Home » Security Bloggers Network » Cybereason vs. NetWalker Ransomware
Cybereason vs. NetWalker Ransomware
The NetWalker ransomware has been one of the most notorious ransomware families over the course of the past year, targeting organizations in the US and Europe including several healthcare organizations, despite several known threat actors publicly claiming to abstain from targeting such organizations due to COVID-19.
Key Findings
Worldwide Threat: NetWalker was employed in attacks across a variety of industries around the world, which caused great damage to many organizations.
Encrypting Mapped Drives: NetWalker encrypts shared network drives of adjacent machines on the network.
Double Extortion Operations: The threat actor behind NetWalker threatens to publicly reveal stolen data if payments are not made.
High Severity: The Cybereason Nocturnus Team assesses the threat level as HIGH given the destructive potential of the attacks.
Detected and Prevented: The Cybereason Defense Platform fully detects and prevents the NetWalker ransomware.
Cybereason Blocks NetWalker Ransomware
NetWalker ransomware first surfaced in August of 2019 (first dubbed Mailto). The group behind NetWalker operates a Ransomware-as-a-Service (RaaS) business model, which means they provide their infrastructure, tools and support in exchange for affiliate payment.
NetWalker operators have adopted the recent popular trend among ransomware purveyors:double extortion. In addition to demanding a ransom for the encrypted files, the group behind NetWalker steals sensitive data and files from its victims. The group extorts the victims by threatening to leak the stolen data unless ransom is paid. This technique renders the practice of data backups all but moot in combating the impact from ransomware attacks. Other known ransomware groups that leverage the double extortion paradigm are Maze, REvil, and DoppelPaymer.
The group behind NetWalker also maintains a blog on the Darknet where the group publishes information about its new victims alongside a countdown to the deadline for the ransom to be paid. If the time limit has expired and no ransom has been paid, the stolen data is published to this blog:
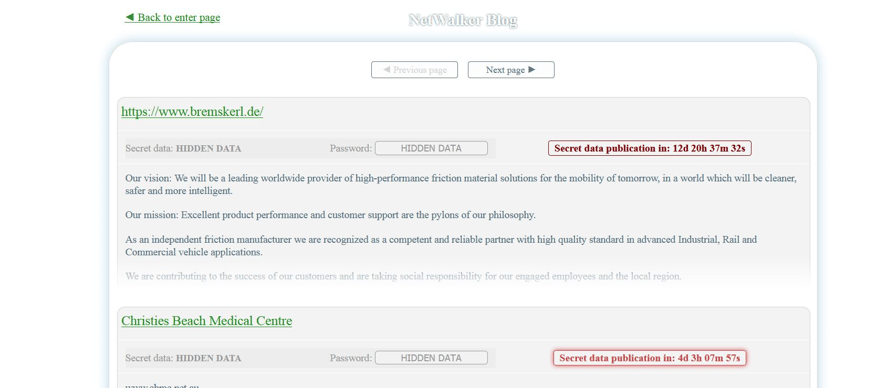
Netwalker Blog
The targets of NetWalker belong to various sectors, among them educational facilities, local government, healthcare providers, and private companies. In June of 2020, three US universities were targeted with the ransomware: the University of California San Francisco, Michigan State University, and Columbia College of Chicago.
Different government facilities were victims of NetWalker in Austria and Argentina in the past year as well. The attackers behind NetWalker do not pass on healthcare facilities as well – it has been reported that NetWalker has attacked Wilmington Surgical Associates and 13GB of data was stolen. Other healthcare facilities have been targeted as well, among them Crozer-Keystone Health System.
Other companies that fell victim include NameSouth, a US-based auto parts distributor, K-Electric, an electricity provider in Pakistan, and Toll Group Deliveries, an Australian transportation and logistics company.
Infection
The NetWalker ransomware has operators have been observed to using several different methods to infect an organization, these including the abuse of COVID-19 topics for phishing mails, weak credentials for Remote Desktop Protocol (RDP), exposed web applications and unpatched VPNs. According to a Federal Bureau of Investigation (FBI) Flash Alert, “two of the most common vulnerabilities exploited by actors using NetWalker are Pulse Secure VPN (CVE-2019-11510) and Telerik UI (CVE-2019-18935).”
