ISO/IEC 27001 Compliance Self-Assessment: The Ultimate ISO 27001 Requirements Checklist
For organizations looking to reassure customers that excellent data governance is one of their guiding principles, and that they’re doing everything in their power to mitigate the risk posed by cybercrime, ISO/IEC27001 certification is one of the best ways to demonstrate that commitment. Nevertheless, it’s a high standard to achieve. According to data supplied by ISO.org, only 28,426 companies worldwide had achieved the certification by 2022. How can you give yourself the best chance of emerging from the audit process with flying colors?
Of course, in order to pass the certification, you’re going to need to pass through an external audit. But to give yourself every chance of emerging with flying colors, it’s smart to use your internal resources to help run through a test preparation checklist. In that spirit, we’d like to present The Ultimate ISO 27001 Requirements Checklist which we’ve prepared based on our extensive experience helping organizations worldwide track and secure their data stores.
What is the ISO 27001 Standard?
ISO/IEC27001 is a world-leading information security standard. It includes a set of detailed requirements for demonstrating that your organization is implementing a professional and reliable Information Security Management System (ISMS). It was introduced in October 2005 as a replacement to the BS7799-2 standard.
Specifically the standard covers:
- Identifying internal stakeholders important to the process of managing data
- Pinpointing leadership in the realm of information security and policy support
- Specifying corrective actions that should be taken in the event of non-adherence to the management system instituted
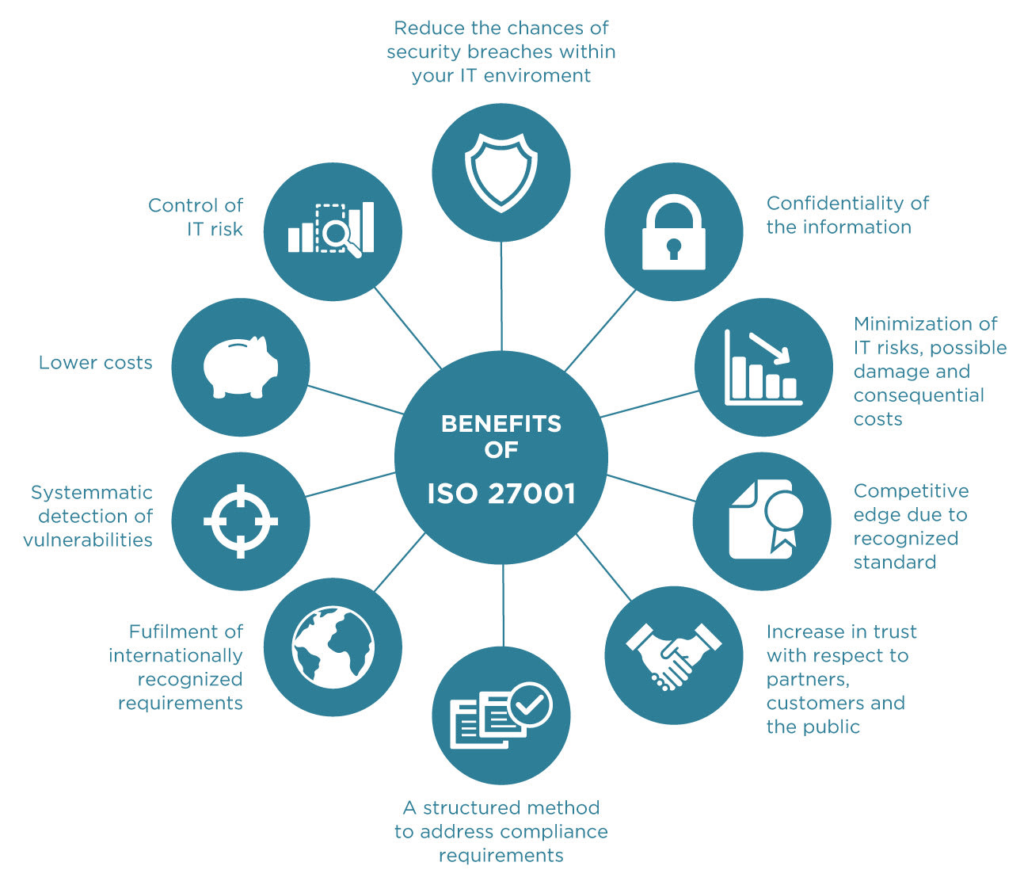
What are the requirements for ISO 27001 compliance?
The core requirements to be certified as compliant with ISO 27001 are:
- Being able to demonstrate an understanding of the organization and the context in which it sits
- Organizations need to be able to demonstrate that they can elucidate what issues might impact upon the ISMS from both internal and external perspectives.
