Product Update – SafeBreach Introduces New Ransomware Encryption Attacks
The 2022 Verizon Data Breach Investigations Report (DBIR) highlighted the continued challenge posed by advanced threat actors leveraging ransomware to target enterprises for financial gain. 2021 saw the highest-ever increase in the use of ransomware with the emergence of several new ransomware trends, including supply-chain attacks, double extortion, and ransomware-as-a-service (RaaS), to name a few.
Security researchers have now identified several threat actors deploying ransomware strains that use intermittent encryption technology to target and stealthily infect victim computers more efficiently. Intermittent encryption is a new method where the ransomware strain only partially encrypts files using either a random key or in a regular pattern. This allows them to more speedily encrypt files and avoid detection by ransomware detection software.
The SafeBreach breach and attack simulation (BAS) platform has always provided a wide variety of ransomware simulations to help enterprise security teams comprehensively prepare for ransomware attacks, including:
- Ransomware execution attacks—a safer version of ransomware defense validation
- Scenarios based on critical US-CERT and FBI Flash alerts that focus on relevant ransomware threats
- The ability to create new custom attacks based on threat intelligence you trust
In response to these recent developments, we are excited to announce NEW enhancements in the SafeBreach platform that will enable security teams to better prepare against complex ransomware behavior like ransomware encryption.
Ransomware Encryption Attacks
The 100+ newly introduced ransomware encryption attacks will now allow teams to simulate the actual ransomware behavior making the attack more realistic and increasing the validity of the results – all in a safe and controlled way without risking production environments. These attacks were made possible by the SafeBreach Labs team, who reverse engineered the latest ransomware to identify various parameters including:
- File types – The file types typically targeted or excluded from attacks
- File extensions – The extensions typically appended to encrypted files and folders by ransomware attackers
- Encryption algorithm – Algorithms typically used by attackers for ransom
- Encryption key – The encryption key used to encrypt the files
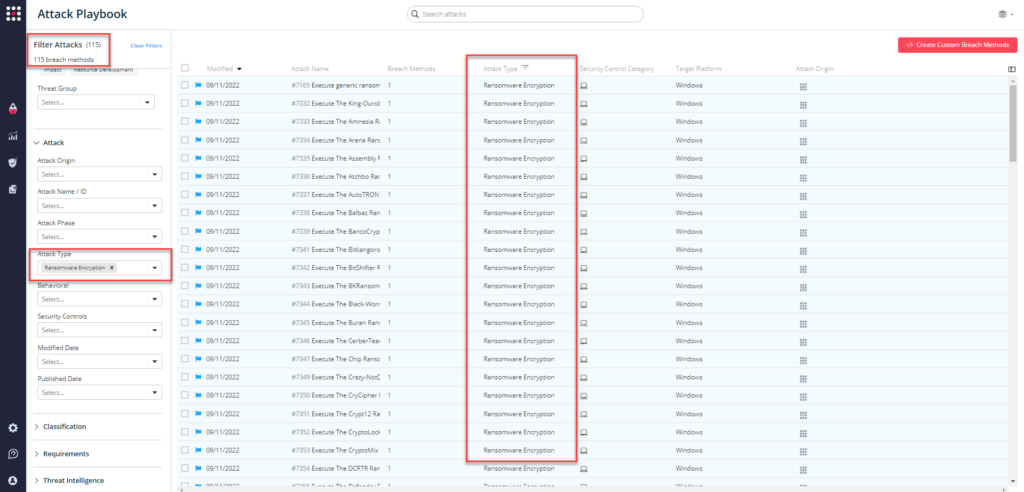
These ransomware simulations replicate the same techniques as real ransomware, so they offer exceptionally high validity. To ensure accurate replication of ransomware behavior, the attacks employ the following process:
- The simulation backs up the data before starting the attack simulation.
- The simulation saves the encryption key data.
- The simulation initiates the ransomware execution process from a designated path (default: execution_directory=”%LocalAppData%”).
- The simulation opens the target folders according to the list of folders to encrypt (default: paths_to_encrypt=Downloads), opening up the defined number of sub-folders (default: depth=-1 This means infinity).
