In Retrospect: The SolarWinds Attack
The recently exposed SolarWinds supply chain attack is one of the biggest cybersecurity events in recent memory. It created a ripple effect that will be felt for years to come on a global scale. Third-party security will never be the same again after this mega-breach, which affected some of the biggest Fortune 500 companies and US government entities. Let’s dive into it.

SolarWinds is a Network Management System (NMS) software vendor that gives companies the ability to monitor and examine their networks. This renowned vendor basically fell prey to a software supply-chain attack, where hackers also gained unauthorized access to multiple companies of large stature, the most ironic one probably being FireEye, a leading cybersecurity firm.
What Exactly Happened?
The culprit? Orion. This proprietary software created by SolarWinds is currently helping over 30,000 companies from around the world manage their IT resources and streamline their operations. While details are still murky at this point, all Orion software updates from around March 2020 were already contaminated due to malware that was planted on the SolarWinds servers.
This means that some SolarWinds clients were unknowingly implementing infected software for many months and putting their data at risk. This malicious code, which took months to be detected, created a backdoor to several companies, chosen by the attackers. Some of the potential victims include Microsoft, Cisco, Intel, Deloitte, and even some parts of the Pentagon.
The extent of the data theft caused by the Orion compromise is yet to be determined, but many experts are estimating that it could be 100 million.
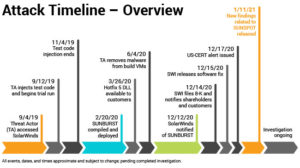
SolarWinds attack timeline. Source: The SolarWinds Blog
The biggest takeaway from this whole incident – Websites providing online services are no different. Third-parties have become an integral part of website ecosystems today due to the time, cost and resource savings that come with their implementation. However, as evident in the SolarWinds case, they also allow hackers to exploit vulnerabilities that are tough to detect.
To understand how broad the risk is, here is another example. Ticketmaster UK was exposed after a third-party chatbot plugin called Inbenta went rogue and was exploited for months. The result – a hefty £ 1.25 million fine by the Information Commissioner’s Office (ICO). Not implementing a layered security approach can damage your business on multiple fronts.
Firstly, your organization bleeds money in real-time, with dev and security teams scrambling to solve the problem. Secondly, there is no knowing why the hackers tried to perform the exploit and what motivated them. How much data has leaked and what happened with it is anyone’s guess. It’s crystal clear that software supply chain attacks and third-party risks can’t be ignored anymore.
Don’t Become The Next SolarWinds
As explained earlier, what happens with software supply-chain attacks is not different from website third-party application attacks. The rapid digitalization of eCommerce, banking, finance, insurance, and eService websites is leading to the massive implementation of sales, marketing, IT, and development third-party solutions. This is creating numerous security risks and regulatory concerns.
Software supply chain attacks, triggered by third-parties (like Orion by SolarWinds), can also happen in your website. Furthermore, unlike the SolarWinds case, your third-parties can be updated and manipulated remotely, making it even more difficult to contain and monitor. Once they go rogue, hackers can access and harvest data for criminal use. Ask Ticketmaster UK.
Learn more about The Cybersecurity Effects of Fourth-Parties
Companies from multiple sectors are encountering a lack of visibility when it comes to their third-party web applications, exposing them to threats created by updates and changes that are out of their jurisdiction. Security teams are having a tough time addressing the security and regulatory risks that are being created due to the lack of visibility into their third and fourth-parties.
The solution? You simply have to consider third-party applications as an integral part of your ecosystem and treat them accordingly from the security standpoint. That means you need to monitor them on an ongoing basis to see if nobody is tinkering with their code and to ensure that they are operating safely. There is also the regulatory aspect you need to adhere to today.
Can SolarWinds happen again? Is your website a third-party initiated software supply chain attack risk? The answer to these questions is YES.
Your Traditional Security Toolbox is Not Enough
Simply put, you have to take care of your security blind spots, just like the ones in the SolarWinds case, which are being created in your third-party ecosystem.
Security blind spots are undetected gaps that take form between your application security processes and the security risks created by third-parties running on your website. Just like the SolarWinds Orion vulnerability opened up thousands of hacking options, the modern website is no different. Traditional security tools are simply incapable of handling the situation.
As per industry estimates, the average website today has over 50 third-party applications running on it at any given time, just like Orion in the SolarWinds case. Even knowing their operational status and performing the occasional risk-assessment is not enough to eliminate the security blind spots they create, which are multiplying due to their dynamic nature.

Third-party apps on websites
To avoid being the next SolarWinds, you need a secure and compliant ecosystem with continuous monitoring of your third-parties, something the traditional tools can’t deliver. The average AppSec toolkit will help you monitor networks, implement security policies, and enforce whitelisting/blacklisting. Traditional tools also primarily provide static outputs, which isn’t enough.
The same applies to third-party risk assessment solutions, which just score vendors and rate risk levels, without doing much on the governance front.
How to Control the Third-Party Apps on Your Website?
The bottom line is clear – third-party applications are providing hackers with a potent way to initiate software supply-chain attacks. With dozens of third-parties already running on the average modern website, the security and compliance risks cannot be ignored anymore. You have to take care of your security blind spots to avoid becoming the next SolarWinds case.
Your third-party application code can contain unrestricted levels of access to sensitive data, all at a browser level. This means that your traditional security tools cannot possibly provide a strong answer to threats that can be escalated via your third-parties. Think JS library vulnerabilities, app backdoors, and other kinds of web-skimming attack variations.
Traditional AppSec tools are still helpful, but only proper ongoing monitoring of critical third-party web applications used on your website can truly secure your website. You can be on top of things by understanding what data is being used by your third-parties, understanding their actions, and discovering previously unknown fourth-party dependencies to connect the dots. Get started now.
Meet Our Experts: Learn how to control your third-party apps and avoid
the next website supply-chain attack
The post In Retrospect: The SolarWinds Attack appeared first on Reflectiz.
*** This is a Security Bloggers Network syndicated blog from Blog – Reflectiz authored by Reflectiz Team. Read the original post at: https://www.reflectiz.com/the-solarwinds-attack/?utm_source=rss&utm_medium=rss&utm_campaign=the-solarwinds-attack





