Here’s How to Fight the Latest Avatar of BNPL Fraud
Like other digital fraud attacks, BNPL fraud is constantly evolving. Attackers are now using stolen consumer details to open new fake accounts and create virtual cards. Are you prepared to fight this new attack tactic?
Buy Now Pay Later (BNPL) is fast becoming a popular digital payment option due to the convenience it offers to the consumers and a new revenue stream to the businesses. Data from The Motley Fool shows that by July 2020, 38% of American consumers used BNPL – in some form or the other – for their online purchases. This figure rose to 55.8% by March 2021 – a 48% increase in adoption in less than a year.
One of the key reasons behind this massive adoption of BNPL services is the negligible barrier to entry. Recently, I tried to sign up for a line of credit with a leading BNPL provider. All I had to do was to provide my name, address, email address, and my annual income. Since I didn’t see any soft or hard pull to my credit report, I can safely say that the annual income consumers share at the time of registration, is not verified.
This ease of getting access to a line of credit also makes it a ripe hunting ground for attackers. Over the years, there has been an evolution in the types of BNPL fraud – from classic to innovative. Now, there is a new type of fraud that has hit the business.
Modus operandi of BNPL fraud
First, a bad actor would list an item on an e-commerce website at a price far less than its current market value. Consumers who want a deal end up ordering, only to not receive the product. This fraud results in a chargeback and the card issuer consequently bears the loss. This example, however, simple version of how BNPL fraud worked earlier.
In its latest avatar, BNPL fraud entails an attacker using the personal details – provided by the victim while placing the order – to open a new fake account. Once the account is activated, attackers create virtual cards and purchase multiple items to exploit the basic credit limit provided by the BNPL provider.
Ultimately, it is the compromised consumer, whose details were used for the fraud, who suffers. This consumer gets blocked from using the BNPL service in future. What’s more, this manipulation results in compounded losses – once due to the consumer filing the chargeback and later due to abuse of the starting credit limit that the BNPL provider offers.
An everlasting tussle between friction and user experience
Consumer-facing companies are in an everlasting tussle between enforcing too little or too much friction – that can let attackers in easily or disrupt user experience, respectively. That said, the effect of fraud goes much further than just a ‘leaky bucket’ for the company. Often, it has far reaching consequences in the form of legitimate consumers getting blocked out from the platform (as explained in the example earlier). Such consumers, who would have transacted a few times over their lifetime, are now prevented from onboarding, which results in unrealized revenue.
To maintain the balance between seamless onboarding and possible revenue loss, companies use basic authentication methods such as 2FA to check email and phone possession. However, there are many websites to help bypass these checks. One can easily see how burner phone numbers and email addresses are being made available at scale. Not only do attackers not need to register anywhere to get an identity, they can use the identifier to see all the communications happening.
Let’s stop online abuse
Stopping advanced attackers needs an innovative and multi-faceted approach. Stopping an attacker from trying to register with a stolen or synthetic identity is difficult, but not impossible. There are certain methods, as described below, that we can employ to spotlight them
- Behavior Analysis: Generally, there are strong callouts in the difference in the behavior of a good user vs a bad actor. Once the attackers have acquired credentials, they may do one or many of the following:
- Copy and paste credentials, instead of manually typing them.
- Are too fast with the typing and clicking/touching speed, given they are usually running against time.
- Start becoming ‘too good and careful’ in trying to mimic good user behavior, which makes them stand out from the others.
There are deeper behavior analysis, too, that can help detect good consumer replays or the presence of a bot, based on how the interaction with the webpage is playing out.
The fig. 1 below depicts automation while fig. 2 depicts mouse movement of a good user.
