Your Employees Aren’t the Problem; It’s Your Technology

Insider breaches are growing – because you can actually see them
In their annual look at trends in cyber security, Forrester made a few startling revelations.
- 33% of your breaches in 2021 are going to be insider threat related
- Insider threat incidents are expected to grow 8% in 2021
In fact, the #1 cybersecurity concern listed was insider breaches. For those of us that have experienced the implications of an insider breach, this shouldn’t sound too surprising. After all, the increase in remote work naturally leads to increased insider risk. And for those who have cast their security spotlight on external threats, maybe this is a timely wakeup call to look within (quite literally).
I want to go on record with two of my own predictions for 2021.
- We will see a growth in insider threat incidents far beyond 8%, because organizations will invest in tools that give them the context and visibility they need to see them
- The conversation will shift to Insider Risk from Insider Threat, because organizations will realize that not all insider breaches are an outcome of malicious intent (38% of insider breaches are because of employee carelessness)
Download the full Forrester Paper: Predictions 2021: Cyber Security
Not all users are malicious – start there
I want to focus on #2 of my predictions or what I like to call The Accidental Insider. By default, we are all accidental insiders, whether or not we want to admit it. Someone has unknowingly hit “send” on that email containing confidential information, someone has created a publicly accessible link on Box, someone has transported data to another non-trusted source with the intent of getting his or her job done and of course, someone has fallen prey to advanced phishing techniques. Accidents happen and at the root of those accidents are people. For far too long have we been misplacing the problem as a “people” problem versus a “technology” problem.
It’s a Technology Problem, Not a People Problem – context matters
As I often like to point out, the very term “Insider Threat” has a preconceived notion that someone or a group of people are doing bad things. It assumes guilt without providing any context to prove innocence. The end result is someone getting blocked (thank you DLP) for trying to do their jobs or worse yet, fired! If security practitioners have zero context into understanding risk based behaviors, I’m afraid that blame is solely on the technology that allegedly monitors for risk. Because so many legacy solutions like Data Loss Prevention (DLP) have conditioned us to think that it’s enough to classify data, write powerful policies and block users when the world appears to be falling down, we tend to be OK with that approach. After all, a regulatory compliance or a passed audit may mean a restful night of sleep. Or does it? Because what’s absent from that scenario is any attempt to actually solve the problem. To protect your organization from Insider Risk requires understanding the context behind the data, vectors and users that are presenting risk. Without that level of detail, there is simply no way you can take an action. It’s time to stop penalizing the user and start asking the hard questions around technology.
The dawn of a new Insider Risk Management category – created by the shortfalls of DLP
It is my belief that the gaps in DLP have exposed the need for an alternate approach to the problem of data risk. We call that approach Insider Risk Management (IRM). IRM is a data-centric approach to solving the insider problem that doesn’t have a villain picked out before the story even begins. This is an approach that focuses on protecting all data & users from everyday exfiltration risks – no matter their intent. This is an important delineation from insider threat where the viewing field tends to be a lot smaller and restricted.
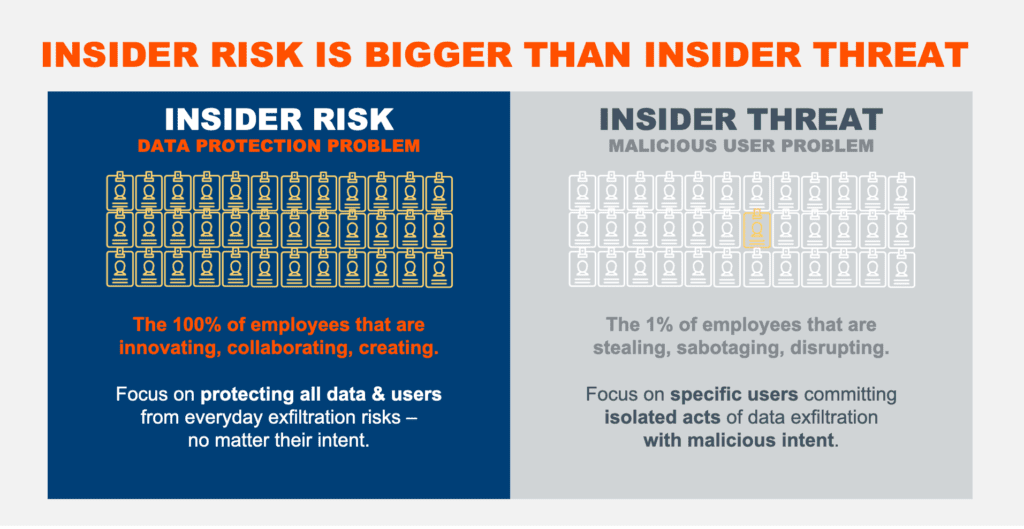
IRM helps security teams bridge the gap between an innovative, collaborative and cloud-based culture and data risk. Unlike old-school approaches like DLP that rely on traditional identify, classify, block methods and disrupt employee productivity, IRM is cloud-native, non-disruptive to employee collaboration and productivity and takes into account all data, all vectors and all users. IRM empowers security teams to reduce data risk exposure and prevent data exfiltration. With an IRM approach, CISOs are armed to secure the collaboration culture, deliver true business value and transform their team – freeing them from the frustrations of policy maintenance to focus on improving the organization’s overall Insider Risk posture and security maturity.
Trust in your employees – and they will in turn protect your data
A disturbing trend of late has been the need to turn insider threat solutions into productivity measurement tools (per the recent Gartner Market Guide for Insider Risk Management Solutions). We’re already in the midst of a pandemic, job uncertainty is looming, and working from home presents enough challenges as it is – is it really the right time to be measuring employee productivity? Maybe if your goal is to build more disgruntled (AKA malicious) users.
Approaching this problem differently starts with empowering employees with the tools they need to succeed, with the training they need to become powerful security allies, and a level of transparency that fosters trust and a commitment to protect an organization’s IP. Sound crazy? If yes, that’s only because we’ve all been brainwashed to think that our users are at the heart of the problem vs antiquated technology. As Jadee Hanson (Code42 CISO & CIO) likes to say “Today, the very nature of classifying and blocking runs counter to the digitally powered cultures that are built for collaborating and sharing. We need a new approach. Now!”
It’s time to hold security companies accountable to not victimize employees!
Recommended Webinar: The Rise of Insider Risk: Why a New Approach is Needed to Protect Data
The post Your Employees Aren’t the Problem; It’s Your Technology appeared first on Code42.
*** This is a Security Bloggers Network syndicated blog from Code42 authored by Abhik Mitra. Read the original post at: https://www.code42.com/blog/your-employees-arent-the-problem-its-your-technology/





