Analytic Co-Pilot Security Use Cases
LogRhythm’s Analytic Co-Pilot Services help customers accelerate threat detection and response by guiding users through the implementation and optimization of security analytics content and custom security use cases.
While working closely with customers in Q2, 2022, the Analytic Co-Pilot team discovered interesting and valuable security use cases to share. We review these each quarter to recap what we’ve been working on and provide valuable trends we’re seeing. Some of these use cases require custom rules that we create from scratch, while others are derived from LogRhythm Knowledge Base (KB).
In this blog, we’ll discuss several recent security use cases that encompass user and entity behavior analytics (UEBA), endpoint threat detection, network detection, and MITRE ATT&CK techniques. We’ll cover how we deploy the use cases, as well as tune and test the rules.
To understand the complexity of a use case and how it may apply to your environment, we provide a key at the start of each section to explain:
- Which Module the use case aligns to
- The log sources required to successfully implement a use case
- Difficulty score that rates the complexity of implementing and maintaining a use case
- Impact rating to assess how a use case can positively impact threat monitoring
Q2 2022 Analytic Co-Pilot security use cases
1. Use case: Monitoring deleted and disabled user accounts
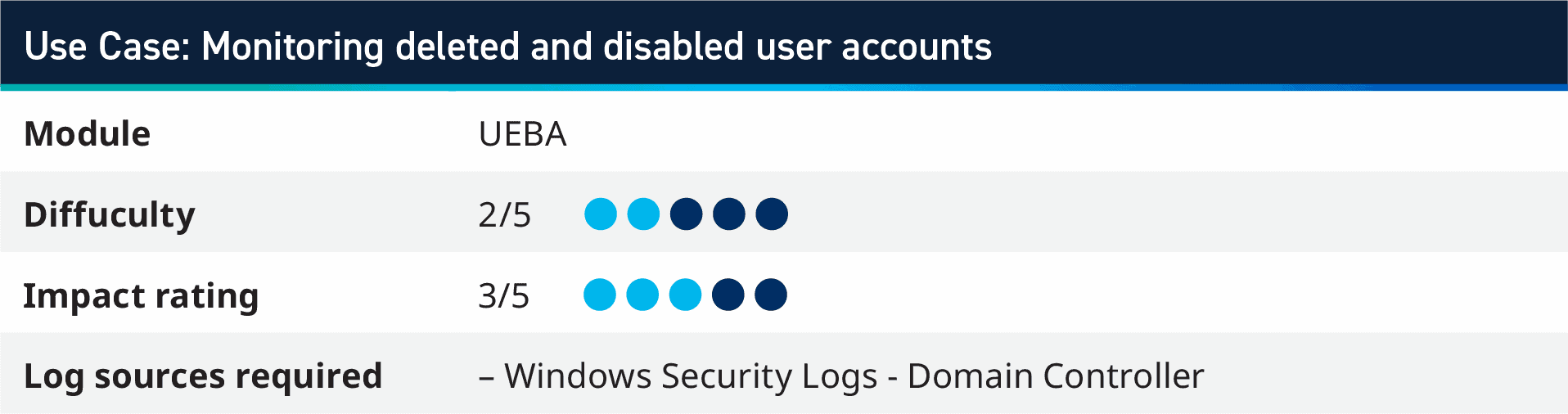
This use case is inspired from the AI Engine (AIE) rule in our UEBA Module which monitors for disabled account authentication failures. Customers can leverage the base rule, which looks for an account deleted and then authentication failures within twenty-four hours, and implement this into a couple of AI Engine rules with a report, too!
The first rule monitors system logs for deleted and disabled accounts. This takes the User Impacted and adds them to a list of Disabled/Deleted Users via SmartReponse™ automation. Optionally, SmartResponse can automatically close the alarm, which allows for a longer-term list of user accounts that have been deactivated.
