Zero-Trust in Web3: Redefining Security for Decentralized Systems
The first time I encountered the concept of zero-trust, it felt revolutionary. I was working on a high-stakes project where we assumed our internal networks were safe by default. One breach shattered that illusion, teaching me a hard lesson about the importance of continuous verification and minimal trust. In traditional IT, we trusted internal or external networks to a fault. But zero-trust flipped that paradigm, advocating for continuous verification, minimal privileges and assuming every entity is potentially hostile.
When I transitioned into the Web3 space, these lessons came rushing back. Web3 systems, while promising trustlessness, face unique security challenges that require a rethink of traditional principles. I wondered how zero-trust applies to decentralized systems, which inherently aim to be trustless. The answer isn’t straightforward, but it is transformative. Zero-trust, when adapted to Web3, isn’t just about securing systems; it’s about aligning with the ethos of decentralization.
Principles in Managing Zero-Trust Architecture
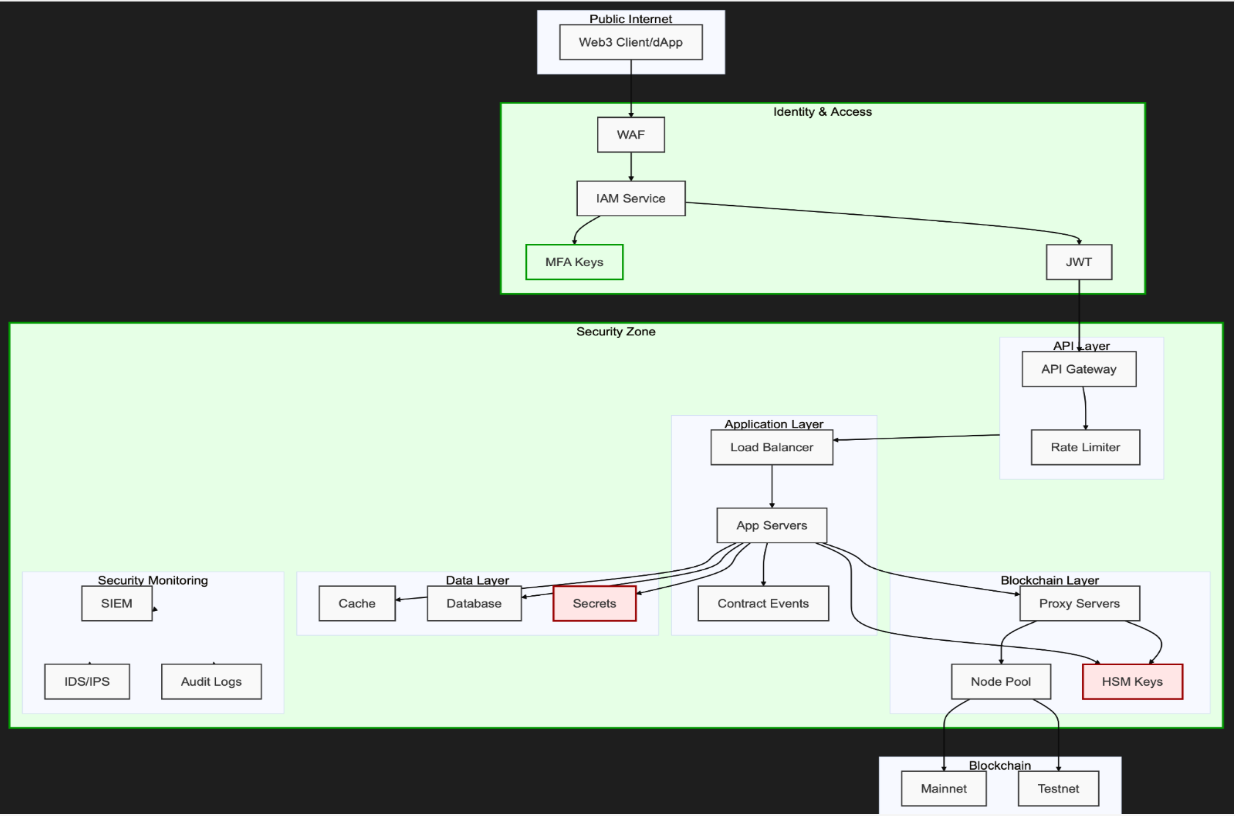
1. Entry Point Security:
- All traffic first passes through a web application firewall (WAF)
- Strong identity verification using IAM services and mandatory MFA
- JWT tokens for session management and authorization API security layer:
2. API Security Layer:
- API Gateway acts as the primary control point
- Implements rate limiting and request throttling
- Each request is authenticated and authorized regardless of origin
3. Application Layer:
- Load balanced application servers
- Smart Contract Event Listener for blockchain state monitoring
- All inter-service communication is encrypted and authenticated
4. Blockchain Integration:
- Node Pool with multiple blockchain nodes for redundancy
- Proxy servers to manage blockchain interactions
- Hardware Security Module (HSM) for private key management
5. Data Security:
- Distributed cache for performance
- Encrypted database storage
- Separate secret vault for sensitive credentials
- Continuous Security Monitoring:
- SIEM system for security event correlation
- IDS/IPS for threat detection
- Comprehensive audit logging
The architecture follows these zero-trust principles:
- Never trust, always verify
- Least privilege access
- Assume breach
- Verify explicitly
- Use of strong authentication everywhere
- Continuous monitoring and validation
The Challenges of Security in Web3
Web3 promises a trustless environment, but the reality is more nuanced. Decentralized systems are inherently complex, involving multiple layers of interaction—from smart contracts and nodes to wallets and bridges. Each layer introduces unique attack vectors:
Smart Contracts: These immutable programs are vulnerable to reentrancy attacks or flawed business logic. Once deployed, their code is accessible to everyone, including bad actors.
