Attack Path Analysis: Breaking Down Paths To Your Data
Reading Time: 5 minutes
If you’re not focused on identity and access controls, then you are running blind to today’s threat landscape. Today, identity is what creates a pathway to your sensitive data.
Many organizations are still speaking the language of firewalls, antivirus, endpoint protection, and vulnerabilities, yet cloud infrastructure is entirely different from that of legacy systems. Attack methods are different and the way bad actors move through your environment is different – so bringing old security concepts and solutions to this ball game isn’t going to cut it.
Today, it’s not just users accessing your data. Non-person identities are a new frontier proliferating in your environment– taking on service principals, roles, access keys, functions and more.

These entities have vast over entitlements, as sometimes security isn’t the focus behind developers work. In reality, only about 3% of entitlements granted are actually used – that is just unnecessary increased attack surface. Sometimes it’s easier to over indulge in privilege to allow seemingly easier and quicker workflows.
All this privilege, permissions and access are what make cloud identities the perfect thing to exploit. Bad actors often start with a low-level identity, and then exploit permissions to move laterally through an environment. As they laterally move through your environment, they gain a level of permissions poised to cause irreparable damage.
One common concern is privilege escalation. Privilege escalation regularly goes unnoticed, especially in a complex cloud environment where companies already have difficulty gaining visibility into their internal users, identities, pieces of compute, services, and actions. A bad actor could spend days, if not weeks, inside your environment and you wouldn’t even know it.
