Encryption Requirements Driven by Data State
Have you ever had that feeling that something is amiss? While conducting research on when data encryption is required, I noticed something that seemed a little off. It is commonplace for regulations to require measures be taken to protect data. Many regulations recommend encryption to protect data as it exists in specific states. Encryption is a “safe harbor” that limits a company’s liability following a data breach, provided there is proof the data was encrypted. That is clear and makes sense.
Of ordinances that specifically call out encryption, a few such as Gramm-Leach-Bliley and New York’s Cybersecurity Requirements for Financial Services Companies convey that companies should encrypt data “in transit over external networks and at rest.” A review of regulations finds that when data states are mentioned, only data “at rest” and “in motion” are identified. Strikingly, they fail to mention the third stage of data—“data in use.” With no government standard nor industry documents referencing this phase, does it mean data in use does not require regulation? Looking at these regulations further, they also fail to define when data is in a specific state. While data in transit or data at rest may seem obvious, there are several nuances to consider.
States of Data
Anyone who handles data and is concerned about protecting it would argue there are three stages, not just two. While there is a good understating of what constitutes data in motion and believe they know what data at rest covers, when considering what data in use actually means, the lines between the three states are less obvious. Adding data in use to the equation creates ambiguity as to where the dividing line is between rest and use.
Many define data at rest as a static and stable data state that is passively stored on a device or data storage medium. Resting data is assumed to be inactive, not being actively modified or altered.
- Data at rest can exist in both powered on and powered off instances.
- Data in use on the other hand exists when a system is powered and resides within a system’s volatile memory.
- Data in use will be in a constant state of change, as it is utilized by one or more applications that are reading, modifying or processing the data for a specific task.
Is There a Question?
It is generally clear when data is in motion, but the line between when data is resting and when it is in use leads to some debate. The ambiguity as to which state data exists in at any given moment occurs along the margin between rest and use. The confusion occurs when data at rest is specifically accessible to the system (see figure 1).
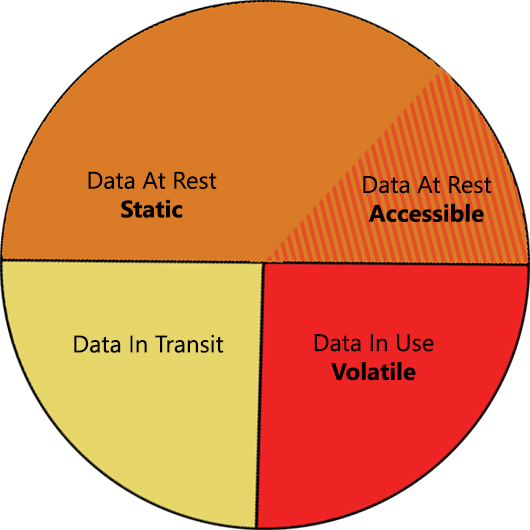
While some argue that if the data is not being actively read or processed it should be considered fully at rest regardless of whether the data store is available. Furthermore, data at rest only transitions to an active state when it is specifically called by an application and moved into some form of volatile storage. Others contend that when a device is powered on, the data is theoretically available. The ability to retrieve data from a local data storage medium or network-attached storage or cloud repository leads some to argue that this availability alters the state from rest to use.
One accessible data space that creates vagueness is data sitting on network-attached storage. Stored data made available to a remote user using a file-sharing protocol may result in a data state change. When files are accessible, some contend they are being used and thus no longer considered to be at rest. Alternatively, the other camp contends that a specific file remains at rest until it is specifically opened. Another illustration is a database associated with a website—dynamic queries of the database result in multiple data states. Since an application is requesting the data, it would now be in use; however, the data is only accessed intermittently, so during those downtimes, it transitions to data at rest.
As illustrated, data states are dynamic and incredibly nuanced and lead to a debate on how exactly to classify. What seemed to be a clear-cut determination has evolved into something that administrators, analysts and executives struggle with: data state dependent on a point of view. For obvious reasons, this can have considerable impact on your security posture.
This is Important Because …
Understanding the state of your data is critical to your overall data protection strategy. Information security is paramount and safeguarding data requires understanding the different states data occupies and how data transitions between modes. Knowing how and when data is traveling, being processed and stored allows for a better understanding of the protection required. Not properly classifying the data state results in a less-than-optimal security technique. There is also the consideration that the company could be open to compliance violations. A worse outcome is leaving the data exposed to malware, ransomware or bad actors operating remote attacks.
Most data occupies the at rest state, be it completely static or accessible. Due to the Natural Law of Digital Data, it becomes imperative that critically valuable and sensitive data be encrypted except when it is expressly required for use. Full-disk encryption is extremely effective at protecting data when a device is powered down. In a powered-on state, it is unable to provide active, granular, file-level protection after a user is logged in to their system. The act of entering the password or passphrase during boot-up grants permission to the system to decrypt any file that’s requested until the computer is turned off again. As a result, files are fully accessible. This is the same for other types of storage-level encryption systems that automatically decrypt when a user authenticates to the system. The encryption is no longer active and thus ineffective to immediate attacks.
For this reason, regulations should go further in their efforts to dictate the parameters of what defines data states. If a solution encrypts data at rest using an automated authentication process such as powering up a device, is it really encrypting data at rest any longer? Adequately protecting information and adhering to mandates as the regulators intended requires solutions built to protect data in the appropriate state.



