Tackling the Rise of Insider Threat Risk After the Great Resignation
Earlier this month, the team over at security firm Kroll released its “Q3 Threat Landscape: Insider Threat the Trojan Horse of 2022” report on the rise in insider threat incidents over the past year and a half, bringing added attention to a number of troubling trends facing security teams.
According to the researchers, “In Q3 2022, Kroll saw insider threat peak to its highest quarterly level to date, accounting for nearly 35% of all unauthorized access threat incidents.”
This figure beats out the 24% from Q2 2022, and even the much higher Q1 2021 when it hit a whopping 31%.
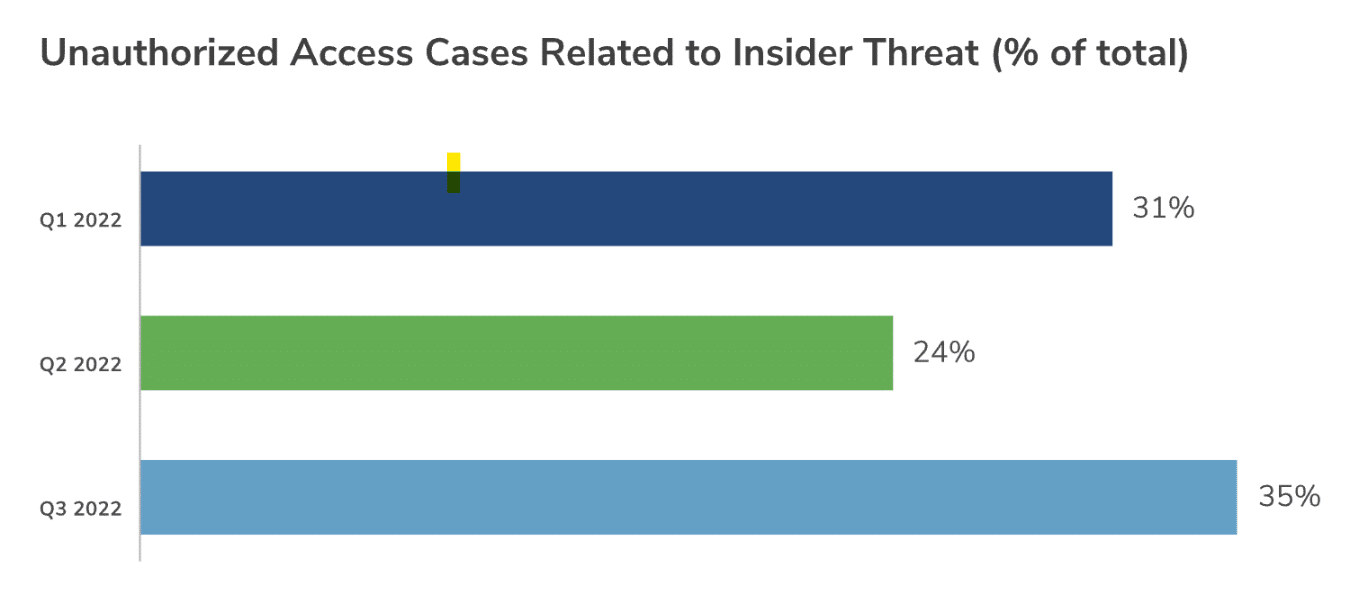
Source: Kroll’s “Q3 2022 Threat Landscape: Insider Threat, The Trojan Horse of 2022”
What happened during this period that led to such a significant spike in the cases of insider threat incidents?
Leavers Raise the Level of Risk
If Q1/2021 and H1/2022 got to claim the title of The Great Resignation with remote work opening up a world of opportunities, then H2 2022 is more likely to get hit with a less glamorous designation like The Disappointing Downsizing.
While they may be on opposite ends of the spectrum in terms of possibilities/outcomes for workers, both periods have marked a challenging time for organizations when it comes to keeping their data secure from soon-to-be-former employees.
In the Joiner-Mover-Leaver (JML) life cycle, a person who leaves or is about to leave (aka a leaver) an organization has a much higher probability of harming their employer than joiners and movers.
The reason for this is that the leaver simply has more incentive. In the less malevolent scenarios, a leaver is more likely to want to take valuable bits of data like client lists or other helpful information with them to their next role. Or if they are leaving under less than ideal circumstances, then they may want to cause harm like deleting important data, think IP or customer info, or worse.
In Q1 2021 as many were working remotely and IT security was still playing catch up with getting controls in place, stealing company data was relatively easy, and there was a spike in incidents as significant numbers of these folks sought out greener pastures. Now we see even higher numbers as companies underwent sizable layoffs during Q3 and into Q4, an upsetting trend that will hopefully abate during Q1 2023 but nobody is quite sure of where we are heading yet.
What we do know is that insiders pose a particularly difficult challenge for organizations.
Any compromise is a rough day at the office, but an insider threat incident comes with additional risk factors that the external actors do not.
Insider Threat has Additional Risks
For starters, the fact that the insider has legitimate credentials and privileges means that identifying the threat can be particularly difficult.
Attackers have focused much of their efforts on credentials and access that the identity’s credentials grant them in recent years. This is due in part to the shift to the cloud where access and what one can do with that access are far more dependent on your identity rather than being in a physical location or other forms of perimeters that were more impactful in the past.
In the Kroll report, they found that credentials are increasingly being exploited for the initial access:
Valid accounts for initial access was another area in which Kroll observed growth from Q2 to Q3, which is where legitimate credentials are used to access an account. Cybercriminals using this method may take over an account in several different ways, such as purchasing credentials from information-stealing malware or credential-stuffing attacks.