2. Use case: Log4Shell vulnerability monitoring
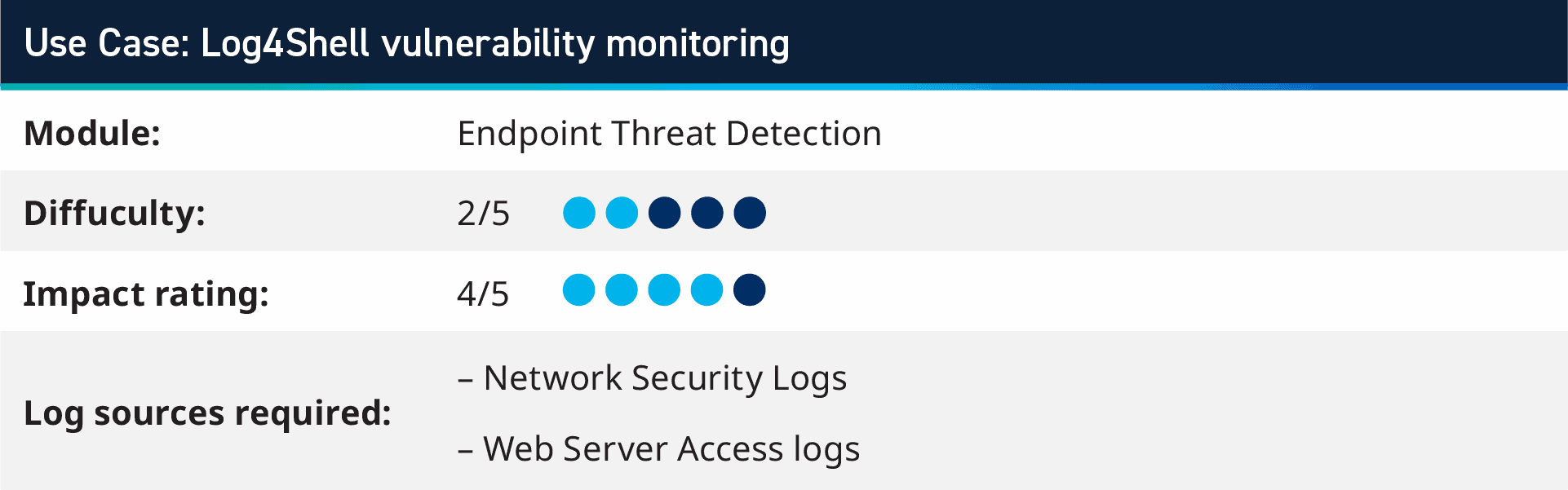
After the cybersecurity world was hit by the widespread Log4Net vulnerability, there are several security use cases that the Analytic Co-Pilot team has created to monitor for Log4Shell attacks. These look for the JNDI strings within any metadata field, as well as encoded and obfuscated attempts for delivering the payload. Customers can take the IP address of the source of the attack, as well as any IP addresses or domains that are in the payload, to monitor outbound network traffic and DNS logs for these IOCs to know if there is any execution of these attacks, either in the original target or downstream processing of logs.
