Slack Security Breach Highlights Risks of SaaS Session Hijacking
Slack Attack: Employee Tokens Stolen
On December 29, 2022, workforce collaboration application, Slack posted a security update that announced the discovery of unauthorized access to some of its code repositories. The company stated that an unknown individual or group had obtained Slack employee session tokens and used them to gain access to the company’s private GitHub repositories and steal some of the code. The incident had reportedly started on December 27, 2022.
Session tokens are meant to improve the authentication experience of legitimate SaaS users by enabling user access over a longer period of time. But they are also vulnerable to abuse by bad actors. Hackers prize them because they can use the tokens to gain access into your critical SaaS apps, such as Salesforce, O365, and Workday, which enable them to steal data.
What is Session Hijacking?
Session hijacking is a technique where a hacker takes control of a user’s active session and uses it to gain unauthorized access to the user’s account or device. Once authenticated, it allows attackers to bypass multi-factor authentication (MFA) and single-sign-on (SSO) controls.
When a session is hijacked, a hacker is able to obtain a copy of a user’s session cookie, which is a small piece of data that is sent from a website to a user’s computer and is used to identify the user’s session. With that cookie, a hacker can impersonate the real user and perform actions on the website as if they were the user.
Once an attacker has a session token, they have persistent access to it until the token is revoked or renewed. Additionally, once in, a hacker can launch lateral attacks on different systems including cloud databases and workloads.
Session hijacking is a common method of stealing tokens (Slack does not say how the tokens were stolen). Typically, tokens can be pilfered by installing malware on a victim’s device or browser. Successfully launching a phishing attack is another way to get a victim’s tokens. A hacker may also be able to obtain a user’s session cookie through social engineering techniques such as phishing, in which the hacker tricks the user into revealing their login credentials.
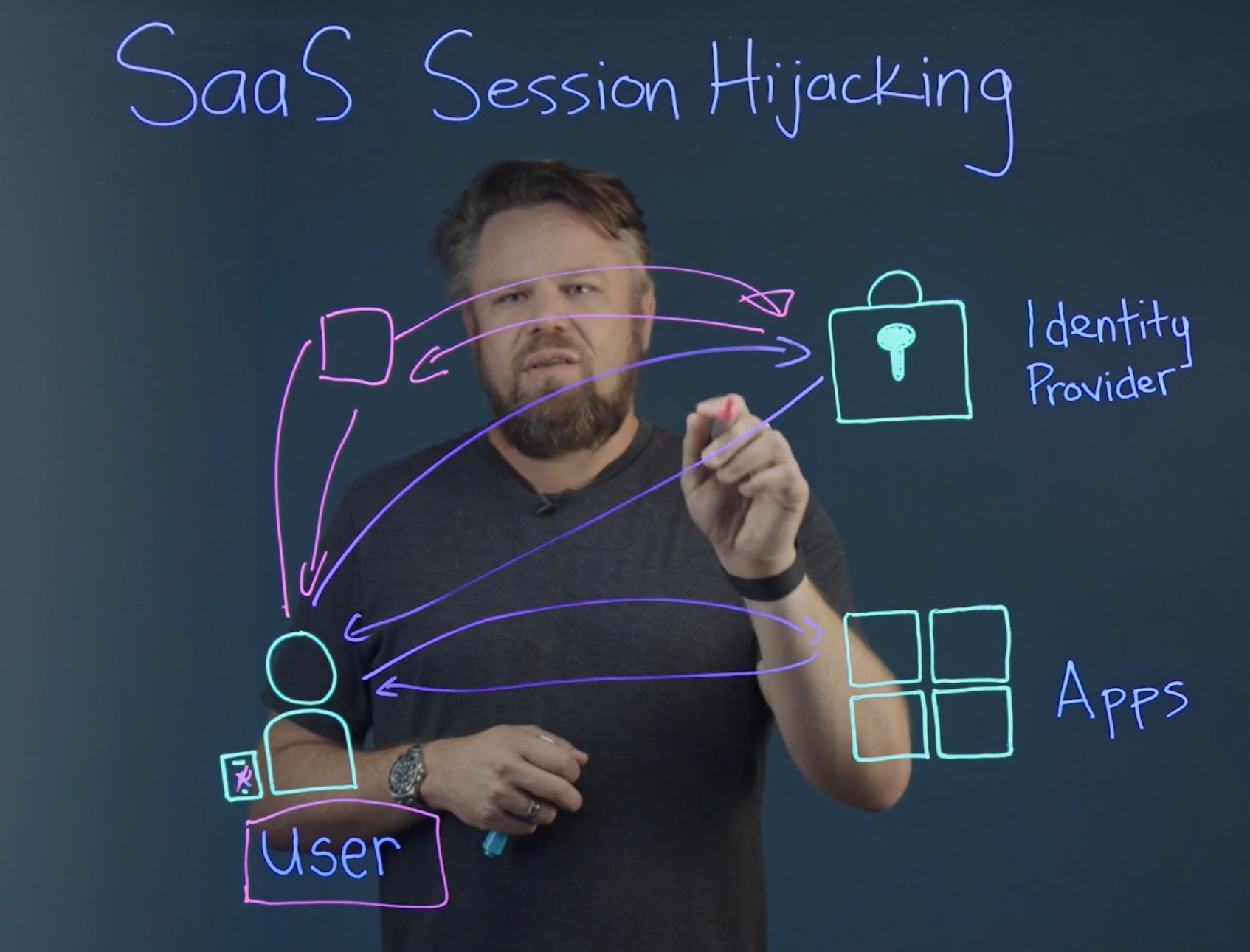
(Watch Glenn Chisholm, Obsidian CPO and co-founder, explain session hijacking basics.)
Why SaaS Session Hijacking Matters
It’s all about data — data that resides in, is processed in, and shared between SaaS applications. SaaS applications are designed to be interconnected, creating a seamless user experience with data synchronization between multiple services. This gives users the opportunity to augment applications with new features, automate manual workflows, and get work done more effectively. But at the same time, this interconnected web of applications makes already complicated SaaS environments even more difficult for security teams looking to minimize risk and secure sensitive data. Every integration requires a different set of permissions and level of access, and every core SaaS platform has a unique, non-standardized approach to handling these connections.
