What Drives DDoS Attacks and Why it Should be a Concern
What is a DDoS Attack?
DDoS stands for Distributed Denial of Service attacks. Let’s ignore the Distributed for now as it refers mainly to the technique and let’s focus on the Denial of Service first. As the term implies, the objective of a DoS attack is to disrupt or deny services from legitimate users. A service can be anything including web sites that provide information, online services such as ecommerce sites or backend services such as payment processing, the communication between organizations and cloud applications, the connectivity of remote internet controlled industrial processes or sensors.
The objectives of the attacks include defacement, creating an impact on the economy of an organization or nation by impacting productivity, creating chaos, or as a smoke screen to hide another attack. Overwhelming a network with random traffic will distract the defenders and give attackers the opportunity and time to perform malicious activity on the side while going undetected as defenders are focusing on the most impacting issue which is the Denial of Service attack.
Depending on the objective, denial of service attacks can be performed in different ways. A volumetric denial of service attack for example aims at saturating connections to the service or between organizations and the cloud or between branches and headquarters basically hampering all legitimate communications and stopping all data traffic.
A Denial of Service attack can also be targetted at a specific service like a website, an API or a Domain Name Service (DNS) in which case the resources of the server are the target. Such application layer or L7 attacks can completely disrupt the service or they can be more insiduous like low and slow attacks that eat away at resources and impact the user experience, forcing the owner of the service to invest in more resources such as CPU, memory or bandwidth to sustain an acceptable level of service. If such attacks go undetected for a long time, they can drain the economic viability of a business or service.
Another type of Denial of Service attacks, exceptional but still important enough to consider as a threat, are vulnerabilities in software or hardware that can result in the crash of a process, halting or rebooting of a device, just by sending malformed packets. A single packet can result in processes exciting without reason or long reboot cycles and can be very disruptive if not discovered timely. Given the attack consist of a single packet, finding the culprit amongst millions of packets and connections can be a daunting task and mostly these attack are discovered by analyzing the crash dumps of kernels or processes. Most of these exploits have a short lifetime because once the vulnerability is discovered, it can be patched and updating systems or network signatures can easily prevent this attack. Nonetheless, the come around from time to time.
Performing a Denial of Service attack does not require extensive skill or specific knowledge, in most cases it requires knowledge of the location of the service, its IP address for example and enough powerful infrastructure to perform the attack. The attack infrastructure can consist of cloud servers, but attackers can also leverage a growing range of consumer and prosumer IoT devices such as IP cameras and routers and enslave them to perform large scale distributed attacks. Because attack traffic originates from all parts of the globe and from different devices, we refer to these attacks as Distributed Denial of service attacks.
What a DDoS Attack is not
As you followed along, you probably noted that there is no infiltration of networks or breaching of servers involved in Denial of Service attacks. An organization that suffered a Denial of service attack will not be subject to stolen data or have persisting malicious software in their infrastructure as a result. With the exception of DDoS as a smokescreen, once the DDoS attack stops, the organization can recover its services and continue its operations, very much unlike ransomware where the organization is typically left in an inoperative state until it recovers or restores its internal systems, and even them it can take days, weeks or months to fully recover all services and operations.
The flip side, however, is that attackers can perform DDoS attacks with very little worries about being caught. Leveraging IoT devices, spoofing and reflection, it becomes very difficult, near impossible even, to attribute the traffic to specific actors. The threshold to perfom a DDoS attack is by consequence much lower compared to infiltrating and extracting information from private networks.
How big is the threat from DoS attacks? Which organizations or industries are particularly at risk? Who are the actors behind those crimes? What are they after and what motivates them?
Starting 2020 we have witnessed a surge in DDoS activity driven by Ransom DoS campaigns that have become a persistent part of the DDoS threat landscape as well as several political and sociological events like elections, #blacklivesmatter and struggles inside and between nations.
To understand the threat and assess the risk for your organization, you need to understand the actors, who they are and what their objectives are. Know how they typically perform attacks. The tactics and techniques leveraged by malicious actors will depend on their objective and skill level. And finally, the actor requires something that is of value to you that he can impact – this is where the opportunities for malicious actors lie and typically consist of important and valuable assets or vulnerabilities.
[You may also like: Does Your DDoS Protection Solution Defend Against the Latest Attacks?]
Organized crime
Ransomware has seen enormous growth and evolution in tactics by operators and affiliates that are getting better organized. Ransomware operators have evolved their tactics to triple extortion, not only encrypting systems but exfiltrating sensitive data and threatening to publish the data for a ransom. If the victim does not comply or resists, they resort to DDoS attacks to get their victims back to the negotiation table.
