“Don’t let your ignorance make you vulnerable to IoT attacks.”
Introduction
Given our growing reliance on connected devices, it’s critical to take into account any potential hazards and weaknesses. The ongoing advancement of technology has led to a sharp increase in both the supply and demand for IoT devices. People now depend on these technologies even for the most basic everyday tasks. By connecting everyday objects to the internet and enabling them to speak with one another and with us, the Internet of Things (IoT) has radically changed how we live and work.
IoT risks are increasing as more people utilize IoT devices. Because IoT devices are built to connect by nature, the risks connected with them are multiplied over the entire network. Both the IoT devices themselves and how they interface with existing organizational systems are designed with hazards. IoT devices are becoming increasingly valued and significant components.
IoT devices come with inherent dangers that affect both the devices themselves and how they work with other organizational systems. All security teams must place a high focus on defending IoT devices from assaults as they become more valued and significant components of organizational and industrial infrastructure.
What are IoT Devices?
IoT devices are internet-connected devices with the ability to gather, send, and receive data. Homes, offices, factories, and cities are just a few places where you can find these gadgets. Smart appliances, security cameras, wearable technology, smart thermostats, and connected autos are a few examples of IoT gadgets. These devices frequently communicate over the internet with one another and with centralized servers, enabling remote monitoring and control of them.
IoT devices offer advantages such as improved convenience, safety, and efficiency. IoT devices could potentially be hacked or used to gather private information, therefore there are worries about their security and privacy.
Impact of IoT Device Vulnerabilities
It is crucial for companies and individuals to prioritize cybersecurity when it comes to IoT devices. Implementing strong passwords, secure firmware updates, robust encryption protocols, and proper authentication measures can significantly reduce the risk of cyber attacks and protect sensitive data.
A hacker’s mindset will never change, regardless of how far technology develops. The cycle of attempting a cyberattack continues with the discovery of network or system flaws, the exploitation of vulnerabilities, and repetition! The cyber attack surface has now increased in size as a result of the introduction of smart linked gadgets.
IoT devices are primarily vulnerable because they lack the necessary built-in security features to resist attackers. The main culprits are the constricted environment and the limited computational capability of these devices.
IoT device vulnerabilities could be exploited by cybercriminals to gain control of the devices and use them to attack critical systems. In addition, IoT issues are frequently the root cause of privacy infractions that give rise to harsh legal repercussions for breaking regulations like the GDPR, CCPA, HIPAA, and PCI DSS.
Top Vulnerabilities of IoT Devices
IoT devices have streamlined and improved our lives, from connected cars to smart thermostats. But as connected devices proliferate, vulnerabilities are more likely to appear. The top IoT device weaknesses are listed below:
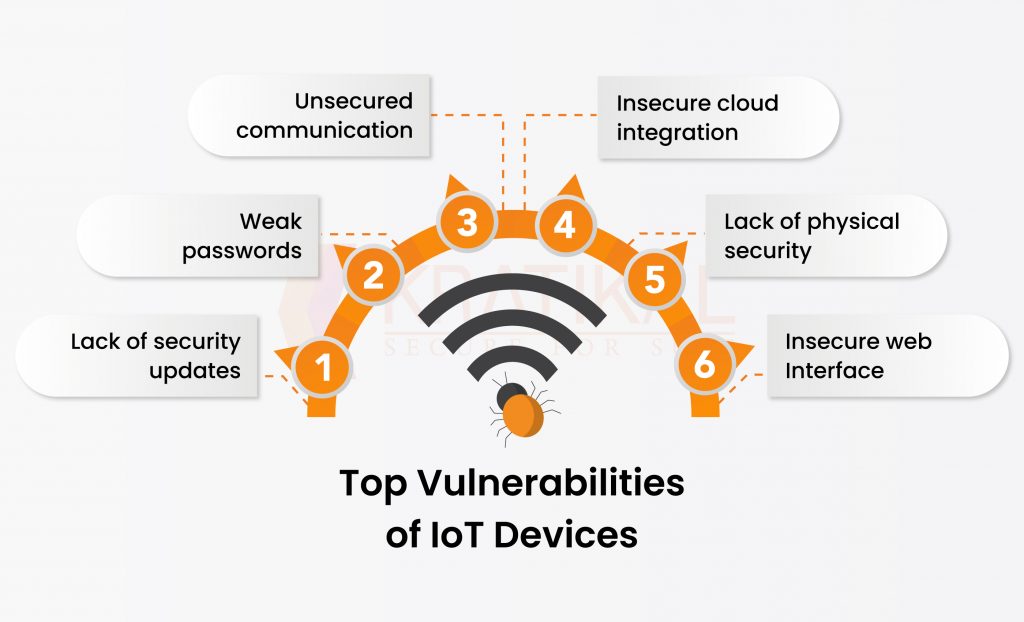
- Lack of security updates: Many IoT devices are not designed with security updates in mind, meaning that once a device is released, it is rarely updated with the latest security patches. This leaves devices vulnerable to attacks that exploit known vulnerabilities.
- Weak passwords: Many IoT devices come with default passwords that are either weak or easy to guess. This makes it easier for hackers to gain access to the device and use it to launch further attacks.
- Unsecured communication: Many IoT devices communicate using unencrypted protocols, This can make it vulnerable to interception and tampering such as SSL downgrade attack by malicious actors.
- Insecure cloud integration: Many IoT devices rely on cloud-based services to store and process data. If these services are not secured properly, it can leave the device vulnerable to attacks. Attacks such as directory listening can also expose sensitive data to threat actors.
- Lack of physical security: Some IoT devices have poor physical security measures, such as weak or non-existent passwords on the device itself, making it easy for hackers to gain access to them. This is especially concerning for devices that are located in public places, such as smart city sensors or parking meters.
- Insecure web Interface : Insecure web interfaces on Internet of Things (IoT) devices can pose a serious security risk to individuals and organizations. These interfaces are often used to access and control various functions of the device, such as changing settings, monitoring performance. However, if these interfaces are not properly secured, they can be exploited by malicious actors to gain unauthorized access to the device and potentially compromise its functionality or data.
To protect against these vulnerabilities, it is important to ensure that IoT devices are properly secured and updated with the latest security patches. It is also important to use strong, unique passwords and to use encrypted communication protocols whenever possible. Additionally, it is important to ensure that any cloud-based services used by the device are properly secured. Finally, physical security measures should be in place to prevent tampering with the device.
Conclusion
In order to safeguard an organization’s IT infrastructure, Kratikal, a Cert-In Empanelled Organization provides a comprehensive array of VAPT services, including network penetration testing, application penetration testing, internet of things (IoT), cloud penetration testing, and many others.
Implementing IoT devices could appear to be all fun and games if you are unaware of how vulnerable the newest technology might make the cybersecurity of your company. Remember that it is always preferable to prevent problems than to try to fix them, so do not wait for a Disastrous cyberattack to happen.
What opinions do you have regarding the top vulnerabilities for IoT devices? Post your comments in the space provided!

The post “Don’t let your ignorance make you vulnerable to IoT attacks.” appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Deepti Sachdeva. Read the original post at: https://kratikal.com/blog/dont-let-your-ignorance-make-you-vulnerable-to-iot-attacks/