What is Attack Path Analysis?
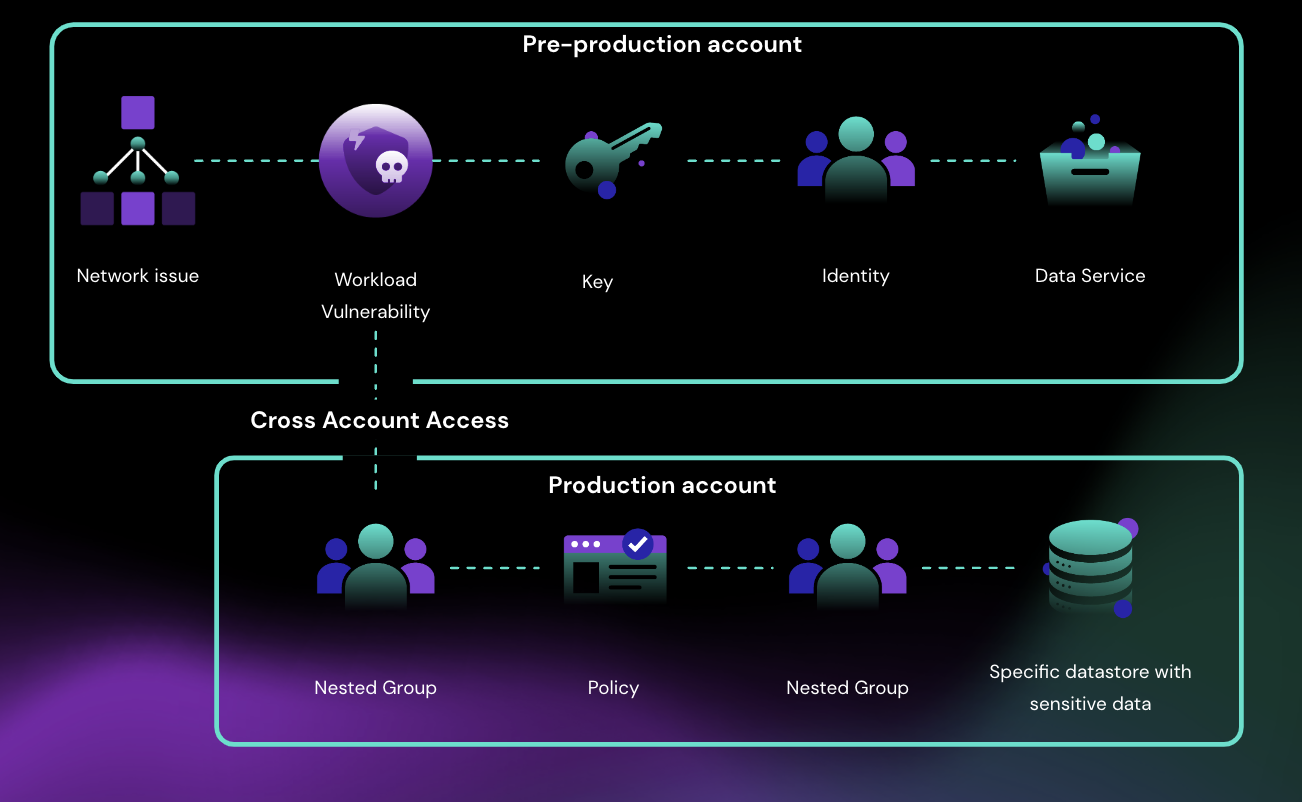
Attack path analysis is the process of automatically detecting and simulating all possible pathways to your data. So much tooling today addresses one point risk, be it workload security or identity and entitlement management. However, identity, workloads, data, and your platform configurations all are interconnected in the cloud, and compound together to create attack paths to your data. Attack path analysis aims to reveal how all these interconnected factors combine to create exploitable pathways. This is the first step, and it enables your teams to break these attack path ‘chains’ and remediate risks.
An attack path follows the following steps: recon, infiltration, lateral movement, exfiltration, and impact. Automatic analysis examines once someone is in, what is the possible movement and escalation in your environment – this is the ‘lateral movement’ aspect of an attack path. Mitigating opportunity for lateral movement is key.
Why Do You Need Attack Path Analysis?
Previously, breach prevention was all about understanding how someone can enter your system and breach your network. This put a lot of focus on vulnerability management to maintain a secure perimeter. In the cloud, breach prevention is less about vulnerabilities and networks, and more about once someone is in your environment, what can they do? Can they access a sensitive datastore? Can they access an overprivileged identity? Attack path analysis answers these questions.
Most organizations are running blind to the risks in their cloud. It feels like an impossible task to see every possible pathway or connection between compute, roles, policies, permissions, and data. However, you cannot protect what you cannot see. Illustrating an attack path is critical in finding that turning point (be it a trust relationship or indirect privilege escalation capabilities) that allows a serverless function in a Sandbox account to access customer files in Production.
