Going After the Good Guys: The Government’s Ransomware Identity Crisis
Why fixing that ransomware attack might get you indicted
Editor’s
Note: We’re pleased to publish this article from attorney Ryan Blanch, sharing
an expert perspective on some of the legal issues in the cybersecurity
industry.
When it
comes to ransomware, malware, and hackers, the government is finding it
difficult to keep pace with the quickly evolving landscape of cybercrime. And
sometimes, the government seems to be going after the good guys instead of the
bad guys, as evidenced by the recent CoalFire debacle in which Iowa arrested
and charged the same cybersecurity professionals it had contracted to try to
breach the state’s security systems.
As a criminal
defense attorney, I’ve been involved in myriad cybercrime cases. There were the
DDoS attacks on the Church of Scientology, and then the infamous Blackshades
malware allegedly used to spy on Miss Teen USA. We defended a sports gambling software company
accused of conspiring with the mob abroad, which went to trial and was ultimately dismissed.
Later, we handled a cryptocurrency hacking case, an online currency arbitrage
platform; and, more recently, the allegedly illegal deployment of scores of
Bitcoin ATM machines around high crime neighborhoods – to name a few.
In most
cases, it’s at least apparent why prosecutors are focusing on our client. But
in other cases, prosecutors are barking up the wrong tree—they’re going after
the targets they can find instead of looking for the actual bad guys. After all,
career hackers can be nearly impossible to track down and apprehend. In the
sports gambling case I handled, my client reported that the New York district
attorney’s office wanted to strongarm him into hacking into his clients’
systems to turn over personal data on gamblers and their bookmakers who may be
involved in illegal gambling.
Another area
where prosecutors seem to be struggling to find and prosecute the right parties
is with ransomware attacks. If you should fall victim to a ransomware attack,
be very careful how you navigate your crisis. And that goes double for those
who try to help you. The government may be looking to indict you both. And the penalties are steep.
Let’s hash it out.
How Ransomware Attacks Work: From Attack to Prosecution
Ransomware
brings companies to their knees in an instant as it encrypts user data and
files irretrievably. In some cases, the only way to resume business as usual is
to pay the ransom outright and most of them only take crypto.
Phase 1: The Attack

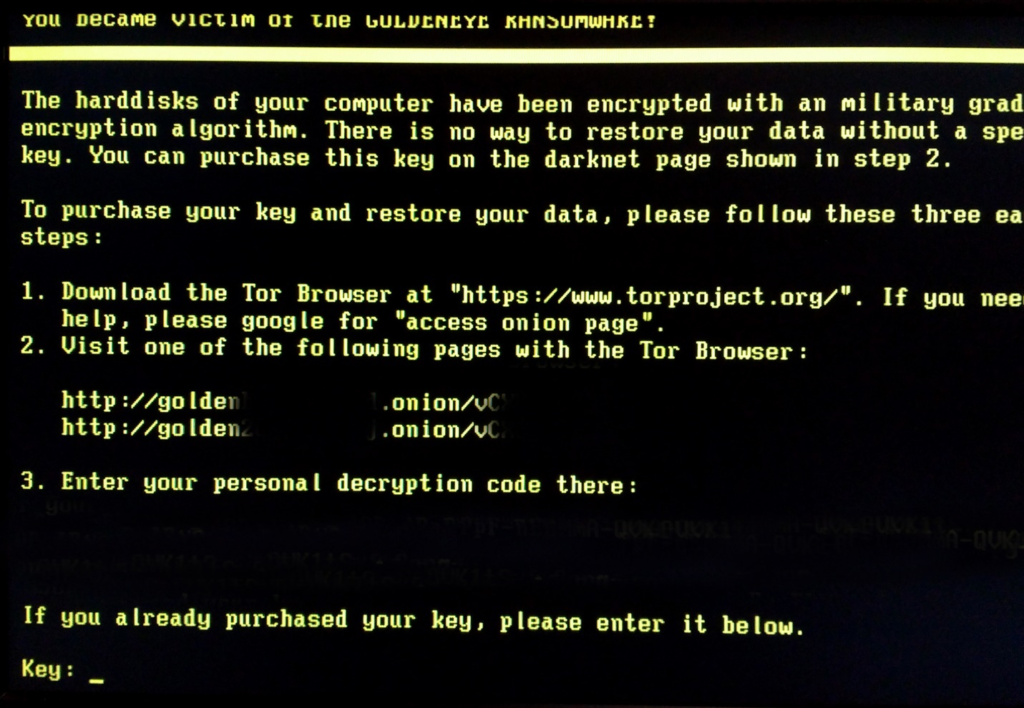
You show up
to work to find a message like this one filling all 100+ displays of your
company’s employee workstations. Your CTO and IT administrator are in a panic. Your
entire company has been locked out of its servers, computers and files. The company
stands to lose hundreds of thousands of dollars each week that this persists. There
is a countdown clock on the monitor, and IT cannot find any way to access the
system. All you can think is, ‘What would Kiefer Sutherland do?’