For example, Cybereason observed an attack that started with a VBS file was attached to a phishing email with a COVID-19 lure content:
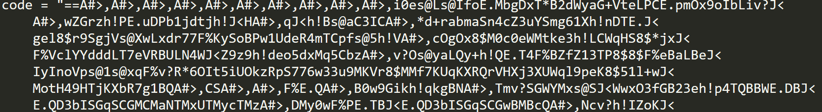
CORONAVIRUS_COVID-19.vbs script
Upon execution, the script will drop the ransomware to “%temp%” and execute NetWalker:
CORONAVIRUS_COVID-19.vbs script deploys NetWalker as seen in Cybereason
In other cases, the ransomware was deployed following an interactive hacking operation using a ported-version of the ransomware payload that was injected to explorer.exe by a PowerShell script:
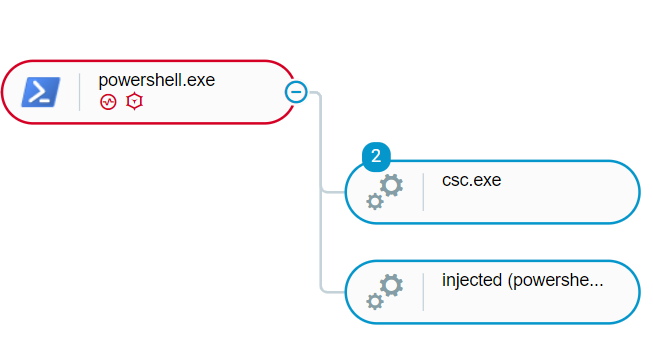
PowerShell payload injects NetWalker as seen in Cybereason
Ransomware Analysis
As a means of evasion, NetWalker does not directly declare its Windows API imported function in the import table. Instead, the ransomware dynamically resolves all of its API as a technique used to make static analysis harder. NetWalker compares a CRC32 hashed value of an API name to the exports of specific modules, then it builds a struct that holds the address of NetWalker’s API:
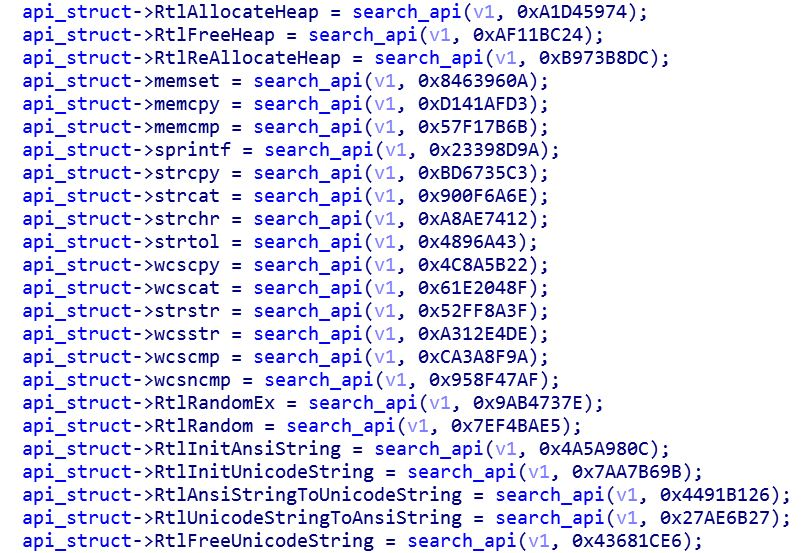
NetWalker dynamically loads API
After resolving the needed API, NetWalker loads the ransomware configuration. The configuration is saved in the ransomware resources and is RC4 encrypted:
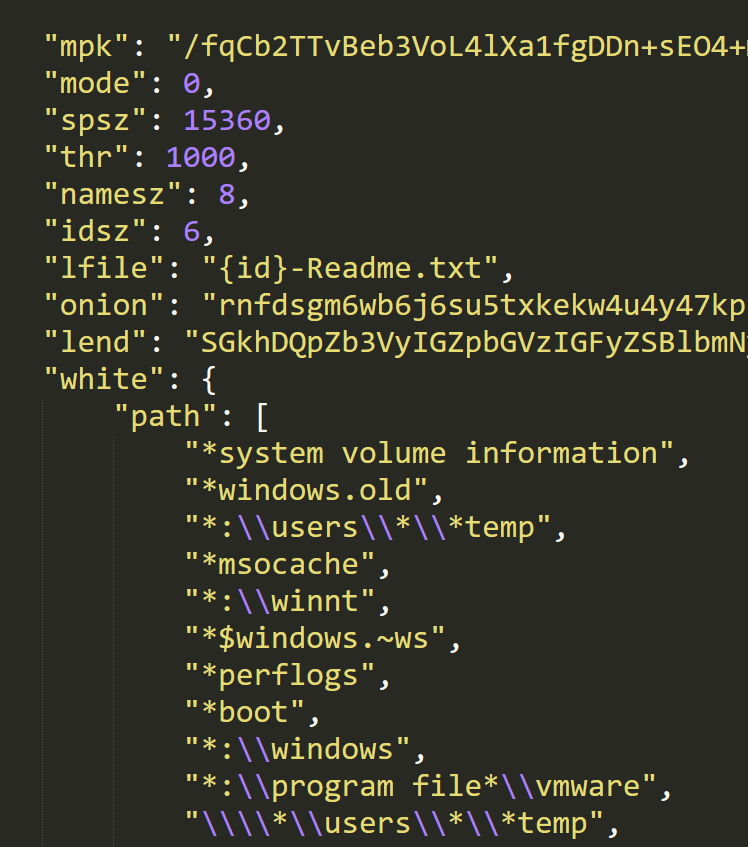
NetWalker configuration file
The configuration file holds the following information:
|
Parameter |
Description |
|
mpk |