- Using the specified encryption algorithm, the simulation encrypts the files that fit the prescribed criteria. The default values can be seen in the Breach Methods tab of the simulation in the Playbook (for example, by default, the maximum number of files is 50; the maximum file size is 10 MB, and files having specific extensions are included).
- It renames the encrypted files in the target folder with the ransomware extension.
- The simulation encrypts the encryption key.
- The result is calculated, based on whether the simulation managed to encrypt files.
- The encrypted files are deleted.
- The original files are restored.
Ransomware Full Kill-Chain Scenario
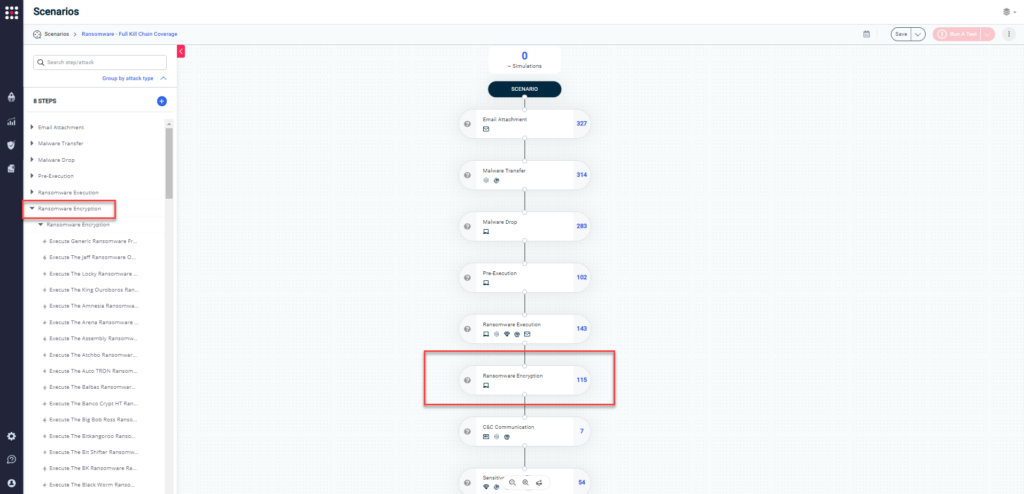
SafeBreach has now significantly enhanced the full ransomware kill-chain scenario to cover the end-to-end process of a typical ransomware campaign, starting with infiltration and lateral movement attacks, ransomware execution and encryption, and finishing by communicating with C2 servers and exfiltrating data for extortion. This scenario includes the following attacks:
- Ransomware Transfers
- Email attachment – Represents both ransomware infiltration and lateral movement over email
- Malware transfer – Represents both ransomware infiltration and lateral movement over HTTP/S
- Ransomware Host Actions
- Malware drop – Writes ransomware to disk
- Pre-execution – Pre-executes the ransomware
- Ransomware execution – Simulates ransomware behavior – the safer version
- Ransomware encryption – Simulates more realistic (and riskier) ransomware behavior
- Command & Control (C&C) Communication
- Outbound C&C communication – Simulates communication between the ransomware and a malicious external server
- Exfiltration of sensitive assets
- Covert channel exfiltration – Simulates exfiltration of stolen data
Interested In Protecting Against Advanced Ransomware?
SafeBreach now offers a complimentary and customized real-world ransomware assessment, RansomwareRx, that provides unparalleled visibility into how your security ecosystem responds at each stage of the defense process. This ransomware assessment includes:
- Training – Understand the methodology around ransomware attacks, persistent threats, and malware attacks.
- Assessment – Review goals and ensure simulation connection to our management console and all configurations are complete.
- Attack Scenario – Run safe-by-design, real-world ransomware attacks across the cyber kill chain on a single device of your choice.
- Report – Receive a custom-built report that includes simulation results and actionable remediation insights.
Empower your team to understand more about ransomware attacks, methodologies, and behaviors—all through the lens of the attacker. Request your complimentary RansomwareRx assessment today.
The post Product Update – SafeBreach Introduces New Ransomware Encryption Attacks appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by Kaustubh Jagtap, Product Marketing Director, SafeBreach. Read the original post at: https://www.safebreach.com/resources/blog/new-ransomware-encryption-attacks/