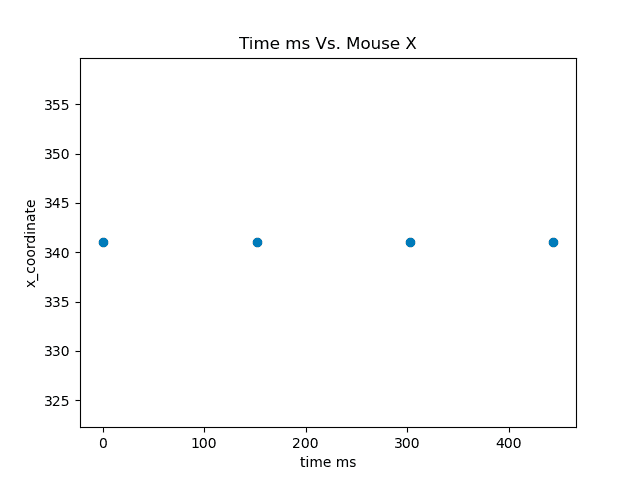
Automation
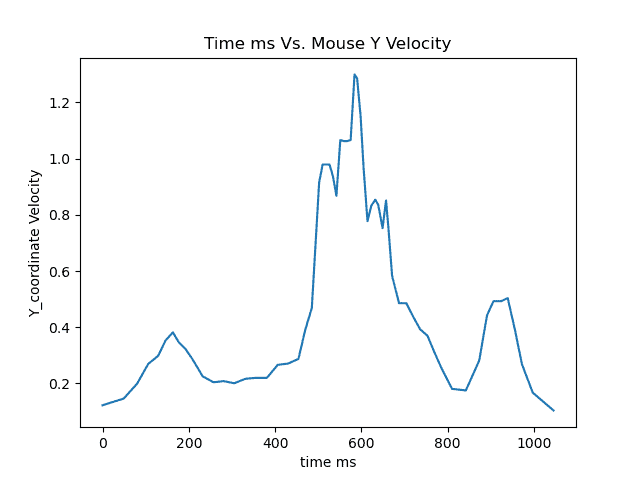
Good User
- Detecting Spoofed and Randomized Devices: When attackers are able to acquire details of consumers en-masse, they may programmatically create mass registrations, given the time constraint. Attackers, however, are well aware that mass registrations emanating from the same device or a handful of devices can be easily identified. Therefore, they randomize device fingerprints to hide the spurious traffic within the pool of good users.
Device randomization or spoofing detection systems can help detect this randomization. If we look carefully, we will find that certain attribute combinations don’t make sense. Imagine an iPhone screen resolution coming from an Android TV! Additionally, we can look for incompatible fingerprints such as an iPhone 12 running on iOS 6. Although rare, such possibilities do exist.
It is possible that attackers succeed in committing the perfect crime – randomize fingerprints to look like a completely legit device. However, their sense of urgency stays – whether it’s a volume-based attack to make the most bang for the buck before anyone finds out, or keep it under the radar to continue targeting. In either case, we can monitor whether the traffic coming from such fingerprint combinations are as expected or not. Based on these observations, we can create sophisticated, threshold-based checks to keep attackers away.