3. Use case: Detecting a large volume of BCC’ed recipients
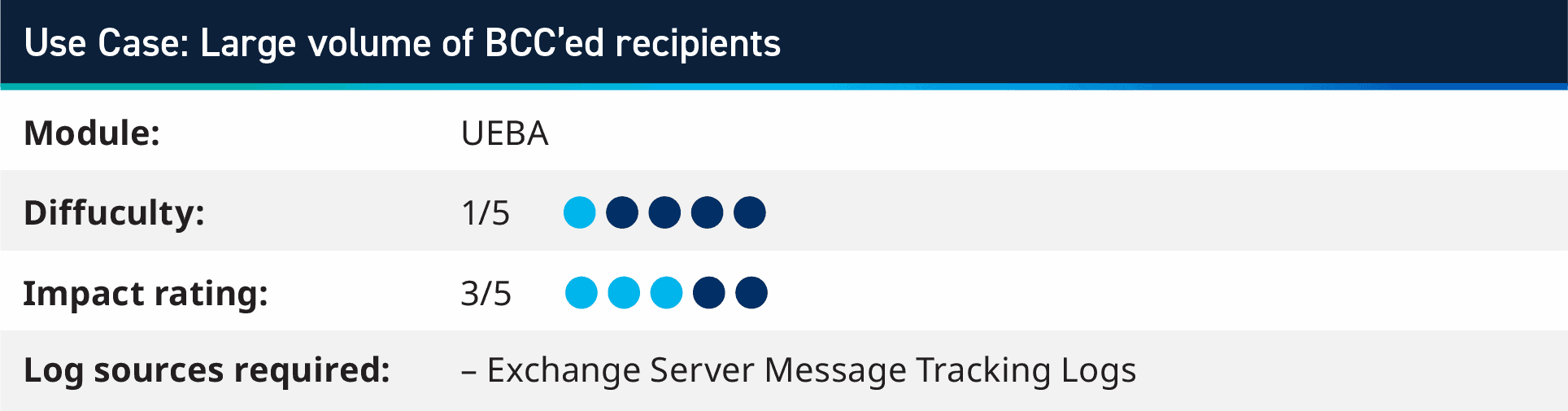
During a recent session with a Co-Pilot customer, we discovered that one of their users fell victim to a phishing attack and their email was used to send hundreds of spam emails. As a result, the organization’s email server IP addresses were added to spam lists and legitimate emails were not received by the intended recipient.
To detect this behavior, we created an AI Engine rule to monitor for a large volume of recipients in BCC. This allowed their security team to stop a second phishing attack on a different user, pausing email flow and remediating the user account swiftly, saving their IP addresses from being added back onto spam lists.
This can also apply to “CC” and “To” fields within an email being sent; however, if these are higher in volume, a feedback rule can be created to monitor for the same user triggering either of these rules multiple times and within five minutes.
4. Use case: DNS large number of DNS queries – T1071.004
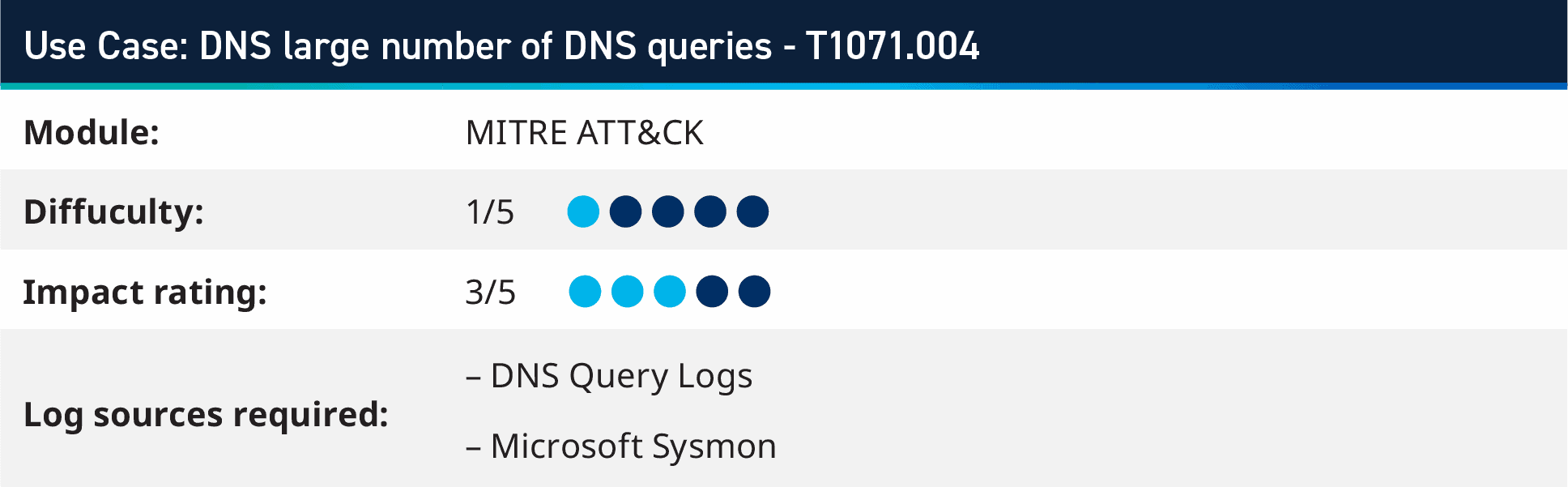
In this use case, we will dive into MITRE ATT&CK technique T1071.004: “Adversaries may communicate using the Domain Name System (DNS) application layer protocol to avoid detection/network filtering by blending in with existing traffic. Commands to the remote system, and often the results of those commands, will be embedded within the protocol traffic between the client and server.”
