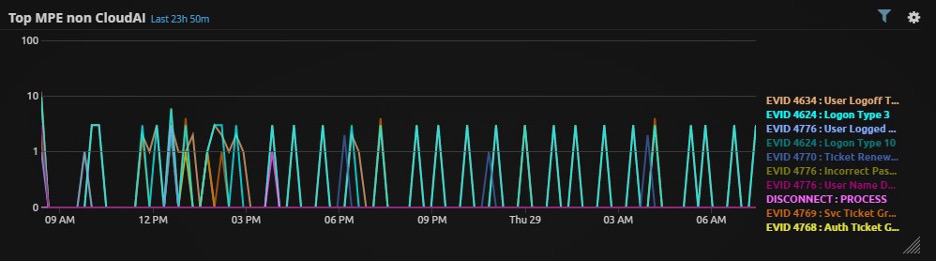
Figure 4: Top MPE non-CloudAI widget
- Scroll further down and examine the widgets Top Origin Hosts and Top Impacted Hosts. Using the context given above, and your knowledge of the environment, evaluate if the user should be logging into or from these hosts at these times. Make sure to lookup any hosts you do not recognize:
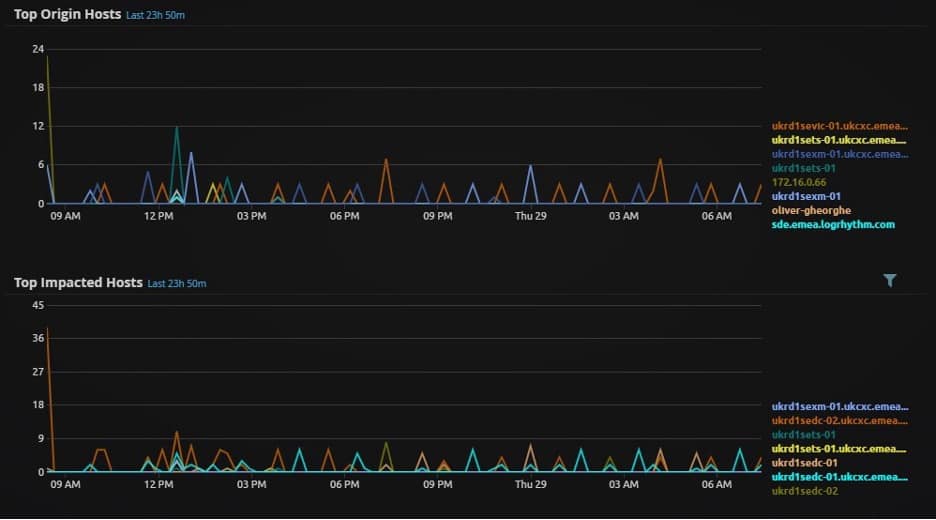
Figure 5: Top origin hosts and top impacted hosts
- Finally, open the CloudAI Heatmap from the LogRhythm Web Console, open the CloudAI tab > CloudAI Lab > Heatmap. Each yellow square in the heatmap represents an anomalous observation and the brightness of the square represents the criticality of that observation.
In the heatmap, search for the user and examine the time of day this user logged into or from each host. Click on each square to look at the details of the observation and decide if this is normal or abnormal behavior for your environment.
