Home » Security Bloggers Network » The 12 Days of Security
The 12 Days of Security
We are all familiar with the (verrrrrry long) holiday favorite 12 Days of Christmas. While security goes WELL beyond 12 days, we wanted to share 12 of our resources to help you in your cyber defense journey this holiday season.
A Weekly Cyber Breakdown
Every week our team uses an AI engine to pull the most relevant cyber articles and resources. These are shared and interacted with actual practitioners and influencers. Top threats, cyber news, scholarship opportunities, cyber events, you name it. It’s all in there. You can find it here on our blog.
2 HolistiCyber Marketing Gals Webinar Series
Our V.P. of Marketing, Nirit Icekson and our Marketing Manager Tricia A. Howard (the two ladies featured in the video at the top of the page) have a mini-series you won’t want to miss. This one is listed as the second day of security because there are currently 2 episodes. Both of them can be found below.
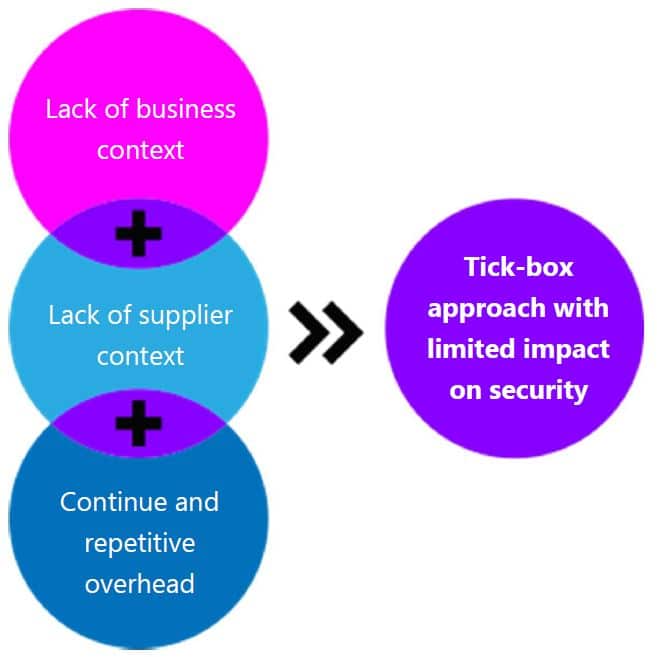
Third Party Risk Management
Alright, we’re stretching the theme here by mixing “three” with “third…” but it’s worth it for this resource. Third Party Risk Management has been a huge discussion this year. The uptick in working from home has increased tech-focused third party usage (*ahem* cloud *ahem*) which means increase in the threat as well. Our whitepaper on Third Party Risk Management unpacks the need for a holistic strategy.
4 Interviews with Nation-State Grade Talent
Our fourth gift is our four best interviews and conference talks with our talent. Since our focus is on nation-state grade talent with real nation-state talent, we figured we’d share some tips on the topic.
5 Golden Memes
This one goes without an explanation. Here are some of our favorite cybersecurity and cyber defense memes.
Previous
Next
6 Top Techniques for Nation-State Grade Cyber Defense
1. Know your attacker
This is why we were founded. Understanding a nation-state attacker’s motivation will help you defend against such. With the recent nation-state attacks this is even more timely. To jump between cybersecurity and actual cyber defense, you have to know the attacker.
2. Exhaust your attacker
We call this the “Green Approach.” If the attack involves too much effort with little to no reward, they will move on. Even if it’s switching up a tactic – something will change. They will either lose interest or you will have time to adjust appropriately.
3. The Violin Analogy
With a surplus of nation-state grade tools being sold on the darknet, there is an increase in this level of sophisticated attack. However, a tool is only as effective as someone who knows how to properly use it. As someone who isn’t proficient in the violin, I can make it make a sound, but a professional could make it make music.
4. Focus on your people
Everyone talks a lot about people, process, and technology. By focusing on the people first in the organization, you will keep your cyber defense plan fresh and scalable. Thinking holistically and involving the other business units will help get new perspectives and reduce blind spots.