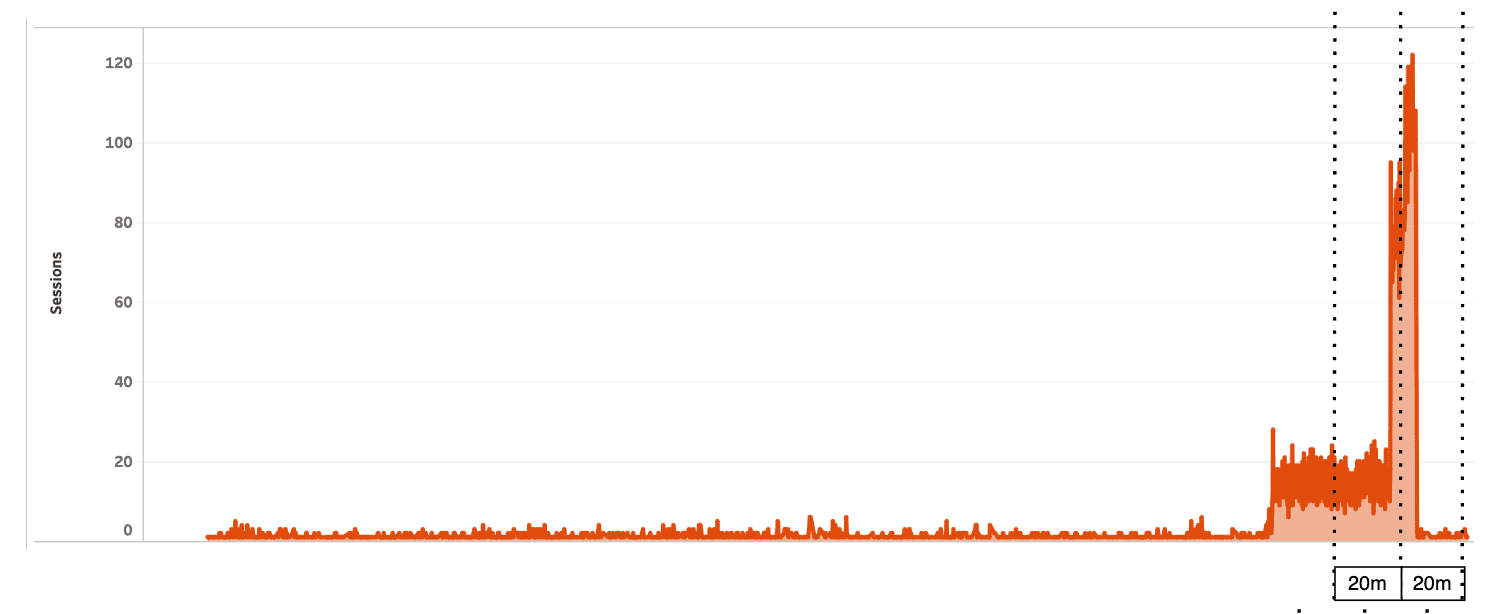
The Data Science team at Arkose Labs has done an analysis (figure below) where it detected subtle spikes when looking over rolling time windows. Attackers were trying to hide behind ‘legitimate-looking’ fingerprints and creating tiered volumetric attacks.
- Employing PII Intelligence: PII Intelligence is one of the key pillars to identifying frauds such as the BNPL fraud. Even though attackers have the personal information of the compromised consumers, they either use disposable emails or create new ones. Basic email intelligence can help unearth facts such as age of the email and the general risks associated with the domain on which the email was created.
At a slightly advanced level, an identity graph can help understand whether one or more attributes used belong to another person or was ever a part of a previous transaction – legitimate or fraudulent. By being able to associate these attributes to the larger picture on the platform, we can prevent many such fraud attempts.
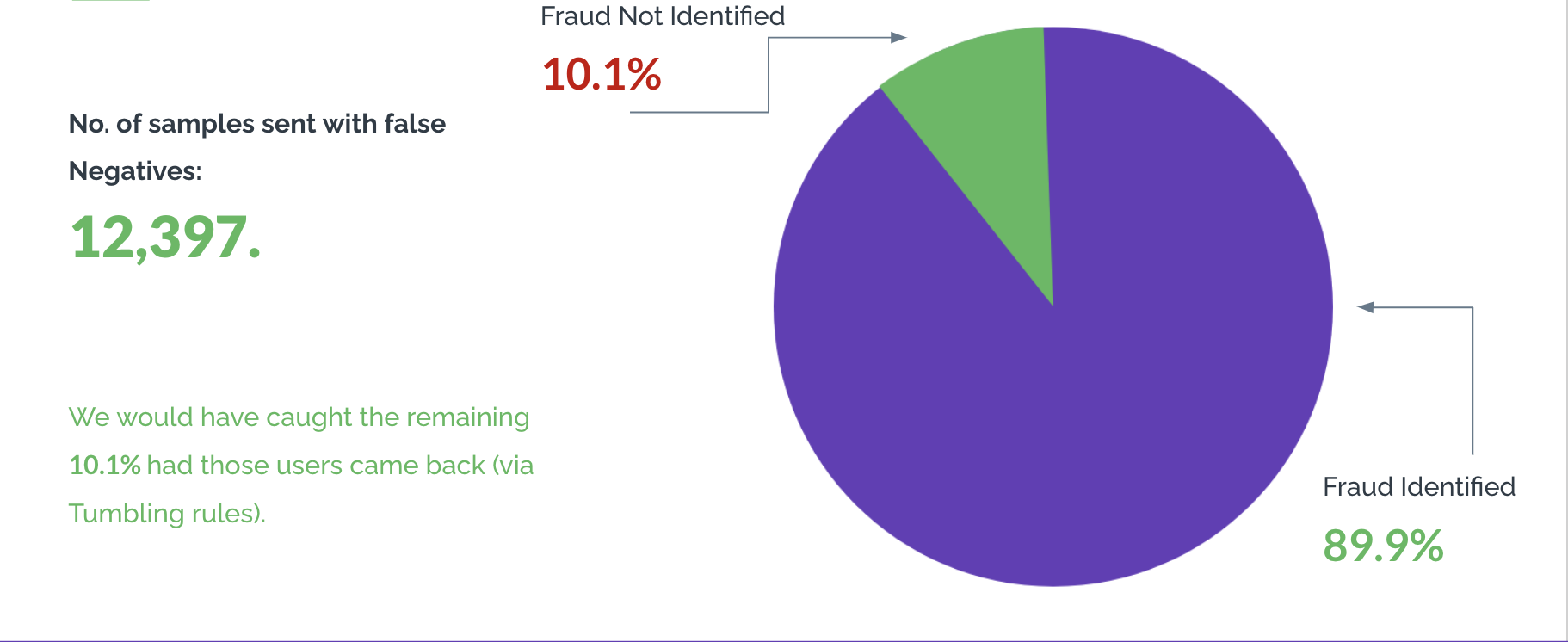
At Arkose Labs, we analyzed the delta in increased detection of fraud with basic email intelligence on a sample of 10,000+ dataset. We found some really positive results and interesting insights.
- Interrogating IP Addresses: IP address is a key entity that can play a massive role in detecting fraud. Whether the IP is being used with a VPN, a proxy, or is simply a TOR exit node, can give early warning about the potential risk. Combining this interrogation with sophisticated investigation such as whether the IP range belongs to a datacenter, whether a private ASN is being used, and the risk associated with the ISP, can help substantiate the risk.
Arkose Labs takes these and more parameters into consideration while trying to profile the risk associated with an IP address and how that risk plays into the overall traffic.