Phase 2: The Fallout
It’s day two
and the losses have already exceeded $40K. Clients are taking flight as they
fear the worst. Employees are asking whether they should come to work, and the IT
department is pulling its collective hair out. You wonder what you have them around for if
they can’t fix your computer-related problems. Arnie, Head of IT (for now), has
resorted to Googling (from his personal cell phone) “ransomware help” to look
for outside companies that might be able to lend a hand.
The 5 bitcoin
demanded hasn’t yet increased, but it might as well have because the volatile
bitcoin market has already added $5,753 to the price (some companies are
starting to keep an emergency bitcoin account to offset the risk of price
fluctuations).
Someone
reminds you that you have business insurance that may cover this sort of thing.
You call your insurer. They do in fact cover ransomware attacks and have a list
of “approved providers” aka cybersecurity firms who can help.
Phase 3: The White Knight Arrives
It looks as
though all that panic-driven Googling may have paid off. Arnie has already
found a cyber security firm and is on the line with them. As luck would have
it, this firm is also on your insurance company’s “approved provider” list. The firm thinks they may be able to resolve
the problem remotely. But when asked, they admit that no one can actually decrypt
the files. More pointedly, if you were
to marshall the combined forces of Homeland Security, the NSA, M.I.T., Kaspersky
Labs and Elliot Gunton to the singular purpose of retrieving the electronic
files of your trading house and photos of your mini labradoodle wearing a tutu,
they would all wind up with zilch. That’s how hard it is to unencrypt what’s
been properly encrypted.
So how can
this cybersecurity firm help?
Pay the
ransom, of course.
So then, what
good are they? Well, for starters, they have a bitcoin wallet on the ready. You
don’t. Secondly, they actually know how to deploy a decryption key. You don’t
(and neither does Arnie).
Turns out
most ransomware, eh hem, artists don’t restore your files for you when you pay
the ransom. They merely send you a key. Technical support doesn’t exist. It’s
do it yourself. And you wouldn’t want your attackers fixing it for you even if
they offered.
Here is why
it makes sense to hire the cyber security firm rather than pay the ransom
yourself in a nutshell:
- They can pay immediately.
- They may be able to get the attackers
to lower the ransom. Probably not enough to decrease your cost but enough to
offset the cost of the firm’s fee. - You shouldn’t be dealing with your attackers.
They may expand the problem to other systems if you let the wrong information
slip. - Once you get the key, if you don’t
deploy it correctly you could corrupt your files forever. Some of these keys
require several steps to deploy them. And you need to make sure you back up
your files first, etc. - After you get your files back you
need to close the proverbial back door. Your attackers could come back if you
don’t. The honor of your extortionist ends with the promise to send you the
key. It does not include a promise to never return. - The best firms will issue and update a
white paper to make sure that you continue to follow best practices to avoid
subsequent attacks. - An honest firm will tell you if the
strain of your ransomware variant is actually undecryptable. Some variants are old,
and the decryption key has already been disseminated publicly. If your firm has
the key, they may just deploy it for you at little or no cost.
Phase 4: The White Knight Gets Indicted
All good? Not so fast. Now the cyber security firm’s principals and employees are contacted by the FBI’s Cyber Division. The U.S. Attorney’s Office wants to talk about a turn-in date and because they know this is a real company with generally law-abiding individuals, they wanted to call and invite them in to “self-surrender” so they can forgo the unpleasantness that comes with a 3AM home arrest warrant execution.
Looks like
your company’s savior is going to need to hire a great criminal defense
attorney.
Why? Turns
out the government doesn’t look kindly on paying ransoms. The reasons
themselves are not objectionable:
- The money could go straight to terrorist
organizations and other criminal cartels - The money is difficult to trace when
transferred through bitcoin.
But the
government also knows that juries don’t like to convict victims for paying
their extortionist. It’s like arresting the mother of a kidnapped child for
paying the kidnappers their ransom to get her baby back.
It would never fly.
How The Government Views Paying Computer Ransoms
Lost
computer files, lost business revenue and even stolen intimate photos are less
sympathetic reasons to sponsor a crime cartel than say, getting a real live
child back. But, just the same, the DOJ doesn’t like to lose. And prosecuting
victims is a losing strategy. So, for now, victims can (probably) pay ransoms
back directly (as ill-advised as that is) to their attackers.
