Zero-Day Spear Phishing Attack Targeting Covid-19 Pharmaceuticals—Likely Nation-State Threat Actors
Today, SlashNext Threat Labs observed a flurry of spear-phishing attacks targeting companies at the forefront of Covid-19 vaccines and therapeutics development. These attacks are active, and as of this writing, there are more than 800 spear phishing domains over 60 days that belong to the same threat actors. There is nothing more critical in the age of Covid-19 than finding a cure, and hostile nation-states who cannot develop their own cure would rather steal it.
In all cases, these attacks point to Office 365 log-in pages. These spear-phishing attacks are designed to appear trustworthy. They are targeting specific individuals, in this case, companies that are working on Covid-19 vaccines or therapeutics in an attempt to steal sensitive account credentials. This threat actor chose to launch a flurry of spear-phishing attacks because it’s the most successful form of acquiring confidential information. The impersonated page is virtually identical to the legitimate page and is hosted on a spear-phishing domain.
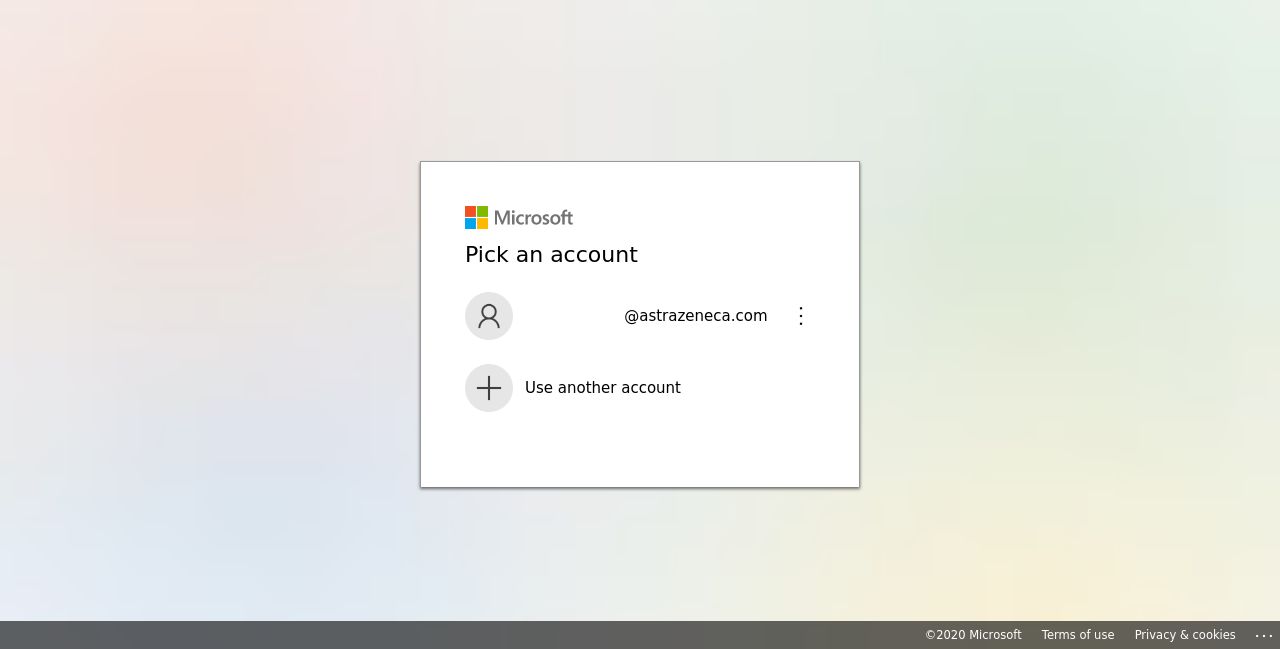
Example: Screenshot of fake Microsoft Office 365 page for AstraZeneca
The following is a list of companies and phishing domains involved in this outbreak.
| Company | Phishing Domain |
| Optum | optum-2989[.]apponline-0238.xyz |
| Gilead Science | gilead-fax16[.]apponline-8473[.]xyz |
| Integrated DNA Technologies | idtdna-fax12[.]apponline-9234[.]xyz |
| Novartis | novartis-fax78[.]apponline-2641[.]xyz |
| Abbott Laboratories | abbott-9196[.]apponline-5673[.]xyz |
| Astrazeneca | astrazeneca-fax34[.]apponline-1424[.]xyz |
| Johnson and Johnson | its-fax83[.]apponline-9234.xyz |
| Pfizer | pfizer-fax80[.]apponline-8473[.]xyz |
| Merck | merckgroup-2585[.]apponline-8473[.]xyz |
Spear phishing attacks are difficult for conventional security defenses to recognize, and in this case, a quick check on VirusTotal showed all of these URLs as clean. These attacks are clearly focused on bypassing the organization’s security defenses to steal intellectual property.
95% of breaches start with successful phishing attacks. It’s not clear if any of the targets in these organizations have been lured into giving their credentials to this threat actor or if a breach has already occurred. If you would like further information on this attack, contact us at [email protected]. Request a risk assessment to see what phishing attacks are getting through your current defenses with our free personalized risk assessment.
The post Zero-Day Spear Phishing Attack Targeting Covid-19 Pharmaceuticals—Likely Nation-State Threat Actors first appeared on SlashNext.
*** This is a Security Bloggers Network syndicated blog from SlashNext authored by Atif Mushtaq. Read the original post at: https://www.slashnext.com/blog/zero-day-spear-phishing-attack-targeting-covid-19-pharmaceuticals-likely-nation-state-threat-actors/





