Browser-in-the Browser (BITB) – A New Born Phishing Methodology
Introduction
There is no one who we can trust in this digital age! Phishing has become a prevalent assault in the previous decade, with the attacker using a false login screen to acquire users’ credentials. A novel phishing technique called Browser-in-the-Browser (BITB) takes advantage of third-party single sign-on (SSO) options embedded on websites that issue popup windows for authentication, such as “Sign in with Google,” Facebook, Apple, or Microsoft.
Tradition Phishing techniques
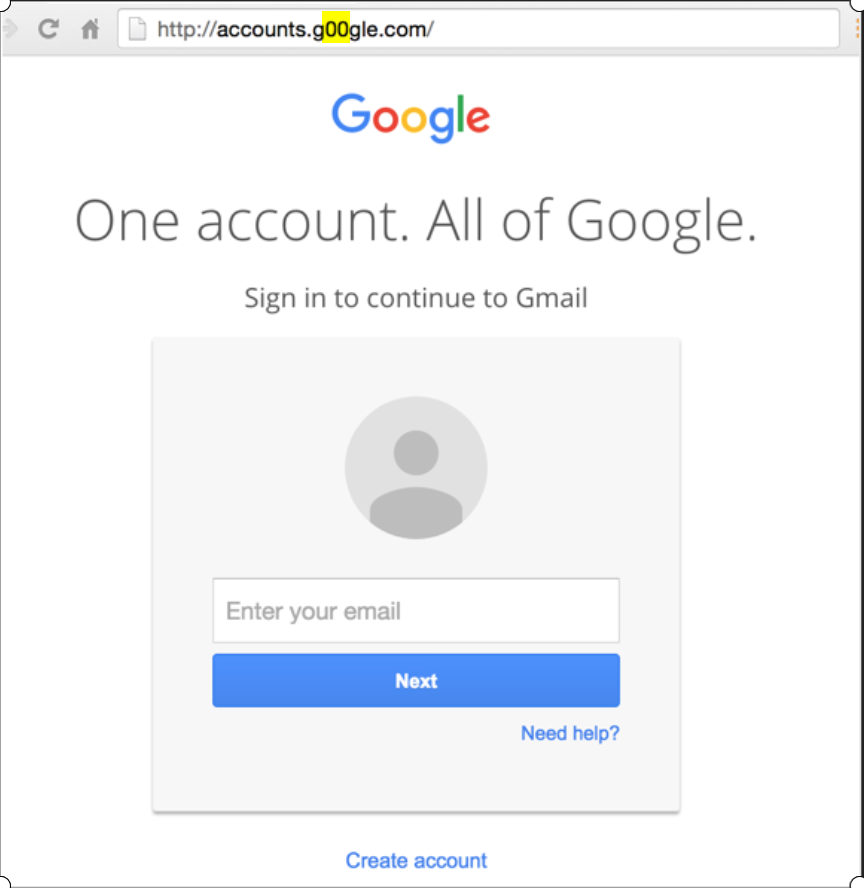
[ Image -1: Old Phishing Method ]
We can see the phishing page for the domain https://accounts.google.com/ in the image above. Security researchers can locate the phishing page using their domain name or a phony URL in this form of phishing assault.
- Real page: https://accounts.google.com/
- Phishing page: https://accounts.g00gle.com/ (Zero instead of “o”)
As a result, it was rather simple to detect the phishing page using the URL.
Modern Phishing techniques: Browser-in-the-Browser (BITB) Attack
A security researcher [mr.d0x] discovered one way that hackers can employ to obtain user credentials to make the phishing attempt harder to detect. An attacker launches a phishing assault using the browser’s popup function in this form of the phishing attack. Anyone can make false website pages that seem just like legitimate login pages with the help of basic scripting. They build a CSS+HTML code that looks just like the real pages because the new Popup windows have no URL.
