Planning Your Cybersecurity Budget for 2022
The fast-paced IT world has changed where cybersecurity has become a paramount concern. Businesses all over the world will be preparing to spend their cybersecurity budgets for the coming year.
In 2021, around 66% of cyber attacks happened in the year alone, and attacks’ frequency has increased. Every 11 seconds, a business or an individual falls under the trap of ransomware attacks. Earlier it was 40 seconds. We can imagine how fast we are proceeding to the cybercrime world.
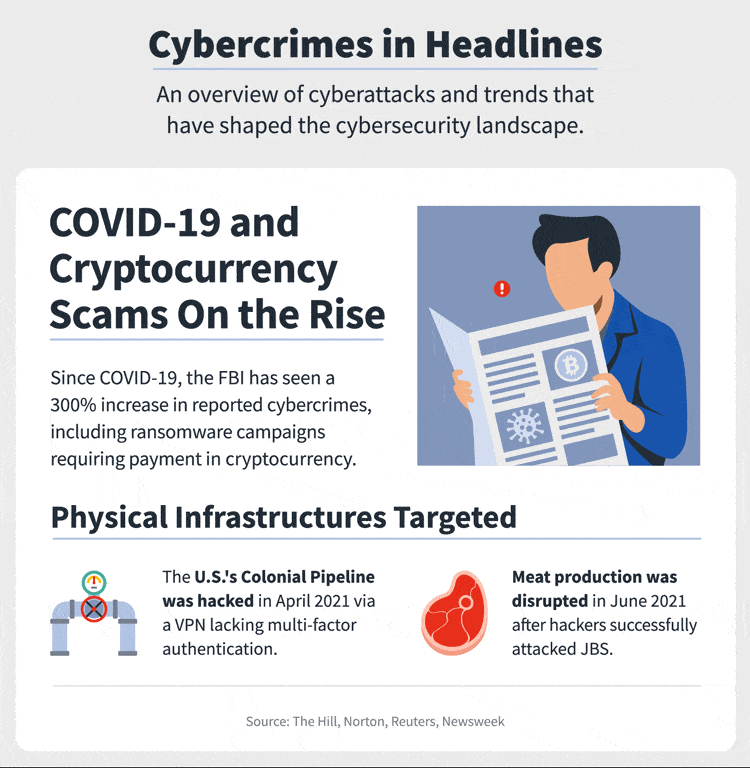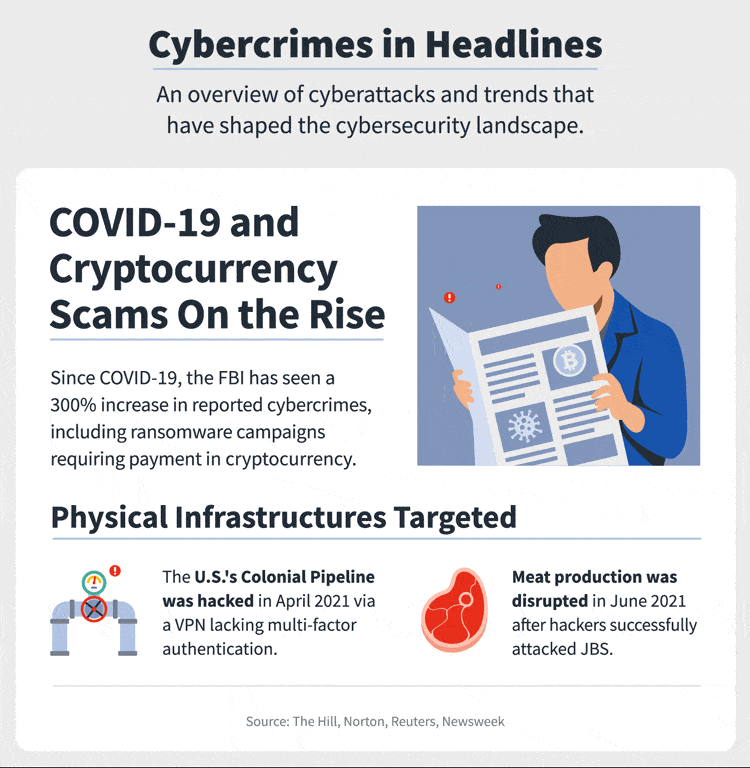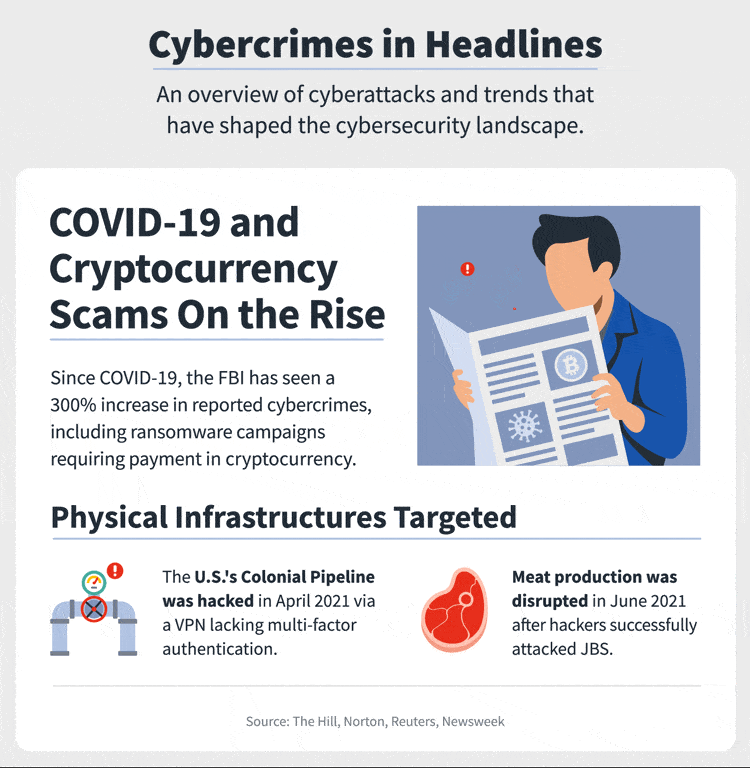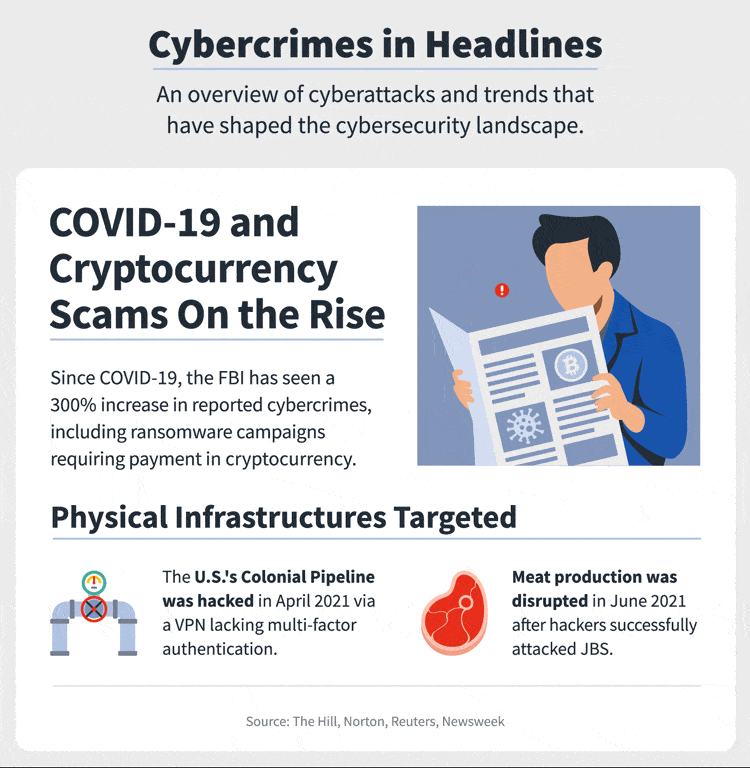
There is panic all around in the cyber world. Entrepreneurs are worried and thinking of the right strategies to cope with their cybersecurity challenges. We need to plan our cybersecurity budget accordingly. Otherwise, nothing can save us from a business disaster.