The labels should provide further context here. You should also lookup any IP addresses that you do not recognize:
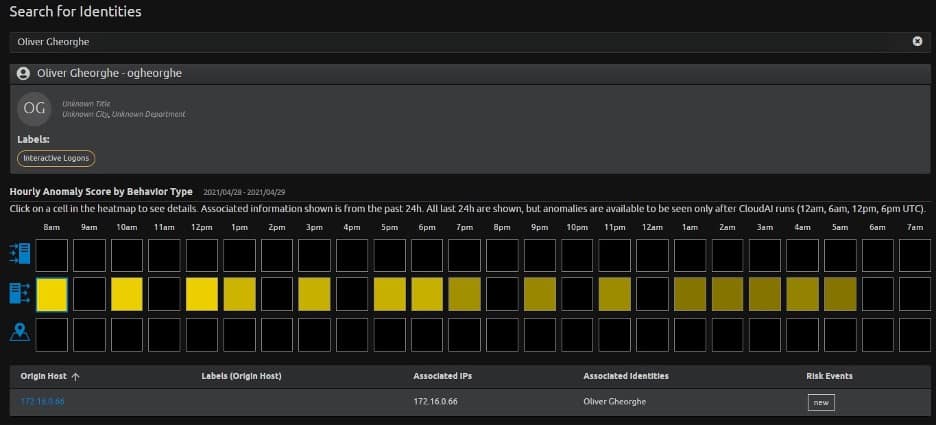
Figure 6: CloudAI heatmap
- If there is nothing immediately obvious or suspicious in any of these steps, perform the same search in Step 2to look at the same user authentication behavior over the past month. Run the same search and set the timeframe as 30 days:
Figure 7: Search timeframe
Here we can see that CloudAI has observed this user logging from an unusually large number of hosts:
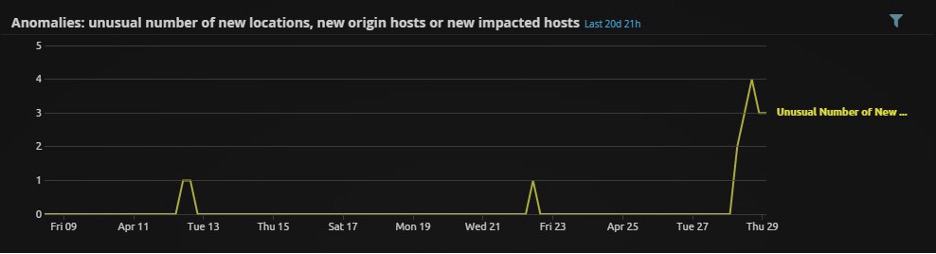
Figure 8: Unusual number of new origin hosts
Scrolling further down, we can see the hosts which this user appears to be authenticating from:
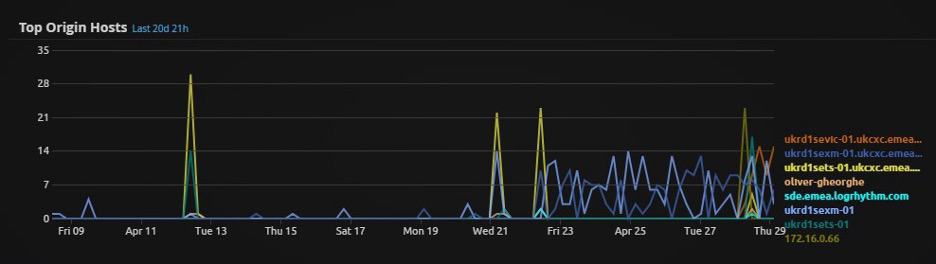
Figure 9: Long-term view of source hosts for this user
- Next, determine if this user should or should not be authenticating from these hosts. This is largely based on your knowledge of the environment. Some further questions to ask are:
-
- What department is this user from?
- What are these hosts?
- What other log data is available from these hosts at those times?
- Should this user be interacting with these hosts at all?
- Could this account be compromised or shared?
- What other log data in my SIEM can help me to confirm this?
- The final step is to document the hunt. There are many ways you can formally do this, but you can start by jotting down some notes as you go. These will help you become a more proficient threat hunter in the future.
This concludes our example of a threat hunting process. In this expedition, LogRhythm CloudAI identified an anomalous user, identified that this user has logged in from a number of new hosts, and then identified those hosts. We then use our knowledge of the environment to decide if this activity should be happening or to take further action.
The AIE rule and dashboards to support this workflow are available to all LogRhythm customers and are on the LogRhythm Community portal. If you are interested in learning more about improving your threat hunting capabilities, download this guide, Threat Hunting 101. It will take you through eight more threat hunting techniques that you can add to your skillset.
The post A Guided Threat Hunting Example with LogRhythm CloudAI appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by Kelsey Gast. Read the original post at: https://logrhythm.com/blog/a-guided-threat-hunting-example-with-logrhythm-cloudai/





