Guide to Evaluating Your Container Security Maturity
As companies embrace containerized, cloud-native applications, they recognize that the need for security is as paramount as ever but struggle to secure these new technologies. Since everyone is learning the new stack, no one has a roadmap for how to apply security across the various stages of the containerization journey.
Each stage introduces novel security challenges, and organizations must learn both the infrastructure and the security at the same time. Understandably, security needs evolve as companies move from developing their first containerized application to doing all new development in containers and managing thousands of microservices. Our maturity model – summarized in the image below – can help organizations understand and successfully meet the security challenges that go along with adopting and expanding the use of containerized applications.
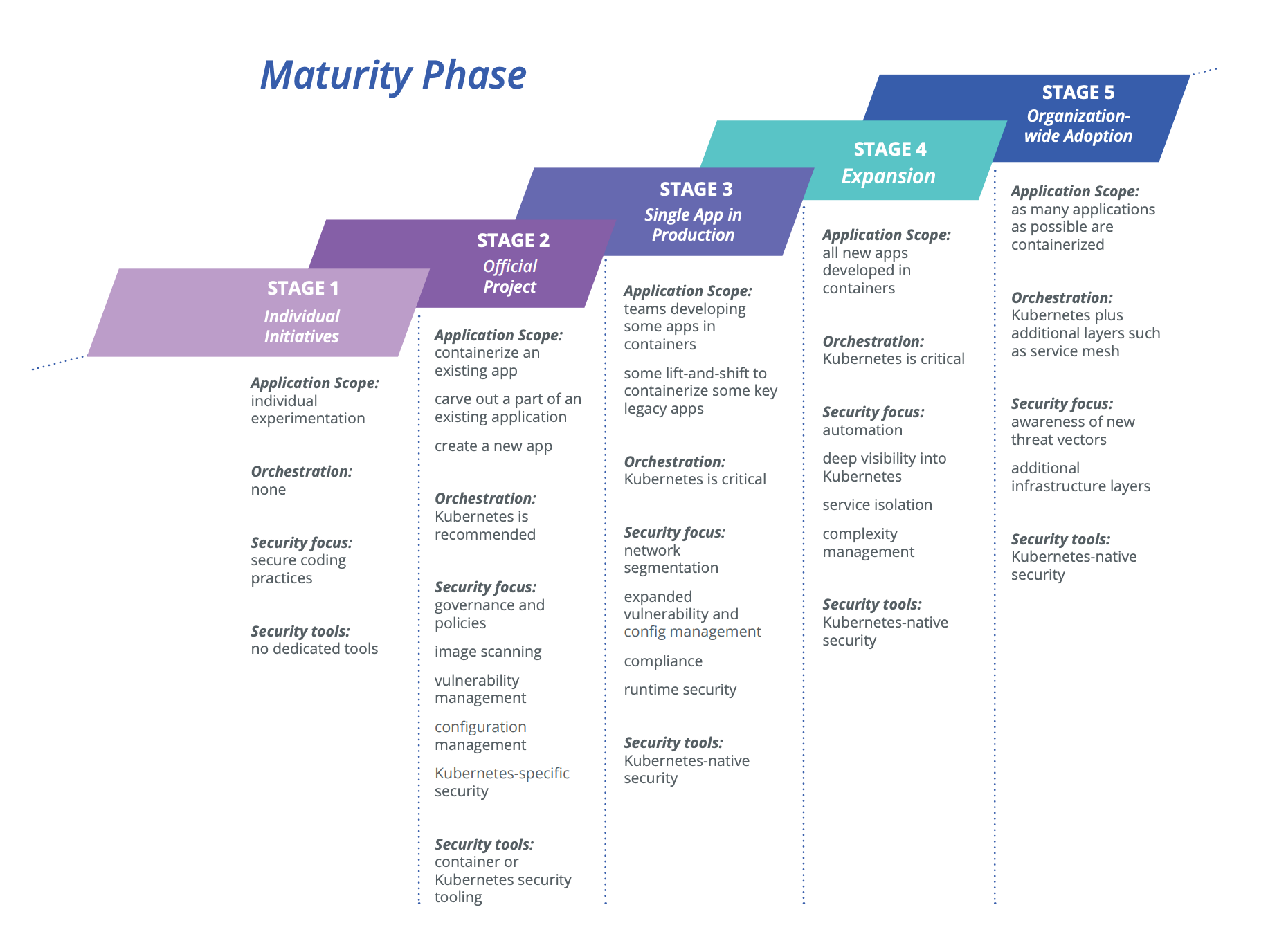
Download the full Container Security Maturity Model
A deep dive into your container security needs across different stages of your container adoption journey
What’s at Stake
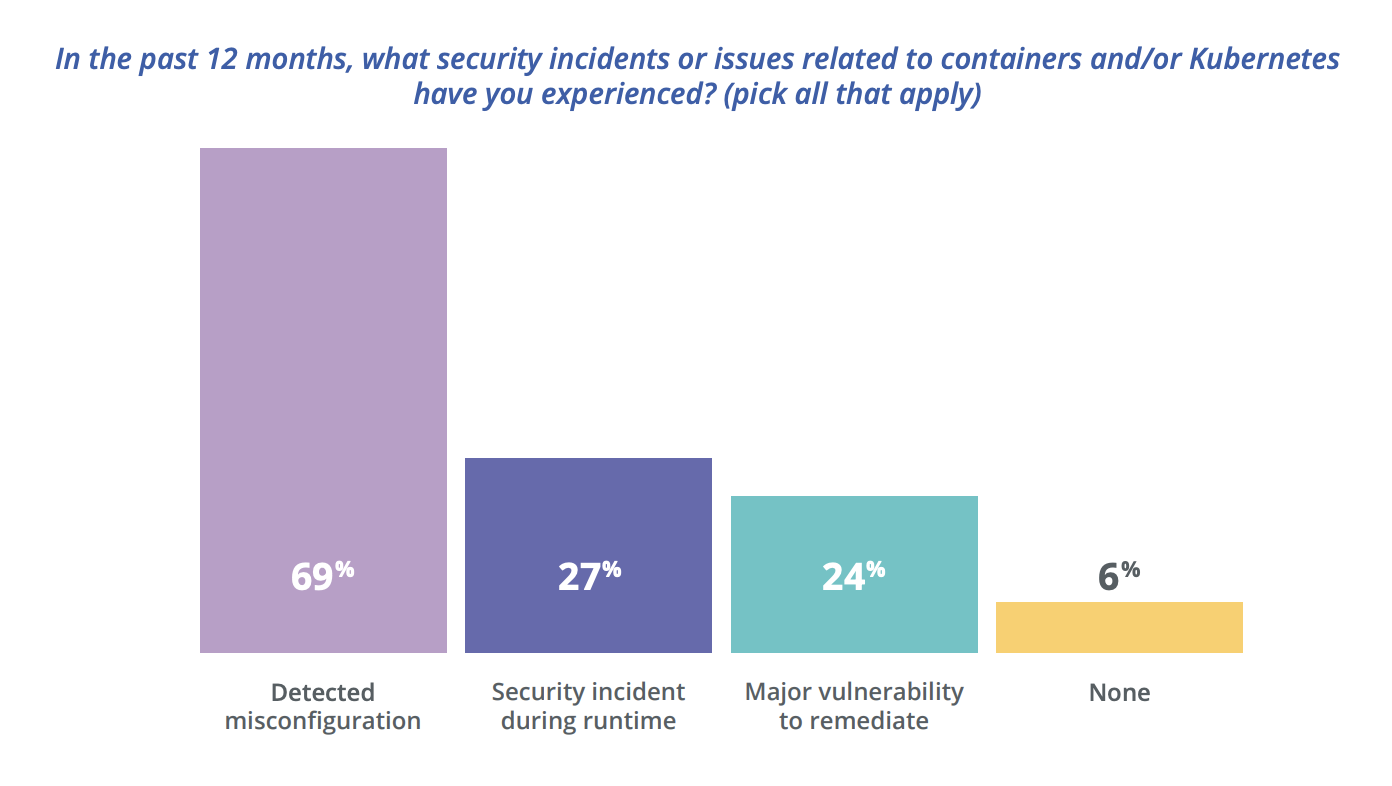
The consequences of a security incident are the same regardless of whether an application is containerized, running on virtual machines, or a legacy system. Security breaches can mean hefty fines, loss of customers’ trust, millions of dollars in lost revenue, and lost time and money spent to urgently patch the security hole. And no amount of after-the-fact security patches can retrieve sensitive data. We know security incidents are happening in containerized apps: 94% of respondents to our 2020 State of Container and Kubernetes Security survey had a container security incident in the past 12 months.
