Behind The Scenes Of Application Security Is A Plumbing Problem
What’s the problem?
These days, finding ways to make technology work for us rather than against us has become the gold standard. And in the world of application security, this means looking for innovative methods of optimizing security initiatives to ensure they meet our changing needs—and not the other way around.
With such a broad range of security tools at our disposal, all of which possess their own unique functions and processes, finding the best way to implement them while still keeping an eye on operations and managing risk at the pace of business demands a shift in perspective from building systems to supporting what is already there. Because despite the tremendous advances in cybersecurity over the past 20 years, multiple factors are still holding us back from making the most of the application security initiatives we have worked so hard to create. Essentially, we don’t need to generate new operations around risk visibility; we just need a big dose of creativity and good old-fashioned common sense—or maybe we just need a plumber?
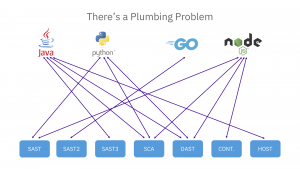
Did you say plumber?
If you are wondering what a plumber has to do with application security management, an image speaks a thousand words—but in simple words, the pipes are messed up. A lot of the critical information being generated and shared across applications and security tools is hampered by an overly-complicated internal structure. Every time we stand up a new tool to scan applications (or use a process that leverages an existing tool), we are essentially laying down a piece of “pipe.” And when an application comes through that doesn’t fit through that pipe—like if a new application uses Golang instead of the typical Python/Java—you’ll need some new ones to accommodate it. And let’s not forget, someone has to lay those pipes, maintain those pipes and pay for those pipes. It doesn’t take much to see how quickly you’re stuck with a complicated and burdensome system.
And it’s getting in the way of real, effective application security.
As it stands right now, the security scanning tools we rely on produce vast quantities of results, some of which don’t necessarily reflect actual risks to business, and developers often lack the time and resources needed to analyze findings and adopt a software security posture that works. This reality can confuse and frustrate operations intent on finding ways to properly assess vulnerability and risk while also securing the deployment of certain tools. It is certainly possible to address this reality through the employment of comprehensive scanning tools, which would provide an ideal scenario for application security, but this is a wildly expensive and impractical solution. In fact, application security initiatives can’t keep pace with expanding business needs because of clumsy and highly fragmented operations that overburden the labor available to manage them.
How are these factors fragmented?
- Organic tool growth has led to incompatible scanning operations.
- Multiple tools are needed to meet a single policy statement.
- Each tool represents a different scanning engine, all of which operate on varying assumptions, requirements and perspectives.
- Every tool classifies vulnerabilities differently.
- Remediation workflow is tool-specific.
- Different consoles are required for each tool.
- A unilateral approach to scanning is inherently weaker than a heterogeneous scanning strategy.
This short list alone confirms the plumbing problem that is exacerbated as security tool portfolios grow and puts a spotlight on the lack of universality in operations. This clunky system not only chafes against reason, but it overtaxes SMEs with an unruly amount of oversight.
How are these factors affecting labor?
- Each tool requires one or more SMEs.
- Timeframes consist of unnecessarily long deployment.
- Results must be manually correlated.
- Qualified talent is expensive and hard to find.
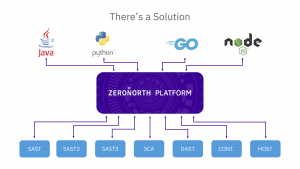
How can you fix the pipes?
Even though most people would agree using multiple scanning tools provides the best results in application security, prohibitive cost is an insurmountable barrier. And this is where the power of better plumbing can make all the difference, as it replaces chaotic operations with an orchestrated platform of cohesion and performance. When it comes to risk vulnerability and operations, the ZeroNorth platform streamlines and simplifies application security testing by…
- Centralizing software and infrastructure testing tool administration = creating actionable risk intelligence
- Significantly reducing human labor requirements and cost = speeding up the rate of remediation by prioritizing risks based on impacts to business
- Simplifying tool comparison and selection = minimizing “noise” by correlating and de-duping vulnerabilities
- Challenging the current pipe-laying problem by removing the entire process = establishing healthy pipes that strengthen your security program
When we manage to improve results through consistent, automated testing—like that offered by ZeroNorth’s orchestrated platform—security, development and operations align with a single source of risk visibility and are able to effectively match vulnerability intelligence to the priorities of business. Situational awareness takes place in real-time, which means all factors related to risk, reporting and remediation can happen before the pipes burst and leave behind one big mess.
*** This is a Security Bloggers Network syndicated blog from Blog | ZeroNorth authored by ZeroNorth. Read the original post at: https://www.zeronorth.io/blog/behind-the-scenes-of-application-security-is-a-plumbing-problem/