- Joining a Consortium: Consider this, you see a consumer for the first time, but the information used during registration correlates strongly to a fraud committed on a company similar to yours, recently. What does this indicate?
Consortium is an old concept but it holds the same power as ever before. Attackers share intelligence among themselves and attack businesses as a ring. We should take the same approach to stop them.
Joining a consortium is a win-win concept. However, fraud prevention vendors still do not drive it with the same vigor as the other sophisticated product features. Privacy compliance laws don’t help either with the adoption of this feature. Ultimately, consumer-facing businesses and fraud prevention vendors should come together to form an alliance, create standards of sharing data, and allow free-exchange in a way not to violate privacy of data.
Prevent fraud to create a harmonious online environment
We must note that attackers are getting more advanced. They are improving BNPL fraud tactics by adapting and taking advantage of the latest advances in technology, which means the cat-and-mouse game between attackers and businesses will continue to plague fraud prevention efforts.
Ultimately, fraud is a business and is run like one. Therefore, rather than focussing on preventing the leaking revenues due to BNPL fraud, we must make every effort to bankrupt the business model of fraud that stops attackers and work together to create a harmonious environment for legitimate consumers.
To learn how Arkose Labs protects BNPL providers from fraud and online abuse, please book a demo now.
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Ayan Halder. Read the original post at: https://www.arkoselabs.com/blog/heres-how-to-fight-the-latest-avatar-of-bnpl-fraud/