This security use case monitors for large number of DNS requests coming from a system. This indicates communication to a command and control system, data exfiltration, or changes to a system configuration. By using either Sysmon Event ID 22 DNS request logs from an endpoint or by using DNS Server query logs, you can monitor for more than one hundred DNS queries within two minutes from the same host.
When tuning these rules, you can use basic exclude filters to remove queries to your internal domains, well known domains, and other queries that may be common from your environment.
5. Use case: LogRhythm UEBA high score user password change
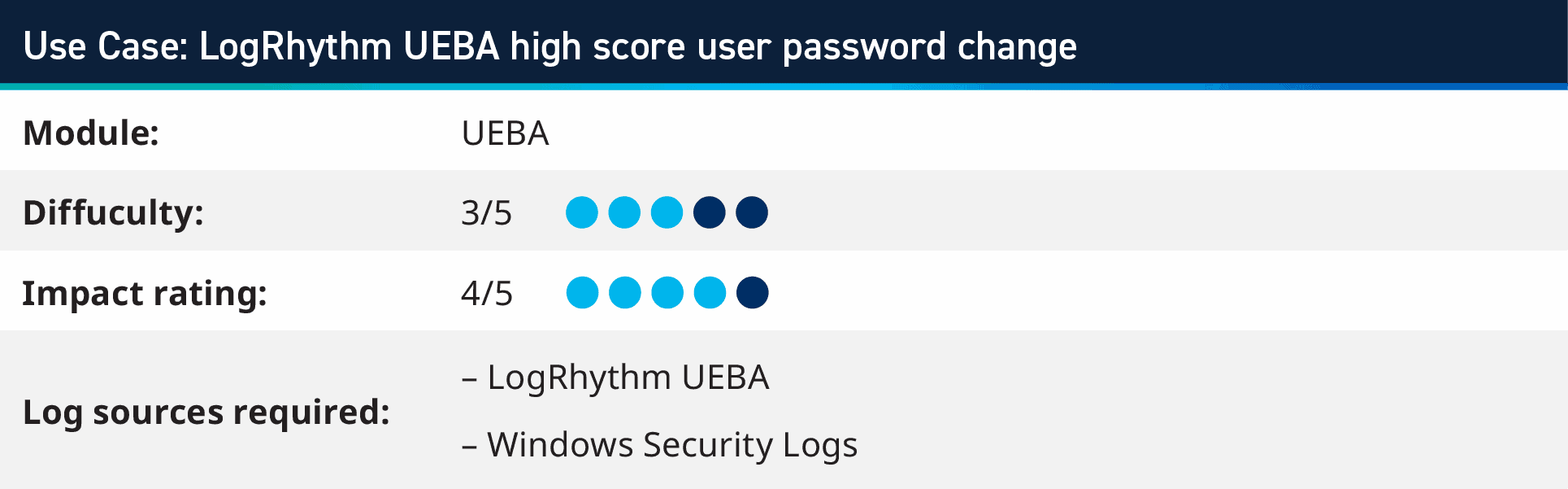
LogRhythm UEBA is a cloud-based add-on to the LogRhythm SIEM Platform that uses machine learning to detect user attacks such as insider threats, compromised accounts, administrator abuse, and misuse. Using output from LogRhythm UEBA’s user with high score alert, you can combine these alerts with monitoring for other activities, which can indicate higher severity confidence.
