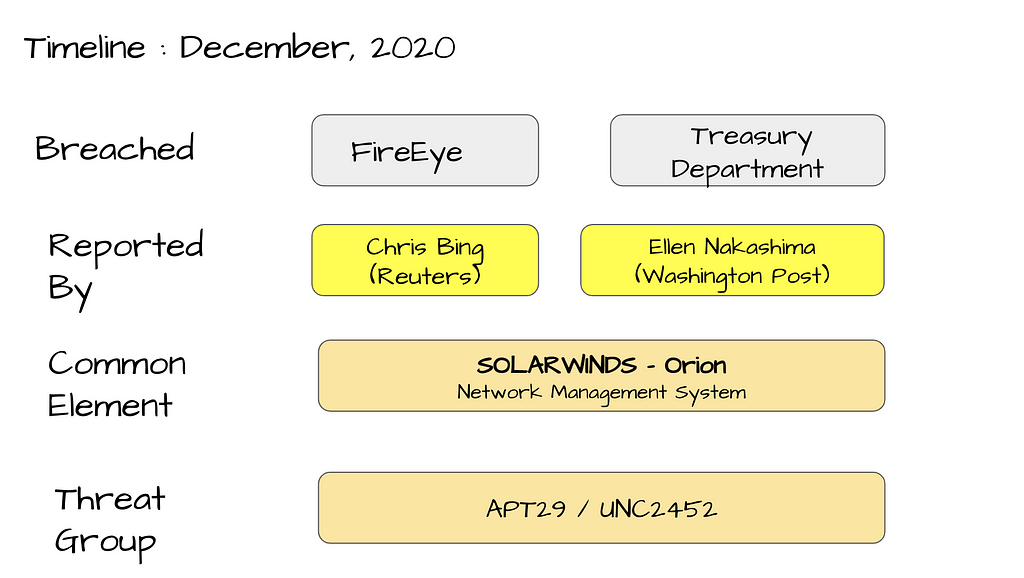
Visual Notes : SolarWinds Supply Chain compromise using SUNBURST backdoor (detected by FireEye)
Visual Notes : SolarWinds Supply Chain compromise using SUNBURST backdoor (detected by FireEye)
First, let me be clear that I have no insider knowledge. This is my best guess at what occurred, based on publicly available information here (FireEye) and others indicated in references section below.
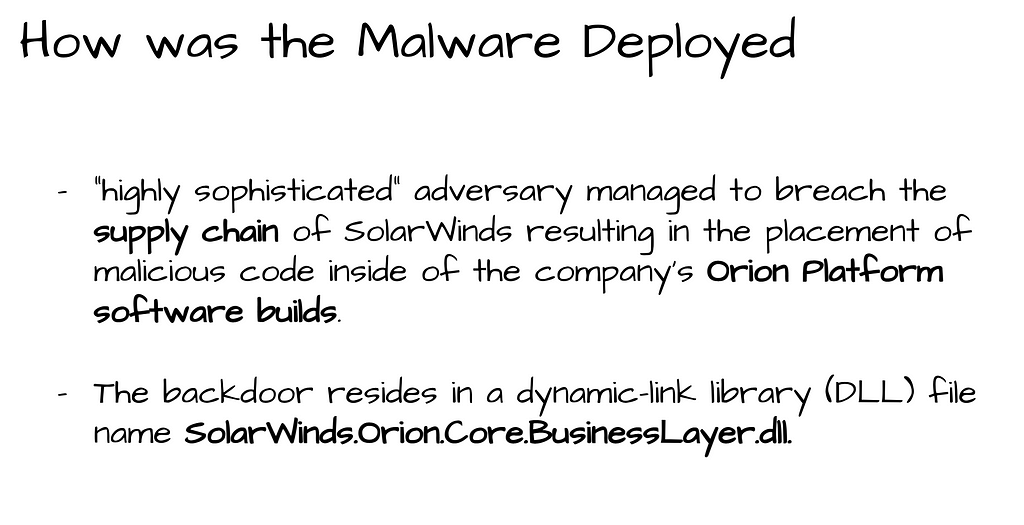
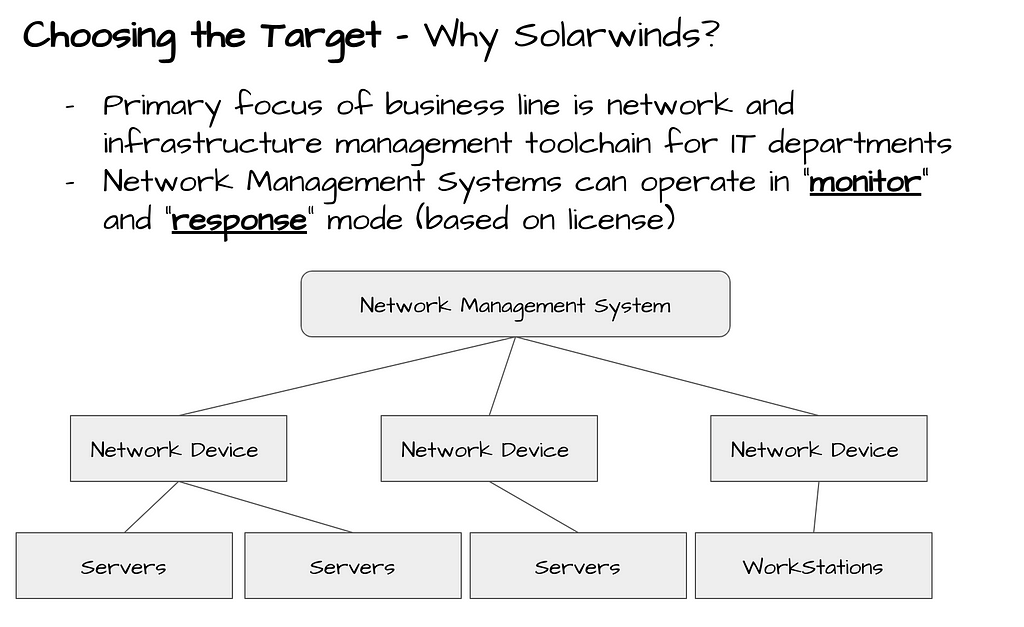