5. Prioritize Wisely
Trying to secure everything is equal to securing nothing. Pragmatism is crucial here. Find what is most important (and what an attacker would be looking for) instead of spending your time protecting data that would never be of interest.
6. Be Creative
The attackers succeed because they think outside of the box. We need to have that same approach when it comes to defense. Try some purple teaming or cross-training your defenders to be attackers as well.
7 Cyber Threats for 2021
We talked with our top consultants and pulled together 7 of our biggest predictions of threats for 2021.
1. MSP attacks will be on the rise
Due to the massive and swift jump to cloud thanks to the pandemic, MSPs will most likely be a major threat vector. Corners were cut, things were missed in order to get up and running. As we saw with SolarWinds, the impact can be massive. There will be more to gain for an attacker to hit a telecom than it would to attack businesses individually.
2. Supply chain will be continually targeted
While MSP attacks are part of the supply chain, the entire vector is worth mentioning. Attackers have seen how effective this vector can be and will try to replicate it. Since there are several links that can be broken in the supply chain, attackers have multiple attempt entry points.
3. Finance, Healthcare, and Pharma will be highlighted targets
Thanks to the vaccine rollout and the precedent that ransomware can actually kill, these industries will be on high alert for attackers. Simply put, there’s more to gain from these industries than others moving forward. Finance is always a large target and with the economic status we are in thanks to the pandemic, it will be even more appealing for an attacker to target them.
4. Remote Workers will continue to be an easy target
As people continue to be more exhausted from the long hours and emotional toll of the pandemic, it will be easy to take advantage. We have been living in an almost purely digital world for several months now, and even the most vigilant of employees can fall victim to bad practices or highly targeted attempts.
5. The financial impact of a breach will increase again
As pointed out in the IBM Cost of a Breach Report, remote work increased the average cost of a breach by over $130k. As discussed above, remote work isn’t going anywhere any time soon. On top of that, more companies have decided to standardize on remote work moving forward, which can contribute to the increase.
6. Disinformation will continue to threaten national security
While this might not sound like a cyber threat per se – any media company knows the potential cyber impact of disinformation. Hacktivist groups, nation-state attack groups, and others can absolutely launch a cyber attack based on disinformation. With geopolitical tensions what they are due to the pandemic, this can continue to be a serious threat.
7. Cyber Insurance is a-changing
The cyber insurance industry is about to go through upheaval as their policies are becoming loss making. Cyber insurance could become more difficult to purchase. While this helps alleviate the relying on insurance problem, other things could go to the wayside to qualify for insurance that have nothing to do with actual cyber defense.
8’s Making Headlines
Sometimes headlines in security are a good thing. We were able to be a part of some major publications this year that are packed with cyber defense knowledge. You can find all of them on our News and Events page, but here are two of our favorites.
On the (Virtual) Stage: 10 Events a-Speaking
The show must go on! While COVID-19 decimated the live event schedule, the world was resilient. We brought it onto the virtual stage. We were fortunate enough to be a part of some of the industry’s leading events such as ISMG, CyberTech Global, Apex Assembly and several others. For those of you we met virtually this year, hopefully we can meet in person next year!
Previous
Next
11 Pentest Fixes
Every single consultancy and MSSP out there likes to tout their pentesting abilities. What we see a lot of is compliance check boxing. We pulled together a whitepaper calling out the pentesting industry and how to reframe the way we look at them. You can find that here.
A Baker’s Dozen Industry Reports
Technically, our UK Breach report has 13 industry breakdown, but we’re still counting it. We all know the Verizon Data Breach Report – our Managing Director of EMEA, Peter Cohen pulled together a report specific to the UK which breaks down both cyber and non-cyber threats. It is categorized by industry, so you won’t want to miss that.
We hope you enjoyed our 12 Days of Security. Thank you for being a party of our community and here’s to 2021!
The post The 12 Days of Security appeared first on HolistiCyber.
*** This is a Security Bloggers Network syndicated blog from HolistiCyber authored by Tricia Howard. Read the original post at: https://holisticyber.com/blog/the-12-days-of-security/