Home » Editorial Calendar » Zero-Trust » Introducing Comprehensive Workload Identity and Access Management Across Microsoft Environments
Introducing Comprehensive Workload Identity and Access Management Across Microsoft Environments
Many enterprises depend on Microsoft technologies for their critical systems, ranging from on-premise Windows Server to cloud-based Azure. While identity and access management (IAM) for human users has advanced with cloud adoption, securing non-human workloads (applications, services, AI agents) in hybrid environments remains a significant challenge due to static credentials, inconsistent security, and fragmented tools.
Aembit has launched expanded capabilities specifically designed to address this by providing seamless, consistent, and robust Workload IAM across the entire Microsoft ecosystem, from on-premises Windows Servers to Azure. This aims to simplify security and bridge the migration gap by offering a unified management platform for workloads regardless of their location. Key benefits include:
-
No More Security Silos: Centralized definition and enforcement of access for all workloads, including Microsoft, Linux, Kubernetes, Serverless and SaaS.
-
Smoother Azure Migrations: Secure and integrated workload access management from day one of migration.
-
Say Goodbye to Credential Sprawl: A “secretless” approach that reduces the attack surface by providing temporary, just-in-time access.
-
Better Visibility, Easier Compliance: Centralized logging and auditing for all workload access, improving compliance and incident response.
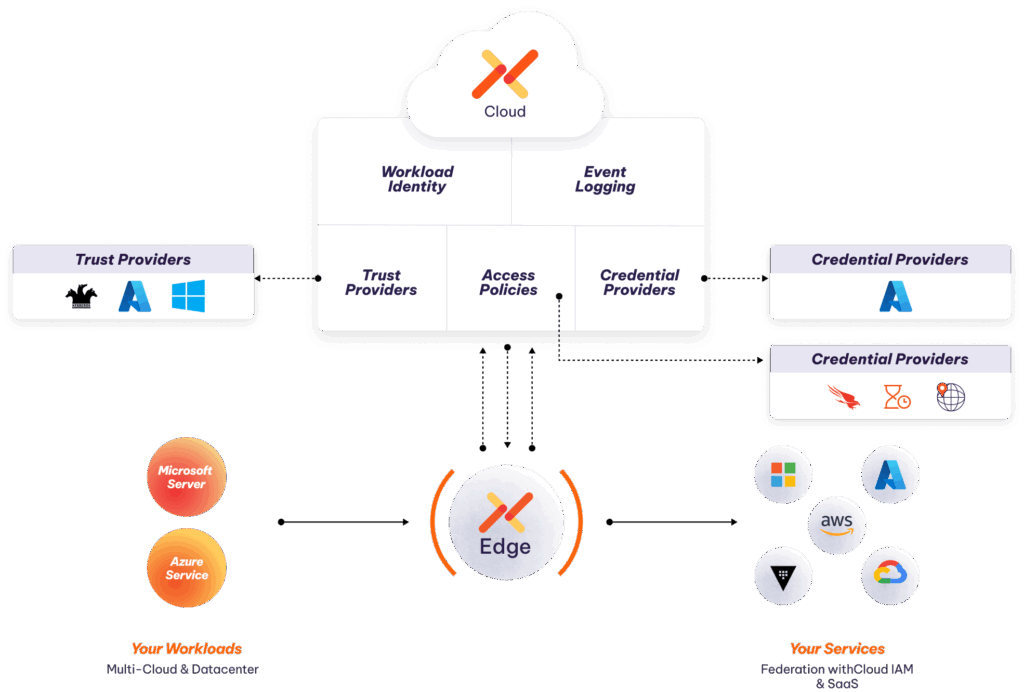
High Level: How We Enable IAM for Microsoft Environments
At the highest level, we believe you should be able to treat every workload the same when managing access. To that end, we have expanded the footprint of what we do to a range of Microsoft-powered environments, and taken care of the behind-the-scenes technology that’s needed to do it. What that looks like for you:
1) Run Aembit Edge on Microsoft Windows Servers
Our Edge component is a lightweight software module that helps us get information about the server and enables us to inject credentials without any additional work by your developers.
2) Verify Identities via Kerberos, Active Directory (Entra ID), and Azure Metadata Service
We use the information from the step above to cryptographically verify the identity of the system using various trust providers on-prem and in the cloud.
3) Provide MFA for Machines Through Conditional access for Windows Machines
Once the identity of the system is verified, we want to make sure it’s healthy and in good standing with the rest of your corporate compliance requirements.
4) Support Azure Workload Identity Federation (WIF) to Provide Short Token Support for Azure
Short-lived, just-in-time (JIT) tokens are much safer than static API keys so WIF is used for access to all Azure resources even when the source is on-prem or from another cloud service provider.
