Home » Cybersecurity » Threats & Breaches » Vulnerabilities » This Week in Malware—Python packages peek into your Telegram, set up Windows RDP access
This Week in Malware—Python packages peek into your Telegram, set up Windows RDP access
This Week in Malware we discovered and analyzed multiple malicious PyPI packages that either set up new Remote Desktop user accounts on your Windows computer or steal encrypted Telegram data files from your Telegram Desktop client.
1. PyPI packages steal your Telegram Desktop files, set up Windows RDP access
The primary packages of interest conducting malicious activities are:
- flask-requests-complex
- php-requests-complex
- tkinter-message-box
These packages were discovered by Sonatype’s automated malware detection system, offered as a part of Nexus platform products, including Nexus Firewall. On a further review, we deemed these packages malicious and reported them to PyPI.
Check out the dedicated blog post to learn more.
2. Dependency confusion packages
The week’s dependency confusion findings, across npm and PyPI, include the following packages.
@cuda-networks/bds-core
@mibuilder/doctor
@ovh-ui/oui-checkbox
@ovh-ui/oui-criteria
@ovh-ui/oui-pagination
@ovh-ui/oui-spinner
@trp-gims-usi-cip/web-portal-lib
ably-asset-tracking-common
ably-common
ably-control-api-action
ably-engineering
ably-fragmenter-test
ably-latency-bot
ably-static-app
am-annotation
am-annotation-drawing
am-remote-control
am-screen-recording-permissions
ankpkg
ankpkg1
api-key-regex
appsmith-rts
bb-netlify
coil-metrics
crowdstrike-falconpy-dev
dedicated-servers
discorddependency
discordselfbotv15
discordselfbotv16
dropbox-internal-sdk
elastic-beanstalk-hello-world
elk-logger
erdapfel
eslint-plugin-translation-vars
forgejs-editor
fully-featured-scalable-chat-app
fxa-payments-server
horizon_dev
kafka-tutorials
lambda-task-generator
legendggwp
lens-starter
lit-payment-form
nativessss
netlify-bb
nexus-snyk-security-plugin
node-network-listener
nsmalkasm
order-link-builder
os-tracking
osds
outsystems-maps
ovhcatalogs
pqc.js
priv-depen
python-dateutils
repository-audit
request-slack-invite
rust-license-check
s3-state-action
shda
shutterstock-cli
sketch-pexels
snei-frames
snei-gensen-starblaster
sync-snippet-action
test-aaa-yyyy-zzz
tkinter-message-box
uasdk
vazgarules
viewgenerator
volpino-italiano-content
vscode-ably
vscode-clangd
vue-test-utils-mic
web-self-serve-ads
web-stories-renderer
wetimejs-twilio-internal
widget-framework
Turn on Nexus Firewall for automatic protection
This discovery follows our last week’s report of malicious Python cryptominers and over 345 dependency confusion packages that were timely discovered and reported by Sonatype.
As a DevSecOps organization, we remain committed to identifying and halting attacks against open source developers and the wider software supply chain, like the ones discussed above.
Users of Nexus Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.
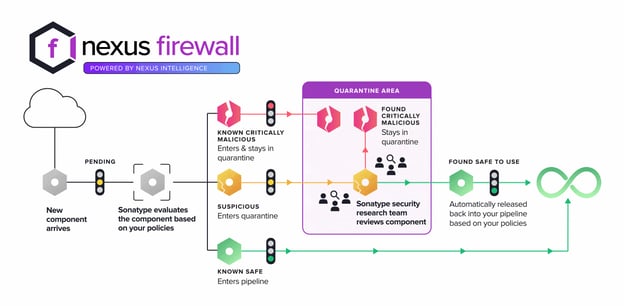
Nexus Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype’s world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Ax Sharma. Read the original post at: https://blog.sonatype.com/python-packages-peek-into-your-telegram-set-up-windows-rdp-access