FireEye discovered the supply chain attack that trojanized SolarWinds Orion business software updates in order to distribute malware they call SUNBURST. This report is a must read to understand details associated to this incident.

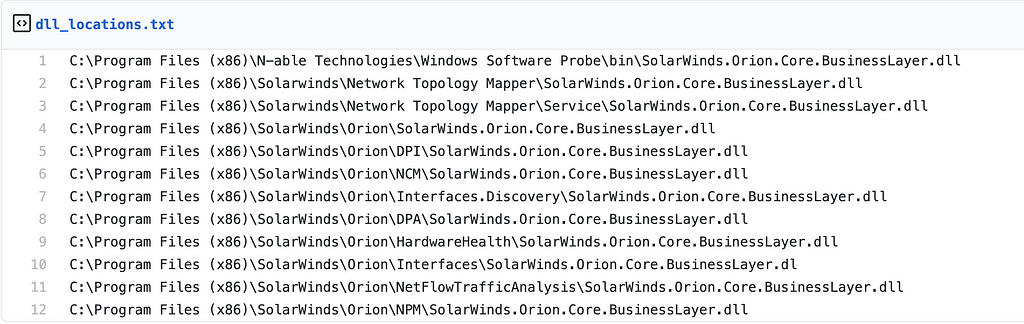
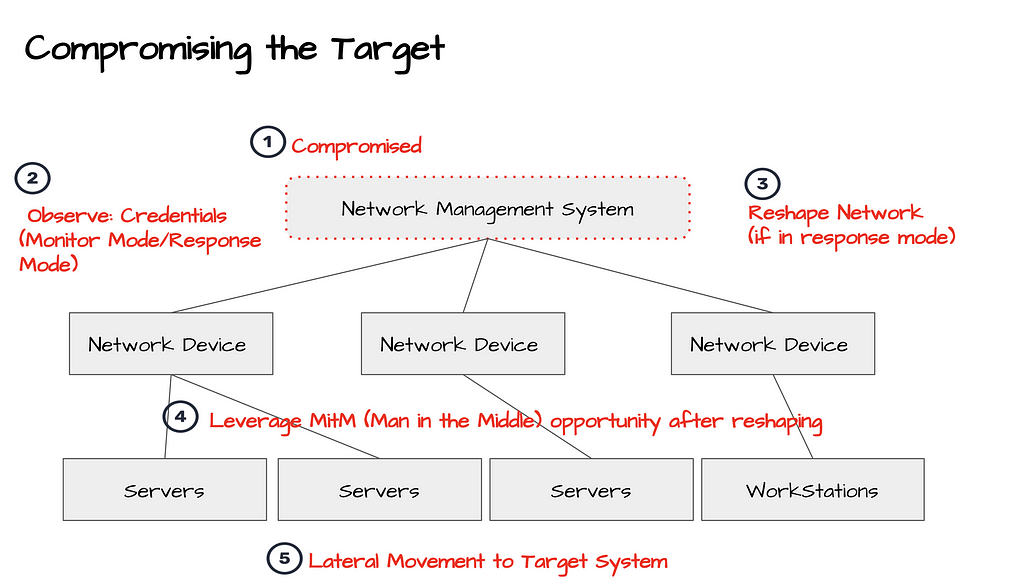
Locations of DLL
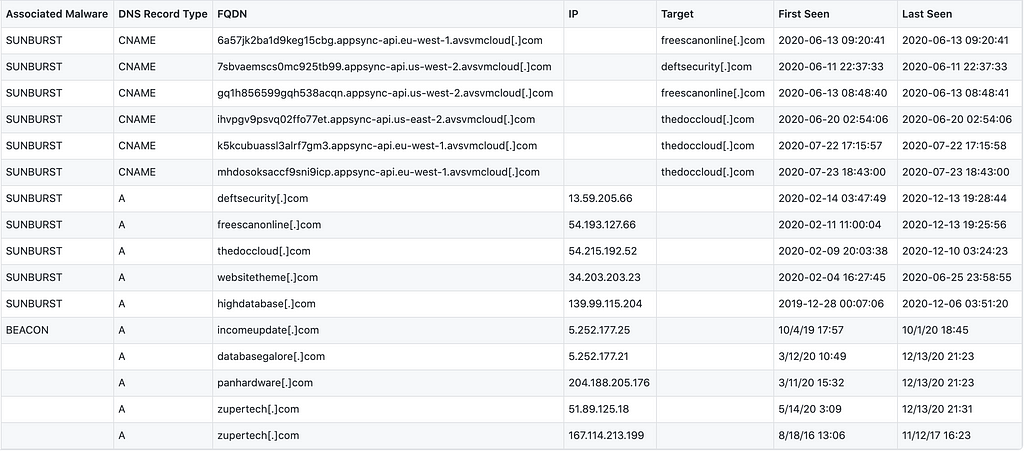
IOC — (Indicator of Compromise) to hunt in DNS logs + full PCAP
- DGA generated C2 Domain : avsvmcloud[.]com
Understanding Domain Generation Algorithms (DGA) - C2 domain for malware to connect to, retrieved via CNAME from DGA-generated C2
