What is Ransomware and How Do Hackers Target Their Victims?
Ransomware is malware, a form of malicious software, that infects computers, encrypts computer files, and holds computer systems hostage until a fee/ransom is paid to the attacker to regain access to their encrypted network.
In a ransomware attack, the users’ computers are locked by the malicious software for a limited period, after which the amount demanded can keep increasing until eventually the users’ data is destroyed. The ransom is usually demanded in cryptocurrency such as Bitcoin as it allows payments to be made online with perceived anonymity (Frankenfield, 2020).
There are various types of ransomware. Here are few of them that are the most common:
- Scareware, a type of ransomware in which scare tactics and intimidation are used to trick victims into paying ransoms (What is Ransomware? n.d.).
- Screen lockers allow for a full-size window to appear stating that a fine must be paid due to illegal activity detected on the computer, and hence the user gets completely frozen out of their computer.
- Encrypting ransomware another common ransomware where files are encrypted and payment is demanded to decrypt and redeliver those files (Ransomware – What Is It & How to Remove It | Malwarebytes, n.d.).
Due to rapid advancement of digital technology, ransomware attacks have been increasing all around the world in businesses, government agencies, financial institutions, medical institutions as well as other organizations. These cyberattacks are carried out for various reasons such as to breach data (sensitive), to make a social statement , or just for the fun of it (Frankenfield, 2020).
How Do Ransomware Attacks Happen?
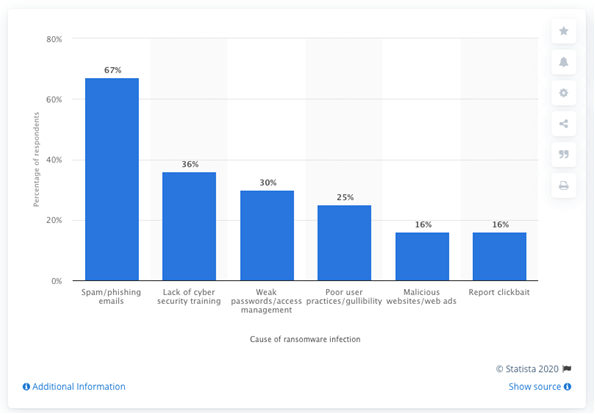
Figure 1 depicts the most common causes of ransomware infections according to MSPs worldwide as of 2019. As seen in this graph, spam/phishing emails is the most common cause of ransomware infections, with 67% of respondents. Phishing emails that have malicious attachments, disguised as a file that can be trusted, and hence leads to the spread of ransomware.
Other common causes of ransomware infections are lack of cyber security training, weak passwords/access management, poor user practices/gullibility, malicious websites/ web ads, and report clickbait. These involve drive-by downloading, where the user visits an infected website unknowingly causing malware to be downloaded and installed without their knowledge (Leading cause of ransomware infection 2019 | Statista, 2019).
Crypto ransomware which involves the encryption of files can also be spread through social media such as instant messaging applications. Moreover, new methods of ransomware infection are being observed such as exploiting vulnerable web servers as an entry point to gain access to an organization’s network (How does a computer become infected with Ransomware? | Information Security Office, n.d.).
What Happens as a Result?
Generally, ransomware can encrypt some or all the victim’s files. Without the mathematical key that is only known by the attackers, these files cannot be decrypted (Fruhlinger, 2020). What is worse is that even after the ransom is payed, it is not guaranteed that the encrypted files will be released. In some cases, the malicious attackers also gain access to the victim’s banking information (FAQ – Ransomware | Information Security Office, n.d.).
Ransomware can target home users as well as businesses, resulting in negative consequences for these victims. As for businesses, these consequences can include the temporary or permanent loss of proprietary or sensitive information, financial losses for the restoration of systems and files, and disruption of regular operations and potential harm to the business’ reputation (Frequently Asked Questions – Ransomware | Information Security Office, n.d.).
In our next blog post, we will discuss options to respond to (and prevent) ransomware attacks.
References
Frankenfield, J., 2020. Ransomware. [online] Investopedia. Available at: <https://www.investopedia.com/terms/r/ransomware.asp> [Accessed 13 September 2020].
Fruhlinger, J., 2020. Ransomware Explained: How It Works and How to Remove It. [online] CSO Online. Available at: <https://www.csoonline.com/article/3236183/what-is-ransomware-how-it-works-and-how-to-remove-it.html> [Accessed 13 September 2020].
Malwarebytes. n.d. Ransomware – What Is It & How to Remove It | Malwarebytes. [online] Available at: <https://www.malwarebytes.com/ransomware/> [Accessed 14 September 2020].
Security.berkeley.edu. n.d. Frequently Asked Questions – Ransomware | Information Security Office. [online] Available at: <https://security.berkeley.edu/faq/ransomware/> [Accessed 13 September 2020].
Security.berkeley.edu. n.d. How Does A Computer Become Infected with Ransomware? | Information Security Office. [online] Available at: <https://security.berkeley.edu/faq/ransomware/how-does-computer-become-infected-ransomware> [Accessed 13 September 2020].
Statista. 2019. Leading Cause of Ransomware Infection 2019 | Statista. [online] Available at: <https://www.statista.com/statistics/700965/leading-cause-of-ransomware-infection/> [Accessed 13 September 2020].
www.kaspersky.com. n.d. What Is Ransomware? [online] Available at: <https://www.kaspersky.com/resource-center/definitions/what-is-ransomware> [Accessed 13 September 2020].
The post What is Ransomware and How Do Hackers Target Their Victims? first appeared on SecureFLO.
*** This is a Security Bloggers Network syndicated blog from SecureFLO authored by Jyotin Gambhir. Read the original post at: https://secureflo.net/2020/10/05/what-is-ransomware-and-how-do-hackers-target-their-victims/