Since August 2020 we have seen Denial of Service extortion or Ransom DoS campaigns targeting all verticals across the globe. Campaigns that were very persisting and where actors posing as Fancy Bear, Lazarus group or the Armada collective sent threatening email messages to organizations. Threathening the organization that they were chosen as the target for their next DDoS attack, refering to some of their previous work and continuing that they they will start a large DDoS attack very soon. To prove their threats are to be taken serious, they will perform a small attack using just a fraction of their attack infrastructure on a given asset of the threatened organization.
To avoid the attack they propose to pay a ransom of 10 to 20 bitcoin to a specific bitcoin address. Failing to pay before the attacks start will increase the fee with 5 or 10 bitcoin for every missed deadline while the attack continues.
Between october and november, the ransom letters seem to slow and eb away. Until second half of december where we started to hear from customers receiving new letters. Organizations that were targeted before and received a ransom letter were now subject to a second letter that said the attackers were busy with more profitable projects and they are now back. They refer to the same bitcoin address and ask for a ransom between 5 and 10 bitcoin. The lower ransom was explained by the rise in bitcoin value that surged in December to over a 100% increase compared to earlier that year. They said they would never give up and they will always come back until they are paid.
Come March of 2021 and as we started to put the last Ransom DoS campaign behind us, it would only take until May when new letters started to surface. This time a group, most probably unrelated to the actors from the previous campaigns, was posing as ‘Fancy Lazarus’. A moniker invented specifically to instill even more fear into victims by combining Fancy Bear, the russian APT, known for its ties to the russian governoment and promoting the political interests of the Russian government and the group believed to be responsible for hacking the Democratic National Committee emails in an attempt to influence the outcome of the United States 2016 presidential elections, cyber attacks on the German and Norwegian parliaments, the French television station TV5Monde, the White House, NATO, and attempting to influence the campaign of French presidential candidate Emmanuel Macron.
And Lazarus Group, the North Korean APT believed to be a state-sponsored hacking organization responsible for the 2014 attack on Sony Pictures, the 2016 bank hiest on the Bangladesh bank where they successfully got away with 81 million USD. This time the malicious actor or group were primarily targeting unprotected assets from organizations in different verticals. Asking for a 0.5 to 5 bitcoin ransom to prevent the attack.
September of 2021 was marked by service impacting DDoS attacks on VoIP telecommunications providers in the United Kingdom and Canada. Starting September 1, UK South Coast–based VoIP operator Voip Unlimited disclosed it was hit by a sustained and large-scale DDoS attack it believed originated from the Russian ransomware group “REvil” following what they described as a “colossal ransom demand.” After 75 hours of continuous attacks, on September 3, Voip Unlimited reported a pause in malicious traffic and confirmed a few days later that they did not observe any further attacks. At the same time, also starting September 1, the London-based Voipfone reported suffering outages on voice services, inbound and outbound calls, and SMS services. It was later confirmed to customers via e-mail that Voipfone services had been “intermittently disrupted by a DDoS attack.” On September 16, a Canadian provider of telephony services, VoIP.ms, announced it became aware of issues preventing customers from accessing its website and were working toward a solution.
One week later, the issue was still ongoing and was attributed to persistent aggressive DDoS attacks causing disruptions in phone calls and services. Public messages exchanged on Twitter between VoIP.ms and the threat actors going by the handle @REvil92457183 provided more insights. The threat actors behind the DDoS assault went by the name ”REvil,” but there is no evidence they represent the same REvil ransomware gang that is known to have previously attacked prominent companies, including the world’s largest meat processor, JBS. As a ransomware operator, it is not conforming to the tactics, techniques and procedures (TTPs) of REvil to perform DDoS extortion attacks. It cannot be excluded, though. It would not be the first time a criminal group is diversifying its activities.
A now-removed Pastebin note put the initial ransom demand at 1 bitcoin, or a little over US$42,000 (at the time of publishing). However, only two days after the initial demand, the @REvil92457183 twitter account increased the demand to 100 bitcoins, or over US$4.2 million, when it messaged: ”Ok, enough communication… The price for us to stop is now 100 Bitcoin into the pastebin BTC address. I am sure your customers will appreciate your 0 f…s given attitude in multiple law suits. REvil”. The actors used Twitter to expose the attacks and condemn VoIP.ms for not paying, in an attempt to make its customers and partners put pressure on the service provider to pay the ransom and rid them of service disruptions. Ransomware operators use similar pressure tactics, such as leaking new victims and sensitive data obtained from victims on their dark web PR sites. Messages from VoIP.ms on Twitter show that the attacks were initially targeting VoIP.ms’ domain name services. VoIP.ms mitigated these attacks by asking partners and customers to hardcode service IP addresses in their systems.