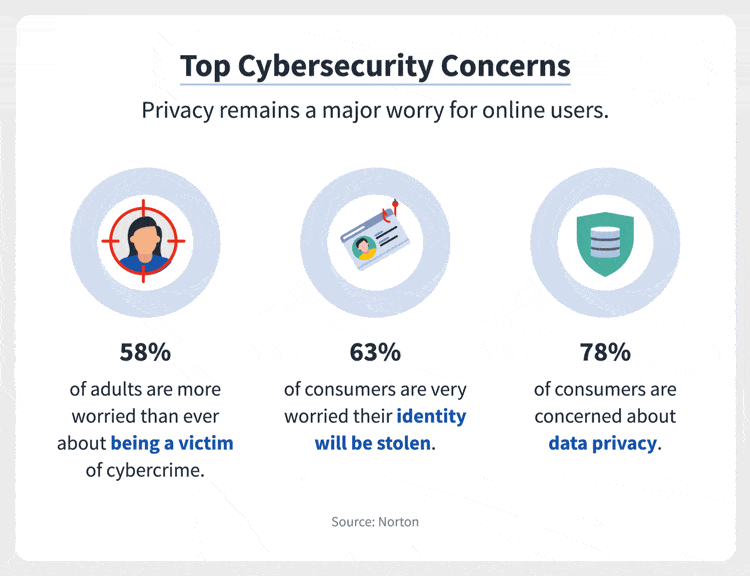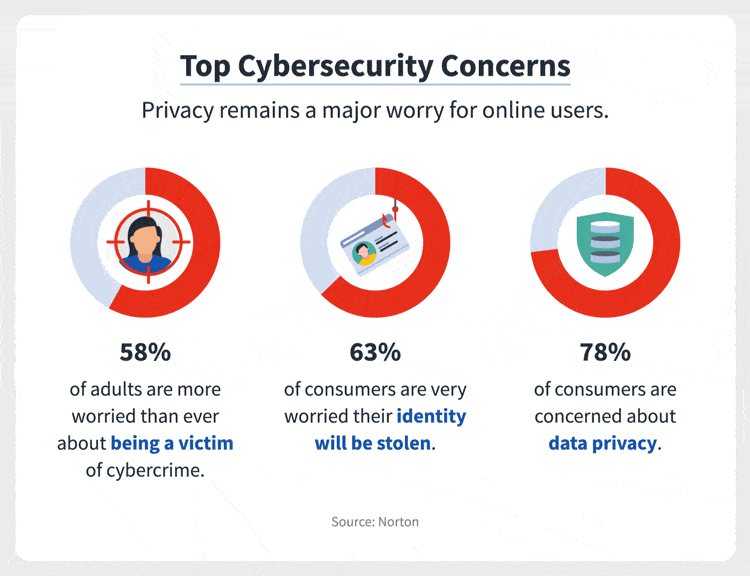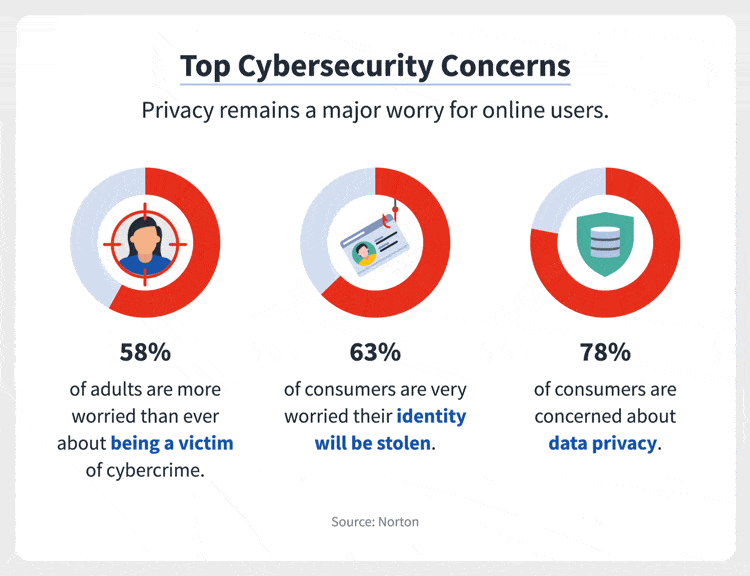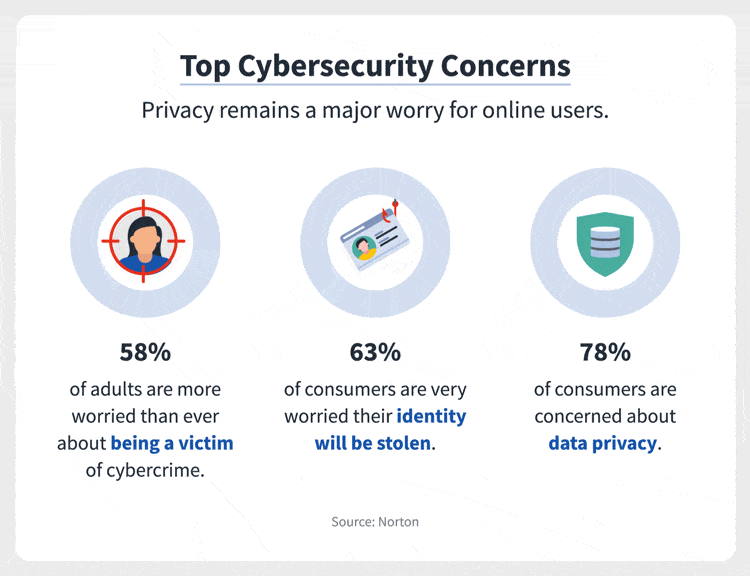
Indeed the cybercrime has become a global concern now. All are thinking of the best solutions to keep these problems at bay. However, many organizations are still unsure about how to allocate those funds in a way that will be most effective for their needs.
To help make things a little bit easier, I’ve put together a guide on how to plan your cybersecurity budget for 2022. Here, I would like to share the top ten areas you must focus on while spending your cybersecurity budget.
So, let’s get started.
1st Priority: Deploying MFA Effectively
Multi-factor authentication is a process of verifying users by using more than one type of authentication factor. It is considered one of the best methods to protect organizations from cybercrimes.
Organizations are investing in authentication technologies. MFA is considered one of the best among them because it helps provide better security for your employees and customers. It also provides reliable protection against data breaches. There are different types of Authentication factors include knowledge factor ( something only the user knows), a possession factor (something only the user has), and the inherence factor (something only the user is).
2nd Priority: Ransomware Risk Assessment and Prevention
A ransomware attack is a significant cyber security risk that every business faces. These attacks have become an urgent problem these days. With time, we can expect its growth rate as well. We read many ransomware crime cases in the newspapers and hear from people around us.
The best way to prevent ransomware attacks is by doing a risk assessment. You need to identify the most vulnerable areas to ransomware and take the necessary steps to protect them. You can also use some preventive measures such as backup and anti-virus software.
3rd Priority: Cloud Inventory and Configuration
Cloud computing has become an essential part of our lives now. This is because it provides many conveniences to people and businesses around the globe. It saves time, money and it reduces environmental pollution as well.