Insiders also already know where all of the best stuff to steal/harm is located. They can use their insider knowledge to avoid canary tokens or honeypots. With the right privileges, or using privilege escalation tactics like role chaining, an insider can easily make their way to their target data undetected.
And the costs of failing to detect a malicious insider can be high.
According to the Ponemon Institute’s “2022 Cost of Insider Threat Global Report”, it cost North American organizations an average of $17.53 million to resolve insider threats over a 12 month period.
This is due in part to factors including:
- The larger number of credentials that are being stolen,
- Value of data being compromised
- Legal/regulatory costs
- Loss of consumer confidence/ a hit to their reputation
Given these challenges and significant potential outcomes, security teams need to build a strategy to assess their risk and mitigate it.
5 Steps to Mitigating Insider Threat Risk
As noted above, the insider’s legitimate access is one of the riskiest aspects in dealing with this threat.
Here below are a couple of the first steps that security teams should take for taking on their insider threat.
-
1. Understand Your Access Picture
With the massive expansion of apps and services in the cloud, organizations now have to deal with more identities than ever before.
Each of these identities have layers of different kinds of access privileges that define what they can access and what they can do with that access, ie. admin, read, write, etc.
Gaining granular visibility over all the access in the organization is an essential first step to taking control of it.
You need to understand:
- Who can access which assets
- Who has privileged access
- What are the various paths that access privileges are granted
- Can an identity escalate their privilege in unexpected ways because of say membership to groups or roles that they are able to assume?
Relying on your Identity Provider (IdP), Okta, Ping, or Azure AD, only shows you part of the picture from the identity side of the equation. If you are not continuously collecting data from multiple sources, from the IdP to the apps/services, then your visibility is not comprehensive and therefore not sufficiently effective. In this case, you only see what is declared in your IdP, and not necessarily your de facto access.
-
2. Reduce Privileges to Narrow Your Threat Surface
The more privileges an identity has, the more opportunity there is to exploit it. This counts for both the insider and for an external actor that compromises your employee’s credentials.
Limiting privileges to only the level that an employee needs to do their job, aka Least Privilege, is a key first step. But deciding which privileges to revoke needs to be based on data if it is going to be effective.
Two factors to consider here:
- Has the employee changed roles and do their current privileges match their job description?
- Is the employee actually using their provisioned access privileges?
By looking at the access privilege usage activity data, we can get to our answer pretty quickly. If a privilege has not been used in say 30, 60, 90 days, then we can assume that it has gone stale, and therefore it is safe to revoke without impacting productivity.
Using this approach, we can tackle challenges like privilege sprawl where an employee retains access that they no longer need over their time at the organization, and deal with risky excessive privilege in general, reducing our threat surface to be a harder posture to break.
-
3. Eliminate Partial Offboarding
When an employee leaves their organization, the only thing we want them to take with them are fond memories. Unfortunately, due to a lack of visibility, employees can often retain access to some of their assets like valuable customer data or even private repositories.
In these cases, they will be off-boarded on some of the apps/services through the IdP based on the declared access. But then other apps/services will be missed. A classic example is that the user has their access to AWS revoked through the IdP, but then retains local IAM user access or still has their personal GitHub account with access to repositories because that identity was not properly merged with the user’s profile in the IdP.
The way to handle this is by not depending solely on the IdP but once again connecting with all the apps/services across all your cloud environments, identifying who has access to what.
-
4. Eliminate 3rd Party Access Risk
Similarly to our employee offboarding issue, as organizations end relationships with 3rd parties that they have shared access to data with, they need to be able to know who has access to what and be sure that they removed it.
Often in these instances, access will be granted directly to the files or services in question, and not through an IdP. In the most basic of cases, a Google Drive or Microsoft SharePoint folder is shared with a freelancer and then kept accessible indefinitely because nobody ever goes in to revoke the access.
Understanding who can access which assets by looking at the identity is important, but we also need to understand it from the asset’s point of view. That means seeing what is accessible by who. The results of such a search may be surprising.
Use the same rules of looking at activity and figuring out if access is still relevant, and remediate accordingly.
-
5. Secure Against IdP Impersonation Attacks
Not to harp too much on the IdPs, but these systems are essentially the keys to the kingdom. Like other Identity and Access Management (IAM) systems we depend on them for managing our identities and associated access.
However, these systems need their own layer of security to protect them from attacks.
If a disgruntled employee on their way out decides to use their privileges to carry out malicious actions within the IdP, they can have severely negative impacts on the organization, potentially maintaining persistence and access even after they are gone.
A smart operator may try to hide their actions by exploiting risky design features in the IdPs and impersonating other users or manipulate the logs in an attempt to throw off the security team.
Using Identity Threat Detection and Response (ITDR) tools, organizations can detect threats to their IAM systems and coordinate their responses with their existing SecOps playbooks for faster, more efficient remediations.
Prepare for Risk but be Considerate
For security teams, turnover comes with its fair share of challenges. And this can be difficult.
But having to leave a job unexpectedly and face a rocky job market is much more difficult.
Even as we prepare for shake ups, we need to be cognizant of the fact that we are dealing with people, our colleagues, who need to be treated not with suspicion but with compassion.
If we are following best practices and technologies to catch malicious actors, then we can harden our posture to mitigate risk, detect active threats, and respond effectively when issues do arise.
To learn more about mitigating insider threat risk and implementing ITDR, contact us for a Free Assessment of our ITDR Platform.
The post Tackling the Rise of Insider Threat Risk After the Great Resignation appeared first on Authomize.
*** This is a Security Bloggers Network syndicated blog from Authomize authored by Gabriel Avner. Read the original post at: https://www.authomize.com/blog/tackling-the-rise-of-insider-threat-risk-after-the-great-resignation/