Along with adopting containers, many organizations are also adopting DevOps principles and practices,and this shift is amplifying the changes to security. DevOps teams now share responsibility for security with central security specialists, and everyone is looking at how to “shift left” and apply security practices earlier in the software development life cycle. And all sides face a learning curve – DevOps is learning about security, and security teams are learning about containers and Kubernetes. Recent research from Microsoft detailing the Kubernetes Attack Matrix highlights the broad set of attacks organizations must defend against.
So the stakes are as high as ever, and companies are less prepared, given the steep learning curves. In many cases, companies simply don’t know what they don’t know — they aren’t fully aware of the security challenges particular to a containerized architecture, let alone how to proactively address them.
One common reaction is to simply try to apply the same security tactics that have always been used, but these new application architectures and development workflows require a different approach. So companies often lag one step behind in security as they move further along in their container maturity.
We’ve developed this container security maturity model (download your full copy here) to help companies get ahead on security, so they can put in place the tools and practices essential to meeting not just the needs of their current stage but to continue serving them effectively as they progress on their container journey.
*** This is a Security Bloggers Network syndicated blog from The Container Security Blog on StackRox authored by The Container Security Blog on StackRox. Read the original post at: https://www.stackrox.com/post/2020/05/guide-to-evaluating-your-container-security-maturity/




