Strong Security or Superior Consumer Experience? The False Dilemma of the Online Gatekeepers
Today’s online businesses are faced with equally important but seemingly antithetical objectives: Keeping the bad actors out while letting the good users through.
Cybersecurity professionals are constantly battling against an array of threats, from automated bots to sophisticated phishing schemes. The mission is clear: Safeguard sensitive data, protect against financial loss, and uphold the trust of customers.
Meanwhile, consumers expect seamless access to services and frictionless transactions. Whether they’re logging into their financial accounts, making purchases, or simply browsing your site, users demand a smooth and hassle-free experience. Any obstacles, such as cumbersome authentication processes, can quickly erode trust and drive consumers away to competitors.
The good news? Businesses don’t have to choose between stringent security measures and user-friendly experiences. Achieving that perfect balance of great user experience and stopping bad actors is well within reach.
Clear, Block, or Challenge
The typical process of evaluating the safety of an online session starts with the business doing some level of threat assessment and then making a determination to allow the user to move forward, deny that service, or challenge the user.
Outright blocking a good user is the most aggressive form of friction, but this creates an experience that is definitely not good for business. If good users are incorrectly determined to be bad actors (false positives), then they get completely blocked, and their only recourse is typically to call customer service and request help. This is user experience friction at its worst, and a high-cost model for dealing with the situation with a call center.
A close relative of the outright blocking approach – and one that can be almost as annoying to your genuine consumers – is to challenge a large percentage of your traffic.
This means subjecting a significant portion of users to additional authentication measures or security checks, even if they pose no apparent risk.
While this strategy aims to err on the side of caution, it often results in unnecessary friction for legitimate users, tarnishing the overall user experience. Users may find themselves repeatedly interrupted with CAPTCHAs or multi-step verification processes, leading to frustration and potentially driving them away from your platform.
Moreover, this approach adds operational complexity and overhead costs, as businesses must dedicate resources to managing and resolving user complaints and inquiries stemming from these challenges.
RECOMMENDED RESOURCE
How a Rideshare Giant Balances SMS Toll Fraud Security with Great User Experience
Behind-the-scenes Assessment of Genuine Traffic
Arkose Labs takes a different approach, one that relies on pinpointing the risk that each online session generates so that only high-risk user sessions see any active intervention. In the overwhelming majority of cases, users never see any type of challenge while the process operates seamlessly in the background.
Rather than subjecting all users to the same blanket security measures, we employ advanced technology to analyze user behavior and distinguish between genuine users and potential threats. This technology relies on a combination of factors, including user behavior patterns, device fingerprinting, geolocation data, and real-time threat intelligence.
By analyzing these diverse data points, we create a comprehensive profile of each user’s digital footprint, enabling us to detect anomalies and flag suspicious activity accurately. This granular approach allows us to tailor our security measures to the specific risk profile of each user, minimizing false positives and ensuring that genuine users can access services smoothly.
By dynamically adjusting our response based on the level of risk detected, we ensure that legitimate users face minimal friction while effectively thwarting malicious activity. In an overwhelming majority of cases, the genuine consumer will never know
they have encountered any security measures at all, as they seamlessly navigate through your website or app without interruption.
This enables your business to strike that perfect balance between the good user experience and stopping threats – while allowing any false positives to easily remediate the situation by playing through a game that takes a few seconds of their time.
Precision Targeting of Challenges
In a typical deployment, Arkose Labs will initially evaluate the threat landscape by transparently (zero friction) monitoring the session traffic and evaluating what egregious threat signals we are seeing. We then collaborate with the business to determine which of these threats have clear attack signatures that are indicative of situations where they want to challenge the user, to make sure they are bad actors and not good users.
Arkose Labs can then tune for this threat and precisely target how to challenge the traffic. This precision tuning can be based on attack signature, geolocation of the user and basically any telemetry that we collect or the customer provides to us.
