Home » Security Bloggers Network » Red Team vs. Blue Team: Discussing the Divide
Red Team vs. Blue Team: Discussing the Divide

Red vs Blue – most people in cybersecurity agree that the gap between the two sides of the industry remains vast. Red-teams work with potent combinations of creativity, training, research, and industry kudos. This is just as well if they are to replicate the kind of attacks seen in the wild. The blue-team on the other hand has been left behind – rarely detecting their red-team colleagues until too late, if at all. This plays out in the real-world too, with average detection times at 200 days after an initial attack takes place.
Why does the Red Team vs. Blue Team divide exist?
There are several factors that combine together in creating this damaging imbalance:
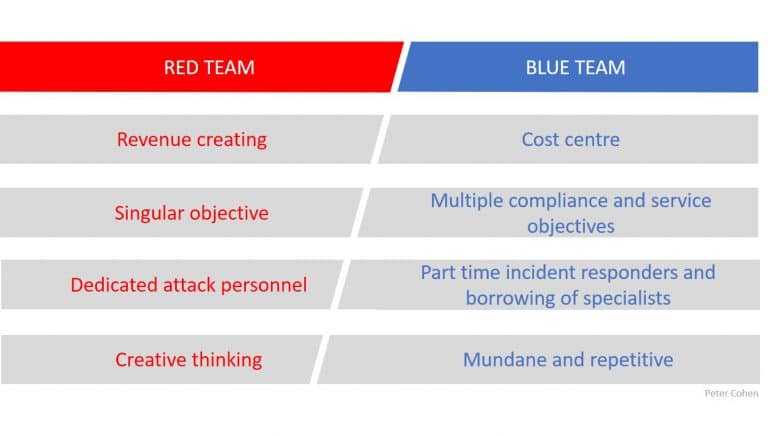
- The red-team is typically revenue creating, which provides opportunities, training, and a quicker route to seniority. When compared with the blue team, who are typically treated as a cost center, are more junior and are often underinvested. It’s clear we aren’t in for a fair fight.
- Many companies outsource their blue team to an MSSP or detection and response service. As these companies scale they often become driven by a compliance and tick-box approach. This is an attempt to drive profit through standardization. Success is measured against a contractual SLA rather than by defending the business. This is in stark contrast to the red-team, whose singular objective – attack and compromise – is very clear.
- Red-teams are comprised of dedicated attack specialists who live and breathe their offensive capabilities and often push the limits of security research. Incident response teams however generally hold several security roles or are outsourced. Most organizations typically can’t cost-justify keeping a dedicated response team in-house. Furthermore, during a live incident, senior decision makers and technical specialists are drafted into the blue-team response team ad-hoc. This again contrasts with the red-team’s ‘always-on’ approach.
- The nature of red-team work drives creativity. It’s a problem-solving exercise with a dash of social engineering, cat-and-mouse, stealth, deep technical expertise and not a small amount of luck. When these combine successfully, the thrill can be unmatched anywhere in the professional arena. Now contrast with the blue-team, where a majority of analysts spend most of their time on mundane and repetitive tasks such as filtering alerts or analyzing logs. This naturally leads quickly to boredom, fatigue, and burnout.
The solution
It’s relatively easy to write an article that merely highlights problems – and there’s enough of those in cybersecurity already. But what about solutions? What can we do, if anything, to solve these issues and actually start to level the playing field?
Team management
Many infosec professionals believe the answer partly lies in how blue-teams are siloed and managed. Indeed, the blue team structure often seen in the industry can be stifling and can create a lack of problem ownership. To overcome this, blue-team management should look to build a creative culture. Break open the old silos of level one / two / three analysts and allow people to take complete ownership of certain aspects of detection and response. Furthermore, there is an opportunity for blue-teams to adopt the excitement and adventure found in red-teams by adopting a purple-teaming approach. This leads to genuine security as well as business benefit. If you want quick wins, they are there to be had simply by keeping people moving. Rotate SOC analysts through other areas of infosec to reduce burnout and further upskill.
People development
Young people joining your blue-team are at the start of their cybersecurity careers and can quickly become disenchanted with the gruelling hours and underinvestment. This is shown in the capability cap and in staff turnover. Ensure your team can see a clear progression pathway. Investing in training and development is key to building an effective team. Too often, firms are reluctant to make these investments for fear that once skilled up, their people will leave. This approach all but guarantees long term systemic failure in defensive measures.
Adopting technology
We need to break the mold in order to progress. This is all well and good, but the next question is ‘how’? Blue-team structures are typically well-established. They can also fall into the category of ‘but we’ve always done it this way,’ making change difficult. This is where technology can come into play. By lifting away some of the repetitiveness associated with the blue-team role, you can allow more focus on human aspects such as making decisions in-line with business context. Many blue-team workloads involve responding to meaningless alerts generated by technology. Instead, challenge the blue team to understand the context of the alert and what it means for the business. This can turbo-charge the tuning for ever-increasing relevance and efficiencies.
Fighting the good fight
So there it is – Red vs Blue remains an unfair fight, and while some progress is being made, it is critical the cybersecurity industry continues to work hard in levelling things up. It’s not an easy challenge. It’s a complex problem requiring change across people, process and technology (and people – again, for emphasis).
Why is this topic so important? Put simply, if we’re unable to defend against ourselves, then we don’t stand much chance against a real-world cyber attack either. There’s too much at stake. The time for change is now.
Interested in red-team blue-team services? You can contact us on the form or on any of our social channels!
The post Red Team vs. Blue Team: Discussing the Divide appeared first on HolistiCyber.
*** This is a Security Bloggers Network syndicated blog from HolistiCyber authored by Tricia Howard. Read the original post at: https://holisticyber.com/blog/red-team-vs-blue-team-discussing-the-divide/





