Medusa Ransomware: Inside the 2025 Resurgence of One of the Internet’s Most Aggressive Threats
Medusa ransomware is making headlines again with its increasingly aggressive tactics. Known for its ruthless extortion techniques and expanding affiliate network, Medusa continues to cause significant disruption and financial damage. This article takes a deep dive into its operations, the main factor driving its recent resurgence, which has led to warnings issued by global authorities, its targets, why it’s so dangerous and the critical strategies organizations must implement to defend against its attacks.
What is Medusa Ransomware?
Medusa is a ransomware-as-a-service (RaaS) operation that first emerged in 2021. It operates through a core group of cybercriminals who develop and maintain the ransomware platform, while recruited affiliates – often with varying technical skills – carry out the attacks and split the ransom payments with the core operators.
What sets Medusa apart from other RaaS groups is its operational discipline, rapidly growing affiliate network and uniquely aggressive extortion process. Victims are contacted directly via email or phone and pressured through a public leak site that features countdowns, stolen data previews and payment escalation options. Its ransom demands have also surged, sometimes reaching $15 million per incident. As a result, affiliates are remaining in networks longer, stealing more data and even initiating multiple rounds of extortion against the same victim.
What’s Behind Medusa’s 2025 Surge?
Medusa’s resurgence is occurring in the wake of major law enforcement actions in 2024 that disrupted several high-profile ransomware groups, including LockBit and BlackCat. Their takedowns last year created a power vacuum in the cybercriminal ecosystem – one that Medusa quickly moved to fill. Case in point: In the first 72 days of 2025, Medusa launched nearly 60 successful attacks, already accounting for more than a quarter of its total known activity in 2024. February 2025 was its most active month to date, with 33 confirmed victims.
Who’s Being Targeted?
Medusa focuses on targeting organizations that provide essential services and are less likely to tolerate prolonged disruption. This includes:
- Healthcare providers, such as US-based SimonMed Imaging and Bell Ambulance (both victims of the Jan. 2025 attack)
- Government and public sector organizations
- Educational institutions
- Critical infrastructure and utilities, including UK-based HCRG Care Group (another victim of the Jan 2025 attack)
These sectors not only face financial risk but also significant operational and reputational damage, making them more likely to engage in ransom negotiations.
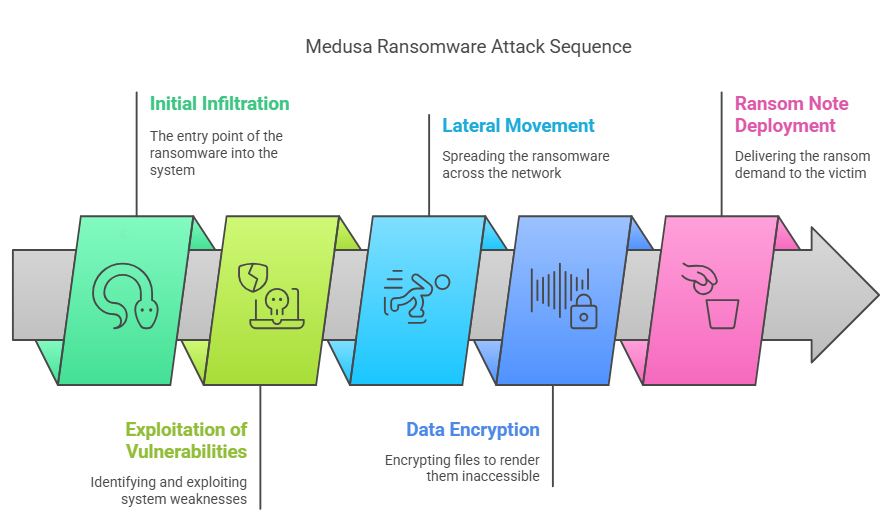
A Closer Look: How a Medusa Ransomware Attack Works
Medusa attacks follow a structured methodology that combines known offensive techniques with legitimate tools. This enables affiliates to remain undetected while maximizing impact. Here’s a step-by-step breakdown:
Initial Access
Attacks typically begin with phishing emails, increasingly generated using AI to mimic trusted services like Microsoft 365 or internal IT teams. These emails contain malicious links or attachments that lead to credential theft or malware installation. Other access methods may include exploiting unpatched vulnerabilities or purchasing access from Initial Access Brokers (IABs).