5) Translate Between a Microsoft Server or Azure Service Identity and an Access Token to Any Other Service – Microsoft and Beyond
Use identity federation and Aembit to access services and data that are outside of your direct Microsoft environment to quickly close the communication gap and help you scale without creating a service mesh
Under the Hood: A Deep Dive into Our Microsoft Prowess
So, what exactly have we built? Let’s break down the exciting new features:
For On-Premises:
We know Windows Server isn’t going anywhere anytime soon, and neither is Active Directory. That’s why we’ve doubled down on making Aembit robust for your existing infrastructure:
- Controller/Proxy for Windows Server: We’ve extended our intelligent agent controller and agent proxy right into your Windows Server environments. This means you can manage and secure access for applications running on your physical or virtual Windows machines with the same fine-grained control as your cloud-native services.
- Conditional Access with CrowdStrike on Windows: This is a big one for dynamic security. We’ve integrated with CrowdStrike on Windows to enable real-time conditional access. Imagine this: a Windows Server with a critical vulnerability flagged by CrowdStrike automatically loses its ability to access your sensitive database until that issue is remediated. This is posture-based security in action, ensuring only “healthy” workloads can access critical resources.
- Kerberos as a Trust Provider: For those deeply invested in Active Directory, we’ve got you covered. Aembit now seamlessly integrates with your existing AD by supporting Kerberos as a Trust Provider. This allows us to cryptographically verify the identity of your Windows workloads joined to your domain, providing a rock-solid, trusted source of identity for on-premises applications without ever relying on static secrets. It’s about leveraging what you already have, securely.
For Azure:
For those expanding into Azure, Aembit provides powerful, native integrations:
- Controller/Proxy for Windows Server (in Azure): Just like on-prem, our controller/proxy extends to your Windows Server instances running within Azure. Consistent control, no matter where your Windows workloads are.
- Conditional Access with CrowdStrike on Windows (in Azure): The same powerful conditional access capabilities you get on-prem are fully available for your Windows workloads in Azure. A unified security approach for all your Microsoft-based systems.
- Azure Entra Workload Identity Federation (WIF) as a Credential Provider: This is a game-changer for simplifying access to Azure resources. Aembit integrates directly with Azure Entra WIF, eliminating the need to manage static credentials for your Azure workloads. Aembit can dynamically fetch short-lived access tokens directly from Azure Entra, providing your applications with just-in-time access to Azure services. Less credential management, more security.
- Azure Metadata Service as a Trust Provider: We leverage the Azure Metadata Service to securely attest to the identity of your Azure virtual machines and other compute resources. This provides a highly assured way for Aembit to verify the identity of your Azure workloads, forming the foundation for robust access policies.
- Broad Protocol Support: Beyond just Microsoft integrations, Aembit supports a huge range of enterprise application protocols. Whether your services are using HTTP(S), MySQL, PostgreSQL, Redis, or many others, we can secure those workload-to-workload communications. This means a vast majority of your applications can benefit from Aembit’s secure access managementc
Imagine this: a Windows Server with a critical vulnerability flagged by CrowdStrike automatically loses its ability to access your sensitive database until that issue is remediated. This is posture-based security in action…
How to Find Us on the Azure Marketplace
We believe in making things easy. That’s why Aembit is now officially available on the Azure Marketplace! This simplifies the process for you to discover, procure, and deploy Aembit directly within your Azure environment. You can check us out right here: Aembit in the Azure Marketplace.
Why Aembit is Your Go-To for Microsoft Workload Access Management
Our mission at Aembit is to secure the modern enterprise, and that deeply involves the Microsoft ecosystem. We understand that whether your applications are long-standing legacy systems or shiny new cloud-native deployments, they all need robust, intelligent access controls. With this expanded Microsoft launch, we’re empowering you to:
- Embrace Zero Trust for Workloads: Stop implicitly trusting any workload. With Aembit, every access attempt is verified against granular, identity-centric policies.
- Automate, Automate, Automate: Ditch the spreadsheets and manual processes for credential management. Let Aembit handle the automation, reducing risk and operational overhead.
- See Everything: Gain unprecedented visibility into all workload-to-workload interactions. Know who accessed what, when, and why, for better security, operations, and compliance.
- Migrate with Confidence: Accelerate your cloud adoption journey, knowing that your Microsoft-based application workloads are securely managed every step of the way.
The future of security is all about securing non-human identities – your workloads. As you navigate the complexities of your hybrid and multi-cloud environments, especially within the vast Microsoft landscape, Aembit is here to be your trusted partner.
Head over to aembit.io or dive into our technical documentation at docs.aembit.io to explore our expanded Microsoft capabilities.
The Workload IAM Company
Manage Access, Not Secrets
Boost Productivity, Slash DevSecOps Time
No-Code, Centralized Access Management
The post Introducing Comprehensive Workload Identity and Access Management Across Microsoft Environments appeared first on Aembit.
*** This is a Security Bloggers Network syndicated blog from Aembit authored by Ashur Kanoon. Read the original post at: https://aembit.io/blog/introducing-comprehensive-workload-identity-and-access-management-across-microsoft-environments/