How Does Attack Path Analysis Work?
At Sonrai, we approach attack path analysis in four parts:
How can they get in?
How can they move laterally?
What can they access?
How sensitive is what they can access?
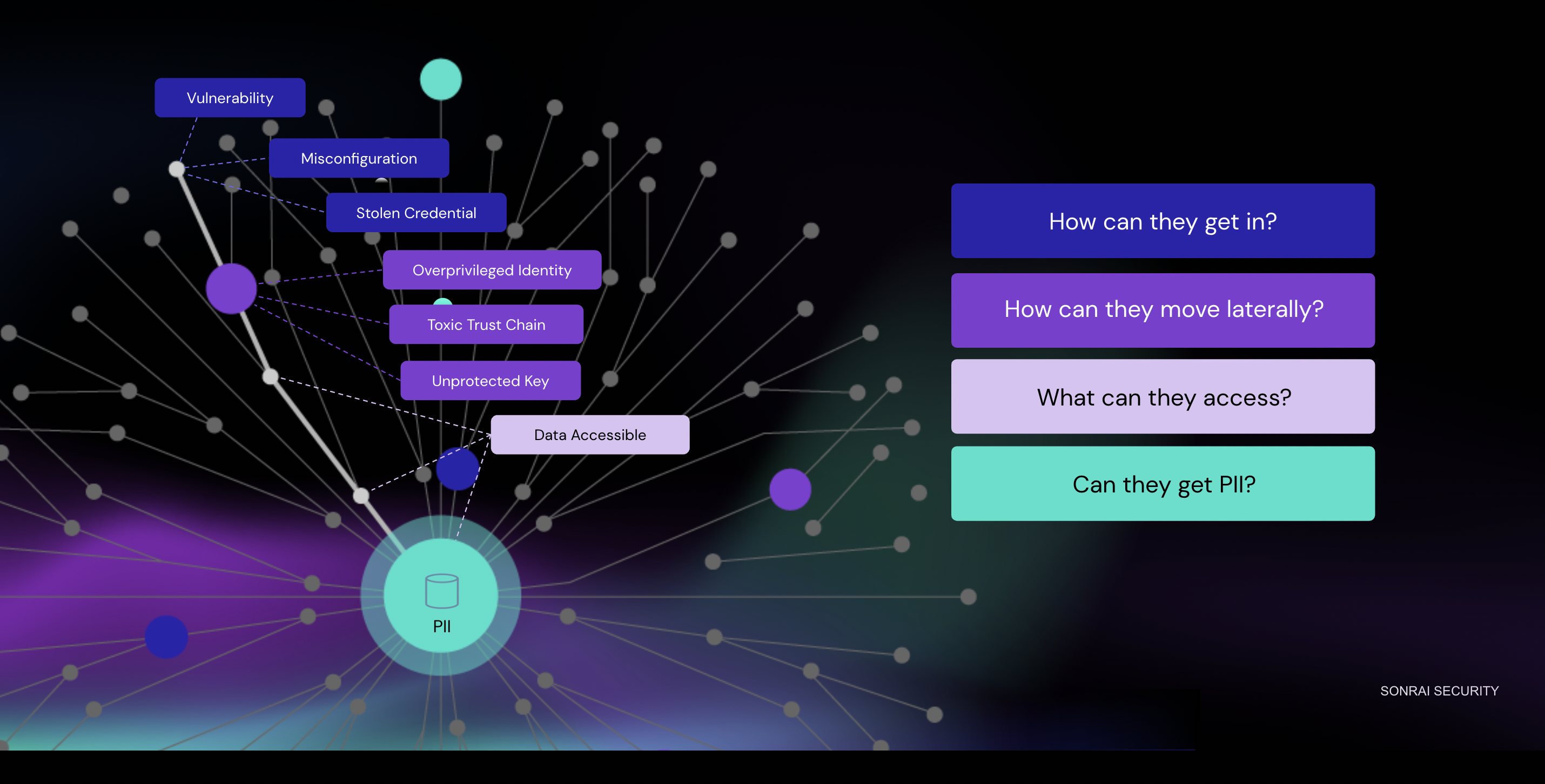
Core to Sonrai Dig is our patented identity graphing and analytics. On a nightly basis, we simulate every attack path model possible in your environment and present it in an easy-to-use dashboard. How?
By discovering what lateral movement is possible in your cloud. Our deep visibility into every connection between identity and data reveals the effective permissions (end-to-end) of each identity. The reality is that teams and manual efforts cannot keep up with the scope of all 37,000 possible actions in the cloud, and the scale at which new policies and individual actions are assigned to identities – we measure 17 new permissions a day. Teams need to lean on automation to address this scale issue, hence the value in automated attack path analysis.
What makes Dig different is its ability to detail where an attack path ends. In the cloud, where an attack path begins (with a vulnerability, or a network misconfiguration) matters less than where an attack path ends. Dig can detail the exact datastore at the end of an attack path, what it is through data classification, and how valuable it is to your business. Or maybe, there’s an overprivileged identity with the ability to wipe out a database through a policy. Dig can detail what policy gives this identity access, but also interpret the specific actions possible as a result of it – this is unique to Dig.