freescanonline[.]com
deftsecurity[.]com
thedoccloud[.]com
websitetheme[.]com
highdatabase[.]com
incomeupdate[.]com
databasegalore[.]com
panhardware[.]com
Zupertech[.]com
Virtualdataserver[.]com
digitalcollege[.]org - Malicious DLL (SolarWinds.Orion.Core.BusinessLayer.dll) beacons out to C2 infra (as indicated below) to get additional payloads and commands (backdoor)
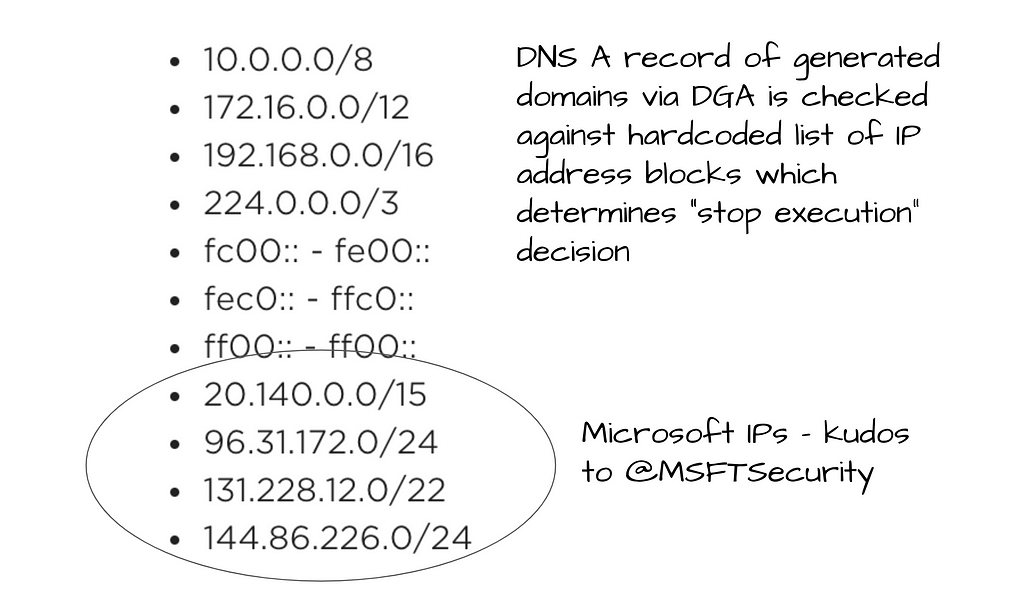
FireEye notes that if the malware resolves the domain to a private IP address, it will not execute.
