Extracting Security Products from SUNBURST DNS Beacons
The latest version of our
SunburstDomainDecoder (v1.7)
can be used to reveal which endpoint protection applications that are installed on
trojanized SolarWinds Orion deployments.
The security application info is extracted from DNS queries for “avsvmcloud.com” subdomains,
which is used by SUNBURST as a beacon and C2 channel.
Here’s an example showing that City of Kingston, Ontario, Canada
were running Windows Defender on their trojanized SolarWinds deployment back in June:
SunburstDomainDecoder.exe < uniq-hostnames.txt |
F9A9387F7D252842 on.ca olc62cocacn7u2q22v02eu
F9A9387F7D252842 2020-06-17T00:00:00.0000000Z q94idf4sjbem0rait7gv
F9A9387F7D252842 city.kingston. r1qshoj05ji05ac6eoip02jovt6i2v0c
F9A9387F7D252842 city.kingston.on.ca
The “F9A9387F7D252842” value is the victim’s unique SUNBURST GUID.
See our blog post Reassembling Victim Domain Fragments from SUNBURST DNS
for more info about how the GUID value is encoded into the DNS traffic.
You can also run SunburstDomainDecoder in Linux, with help of
Mono, like this:
mono SunburstDomainDecoder.exe < uniq-hostnames.txt |
76330B4D49BF7EC4 LABELMAR e8fh1ravufms0qpt00gudir2951udivf
76330B4D49BF7EC4 nde5gaefm oiltaoj08jjd8h12vnr4tur5h
76330B4D49BF7EC4 LABELMARKET.ES
The file “uniq-hostnames.txt” is a publicly available SUNBURST passive DNS repository created by Bambenek Consulting.
Time Analysis of SUNBURST Beacons
This bash one-liner indicates that the passive DNS data shared by Bambenek
contains queries posted between April and October 2020.
mono SunburstDomainDecoder.exe < uniq-hostnames.txt |
2020-04-04T06:30:00.0000000Z
The April 4 date here might indicate that this is when the first backdoored installer was released in the wild,
but we only see SUNBURST DNS queries from a single GUID (CB28867A08967B43) on that date.
The second victim doesn’t appear until April 11, with additional victims starting beaconing on April 13, 14 and 15.
The first known SolarWinds Orion update containing the SUNBURST backdoor was
“SolarWinds-Core-v2019.4.5220-Hotfix5.msp” (02af7cec58b9a5da1c542b5a32151ba1),
which was signed on March 24.
This hotfix was released publicly on March 26, according to SolarWind’s
Orion Platform Hotfix Release Notes.
Both these dates are well before April 4, but the SUNBURST code was actually hardcoded not to start until at least 288 hours (12 days)
have passed since the executing assembly was written to disk (it actually picks a random wait interval between 288 and 336 hours).
This means that an organization installing the trojanized Hotfix 5 update, when it was released on March 26,
will not start sending SUNBURST DNS beacons until at least April 7.
Hence the mystery GUID CB28867A08967B43, which was sendng SUNBURST DNS beacons already on April 4, is most likely not a regular SolarWinds customer.
We did unfortunately not find any SUNBURST DNS beacon with an encoded domain name for the mystery CB28867A08967B43 GUID.
Nevertheless, here’s a list of victim GUIDs, with corresponding domain names, that were sent in SUNBURST DNS beacons during April this year:
1B33246AC9917060 tx.org
29964E4A8F627CA1 aerioncorp.com
2EAC3EB75D4B3C8C rp
3247C6644BE3F231 detmir-group.ru
369080B3E59A4EE1 rccf.ru
40A97F7746D6BA4D edg.net
4A2986E3161612C4 gnb.local
4AF99133CB8E23F2 bok.com
59E0EB67DCE7CF9B WASHOE.WCSD
5A107058A310ADEA *TED.co
6776C1C2C729F869 ciena.com
6B740B9519FCAB6B btb.az
72E2D872130A33F8 calsb.org
831DBA83CED9C7D4 uont.com
8D3B008A2532D350 bok.com
92CFB39FA70AF6C5 RCWFactory.local
AA53764C15581A1A pageaz.gov
AFB5B6D3337C8448 LOGOSTECH.NET
B956E216974A17ED rai.com
CA7D468F9242EB3C fortsmithlibrary.org
D9EF8CDC3A72F7FA MOC.local
E6B2E46C5ED604DD christieclinic.com
F5D6AA262381B084 glu.com
Security Product Statistics
It is also possible to use the passive DNS data shared by Bambenek, Joe Słowik and others
to compute statistics of which security products that are popular among SolarWinds’ customers.
| Application | Count |
|---|---|
| Windows Defender | 150 |
| Windows Defender ATP | 1 |
| MS Azure ATP / Defender for Identity | 0 |
| Carbon Black | 21 |
| CrowdStrike Falcon | 25 |
| FireEye | 9 |
| ESET | 32 |
| F-Secure | 0 |
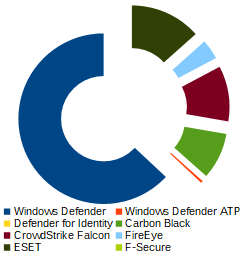
It is worth mentioning that SUNBURST does not report status for several other major endpoint protection vendors, such as Kaspersky, McAfee and Symantec, Sophos and Trend Micro.
Download SunburstDomainDecoder
Our tool SunburstDomainDecoder is released under a Creative Commons CC-BY license,
and can be downloaded here:
You can also read more about SunburstDomainDecoder in our blog post
Reassembling Victim Domain Fragments from SUNBURST DNS.
 Share on Facebook
Share on Facebook  Tweet
Tweet  Submit to reddit.com
Submit to reddit.com
*** This is a Security Bloggers Network syndicated blog from NETRESEC Network Security Blog authored by Erik Hjelmvik. Read the original post at: https://www.netresec.com/?page=Blog&month=2020-12&post=Extracting-Security-Products-from-SUNBURST-DNS-Beacons





