How to Prepare for a Data Breach before it Happens
Preparation is key in preventing the worst outcomes from a data breach, so it is important to have a plan in place ahead of time. Here are some steps you can take to prepare for a potential data breach:
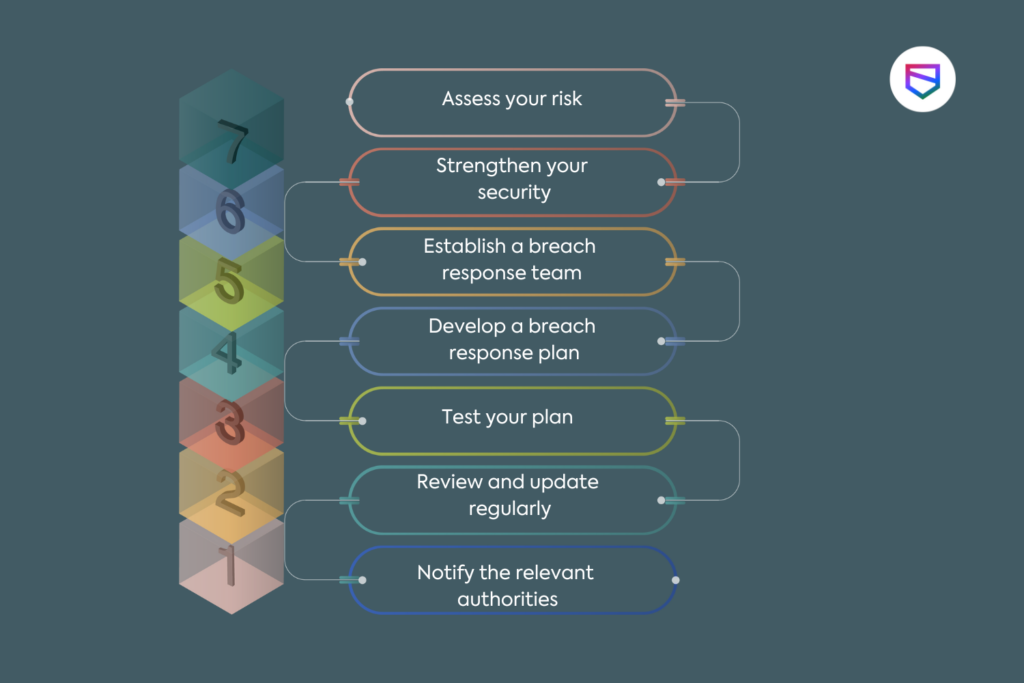
- Assess your risk: Conduct a risk assessment to identify sensitive data, potential sources of threats, and vulnerabilities in your systems and processes.
- Strengthen your security: Implement strong security measures such as encryption, multi-factor authentication, and firewalls to protect your systems and data. Regularly update and patch your software and hardware to stay ahead of the latest threats.
- Establish a breach response team: Designate a team of employees who are responsible for responding to a breach. Train them on their roles and responsibilities, as well as the latest breach response techniques.
- Develop a breach response plan: Draft a plan that outlines the steps to be taken in the event of a breach. Make sure everyone on the response team is familiar with the plan and knows their part.
- Test your plan: Regularly test your breach response plan to ensure it is effective and everyone knows what to do in an actual breach.
- Review and update regularly: Regularly review and update your security measures and breach response plan to stay ahead of the latest threats and techniques.
- Notify the relevant authorities: Be aware of the laws and regulations regarding data breaches in your jurisdiction, and have the contact information for relevant authorities readily available in case of a breach.
By taking these steps, you will be better prepared to respond to a data breach if it occurs, and you may be able to prevent it from happening in the first place.
Strategies for responding to a data breach after it happened:
When a data breach occurs, it is important to respond quickly and effectively to minimize the damage and protect sensitive information. Here are some strategies for responding to a data breach:
- Contain the breach: Take immediate action to stop the breach from spreading further, such as disconnecting affected systems from the network or shutting down affected applications.
- Investigate the breach: Conduct a thorough investigation to determine the extent of the breach and what information has been compromised.
- Notify affected individuals: If personal data has been compromised, it is important to notify affected individuals as soon as possible and provide them with information on what they can do to protect themselves.
- Implement remediation measures: Based on the results of the investigation, implement measures to prevent similar breaches from happening in the future, such as updating security protocols, patching vulnerabilities, and improving access controls.
- Communicate with stakeholders: Keep stakeholders, including customers, employees, and regulators, informed about the breach and the steps being taken to respond to it.
- Review and improve: After the breach has been contained and the immediate response measures have been taken, take time to review the response process and make improvements where necessary.
- Seek professional help: Consider seeking the assistance of a breach response consultant or cybersecurity professional to help you navigate the complexities of responding to a data breach.
It is important to remember that the steps taken during a breach response can have long-term consequences, so it is crucial to act quickly and effectively to minimize damage and protect sensitive information.
Real-life examples of successful data breach responses:
Data breach responses can be successful or unsuccessful. The first step to effectively responding is having a plan ready in advance, as well as resources available when you need them. Not having a plan will lead to extended problems and increased costs of incident response. Here are several real life examples of successful data breach response efforts:
- Target: In 2013, Target suffered a massive data breach that compromised the payment card information of millions of customers. The company quickly contained the breach and launched an investigation, informing customers and offering free credit monitoring services to those affected. The response was widely praised for its transparency and speed, and Target took steps to improve its security protocols to prevent future breaches.
- Equifax: In 2017, credit reporting agency Equifax suffered a massive data breach that compromised the personal information of millions of customers. The company was criticized for its slow response, but eventually, it hired a third-party cybersecurity firm to help with the investigation and notification process. Equifax also offered free credit monitoring services to affected individuals and reached a settlement with the Federal Trade Commission and state attorneys general.
- Marriott: In 2018, hotel giant Marriott suffered a data breach that compromised the personal information of hundreds of millions of customers. The company responded quickly, launching an investigation and informing affected individuals. Marriott also offered free credit monitoring services and took steps to improve its security protocols to prevent future breaches.
The recent news about the Chinese hackers who stole information from hundreds of companies has been all over the news, but not everyone is aware that many other similar cyber attacks on large organizations preceded this attack. In some cases, as in the case of McAfee and its employees, after being hacked they paid a $100m ransom in bitcoins to obtain back their stolen data. Unfortunately, we are still far away from having a real-time electronic defense that can ensure 100% protection against such attacks. Even if these attacks were detected earlier than they actually happened, it would take an extended period of time for their damage to be fully assessed or mitigated. In other words, cyber security awareness at all levels will always be an issue that requires serious attention so it does not happen again in the future.
Conclusion:
Unlike other security threats, data breaches are not always immediately obvious. In many cases companies don’t know they’ve been breached until well after the fact. Effective responses to these incidents can be difficult to predict, but there are a few key things that successful companies have in common. Data breaches are not a new phenomenon. They have been around for decades, and they continue to grow in number and severity. While no two data breaches are the same, there are several commonalities that can help predict how successful your company’s response will be.
Recommended Reading:
Assumed Breach Assessment Case Study: Uncovering WeSecureApp’s Approach
Automation and Scalability in Red Team Assessments
Don’t Leave Your Security to Chance: The Importance of Zero Security
The post How to Prepare for a Data Breach before it Happens appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Naimisha. Read the original post at: https://wesecureapp.com/blog/how-to-prepare-for-a-data-breach-before-it-happens/