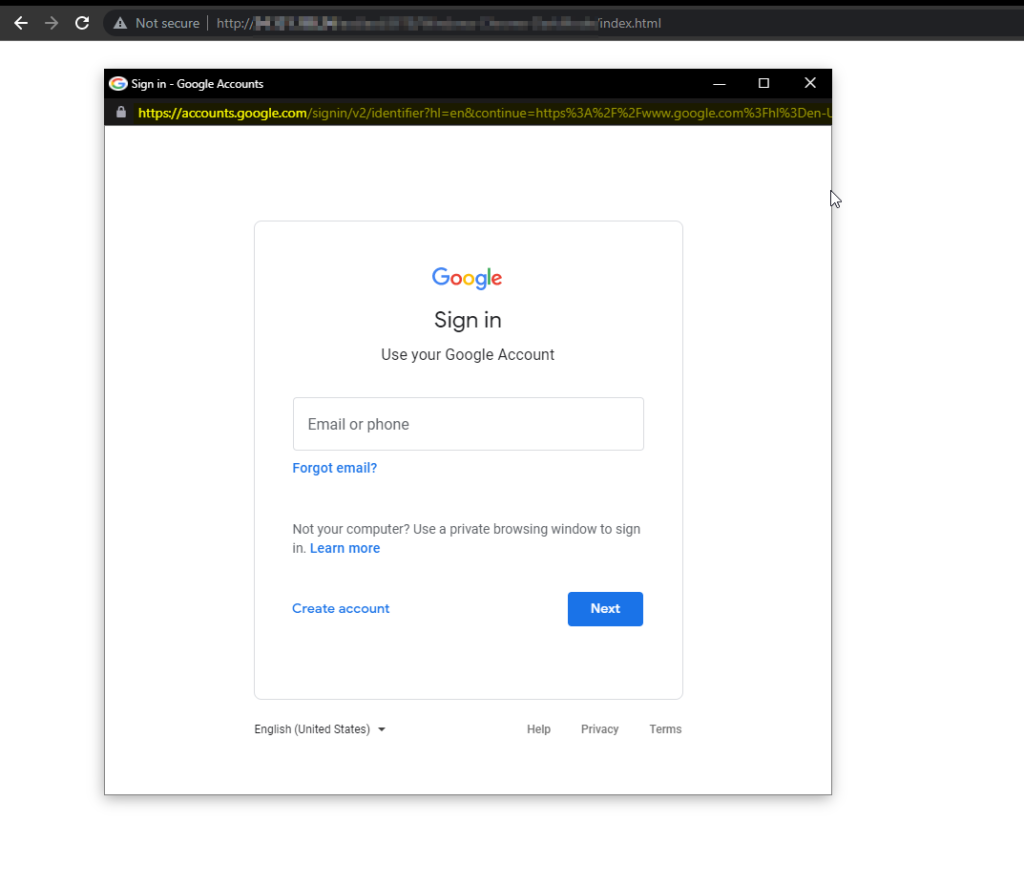
[ Image -2: Browser-in-the-Browser]
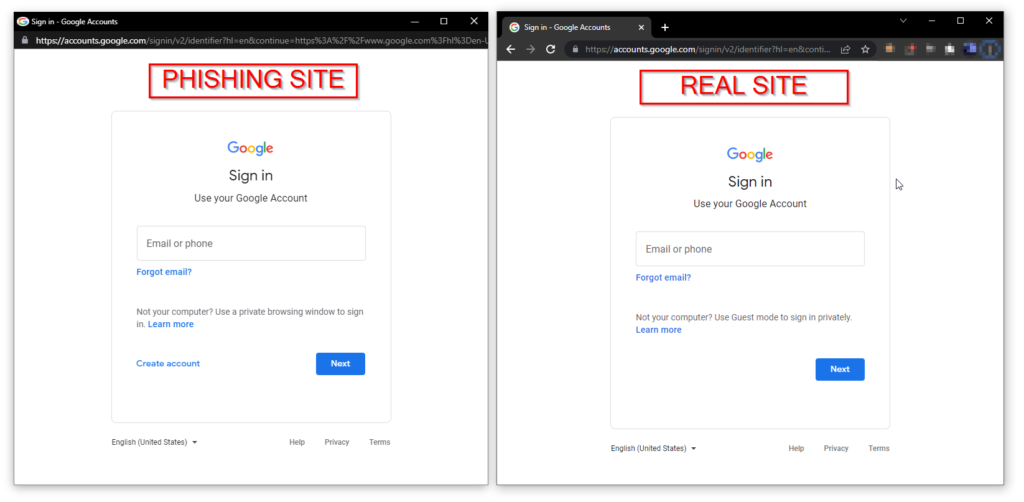
[ Image -3: No Difference between real and phishing site ]
When a user hovers the mouse pointer over the legal website link, a new phishing window appears, thanks to the “on-hover” JavaScript function.
Browser-in-the-Browser Demo:
Because there is no discernible difference between the two photos, identifying the true site for verification is extremely challenging. Also, some web apps use a windows pop-up function for authentication, thus users should expect pop-ups in their browsers.
- Real page: https://accounts.google.com/signin/v2/identifierhl=en&continue=https%3A%2F%2Fwww.google.com%3F
- Phishing page: https://accounts.google.com/signin/v2/identifierhl=en&continue=https%3A%2F%2Fwww.google.com%3F (No difference in URLs)
The site’s look and URL will be identical to the real website in this type of assault. As a result, finding the discrepancies will be difficult.
Be Aware: For now, public exploits are available for Mac OS Chrome and Windows Chrome browser.
Conclusion
The sole defense against this type of modern phishing attack is awareness. Ensure to arrange “Employee Security Awareness Programs” offered by WeSecureApp. Let WeSecureApp organize all your cyber-security challenges. Get aggressive security services by just clicking below. We look forward to hearing from you.
Services Offered by WeSecureApp:
Red Team Vs Blue Team Exercises

About Author
Keyur Talati
Security Analyst – WeSecureApp
The post Browser-in-the Browser (BITB) – A New Born Phishing Methodology appeared first on WeSecureApp :: Simplifying Enterprise Security!.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security! authored by Keyur Talati. Read the original post at: https://wesecureapp.com/blog/browser-in-the-browser-bitb-a-new-born-phishing-methodology/





