December 2020 Patch Tuesday: A Light Finale to a Heavy Year
Whether it’s because the code is better, or whether the cybersecurity research community is giving the Microsoft guys a break, we only have 58 CVEs to deal with this month. This is roughly half of the CVEs we had last month, and the lowest count in a patch Tuesday we’ve had since January. Of the 58 CVEs, 10 are marked as critical, 2 have moderate-severity exploits, and the rest of them are simply “important”. Not bad eh?
Of the vulnerabilities to note, the remote code execution (RCE) flaws most likely to be exploited soon exist on Exchange and SharePoint. One of the most serious lives in SharePoint (CVE-2020-17118). This vulnerability is an RCE flaw that could allow an attacker to gain unauthorized access to create a site and execute code remotely within the kernel.
“Sharepoint can be used like a watering hole inside large organizations by an attacker. All it takes is for a few weaponized documents to be placed for malicious code to spread across an organization,” said Kevin Breen, Director of Cyber Threat Research at Immersive Labs.
For Exchange, there is CVE-2020-17117, which can be exploited by sending a malicious email, potentially allowing an attacker to run arbitrary code as the “system” user. Microsoft says it’s “less likely” to be exploited in the wild for the time being.
Another CVE patched this month lives in Hyper-V (CVE-2020-17095), Microsoft’s virtualization technology. This flaw is exploitable via a malicious SMB packet, and could allow remote attackers to compromise virtualized sandboxed environments.
All affected software this month:
- Microsoft Windows
- Microsoft Edge (HTML-based)
- ChakraCore
- Microsoft Exchange Server
- Microsoft Office, Office Services & Web apps
- Microsoft Dynamics
- Azure Sphere
- Microsoft Teams
- Azure SDK
- Azure DevOps
- Visual Studio
For more information or to access the security updates, see
https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/2020-Dec
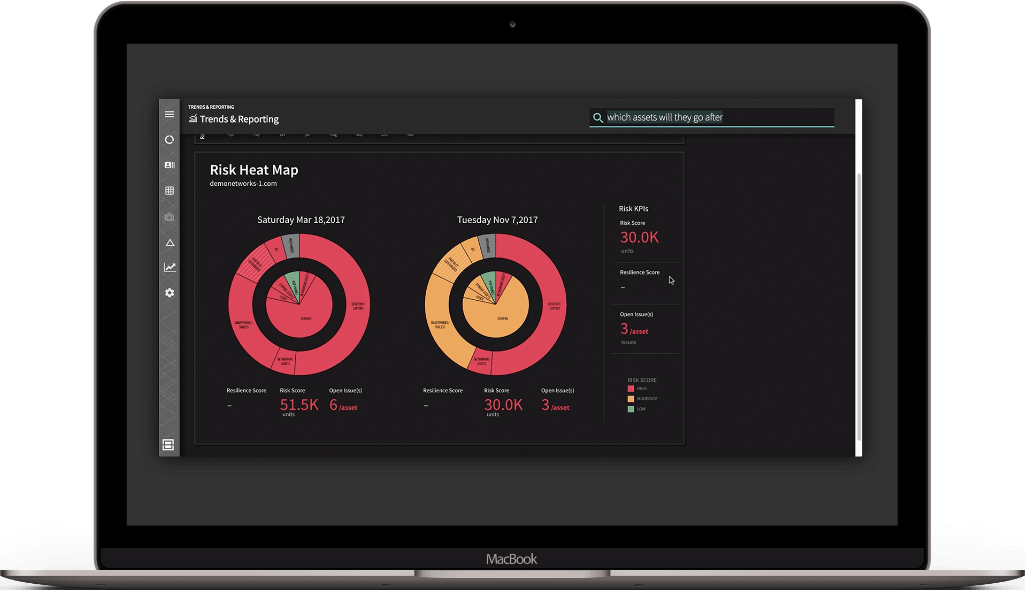