Public key |
|
mode |
Encryption mode |
|
spsz |
Encryption chunk size |
|
thr |
Threading limit |
|
namesz |
Length of generated named of persistence executable |
|
idsz |
Length of generated id |
|
lfile |
Template for the ransom file name |
|
onion |
TOR site |
|
lend |
Base64 encoded template of the ransom note |
|
white |
Whitelist of directories, files, and extensions |
|
kill |
Processes and Services to terminate, as well as a task to do after encryption. |
|
net |
Flags for network resources encryption |
|
unlocker |
Exclusion during encryption |
NetWalker Configuration Data
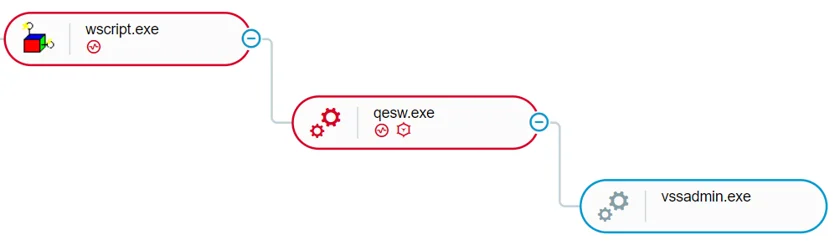
Before encrypting the victim’s files, NetWalker deletes the Windows’ Shadow Copies using the vssadmin.exe delete shadows /all /quiet command. On some variants, the command is spawned by the executable of the ransomware; on others, it is spawned by the PowerShell script which executes NetWalker:
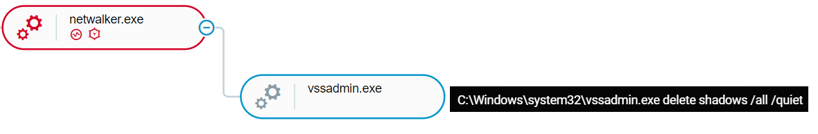
NetWalker deleted shadow copies
Next, the ransomware will start the encryption stage. NetWalker ransomware checks for valid drives in the system using GetLogicalDriveStringsW. For network drives, the ransomware uses ImpersonateLoggedOnUser in an attempt to impersonate the context of the current user in order to access the remote drive. NetWalker then encrypts the files on the network and local drive using Salsa20 encryption. After the files are encrypted, the ransom note is placed.
