DoH! Firefox Engages More Secure DNS Over HTTPS Protocol — Here’s What That Means for You
Mozilla announced that the browser will automatically enable domain name
system encryption for U.S. users ‘over the next few weeks’ to increase privacy
& security
On Feb. 25, Mozilla announced that it began its implementation of encrypted DNS over HTTPS (DoH) for U.S. users of its Firefox web browser. The goal is to increase data privacy and offer greater security to browser users. But this project isn’t something new — it’s been in the works for more than two years. Enabling DoH is something that other browsers have also joined in supporting since that time.
But why are they choosing to do this now? And, furthermore,
what is DNS over HTTPS and why should you care? We’ll answer these questions
and more, including what this rollout means for you and your organization.
Let’s hash it out.
DNS Over HTTPS: Why Firefox Is Encrypting DNS Requests
No matter what you search for online — whether at home, at
work, or on-the-go on your personal device, there’s a virtual trail that’s
available to virtually anyone who knows how and where to look. With this in
mind, Mozilla has been public about trying to increase the privacy of online queries.
In their announcement, Firefox reiterated the importance of
securing the domain name system:
Because there is no encryption, other devices along the way might collect (or even block or change) this data too. DNS lookups are sent to servers that can spy on your website browsing history without either informing you or publishing a policy about what they do with that information.”
Now, they could choose to do this using DNS
over HTTPS or by using DNS over TLS (DoT). HTTPS stands for hypertext transfer
protocol secure and TLS stands for transport layer security. The difference
here would be the type of port that would be used for the transaction. For
example, DNS over HTTPS uses port 443 (the standard HTTPS port), whereas DNS
over TLS uses port 853. Both are viable options, and frankly, many people are
still arguing about which method is necessarily better.
However, it appears that Mozilla has decided to roll with DoH instead of DoT:
We chose DoH because we believe it is a better fit for our existing mature browser networking stack (which is focused on HTTP) and provides better support for future protocol features such as HTTP/DNS multiplexing and QUIC.”
So, what this means now is that Mozilla is choosing to enable
DoH automatically for any Firefox users with U.S. IP addresses. But when we
talk about DNS, what exactly are we talking about?
What the Domain Name System Is and How It Works
Before we can jump into the nitty-gritty of DNS over HTTPS, let’s briefly review what DNS over UDP (user datagram protocol) is and how it works (in the most basic sense, at least).
Whenever you or one of your employees opens a web client (browser)
and types in a specific website address, it’s essentially making a plaintext DNS
request to the DNS server to get the numerical IP address for that specific
website. IP addresses consist of four separate numbers that are up to three
digits in length (between 0 and 255) that are separated by periods (for
example, 123.123.123.123). In response to the client’s DNS query, the DNS
server gets the IP address then sends a response to the client. After that, we
leave the DNS system and the client connects to the web server via the
transmission control protocol (TCP) and HTTP protocol.
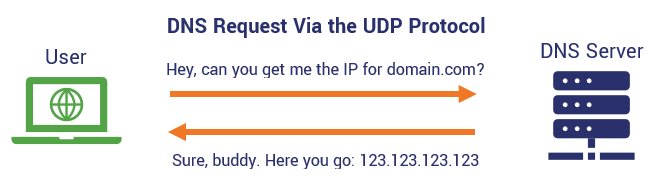
Traditionally, this DNS interaction is done through the user datagram protocol, which uses port number 53. UDP and TCP are both non-secure web protocols that are still used by some insecure websites that lack SSL/TLS encryption. But this isn’t a secure transaction, and here’s why:
The path from the client to the server isn’t exactly that
direct — there are plenty of other hands that the request passes through, such
as your ISP, before a request reaches the server. However, since the request
itself is in plaintext, it means that any of those other entities that
intercepts the request — or that the message passes through on its way to the
server — can essentially read it.