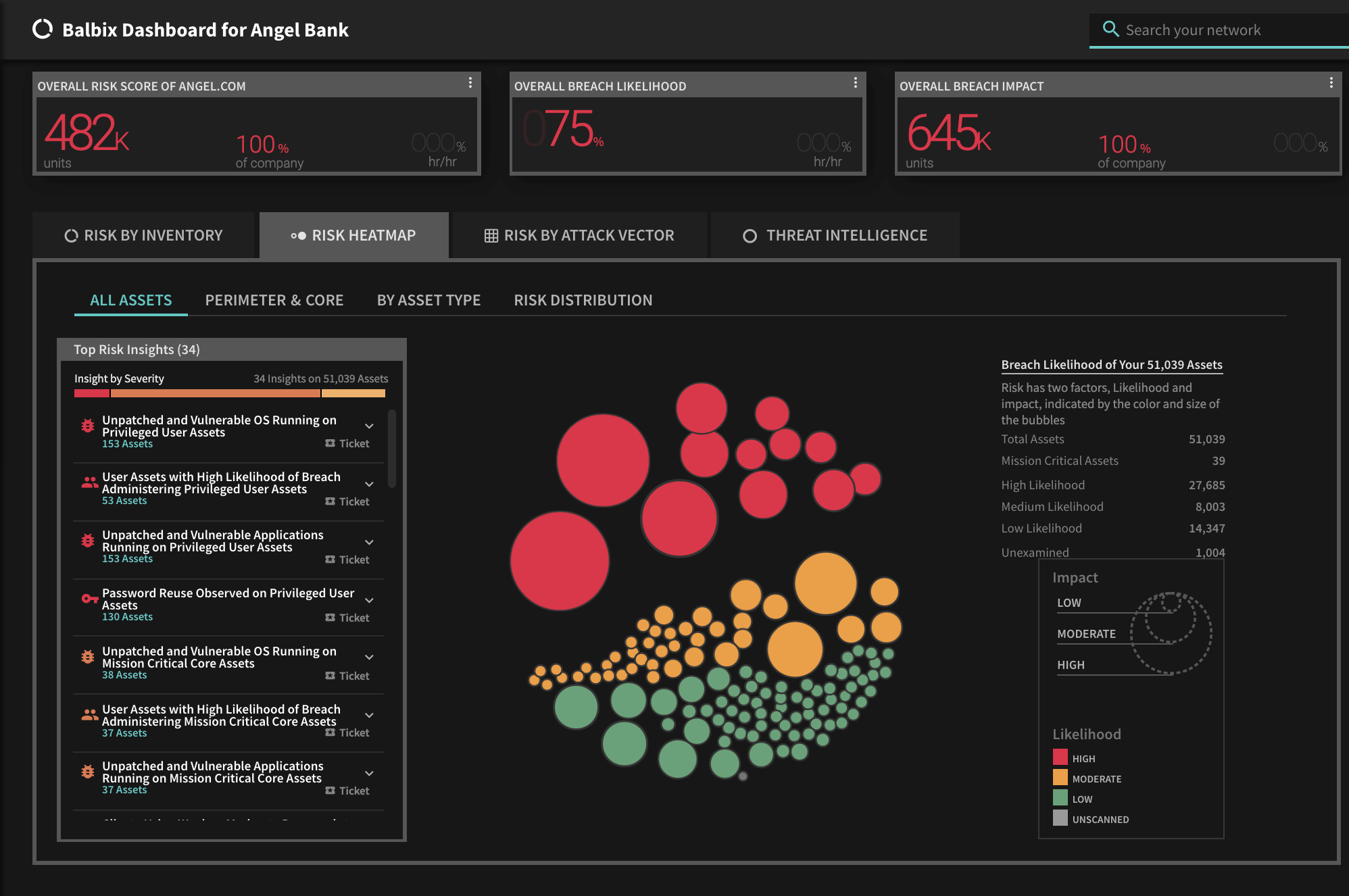
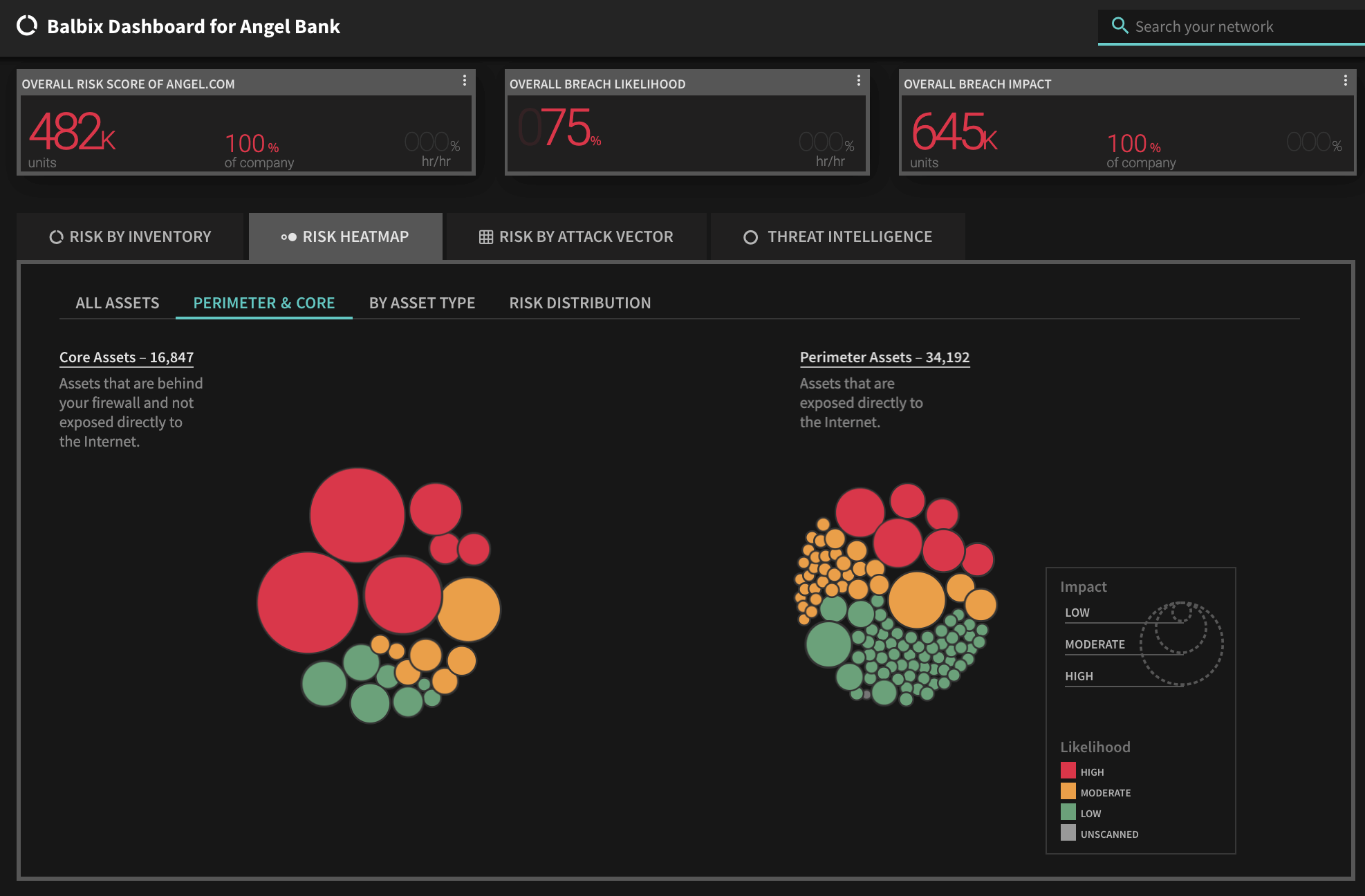
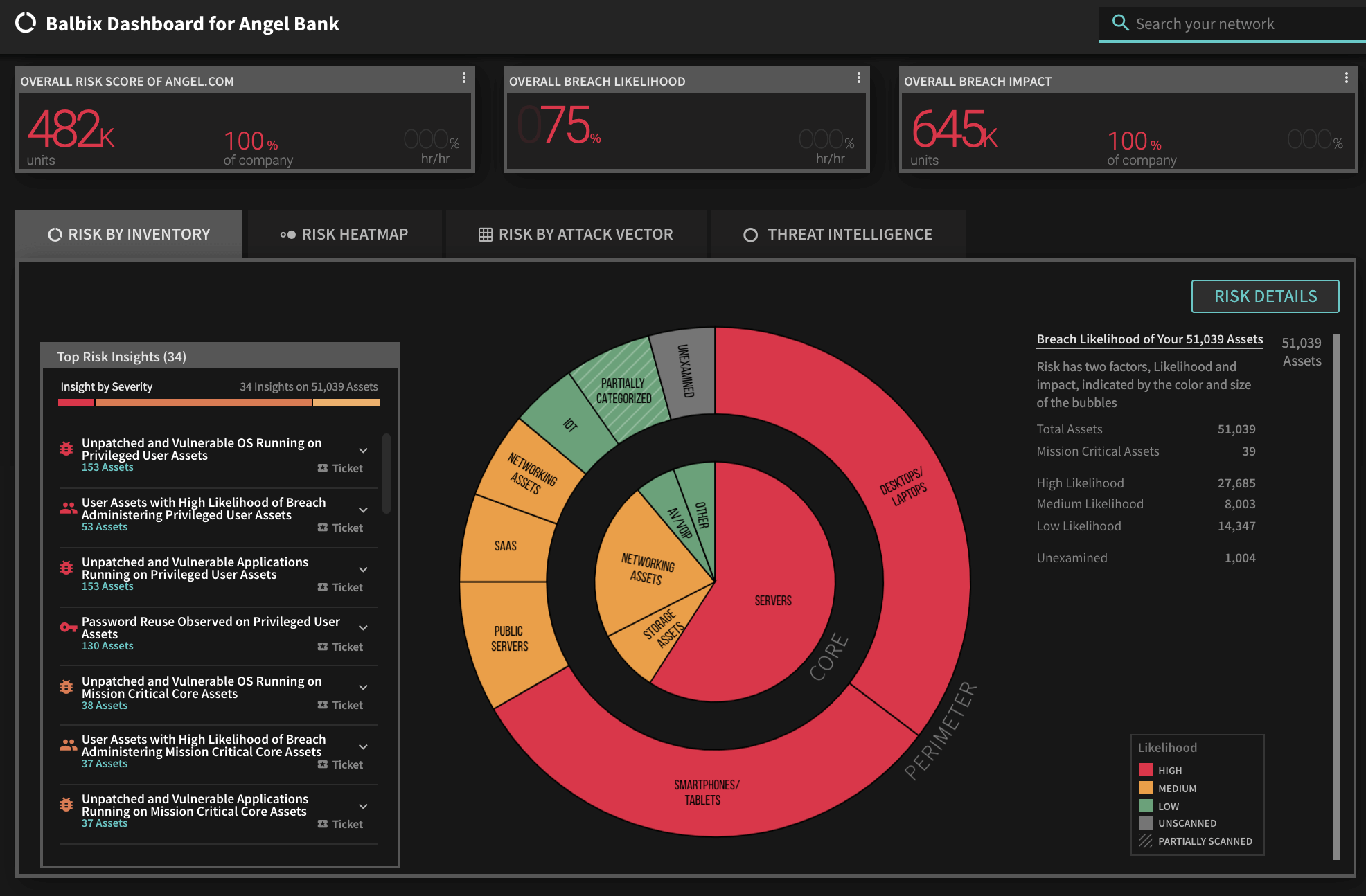
To view the list of affected assets for a specific CVE in your Balbix dashboard:
Enter the CVE in the Search field and hit Enter. Balbix automatically prioritizes the search results for remediation. You can also use the filtered search functionality to search for the CVE by site, subnet, location, or other distinguishing factors.
If you have additional questions, please contact [email protected].
See Balbix Live
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Matt Barrett. Read the original post at: https://www.balbix.com/blog/patch-tuesday-december-2020/