Blockchain Nodes: Operating a node can expose vulnerabilities, especially if the setup lacks proper access controls or security hardening.
Bridges and Interoperability: Cross-chain bridges, which enable assets and data to move between blockchains, have become prime targets for exploits due to their complexity and lack of standardization.
Decentralized Identity (DID): While DID systems promise self-sovereignty, they’re only as secure as the private keys that protect them.
I recall an incident where a poorly configured node setup in one of our projects led to a vulnerability that could have been catastrophic. That experience reinforced the need for zero-trust principles in every layer of the system.
Adapting Zero-Trust Principles to Web3
In traditional systems, zero-trust assumes that no user, device, or application can be trusted by default. In Web3, this principle must extend to decentralized components, creating a new paradigm I’ve started calling “Decentralized Zero-Trust.” Here’s how the principles translate:
Verify Everything, Continuously: In Web3, verification often hinges on cryptographic proofs and consensus mechanisms. However, we can extend these principles:
- For Smart Contracts: Adopt formal verification tools to mathematically prove the correctness of contract code before deployment.
- For Users and Wallets: Employ decentralized identity systems like DID to verify user authenticity without centralized intermediaries.
- For Nodes: Continuously monitor node behavior, validating that they’re adhering to protocol rules.
I remember the satisfaction of deploying a formal verification tool to a DeFi project—catching a logic bug that could have cost millions. Continuous verification is not just theoretical; it saves real money and reputations.
Least Privilege Access: Applying the least privilege in Web3 requires careful design.
- For Wallets: Limit smart contracts to access only the necessary tokens or data for a given transaction.
- For Infrastructure: Use role-based access controls (RBAC) to ensure that even decentralized infrastructure components have minimal permissions.
Immutable Logs for Forensics: The immutable nature of blockchain is a boon for zero-trust. Every transaction is logged permanently, enabling robust forensic analysis. Yet, I’ve seen teams overlook the importance of correlating on-chain activity with off-chain systems. Integrating tools that map off-chain logs to on-chain activity is crucial for comprehensive observability.
Decentralized Microsegmentation: Microsegmentation — dividing a network into smaller, isolated segments — is challenging in a decentralized environment. But we can achieve similar results by:
- Using layer-2 solutions to isolate specific types of transactions or data.
- Employing private subnets for sensitive node communications.
Practical Use Cases of Zero-Trust in Web3
Securing Validator Nodes: Operating blockchain validator nodes requires robust security. In one of my recent projects, we implemented a zero-trust framework where each node:
- Was isolated in its secure environment.
- Used encrypted communication channels for all peer-to-peer interactions.
- Was continuously monitored for anomalous behavior, with automated responses to shut down compromised nodes.
This setup came after a near-miss where a single misconfigured node jeopardized an entire cluster. The lessons learned from that scare now inform every node deployment I oversee.
Protecting Smart Contracts: In a DeFi project, we adopted zero-trust by integrating automated audits into the CI/CD pipeline. Every update to the contract required not only developer sign-off but also third-party audit checks and formal verification before deployment.
Cross-Chain Bridge Security: For a cross-chain project, we used a zero-trust model to secure bridge operations. Each transaction required multi-signature approvals, while all interactions with external chains were verified through cryptographic proofs.
Challenges and Future Directions
Implementing zero-trust in Web3 isn’t without challenges. Decentralized systems often prioritize transparency over security, creating a tension between openness and protection. Additionally, the lack of standardized tools for Web3 security means that teams must often build bespoke solutions.
However, the future is promising. Emerging technologies like zk-SNARKs (zero-knowledge proofs) and secure multi-party computation (SMPC) are enabling new ways to implement zero-trust without sacrificing decentralization. For instance, zk-SNARKs can provide verifiable proof of computation without exposing the underlying data, a perfect fit for decentralized systems.
Conclusion
Web3’s promise of a trustless future doesn’t eliminate the need for trust — it redefines it. By adopting zero-trust principles, we can build systems that are not only decentralized but also secure, resilient and future-proof.
I’ve come to see zero-trust as more than a framework; it’s a mindset. It challenges us to assume nothing, verify everything, and embrace accountability at every level. In a space as transformative as Web3, adopting this mindset isn’t optional — it’s essential. Let’s redefine what trust means and ensure that our decentralized future is both secure and sustainable.