- Knowing the needs and expectations of interested parties
- At a minimum, organizations need to be able to list which groups of stakeholders may be impacted by the ISMS. Their requirements need to also be mapped out, especially compliance ones.
- Scope determination of the ISMS
- A scope determination process needs to be followed in order to map out which systems will be potentially impacted by the system from a compliance standpoint. For instance, an organization would have to take an inventory of all information management systems that they have deployed.
- Defining an information security management system (ISMS)
- A working definition has to be established so that various compliance professionals all understand what is being referred to for the purpose of passing the checklist.
- Leadership and commitment
- The business will have to provide concrete proof that leadership is aware of the initiative and has integrated efforts to remain compliant into its standardized set of business processes.
- Policy (and defined objectives)
- Roles need to be clearly defined and all policy and objectives mapped out.
- Planning (and defined objectives)
- A systemized process needs to be instituted which ensures that targets will be met towards passing the audit.
- Support (and defined objectives)
- Support process must be instituted. For instance, an individual should be appointed who will have overall responsibility for passing through the audit checklist.
- Operation (and defined objectives)
- Performance evaluation (and defined objectives)
- A system must be put in place in order to evaluate whether the business is remaining on target with its objectives. This will ensure repeat passing of the standard.
- Improvement (and defined objectives)
- Improvement objectives must be set and carefully defined in order to ensure preparedness for the audit and passing it.

Cumulatively, these are listed, in full, as Annex A to ISO 27001 which provides the full list of controls that are necessary to demonstrate in order to pass the audit. Those looking to obtain a more detailed list of requirements necessary for successful passage of the certification standard should consult this source.
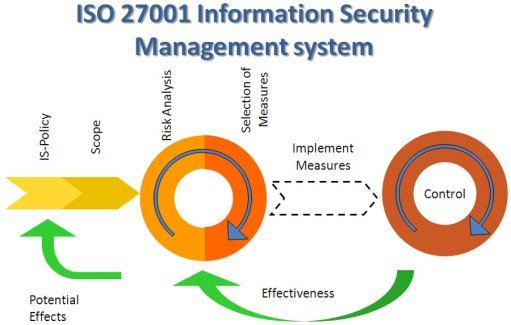
What is an ISMS?
An Information Security Management System is at the core of the ISO 27001 certification process. In fact, the Standard sets down policies and procedures that involve technology, people, and processes related to its safe upkeep.
The certification will evaluate what
- Information security policies are in place
- How assets are managed
- How human (as well as computing) resources are secured so that they securely interface with the various ISMS systems in place and the data that they safeguard
Additional areas that organizations will need to demonstrate competence and proper governance in order to emerge with the certification include:
- Business continuity management – a thorough risk analysis process can help to drastically mitigate the potential impact to these crucial data-holding systems in the event of unforeseen circumstances. Documented crisis management processes are therefore integral to ensuring that data survives any risk to the business.
For organizations embracing modern development methodologies — such as DevOps and DevSecOps — passing through this certification can provide an enormous safeguard. With robust governance of ISMSs assured, rapid development processes can proceed unimpeded by the risk of the failure of any systems which are crucial to the development process.
In order to pass the ISO 27001 standard, organizations need to go through an auditing process. Nevertheless, a self-assessment is a great way to probe your level of preparedness for that process without the associated cost and stress.
A checklist provides a systematic framework for going through the self assessment process. It should provide a logical and robust means of assessing your internal readiness to take the actual audit.
Because every organization is unique, we recommend taking the time to develop an internal and proprietary checklist that can integrate the specific information as it relates to your business. However, the model we have provided below should provide a good starting point.
As your own individual journey towards the audit evolves, it may also be worth periodically updating this in order to reflect those areas that you feel may require more or less attention.
How to use an ISO 27001 Requirements Checklist
Our recommendation is to start with an expertly-prepared requirements checklist for passing the audit.
You can add items to the checklist if you’re particularly worried about your ability to demonstrate know-how in a particular area of the audit.
Alternatively if you’re really sure that you’ve already excelled in a certain domain of competence – like support awareness – then you can skip over that in one of your internal requirements checklists.
Together this will give you the best chance of passing through the audit with flying colors.
The post ISO/IEC 27001 Compliance Self-Assessment: The Ultimate ISO 27001 Requirements Checklist appeared first on Spectral.
*** This is a Security Bloggers Network syndicated blog from Security boulevard – Spectral authored by Eyal Katz. Read the original post at: https://spectralops.io/blog/iso-iec-27001-compliance-self-assessment-the-ultimate-iso-27001-requirements-checklist/