Now, if you don’t give a hoot about privacy, using the
insecure UDP protocol isn’t going to bother you. However, if you’re someone who
values privacy, then DNS over UDP likely isn’t for you. This is where DNS over
HTTPS comes to the rescue.
How Does “DNS Over HTTPS” Differ from Traditional DNS Requests
In a nutshell, DNS over HTTPS is more secure than the
traditional DNS because it’s using a secure, encrypted connection. Using DNS
over HTTPS means that your ISP — and any of the other “hands” that we mentioned
earlier — won’t be able to see certain aspects of the DNS lookup process
because they’ll be encrypted.
As you likely know, UDP has been around for quite a while in “internet” time — basically since the mid-90s. But as far as web protocols go, DNS over HTTPS is actually relatively new. The Internet Engineering Task Force (IETF), the international standards body, recommended DNS over HTTPS as a standard back in October 2018 in its request for comments 8484 (RFC 8484). It works similarly to how traditional DNS over UDP works — it’s just that it does so by encrypting the request by routing it through the HTTPS (the secure version of HTTP) using SSL/TLS encryption.
My colleagues and I have repeatedly talked about the importance of using HTTPS to protect data in transactions to the point that we look like Smurfs, so I’m not going to rehash all of that here. But what I will say is that this move by Mozilla is a win overall for privacy advocates.

Manage Digital Certificates like a Boss
14 Certificate Management Best Practices to keep your organization running, secure and fully-compliant.
What Firefox Is Doing to Make DoH Possible
In their announcement, Mozilla said that they’ve partnered with Cloudflare as their primary “trusted recursive resolver” (TRR). Resolvers are what resolve domain name queries from users and send responses. So, by using a TRR, what this means is that Mozilla worked out policy requirements that Cloudflare as a TRR must satisfy concerning how data is collected and stored (among other things).
Essentially, Firefox’s recent announcement of their move to
DNS over HTTPS will involve:
- Encrypting all DNS queries using DNS over HTTPS,
and - Securely resolving DNS queries using Cloudflare
as a trusted recursive resolver.
So, by making U.S. users’ DNS queries go through Cloudflare’s
DNS servers using HTTPS instead of UDP, it means that the domain name queries
will be resolved by a trusted entity, and that certain parts of DNS requests
themselves will be encrypted.
Remember the process we mentioned earlier about how DNS
requests work? Whenever your web browser makes one of those requests, the
request passes through a lot of hands — but not all of them are necessarily
good or secure hands. This means that you have no idea whose hands that information
will pass through. So, by encrypting DNS requests, it helps to offer greater
protection to Firefox users.
The Benefits of DNS Over HTTPS
Because DNS over HTTPS essentially encrypts the website
connection requests for users using the Firefox browser, it lends itself to
helping to increase security for your organization without hamstringing your IT
security team’s abilities to monitor website network traffic.
DoH Offers Greater Overall Privacy to Users Concerning Their Queries
In a general sense, DNS lookups via HTTPS essentially hides
your browsing history from prying eyes and prevents data from being collected
by third parties. This can be particularly beneficial for users in countries where
internet access is limited or people accessing non-government sanctioned
websites can result in imprisonment or jail.
DoH Mitigates Eavesdropping and MitM Attacks
Don’t like the thought of someone spying in and reading your
plaintext domain lookups? Then you’ll be happy to know that DNS over HTTPS helps
to prevent actors who may be hiding on your local network, public Wi-Fi, or
even at the ISP level from seeing what sites you’re connecting to and any
information you share during the connection. This helps to minimize the risk of
man-in-the-middle attackers from having a heyday at the expense of your
personal information.
DoH Minimizes the Chances of DNS Spoofing
DNS spoofing, or DNS server compromise (or DNS
poisoning), occurs when a bad guy (or is a non-trusted resolver) is
involved in the communication between the client and the DNS server and changes
the response to a phony IP for the website. This re-directs users to fraudulent
websites that appear to be the real thing, swapping out a legitimate link for
one that’s a scam.