The same way Amazon Web Services (AWS), Microsoft Azure, Salesforce, etc., are significant assets to businesses, but they also pose a risk for organizations if not configured correctly. Unauthorized access to cloud assets, vulnerabilities in security settings, etc., are the risks you need to tackle as a responsible business owner.
4th Priority: Supply Chain Risks and Breach Preparation
Cybersecurity is not just an issue for an individual or a company but also a global concern. Organizations can protect themselves by investing in the right strategies and planning.
Supply chains are the backbone of every business! It helps increase your business growth rate and adds value to your customers. But, if not managed properly, it can make you prone to security risks.
Take proper actions while dealing with supply chain partners because many cyber criminals hide their identities through these relationships. Make sure to have a cyber security plan in place so that you can quickly detect and prevent any breaches.
5th Priority: Proactive Threat Hunting and Monitoring Services
We are in the era of big data and advanced persistent threats (APTs). Cybercriminals are getting smarter day by day, and it has become difficult for the average organization to manage its IT security.
Threat hunting is one of the best strategies that you can adopt to protect your critical data from being stolen by an unauthorized person. We also need a robust cyber security plan to detect threats early on and address them accordingly.
Many companies on the internet can provide you with these services. It is better to invest in a reliable threat hunting service provider rather than doing it yourself because this way, you can save time and energy as well.
6th Priority: Training Priorities for Your Leadership and Team
People who work in cyber security should be well equipped with the latest technologies and strategies adopted by cybercriminals. Up-to-date knowledge about threats, response methods, and prevention techniques can help people to do their job efficiently and, more importantly, improve your company’s security posture.
Training is an essential aspect of any security strategy because it helps organizations evolve with every new development in the field. To get the most out of your security investment, you need to ensure that your team is adequately trained and has access to the right resources.
7th Priority: Developing a Cybersecurity Incident Response Plan
As the number of cyberattacks grows at an alarming rate, organizations need to develop a robust incident response plan. It can be used as a guide if your system faces any malware or virus attack. Without having such plans in place, you may not know what to do when a security breach occurs.
If you are not sure how to develop a security incident response plan, you can seek help from experts in the field. They will provide you with the necessary guidance to protect your assets effectively.
8th Priority: Penetration Testing and Vulnerability Assessment
Organizations need to keep their software and systems up to date with the latest patches and security updates. However, this is not always possible due to various reasons. Organizations need to conduct regular penetration testing and vulnerability assessment in such cases.
This will help them identify any potential weaknesses in their system that cybercriminals can exploit. It will also help them take the necessary action by updating their software and plans accordingly.
9th Priority: Using artificial intelligence to Comply with Regulations and Security Standards
As the number of cyberattacks increases, organizations are under pressure to adopt various measures to protect their systems and data. One of the best ways to do this is by using artificial intelligence. AI can help organizations automate multiple tasks such as identifying and responding to threats. It can also help them to comply with different security standards and regulations.
10th Priority: Using Big Data and Predictive Analytics for Threat Detection and Prevention
It is important to monitor activity across your entire network to be aware of any suspicious activities. By tapping into big data and predictive analytics, you will be able to uncover hidden threats and take the necessary steps to protect your asset. Big data can also help you understand your customer’s behavior and improve your marketing strategy.
Closing Thoughts
These are some of the top areas you can focus on while planning your cybersecurity budget for 2022. Make sure to invest in the right strategies and technologies so that you can stay ahead of cybercriminals.
So, what are you waiting for? Start prioritizing your budget and get the most out of it. If you need assistance or guidance, reach out to a cybersecurity company or agency to help you prioritize.
Download the latest eBook:
Learn the Basics of Cyber Security & Take the Lead: eBook
The post Planning Your Cybersecurity Budget for 2022 appeared first on WeSecureApp :: Simplifying Enterprise Security!.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security! authored by Naimisha. Read the original post at: https://wesecureapp.com/blog/planning-your-cybersecurity-budget-for-2022/