On October 7, Voip Unlimited again reported intermittent loss of connectivity and voice services as its engineers were working to mitigate DDoS attacks against its telephony platforms. Issues were first reported on its service status webpage in the evening on October 7. In the evening on October 8, VoIP Unlimited was still reporting disruptions caused by ongoing DDoS attacks against its customers.
Hacktivist
Much the opposite of the organized crime, these malicious actors are not driven by financial gain but mainly by political or ideological ideas. They are out for defacement, doxing and destruction or disruption of websites and resources, all with the aim to promote a political agenda or a social change. Businesses can become entangled and in the crosshairs of hacktivists wihtout even having control over the situation. These groups are typcially unsophisticated but rely on their large following and social media to perform and promote attack campaigns. They use private forums to distribute and educate their followers on denial of service tools. These tools are typcially ancient and very simple, well known and publicly available. Yet, in the hands of a large enough crowd, these simple attack tools become very effective distributed weapons. In the recent attack campaigns orchestrated by the politically oriented hactivist group Dragon Force Malaysia, tools like torshammer, low and high orbit ion canon also known as LOIC and HOIC, and a mobile attack tool for Android called Garuda, were leveraged in cyber attacks against Israeli targets throughout the month June and July 2021 to protest against the strengthening of diplomatic ties beween the Israeli governemnt and Southeast Asia’s Muslim-majority nations.
Disgruntled employees and angry customers
Another group of typically lesser sophisticated attackers, operating as lone-wolfs, are disgruntled employees and angry customers. The gaming and betting industry is frequently targetted by unhappy customers that act on flaring emotions and driven by anger upon losing large amounts of money in bets. But we also see this group across other verticals, like when a website is advertising wrong information, an incorrect or unadequate delivery of goods or services, etc.
Given their needs for immediate and temporal access to an adequate tool, this group mostly resorts to publicly available DDoS-as-a-Service portals that provide convenient and subscription based access to DDoS botnets and attack servers. In just a few clicks these actors can easily disrupt online resrouces and harm the reputation of businesses.
[You may also like: 2021 Year in Review: Denial of Service]
Nation states
Nation States on the other hand have the expertise and resources to build vast weapons of destruction, in the physical as well as in the cyber world. Mostly known for using cyber weapons to cause disruption and chaos in an attempt to destabilize economies or regimes. Critical infrastructure such as power grids, fuel pipelines, water supply, but also financial institutions can be the target of competing nations and fall victim to large scale attacks, amongst which DDoS are very effective as attribution is so hard and one of the prime objectives of nation state attacks is not to get caught in the act or trying to influence foreign politics by blaming another nation.
Competitors
Finally, I want to highlight a frequently forgotten threat group that is more present than most would suspect: competitors. Unsurprisingly, this group’s aim is to get competitive advantage by destroying the reputation, stealing intellectual property or undercutting prices of competing businesses and nations. This group will resort to automated attack tools such a bots to scrape information, some will hire attackers to disrupt services while other will step up the game and sponsor groups to infiltrate and steal confidential and sensitive information.
In the aftermath of the Mirai botnet attacks against Krebs, OVH and Dyn DNS, an actor going by the name of ‘best buy’ was observed and stopped while trying to enslave 900,000 of Deutsche Telecom’s consumer internet modems. Bestbuy, or Daniel Kaye in real life, already owned a 400,000 bot Mirai based botnet at the time. He started his project after being hired by the CEO of Cellcom Liberia to destroy the reputation of Lonestar MTN, Cellcom’s largest competitor in Liberia. Daniel started his attacks through the most renowned stresser service at the time: ‘vDoS’. vDoS didn’t provide him the power needed to disrupt a large mobile organization such as Lonestar. Given the then recent publication of the Mirai botnet source code, he picked up the code and build his own botnet. In November 2016, in an attempt to disrupt the services of Lonestar MTN, Daniel Kaye, hacker-for-hire, disrupted the internet connectivity of the whole of Liberia. Daniel Kaye was apprehended in January 2019 in Luton Airport in London UK while travelling home to Cyprus after meeting with his Cellcom contact.
Which tools and techniques do attackers prefer to use for DoS attacks?
Actors who are less sophisticated will reach for DDoS-as-a-Service portals. These portals are widely available on the clear net and can be found through simple Google search. DDoS-as-a-Service platforms, also known as booters or stressers, wield enough attack power to impact most organizations.