The Drawbacks of DNS Over HTTPS
Now, just like how it is with any technology, DoH isn’t
perfect. While it is useful in trying to mitigate cybercrime through
eavesdropping and spoofing, it also could potentially make it more difficult to
evade certain risks. For example, the
Here are a few of the potential drawbacks of DNS over HTTPS
that you should know:
DoH Defaults to Bypassing Your Local DNS
Resolver
If you or your organization relies on your DNS to block
malware or to carry out specific policies, such as blocking access to specific
websites, then you’ll likely not like what have to say next. That’s because,
when enabled, DoH will automatically bypass your local DNS resolver. There is good
news, though. Through your individual browser settings — or your enterprise policies
— you can disable DoH.
Trusted Recursive Resolvers Like Cloudflare
Will See Your Queries
Like we said,
it’s not perfect. When talking about the benefits of DoH, Mozilla also points
out that one of the risks is that the DNS servers that will be handling the
requests will be able to see users’ queries. But there is a catch — Cloudflare,
along with any other DoH partners — are strictly forbidden from collecting
personal identifying information (PII) about those users.
Queries Made via DoH May Result in Slower Response Times
Firefox also reports that queries made via DNS over HTTPS could be slower than those made over traditional DNS over HTTP — but that’s not a guarantee. Of course, Mozilla was quick to say that their own tests of this hypothesis indicate that “DoH had minimal impact or clearly improved the total time it takes to get a response from the resolver and fetch a web page.”
How DoH Will Affect You and Your Organization
What This Change Means for U.S. Firefox Users and Enterprises
So, if you or your customers are in the U.S. and use
Firefox, this implementation will affect any web individuals using Mozilla’s
browser by default once it rolls out— with just a couple of notable exceptions:
Firefox Will Honor Enterprise Configurations
Mozilla said in a previous announcement about DNS over HTTPS back in September 2019 that they’ve disabled DoH by default in enterprise configurations to honor their configurations in Firefox. This means that as long as you’ve set policies, the browser won’t enable DoH in ways that will affect it.
Firefox Won’t Override Parental Controls
For non-enterprise users, there’s good news as well. Mozilla
also said they will “respect user choice” concerning opt-in parental controls.
This means that if Firefox detects such settings, it’ll leave them alone and
not override them.
However, if you don’t want to wait and wish to take
advantage of DoH now in Firefox, you can do so by simply enabling it manually. We’ll
tell you how to do so momentarily.
What This Change Means for Non-U.S. Firefox Users
If you’re outside the U.S. and don’t use Firefox, this won’t automatically affect you when using the browser. However, if you’re outside the U.S. and don’t want to feel left out — or if you’re in a country with strict censorship and wish to obfuscate your DNS queries due to safety concerns — then no worries. You can manually enable DoH in your browser right now!
To enable DoH in Firefox, simply go to Options > General
> Network Settings > and click on the Settings button
there. Once there, select the checkbox to enable DNS over HTTPS.
However, maybe rolling with DoH enabled just isn’t for you. If
you wish to disable DoH, you can do so by going to Options > General
> Network Settings and de-select DoH.
It really is that simple!
Final Wrap Up
There are a lot of changes going on right now concerning
data privacy and website security. Data privacy laws have been rolling out over
the past few years — GDPR,
CCPA, NY’s
SHIELD Act, etc. — and we recently told you about how Apple
will no longer trust websites using SSL/TLS certificates with more than
one-year validity. This move by Mozilla seems to be following suit with all of
these changes for greater privacy and security.
*** This is a Security Bloggers Network syndicated blog from Hashed Out by The SSL Store™ authored by Casey Crane. Read the original post at: https://www.thesslstore.com/blog/doh-firefox-engages-more-secure-dns-over-https-protocol-heres-what-that-means-for-you/



