Patch Tuesday Update – October 2021
74 patches, 4 zero days, and an active exploit
For October, Microsoft released patches for a total of 71 security vulnerabilities. Compared with this time last year, the total number of patches released is lower, but the number of zero days has increased. This month, we have 3 critical patches to contend with, and a whopping 70 marked as important. One thing to note, Microsoft doesn’t classify patches as critical by default if there is an exploit or if the patch is for a zero-day. The scoring system used takes a number of factors into account, including ease of exploitation, potential impact, etc. That said, exploits and zero days are very dangerous and need to be patched ASAP.
The critical patches for this month include two remote code execution (RCE) vulnerabilities for Windows Hyper-V: CVE-2021-38672 affects Windows Server 2022 and Windows 11, and CVE-2021-40461 which hits both Windows 11 and Windows 10. The third critical bug, also a RCE, affects Microsoft Word (CVE-2021-40486).
The active exploit for this month (*sigh*, again only marked as “important” by Microsoft), is an elevation of privilege vulnerability that affects the majority of Windows versions. Elevation of privilege vulnerabilities are typically used in concert with other flaws to gain further access into vulnerable systems.
Other important bugs addressed this month include CVE-2021-26427 for Microsoft Exchange Server, another RCE threat. This should be patched quickly, but Microsoft was quick to explain that in order for an exploit to occur, the attacker must already be in the network.
Last, but certainly not least on the Microsoft front, yet another bug was found in the infamous Windows Print Spooler. If you recall, back in July, Microsoft was forced to release an emergency mid-month patch for what is now known as the PrintNightmare attack. This flaw (CVE-2021-36970), is a spoofing vulnerability that currently also requires direct network access, but Microsoft has still given the designation “Exploitation More Likely” to this one, and given the recent activity surrounding Print Spooler, this is one to patch ASAP.
On a non-Microsoft related note, Apple has also released some very important patches for its iOS and iPadOS operating systems. A zero-day vulnerability was discovered that could allow attackers to steal data or install malware. This vulnerability CVE-2021-30883 has been seen exploited in the wild, so be sure to update your Apple devices.
As always, Balbix can identify all affected assets within 1 hour of release. There are no scans to run. Balbix customers can search for the CVE name in the Balbix dashboard to view the list of affected assets. You can also use the filtered search functionality to search for the CVE by site, subnet, location, or other distinguishing factors.
A Call to Action For You
How quickly can you resolve the exposure from this set of CVEs?
Remember you are racing against the adversaries. The industry average for mean detection time for CVEs in IT networks is 15 days and for MTTP is over 150 days. Balbix customers can detect CVEs in less than 1 hour and fix them within a day or two. As the example shown in the graph below illustrates, your likelihood of breach due to unpatched software will go up for a few hours (as new CVEs are identified) and can come down just as fast (as they are fixed).
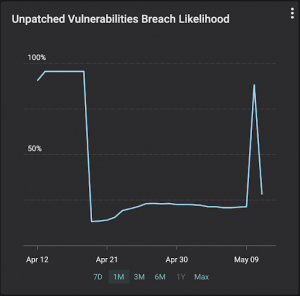
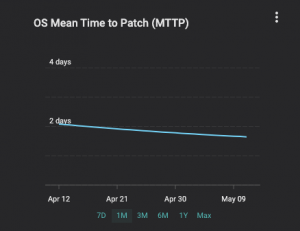
Over time, Balbix users typically achieve a decrease in mean time to patch (MTTP), as the graph below shows for a customer we onboarded earlier this year.
If you have additional questions, please contact [email protected].
See Balbix Live
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Matt Barrett. Read the original post at: https://www.balbix.com/blog/patch-tuesday-update-october-2021/