To better understand this capability, we’ve captured examples from our product:
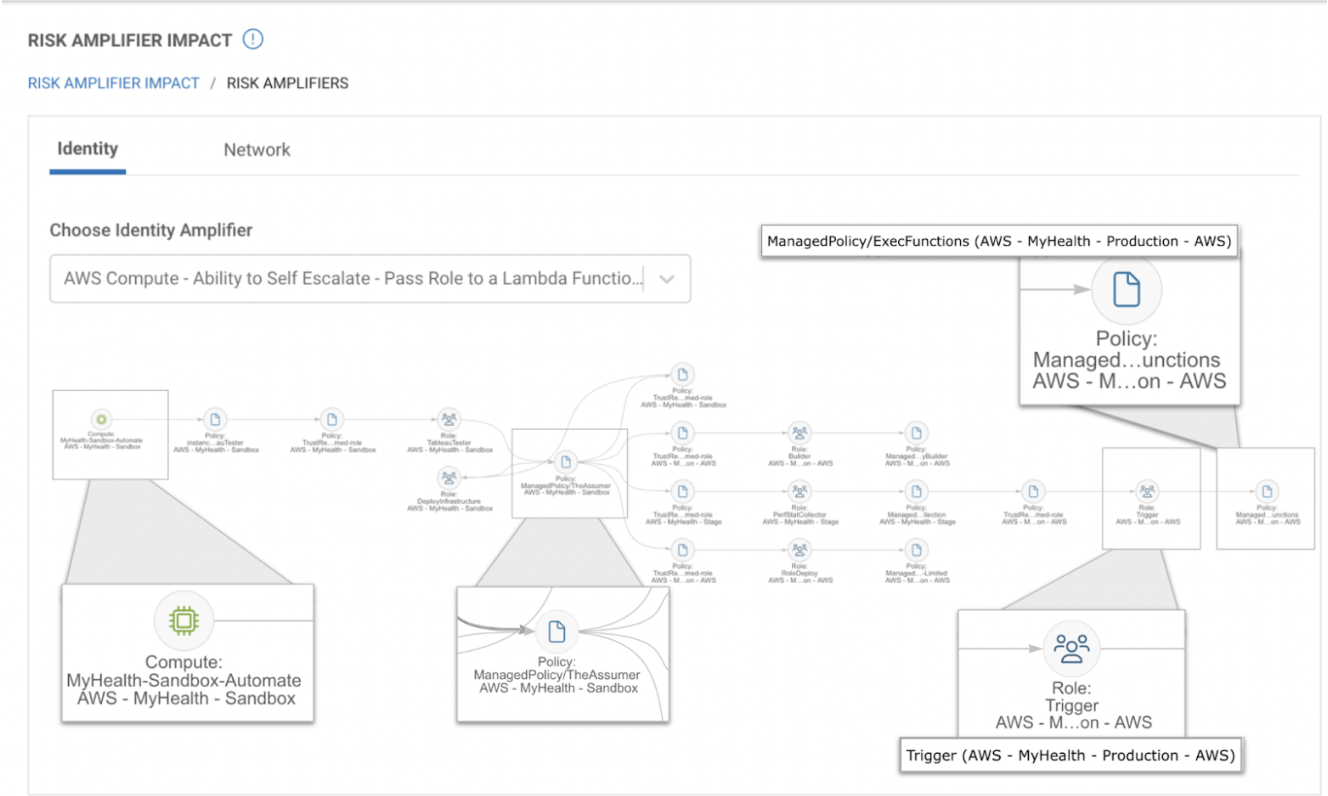
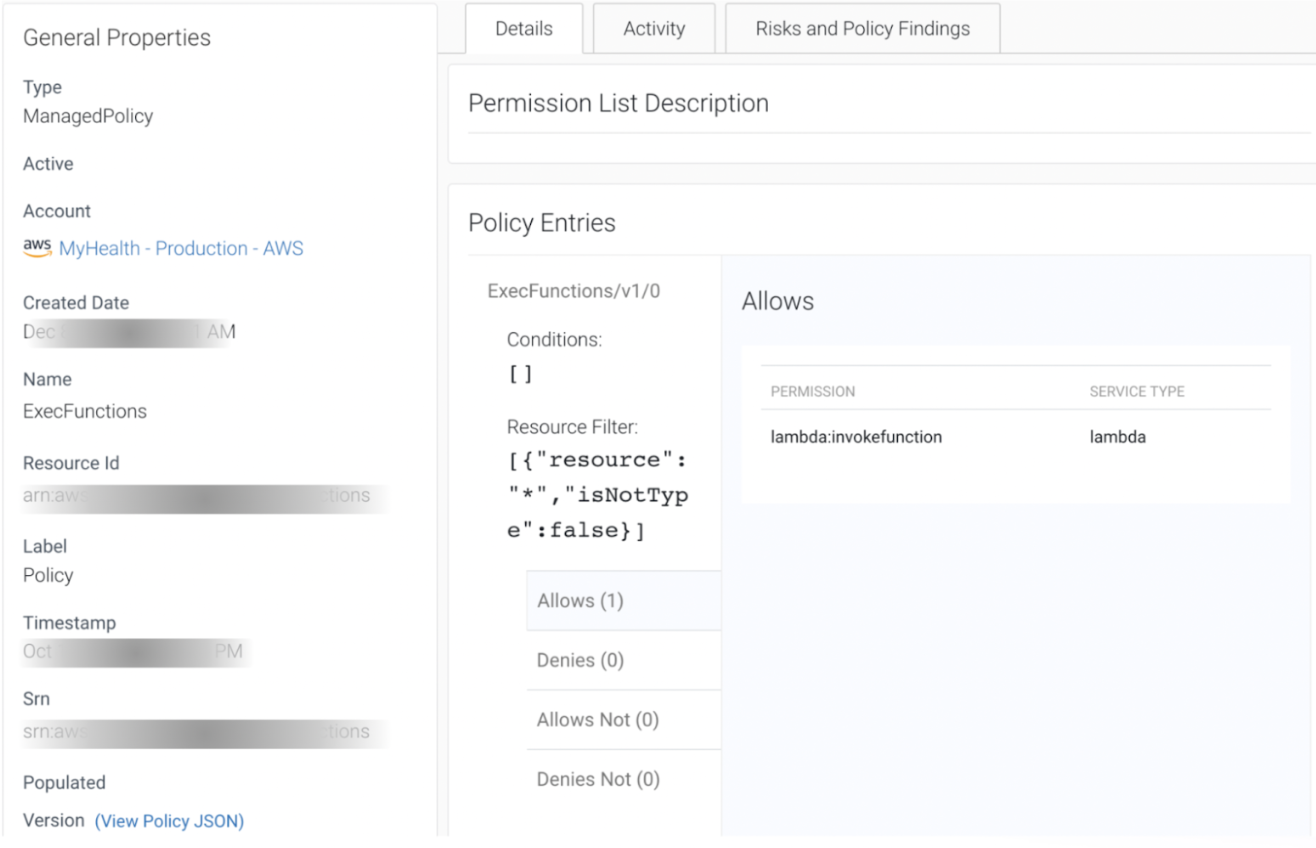
Break Down the Attack Paths To Your Data
You want to find risks before an attacker has time to capitalize on them. With attack path analysis and patented identity analytics, your organization can break the permission chains leading to your data.
Of course, not all risk is created equal, as privilege and data sensitivity come in a gradation. Dig’s insight into these unique risk levels allows your organization to better understand business impact, and prioritize remediation accordingly.
Teams are inundated and alert fatigue is universal. Having insight into what attack paths are the most pressing allows your team to address top concerns first.
See what an attack path looks like in the cloud in this attack path simulation blog.
*** This is a Security Bloggers Network syndicated blog from Sonrai | Enterprise Cloud Security Platform authored by James Casagrande. Read the original post at: https://sonraisecurity.com/blog/attack-path-analysis-breaking-down-paths-to-your-data/