This attack on Slack’s private GitHub repositories is not the first of its kind. In fact, it’s an increasingly common mechanism attackers are leveraging to gain access to sensitive data. As evidenced by a recent string of newsworthy compromises such as the Okta breach, attackers are increasingly targeting SaaS integrations as an entry point for executing larger, more damaging campaigns. Although the importance of managing this vulnerability is well recognized, security teams often lack a fundamental understanding of which integrations are deployed across their SaaS environment, what excessive risks are posed by those connections, and where their data is exposed. Gaining visibility and control of this sprawling, interconnected landscape is only possible with the right tooling.
How Obsidian Helps Customers Defend Against SaaS Session Hijacking
To accurately identify token theft and other compromises within your SaaS environment, Obsidian begins with a consolidated understanding of your users, activities, permissions, and configurations from across your core applications. This data is normalized, enriched with context and threat intel, and ultimately populated into a central knowledge graph of your SaaS environment. This serves as the foundation for our models to detect malicious activity in its earliest stages, giving your team the chance to mitigate threats before sensitive data is being exfiltrated.
Because Obsidian carefully examines and analyzes details about the users and client connections to the identity provider and SaaS applications, we detect the potentially subtle anomalies consistent with token capture and reuse by an attacker. When this is identified, our platform immediately flags the event for your security team, providing a single timeline of events related to the attack and a clear path for prompt remediation.
You can learn more about how you can defend against Session Hijacking attacks here.
Get a Free SaaS Security Risk Assessment
Want to see how your SaaS environment stacks up? Get a free SaaS security risk assessment that comes with a full report of your SaaS posture with actionable steps you can take to mitigate SaaS session hijacking attempts.
The post Slack Security Breach Highlights Risks of SaaS Session Hijacking appeared first on Obsidian Security.
*** This is a Security Bloggers Network syndicated blog from Obsidian Security authored by Emile Antone. Read the original post at: https://www.obsidiansecurity.com/blog/slack-security-breach-risks-of-session-hijacking/





