IBM Integrates Data Security
IBM Security today announced it is adding data security capabilities to IBM Cloud Pak for Security for the first time.
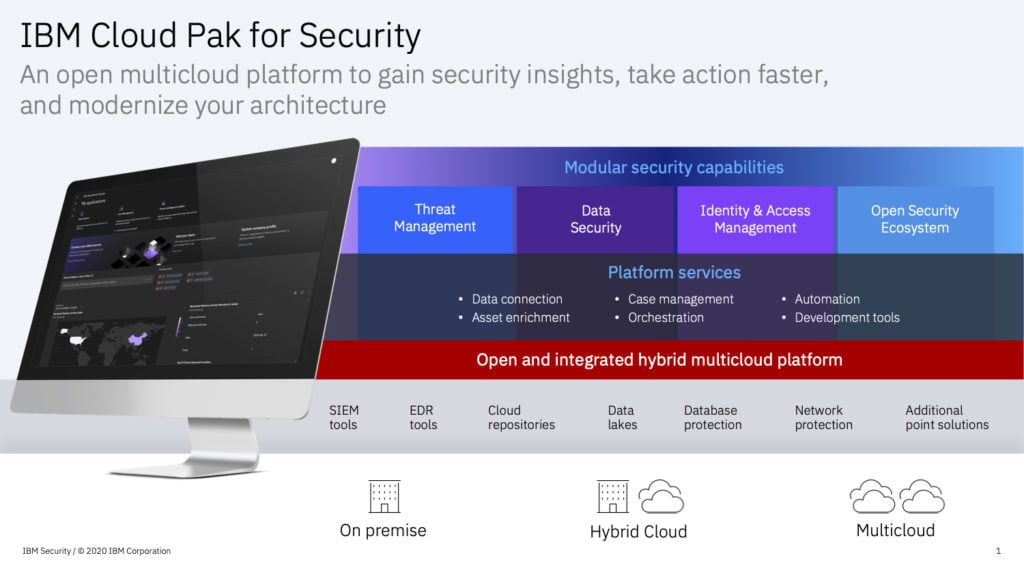
Built on top of the Red Hat OpenShift platform, IBM Cloud Pak for Security is an integrated suite of threat management tools and processes that includes a security information and event monitoring (SIEM) platform, threat intelligence feeds, user behavior analytics based on artificial intelligence (AI) capabilities, a security orchestration, automation and response (SOAR) platform and now a data security hub based on existing IBM Guardium tools for securing databases.
In addition, IBM announced today it is adding support for pre-built integrations with five additional threat intelligence feeds from third-party sources, including AlienVault OTX, Cisco Threatgrid, MaxMind Geolocation, SANS Internet StormCenter and Virustotal alongside its own X-Force Threat Intelligence Feed.
Finally, IBM is also making available a dedicated security services offering to help organizations deploy IBM Cloud Pak for Security.
In total, IBM Cloud Pak for Security will include access to six threat intelligence feeds, 25 pre-built connections to IBM and third-party data sources, and 165 case management integrations based on automation and orchestration playbooks included with the platform. Cloud Pak for Security aligns its threat-hunting capabilities to the MITRE ATT&CK framework and includes technologies such as STIX-Shifter, an open source library that allows security analysts to search for threat indicators across all connected data sources with a single query. IBM gained access to STIX-Shifter as part of its participation in the Open Cybersecurity Alliance, an open source cybersecurity consortium managed by OASIS.
The Red Hat OpenShift platform that IBM relies on to deploy IBM Cloud Pak is based on Kubernetes, which means IBM Cloud Pak for Security can be deployed as a set of containers on any public cloud or on-premises IT environment.
Aarti Borkar, vice president of offering management for IBM Security, said by including the IBM Guardium tools, cybersecurity teams via the same user interface will now be able to secure data more easily at a time when the traditional security architectures based on moats and castle walls has become less effective now that more end users working from home are accessing data directly.
As the network perimeter becomes more porous, security tools that restrict access and encrypt data become the last line of defense, noted Borkar.
Historically, database security has been managed in isolation from network and endpoint security. IBM is betting that as the IT environment becomes more complex, however, data security increasingly will become more integrated with other security processes and functions. That approach should also enable cybersecurity teams to enhance collaboration and reduce the total cost of security by enabling cybersecurity teams to access a portfolio of tools via a common user interface.
It’s not clear to what degree cybersecurity teams are rushing to further integrate cybersecurity processes. However, these processes become more automated with each passing day. That is critical as the attack surface that needs to be defended continues to expand at a time when cybersecurity teams themselves remain shorthanded as ever.