For those with bigger ambitions, like organized crime groups or hackers-for-hire, stresser services typically do not provide the scale, flexibility or Return on investment. They tend to build their own attack tools consisting of botnets and attack infrastructure. Botnets are typically used to generate high packet or request per second attacks that drain the resources of network devices or servers. Attack servers are typically used to perform reflection and amplification attacks. These servers scan for internet services that allow amplification attacks, such as DNS, NTP, SSDP, and Memcached, amongst others. Once amplification server lists are compiled, the attack server will leverage those in uplink saturating volumetric DoS attacks. Do not be mistaken, the internet is full of potential for amplification. Reflection points do not need be large servers. We have observed many attacks leveraging well-known router brands that expose DNS services that allow recursion by default. In 2021, academic researchers published a paper detailing new ways of leveraging forged TCP packets to generate devastating DDoS amplification attacks with amplification factors ranging from 50,000 to 100,000,000s.
How can you protect yourself? Which defense mechanism is the most effective?
In our experience, a cloud-based solution is the most effective at stopping all attacks, even those volumetric attacks that are beyond the capacity of the internet links of the protected site. The ultimate solution for businesses that require the lowest latency and best protection is a hybrid DDoS solution. This option combines on-prem detection and prevention, while automatically diverting to a cloud scrubbing center when the attack volumes are threatening to saturate the internet links.
The future of the DDoS Threat Landscape
As bandwidths of interconnects, clouds and internet connections grow, attacks are becoming larger and more impactful. Our businesses and lives (home automation, online streaming, connected cars) are becoming ever more dependent on internet connectivity. Digitalization accelerated during the pandemic, and that means there is more opportunity to impact businesses and people through DoS attacks. Motivated by the success of past ransomware campaigns, there is a good probability to see an increase in ransom DoS attempts in the near future.
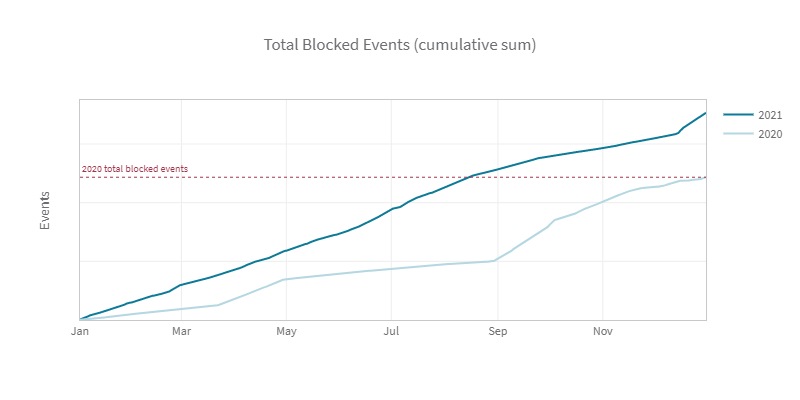
With a steady growth in blocked malicious events per customer, it does not look like DDoS attacks will disappear anytime soon. With all the vulnerabilities disclosed in the last couple of years the opportunity to build large botnets and abuse more capable amplification services keeps growing. As we digitalize our businesses and our lives by migrating applications to the cloud, creating fully meshed dependencies between online and mobile applications, depending more and more on services and web APIs provided by third parties, connected cars, connected homes, consumption of online video, we start to depend ever more from cloud and connectivity and we make ourselves more vulnerable and create more opportunities for bad people to abuse.
Motivated by the success of ransomware campaigns, there is high probability to see an increase in Ransom DoS attempts in the near future. My team of researchers are all aligned on a future that will bring more and larger denial of service opportunity and attacks, which is why we are observing very closely the moves, tactics and techniques of malicious actors in the DDoS threat landscape, reporting and sharing our observations and trying to help businesses to protect themselves timely and accurately so bad guys can make little to no impact with their onslaughts. As with most security threats, if you can take away the economy from the threat, attacks and attackers will slowly fade away. But it is very much a perpetual circle that puts us back in every achievement as technology and digitalization of the world continues.
Learn more about threat actors and their tactics and techniques in Radware’s 2021 Hacker’s Almanac – The Evolution of Threat Actors.
Like this post? Subscribe now to get the latest Radware content in your inbox
weekly plus exclusive access to Radware’s Premium Content
*** This is a Security Bloggers Network syndicated blog from Radware Blog authored by Pascal Geenens. Read the original post at: https://blog.radware.com/security/ddos/2022/01/what-drives-ddos-attacks-and-why-it-should-be-a-concern/