Lateral Movement
Once inside a victim’s network or system, attackers use legitimate administrative tools to navigate. Commonly used tools include:
- PowerShell
- Windows Management Instrumentation (WMI)
- PDQ Deploy
- Remote desktop tools like AnyDesk and Splashtop
Attackers often extract credentials using Mimikatz and disable endpoint protection to avoid detection.
Data Exfiltration & Encryption
Before launching the ransomware, Medusa operators exfiltrate sensitive data using tools like Rclone. They conduct network reconnaissance with Advanced IP Scanner or SoftPerfect Network Scanner.
Once data is secured, the ransomware is deployed to encrypt files using AES-256 encryption. Victims receive a ransom note titled !!read_me_medusa!!.txt while backups are deleted and system logs are wiped to hinder recovery.
Why Medusa is so Dangerous: A New Level of Ransomware Aggression
Medusa’s aggressive, multi-layered extortion process is specially designed to apply psychological pressure on victims. Here are its four main approaches:
- Sophisticated Extortion Portal
Victims are directed to a Tor-hosted portal used to manage negotiations, featuring:
- Countdown timers that escalate ransom amounts and threaten data publication
- File verification tools to decrypt a few files as proof that the decryptor works
- Sample data leaks to demonstrate the theft and heighten urgency
- Direct Victim Contact
If initial demands are ignored, Medusa affiliates escalate by directly contacting victims via email or phone. This increases pressure on internal teams and compresses response timeframes.
- Triple Extortion
Some victims report being targeted a second time after paying the ransom. Medusa actors claim the negotiator was fraudulent and demand an additional ransom for the “real” decryptor, significantly amplifying financial and emotional strain.
- Data Sale & Countdown Extension
Stolen data is simultaneously advertised for sale on Medusa’s leak site. Victims can also pay a fee (e.g., $10,000 in cryptocurrency) to delay public release by extending the countdown timer by one day – a temporary solution that only deepens the urgency and fear.
Staying Ahead of Medusa: What Works
Despite Medusa’s speed and aggression, its attack playbook is predictable and preventable. The following tips are what organizations must implement to safeguard themselves from Medusa ransomware:
Patch Fast
Medusa exploits known flaws like CVE-2024-1709 and ProxyShell within days of disclosure. Prioritize patching, subscribe to threat alerts and use WAFs if patching lags.
Enforce MFA
Weak or stolen credentials still open doors. Enforce MFA across all remote access, use phishing-resistant methods and don’t skip service accounts.
Segment Networks
Flat networks make lateral movement easy. Use VLANs, isolate critical systems and monitor unexpected cross-network traffic.
Upgrade Endpoint Visibility
Medusa uses legit tools like PowerShell and Mimikatz to evade detection. Deploy EDR, monitor admin tool usage and flag unsigned executables.
Secure Email & Train Users
AI-powered phishing makes spoofed IT messages hard to spot. Use advanced filters, enforce DMARC/SPF/DKIM and run regular simulations.
Hunt for IoCs
Watch for remote access tools, credential dumping, or outbound data spikes. SIEMs or XDR platforms can help spot early-stage activity.
Protect Backups
Medusa deletes backups before ransom. Keep one copy offline or immutable, test restores regularly and monitor for deletion attempts.
Final Thought: Ransomware in the Age of AI
Medusa’s current resurgence highlights how cybercriminals are integrating AI-driven tactics into their operations. AI isn’t the source of the threat, but it is quietly reshaping the way attackers craft and scale their campaigns.
In Medusa’s case, AI is allowing affiliates to generate phishing emails at scale that are:
- More tailored to the target’s organization or role
- Better formatted, with correct branding and fewer telltale errors
- Capable of adapting in real time (e.g., sending follow-ups when recipients don’t engage)
These AI-generated messages can impersonate internal IT teams, trusted vendors, or widely used services like Microsoft or Google, increasing the likelihood of user interaction and decreasing the chances of being flagged by filters or spotted by users.
This shift isn’t unique to Medusa – AI is now being weaponized across the cybercrime ecosystem. The challenge ahead is to adapt with equal speed. Therefore, organizations must:
- Train employees to recognize more subtle phishing attempts
- Invest in email filtering and behavioral detection tools that go beyond static indicators
- Leverage AI to serve both sides of the cybersecurity equation
AI won’t replace traditional attack methods, but it will continue to shape how quickly and convincingly those methods are delivered. The challenge for defenders is not just to catch up to today’s ever-evolving ransomware threats, but to anticipate them.