But if you
hire an intermediary, that’s where the government is testing a prosecutorial
theory. The theory is if they can prosecute the cyber firms who pay the ransoms
then they can get a pelt for what they view as an ugly business. Hey, somebody
has to pay. Cybercrime is the new bank robbery and it’s turning into an
epidemic. The government’s so-called ransomware “experts” are in the stone
ages. But prosecuting cyber security firms makes it look like they are doing
something about this epidemic (spoiler alert: they aren’t).
Strangely
enough, the FBI has made multiple statements encouraging or allowing companies
to pay off ransomware attacks:
- Joseph
Bonavolonta, Assistant Special Agent of the FBI’s Cyber and Counterintelligence
Program, said that in most cases, because the FBI can’t
help these companies recover files, their agents often end up recommending them
to pay the ransom to get their data back. - An
official statement from the FBI said they don’t “advocate” paying
ransoms, but that the “FBI understands that when businesses are faced with an
inability to function, executives will evaluate all options to protect their
shareholders, employees, and customers.”
They haven’t yet publicly announced a policy of indicting companies for paying ransoms or started issuing mass indictments. But they are hovering around the periphery, looking for instances where they think they might be able to dirty-up the white knight cyber security firm to make them a public example of the perils of paying ransoms as a business model.
What if they succeed? What does that accomplish? It doesn’t stop the ransomware attacks. It doesn’t stop the victims from paying those ransoms directly. But it takes out a middle man would-be protector, leaving the victim to their own devices.
Making the Good Guys Prosecutable: Dirtying up the White Knight
If juries
don’t like to convict victims, how would they feel about their heroes? As a
matter of public policy, do we want to criminally prosecute the saviors of
those who have otherwise irretrievably lost their businesses?
The answer
is it depends. We should not criminalize the only people that offer any
protection whatsoever to the victims of ransomware. They also provide a
mechanism for insurance companies to insure the losses of such an attack. The
government is putting this in jeopardy (more on this to come). In order to make
a white knight prosecutable, the government needs to shift our view of them. The
prosecution will want the jury’s perception of the white knight to be that of
an opportunistic broker of shattered dreams. Instead of saving their victims
from further attack, they provide a surcharge to further exploit them. As
ridiculous as this sounds, this is what in fact is being kicked around at DOJ
offices everywhere.
The Insurance Companies as Co-Conspirators?
So, if the
cybersecurity firm is recommended and, in some instances, paid for by the
victim’s insurance company, doesn’t that make said insurance company an
accomplice in the conspiracy to pay ransoms to possible crime cartels? After all, the insurance company knows exactly
how the cyber security firm addresses the problem – by paying ransoms. So, will
the government start prosecuting Allstate for providing ransomware protection
to its insureds?
Probably
not.
But, by
taking the cyber security firm out of the equation, it would force the
insurance company to pay the ransom to the insureds or even worse, pay it
directly to their attackers. Knowing that would result in potential
prosecution, they would have to stop insuring businesses and individuals from
ransom attacks all together, compounding the victim’s losses exponentially.
No Good Deed Goes Unpunished
So if the
reasons listed above are all valid reasons why you SHOULD hire a cyber security
firm in a ransomware attack and if billion dollar insurance companies are
recommending that their insureds hire these companies (knowing full well that
those companies will pay the ransoms), then how in the world can the government
look to criminally charge these very same companies for doing what it has
failed to do – rescue victims of
ransomware?
For now, the government is limiting its
prosecutorial powers to low hanging fruit; looking at smaller cyber security outfits
that they believe make easy targets to test-flex their muscles. They have yet to rope in the insurance companies
who refer them business. And their internal (and informal) policy of the moment
seems to militate against charging ransomware victims who pay ransoms
directly.
But it’s
‘victim beware’ when it comes to paying ransoms. You don’t know where the money
is going—and the U.S Treasury’s Office of Foreign Assets Control (OFAC)
maintains a nearly incomprehensible and ever changing
list of thousands of countries, individuals and entities to whom it’s a crime
to send funds.
The takeaway: If you fall victim to ransomware, hire a cyber security
firm to handle it. If you are such a
firm, proceed with caution and consult with legal counsel about best practices.
*** This is a Security Bloggers Network syndicated blog from Hashed Out by The SSL Store™ authored by Ryan Blanch. Read the original post at: https://www.thesslstore.com/blog/going-after-the-good-guys-the-governments-ransomware-identity-crisis/