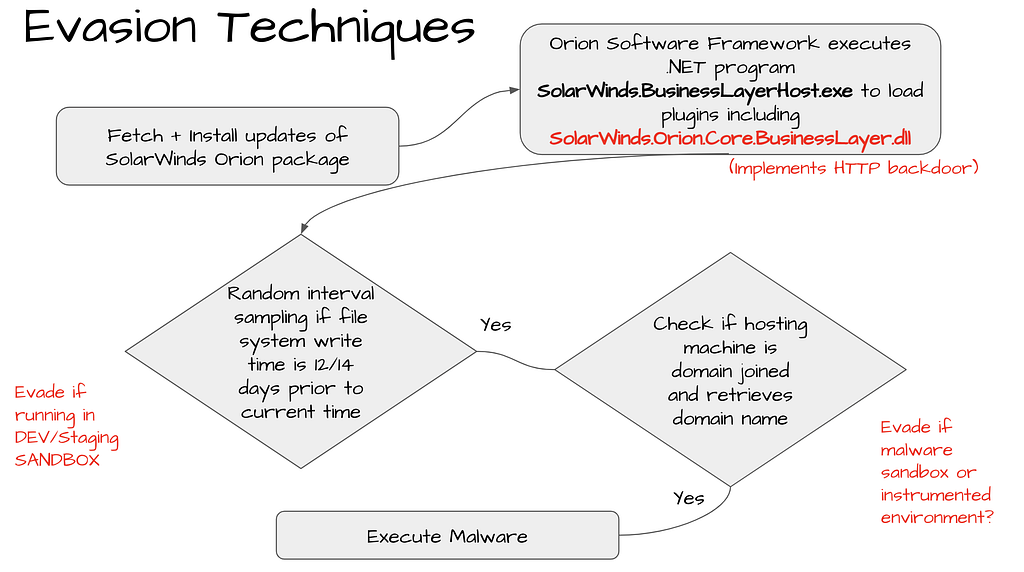
Command data is spread across multiple strings that are disguised as GUID and HEX strings.
References
- FireEye Advisory : https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html
- Jake Williams tweet stream : https://twitter.com/MalwareJake/status/1338641921846239232
- Kyle Hanslovan / DLL Locations https://gist.github.com/KyleHanslovan/0c8a491104cc55d6e4bd9bff7214a99e
- Decompile of the SolarWinds “SUNBURST” Trojan associated with Campaign UNC2452 (for those interested in RE’ing or Static Code Analysis) https://github.com/Shadow0ps/solorigate_sample_source/tree/main
- Play by Play tweet stream analyzing decompiled source code https://twitter.com/Shadow0pz/status/1338616137001693184
Visual Notes : SolarWinds Supply Chain compromise using SUNBURST backdoor (detected by FireEye) was originally published in ShiftLeft Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from ShiftLeft Blog - Medium authored by Chetan Conikee. Read the original post at: https://blog.shiftleft.io/visual-notes-solarwinds-supply-chain-compromise-using-sunburst-backdoor-detected-by-fireeye-561e097fff3c?source=rss----86a4f941c7da---4