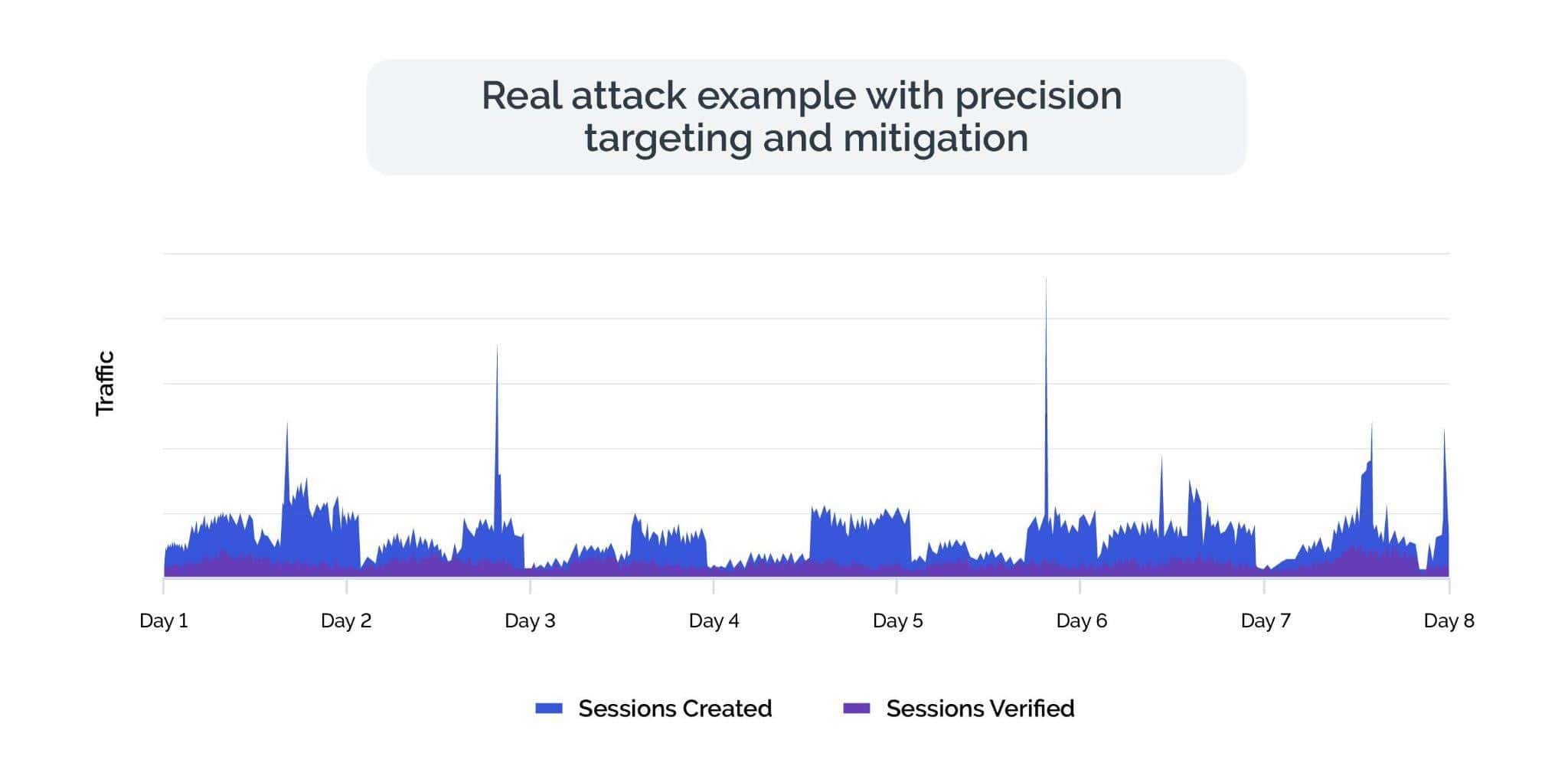
In the example above, we isolated the attack signature for two different attacks on a customer user experience. The purple line represents the good user and healthy traffic, while the dark blue spikes represent attempts to bypass our technology by simply blocking JavaScript, and the dark blue deeper wide segments represent bot-assisted human fraud farms. In both of the cases, we were able to isolate the attack signature for each attack, and provide the appropriate challenge to stop both bot and human attacks.
Suspicious sessions are presented Arkose MatchKey challenges, real-time challenges that make it difficult for cybercriminals to use automation (bots and botnets) to solve. And when attackers pivot to human labor, we leverage challenges that are time-consuming for humans to solve at scale.
Genuine consumers, however, seamlessly navigate through these challenges and quickly move on to doing what they were intending to do: interact with your online property.
By adopting this innovative approach, your business can confidently navigate the complex landscape of online security, knowing that you are effectively protecting your platforms while delivering a frictionless experience for your valued consumers.
Learn more about how to create seamless user experiences with Arkose Bot Manager.
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Liam Maxwell. Read the original post at: https://www.arkoselabs.com/blog/securing-great-consumer-experience/