On some variants, NetWalker also creates persistence via the run registry key and drops a copy of the ransomware to C:Program Filesrandom_generated_namerandom_generated_name.exe’ or ‘C:Program Files (x86)random_generated_namerandom_generated_name.exe’.
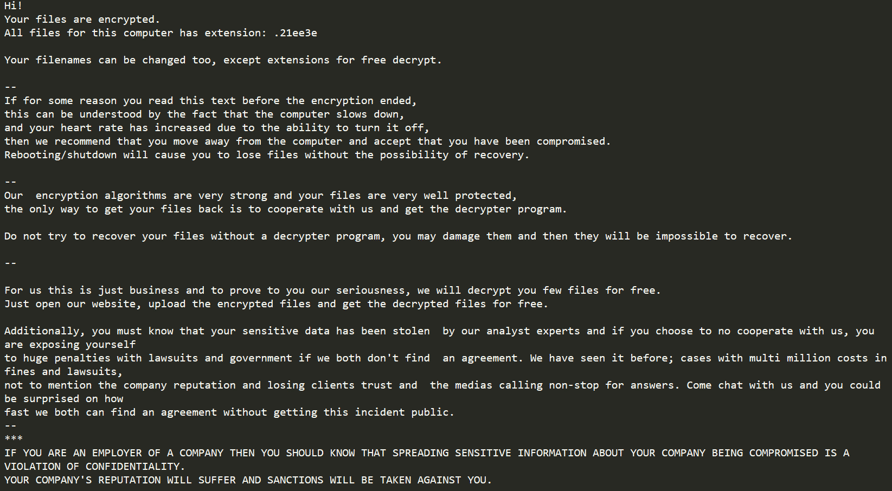
NetWalker ransom note
CYBEREASON DETECTION AND PREVENTION
The Cybereason Defense Platform is able to prevent the execution of NetWalker Ransomware using multi-layer prevention that detects and blocks malware with threat intelligence, machine learning, and Next-Gen AV (NGAV) capabilities. Additionally, when the Anti-Ransomware feature is enabled, behavioral detection techniques in the platform are able to detect and prevent any attempt to encrypt files and generates a MalopTM:
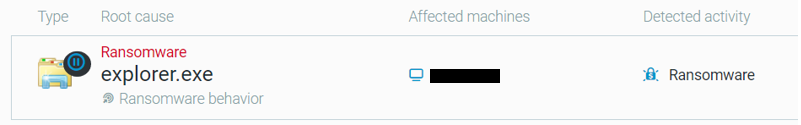 Malop triggered due to the malicious activity
Malop triggered due to the malicious activity
Additionally, using Cybereason’s PowerShell protection feature, Cybereason is able to detect and prevent the initial PowerShell infection stage of NetWalker:
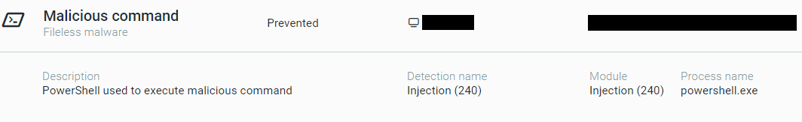
PowerShell protection blocks script which injects NetWalker
MITRE ATT&CK TECHNIQUES
|
Initial Access |
Execution |
Persistence |
Privilege Escalation |
Defense Evasion |
Lateral Movement |
Impact |
|
Access Token Manipulation |
||||||
*** This is a Security Bloggers Network syndicated blog from Blog authored by Tom Fakterman. Read the original post at: https://www.cybereason.com/blog/cybereason-vs.-netwalker-ransomware