For example, the use case combines a user high score from LogRhythm UEBA with the user’s account Password Change, indicating that a user that has suspicious activity has then triggered the alert, which could be a nefarious actor gaining access and changing the password to maintain longer term access. This can elevate a password change log into an alert when combined with suspicious behavior triggers.
6. Use case: DNS C2 – Command and control using DNSCAT2
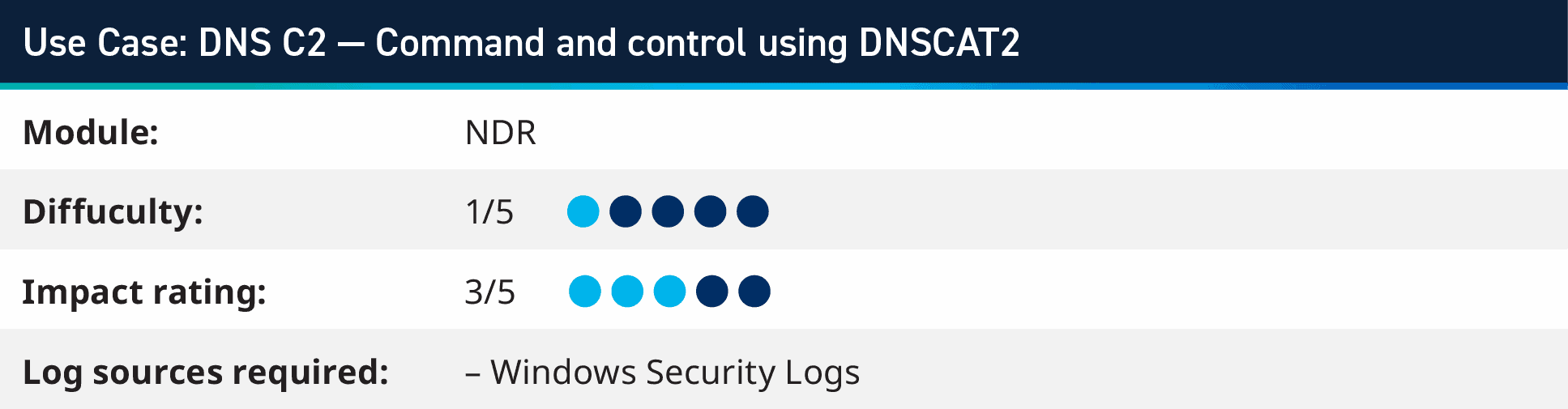
For our second DNS-based use case this quarter, we will look at how to monitor for DNS tunneling using DNSCAT2. The tool uses DNS to send data over channels that may not be expected to be used other than name resolution. It works as a Client/Server model, where the server is a DNS server which can be configured to forward up stream requests that it doesn’t want, and only monitor the traffic for certain domains. When it receives this data, it can either export the encrypted data or documents that it received (data exfiltration) or return commands to the system to be executed (tunneling).
You can monitor for this rule in two ways, the first is using encoded PowerShell (which is typically how the client is initially executed) and the second is by monitoring for excessing NSLookup processes being started. that the DNSCAT2 client creates very large number of NSLookup processes to communicate to C2 Server.
Hone your security use cases with a Co-Pilot
Since the beginning of 2022, the Analytic Co-Pilot team and our customers have observed several different and interesting developments, ranging from world events influencing cyberattacks to new vulnerabilities found in open-source logging libraries which are used in a lot of applications within enterprise environments.
The sessions we run with our customers and the research we work on in our labs, ensures that customers are monitoring against the latest threats. We optimize their potential by helping to tune their existing environment and keep up with security best practices.
You can find out more about LogRhythm’s Analytic Co-Pilot Services here, or please reach out to your customer success manager or account team to learn how we can help you with all things analytics.
The post Analytic Co-Pilot Security Use Cases appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by Kelsey Gast. Read the original post at: https://logrhythm.com/blog/analytic-co-pilot-security-use-cases/





