The Risks In Using Third-Party Code
The Risks In Using Third-Party Code
·
Part two of a three part series.
Your Code, Your Problem
Vulnerabilities can be inherited through your software supply chain, and it’s more common than we may like to admit. BlackDuck Software uncovered that 67% of the applications they analyzed contained open source security vulnerabilities.
- Security is a top risk of using third-party code. For some businesses, a crashed service may be a negligible inconvenience. For other businesses, a software outage or unauthorized access can be catastrophic. There are several intangible costs an organization may incur:
- Financial loss. In September 2017, Equifax faced a data breach. Nefarious actors stole customer data, including names, social security numbers, birthdates, and home addresses. Equity research firm, Baird, estimated that at least 143 million customers are affected. The breach was made possible due to a zero-day vulnerability in a popular open source server framework, Apache Struts. In a May 2019 financial earnings call, Equifax disclosed that the cybersecurity incident cost the organization $1.4 billion in incident response and an overhaul of their technology and data security program. This estimate does not include legal costs. Equifax’s Buzz Score — an indication of how negative or positive people feel about a brand — fell 33 points in the first 10 days after the hack was publicized.
- Damaged reputation. During 2013’s peak holiday shopping months, popular retailer Target was breached — 40 million customer credit card accounts, and up to 110 million sets of personal information such as email addresses and phone numbers were stolen. Target is still reeling from the aftermath of its breach. The breach was made possible through stolen HVAC credentials, allowing unauthorized access through across the network and to their POS systems. Thus far, the breach has cost the retailer $61 million. In 2013, Target had a Buzz Score of 20.7. The year following the data breach, Target’s Buzz Score dropped to a shocking 9.4. The retailer has spent the last 5 years recovering its image. While they’ve managed to win back the trust of their loyal customer base, their Buzz Score in 2018 clocked in at 17.3 — 3.4 less than before its breach.
- Threatened public safety. In July 2015, two renowned security researchers Charlie Miller and Chris Valasek demonstrated the remote hacking of a then newly released Jeep Chrysler. Miller and Valasek leveraged a zero-day exploit within the OBD-II connector, allowing access to the car’s CAN bus. Initially, the hack was received with amusement and humor. The windshield wipers violently and unexpectedly swishing back and forth was welcome entertainment for both the viewers and the driver. That is, until the transmission and brakes were disabled, bringing the vehicle to a grinding halt on a South Bend, Indiana highway. Consumers grew concerned over their safety. Since the hack demonstration, 1.4 million Jeep Chryslers have been recalled and fixed to ensure the safety of Fiat Chrysler passengers. The demonstration was a cornerstone for cybersecurity. Adequate cybersecurity measures in automobiles grew to become a market-driven demand.
Free is Never Free
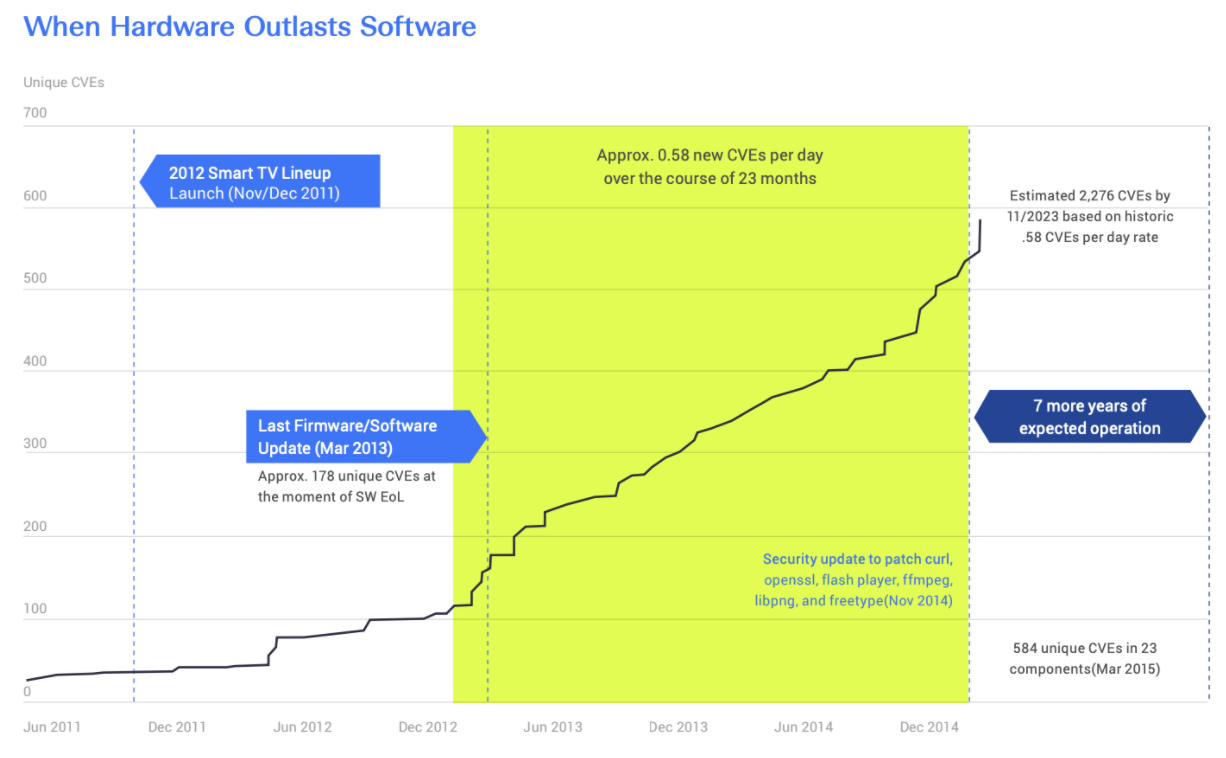
The odds are against us. Since 2014, the National Vulnerability Database (NVD) has reported more than 6,000 new open source vulnerabilities. The Application Security Report from Cybersecurity Ventures predicts that zero-day exploits will rise from one-per-week in 2015 to one-per-day by 2021. At the incredible speed at which new vulnerabilities are disclosed, software that was once secure will inevitably become insecure. Internal research conducted by cybersecurity company, Codenomicon, found that a 2012 smart TV inherited vulnerabilities at a rate of 0.58 CVEs per day over the source of 23 months — from 178 unique vulnerabilities in 2012 to 584 unique CVEs in 23 components in 2015. See graph above.
The key takeaway? Software decays without ongoing maintenance. Akin to proper dental hygiene, continuous testing of third-party code is required for your organization’s security health.
Stay Connected
Subscribe to Updates
By submitting this form, you agree to our
Terms of Use
and acknowledge our
Privacy Statement.
This site is protected by reCAPTCHA and the Google
Privacy Policy
and
Terms of Service
apply.
*** This is a Security Bloggers Network syndicated blog from Latest blog posts authored by Tamulyn Takakura. Read the original post at: https://forallsecure.com/blog/the-risks-in-using-third-party-code